Hackers on the screen - 2

This post is a continuation of an article about how hackers are portrayed in movies . This topic seemed rather interesting to me (and far from exhausted), and this weekend I decided to continue to describe the phenomenon of “hackers on the screen” and complement the collection of film clips.
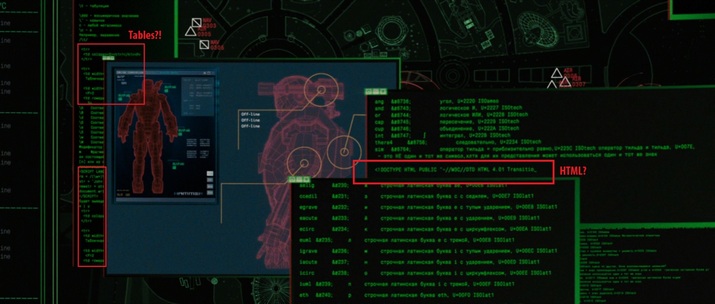
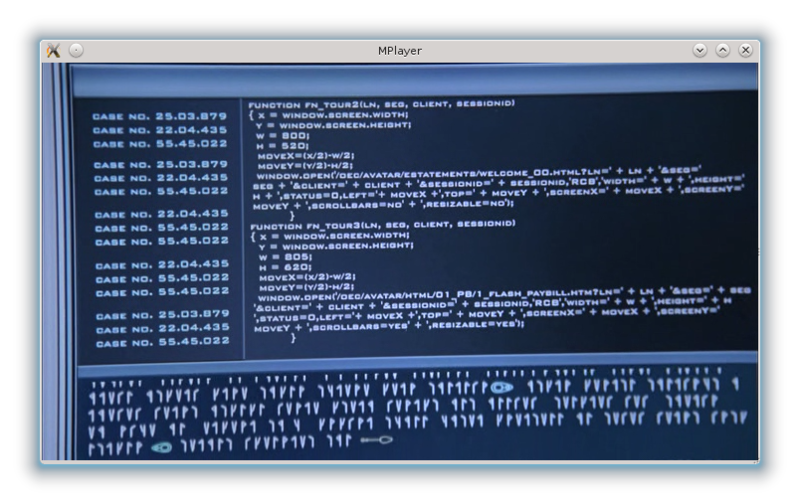
At KDPV, a still image of the movie "Iron Man-2". As you might guess, the designers who draw this combat suit control interface went into the first Russian-language online store selling air conditioning (touches even the preserved name of the variable “kolichectvo”) and cut out part of the html code ...
Nothing happens in life. Of course, something constantly happens in life: they don’t get paid on time, the child is sick, winter suddenly comes, but the series of pseudorandom cases is monotonous, like the work of a Chinese man at Foxconn factory. Therefore, we love artistic fiction, in which the line of life is a flickering arrhythmia. A doctor, no, no, and he'll watch a series about doctors, a policeman about honest cops, a programmer will appreciate an IT-themed movie with mandatory action, which in the real world is limited to cursing guests at the server room.
What could be more intense and exciting than films about hackers? A good film and blunders will not spoil. An attentive viewer will especially enjoy looking at the interfaces of movie programs, flickering lines of code and the negligent work of a technical consultant.
Orthodox geeks are not so common among viewers who are ready for every blunder to burn the stigma of scriptwriters and directors. Errors in films are most often nothing more than a convention that adds to the entertainment. It’s hard to blame the director for spreading sound in space, if the rest of the picture is fascinating. With this opinion, you can look through your fingers at cool hackers, robbing banks, erasing digital traces of personality, controlling any technology with ultra-fast typing on the keyboard without using spaces.
Bloopers in films, whether they are connected to computers or not, are a funny trifle, which you recall only on thematic online forums. Or when the real masters of the word, representatives of cosmic horror, who take to flight any professionalism endowed with such colossal, ultralight illiteracy, that cover the neurons and axons of the viewer with a crust of thick dirty ice of insensibility, take up the matter.
We are talking about the creators of stereotypes trying to please any audience. Do you think that in most films, hackers are eccentric, but cute helpers of the protagonist who solve complex problems exclusively by the power of intelligence? It is disappointing to realize how the film industry actually forms the image of an ordinary programmer in the mass consciousness, not to mention the high-tech environment guru. If this is not the story of a person of the Jobs level, with an IT specialist on the screen you can do any vile things.
One could assume that such scenes are the result of an NSA conspiracy with Hollywood producers, whose goal is to make the hacker's “profession” so complicated and incomprehensible that it discourages ordinary (novice) users from any desire to learn programming languages, operating system vulnerabilities, or even the “security” tab »In Facebook settings.
But, unfortunately, everything is much simpler: this is just the fruit of poor-quality work of scriptwriters who are trying to write about what they don’t know. After all, they could spend several minutes searching on Google to avoid embarrassing situations, but each time, in every scene, they convince us of their own pathological laziness. Of course, this is only a movie, so “smart technology” can look like anything silly.
My "two penny" in the collection of kinolapov:
Do the authors really believe that most viewers are idiots? What in 2013 you can look at the monitor and ask "is that 12-core?"
In the world of the Numb3rs TV series, chat that millions use is used for secret negotiations between hackers. Guess how the police will track down the IP address of hackers. Technology is magic, username.
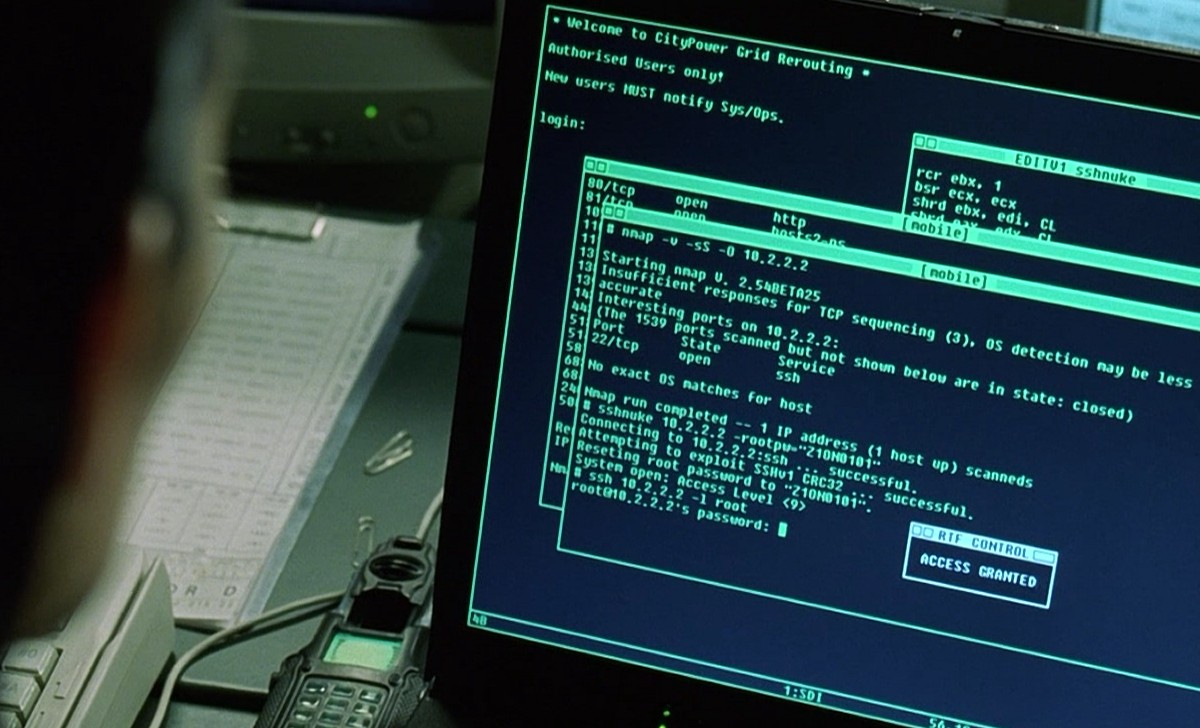
In the screenshot - one of the few real programs that flashes in Hollywood films. You say that everything is ok? This is actually the only real program appearing in films. In many tapes, Nmap is a formidable weapon for hackers (only JavaScript is more popular). It doesn’t matter how the characters use this program, the main thing is to show beautiful shots:
Dredd (2012) ( http://nmap.org/movies/dredd/dredd-nmap-trailer-screenshot-1589x805.jpg ),
Bourne Ultimatum (2007) ( http://nmap.org/movies/bourne/bourne-nmap-1.png ),
Die Hard 4 (2007) ( http://nmap.org/movies/diehard4/nmap-diehard4-1080p-1920x801.png ), The
Girl with the Dragon Tattoo (2009) ( http://nmap.org/movies/gwtdt/ gwtdt-nmap-screen.jpg ), Wiretap
(2006) ( http://nmap.org/movies/listening/2.png ),
Chase (2011) ( http://nmap.org/movies/abduction/Abduction- Nmap-1920x800.jpg ),
Extract (2012) ( http://nmap.org/movies/extracted/extracted-nmap-clip.png ),
Battle Royale (2000) ( http://nmap.org/movies/matrix /Battle-Royale-Nmap-1-344x214.jpg ).
And even in the movie HaXXXor: NoLongerFloppy.
The quality of the films does not correlate with the use of real software in the plot. Its appearance is more often accidental, and in other cases so insignificant that it is designed for geek fans who are ready to discuss this interesting fact with friends.
(clickable) Do you know how to control robots using html code? The film "Iron Man 2" as if tells us "this is nothing complicated." Let's take into account that on the screen is a drone controlled by a harsh Russian programmer. All three parts of Iron Man are incredibly pleasing with the code, review carefully. Firewall (2006). Hacker uses brute force. Harrison Ford knows how to stop the attack - we look at the console. Any student who is interested in computers will feel disappointed.
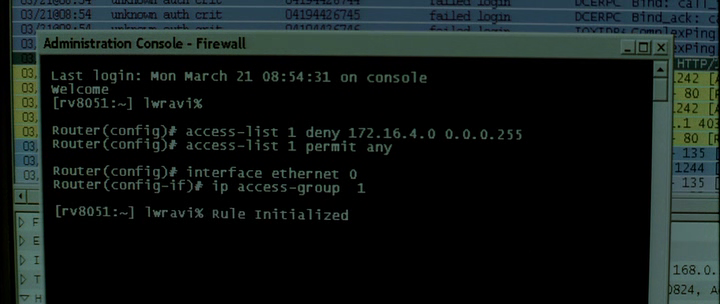

Win2K will outlive us all. Who will guess the series in one frame?
Creepy code from StarGate. To many, he may dream of nightmares.
In the remake of the Italian Robbery movie, characters must crack the traffic control system and cause a traffic collapse in the city. Judging by such films, then every computer in the world is connected to the Internet and, therefore, is available for hacking.
If you add a hacker to the plot of any movie, then the implausibility of the actions on the screen will be off the scale. One of the most epic shots in “hacker films” is hacking driving a car using an application in a smartphone. The hacker will not only open the car, but also be able to remotely turn off the alarm. This is not a simplification of complex technologies for viewers. This is just a swindle.
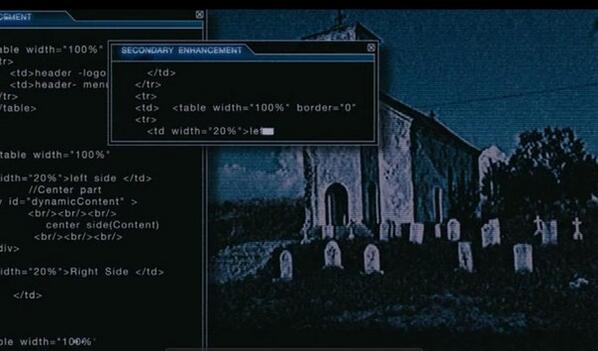
Hacking the system in the film "Survival Tournament."

So in the series " Arrow " looks like "military-level encryption algorithm."
This list can be continued indefinitely. “ So what,” you say, even in the dumbest scene (NBC, Life) there is a certain element of entertainment. We will forgive everything for him!"Friends, the police find out that the only way to get an encrypted file is to complete the game" Prince of Persia: Two Thrones "to level 10, after which the secret file will be opened on the screen; the hacker actually rewrote the game code to crank up such a tricky trick. Horror is not that. What do you think, who dares to pass all the tests to get the file? The man who pronounces the following sentence: “ Detective, I’m 30 years old, I live with my mother and I have Captain Kirk’s costume in the closet .”
PS It is worth recognizing that not all screenwriters (or movie interface designers) are equally

Of course, it is not clear why this code should be displayed on the screen at the time of authorization, but still it is much better than a code fragment from the online store of air conditioners :)
PPS The number of films and TV shows that are released daily is amazing (oh, if I were to collect all these budgets, let’s go into space exploration ...) And given the fact that more and more people are dealing with computers, stories with computer mistakes will appear more and more often. So I will be glad if someone picks up this baton and writes a “sequel” to this post :)
