Attackers can get full remote access to the Android device through a public USB charging port
With the advent of USB devices and USB ports into our lives, one of the main security requirements was the attentive attitude to connection points that are able to transfer data between devices. Actually, for this reason, in the Android OS, from the earliest versions (from 2.0 for sure), there is an option to manually enable the device port to transfer information with the connection object, i.e. with a USB port. Without activating this function, the device only charges from USB, ignoring all sorts of (obvious) requests for information exchange from the second side.
But Kevin Butler and his research group in the field of information security at the University of Florida recently discovered a very elegant and, at the same time, quite dangerous way to attack user devices via a USB port. At the same time, the port itself appears to the observer only as a power source and can be placed in any public or not so much place, for example, on an infected PC, in a cafe or a charging point for USB devices at the airport. For an attack, one condition must be met, in addition to access to the data exchange with the charging port from the attacker: leaving the smartphone screen out of the host’s sight (so that he doesn’t notice that the device has become “living its own life”).
At the same time, the screen lock password is bypassed with one short command, which gives the attacker access to the main screen of the smartphone.
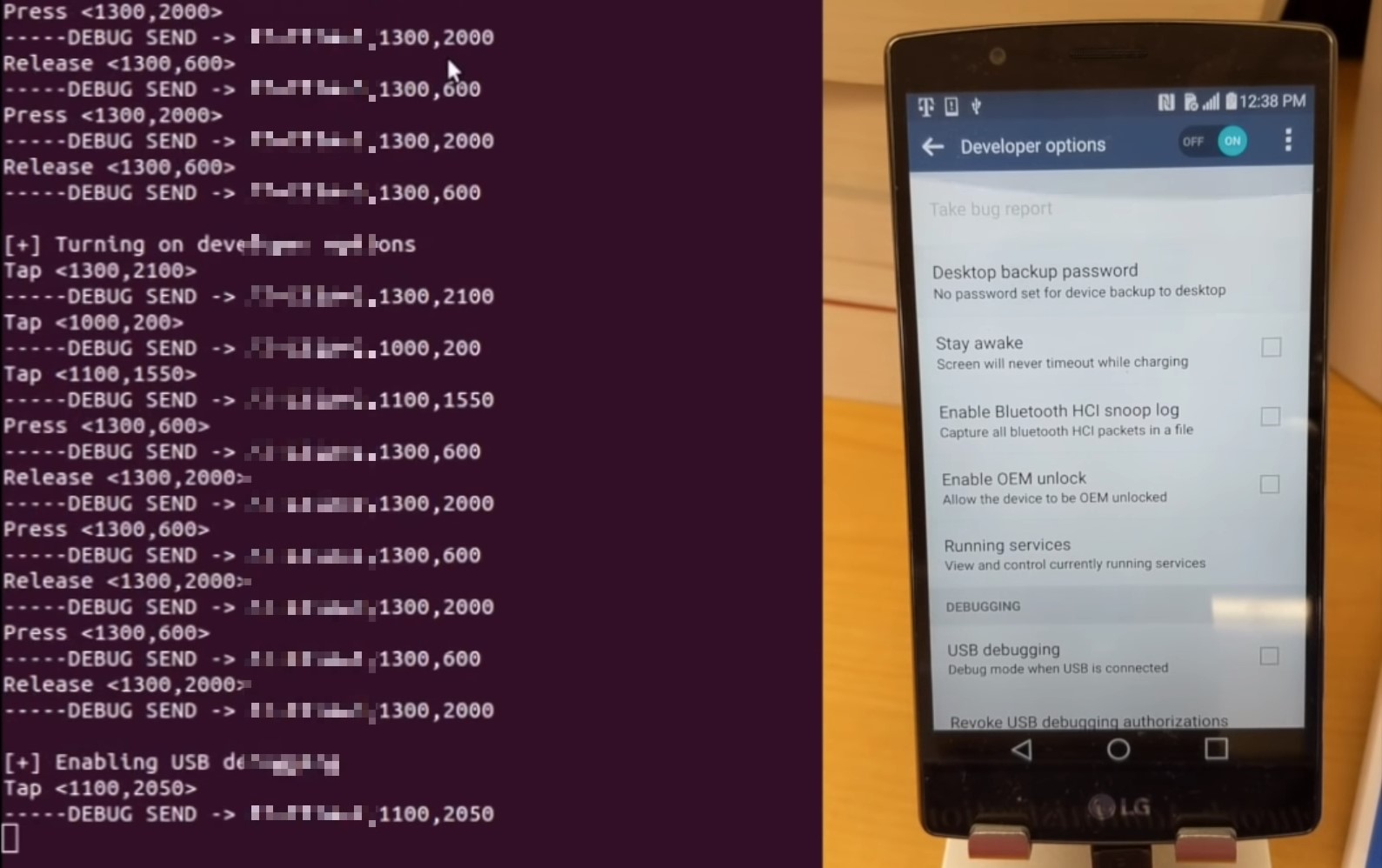
According to the report of Butler and his team , in the attack on smartphones, undocumented AT commands can be used in an original way to remotely control the screen of a smartphone, which technically eliminates various protective functions of the OS from third-party interference. In fact, the butler and his team found a way to create a “Ghost User'a,” completely deceiving the existing Android security functions and completely imitating touching the screen with low-level AT commands. Samsung and LG devices are susceptible to attack - laboratory experiments were performed on the devices of these manufacturers.
Such an attack vector has long been known to information security specialists. The first reports that a device connected via USB can become the target of an attack by attackers date back to 2011-2013. For example, at that time, Kaspersky Lab experts warned users that connecting any USB device involves the exchange of identification codes between the user device and the periphery. We also talked about using this attack vector in our article about deception and hacking of Apple devices and their new USB Restructed function.
But if they got used to fighting with obvious attacks on the OS itself, the use of low-level AT-commands has not been widely used yet. Butler and his team recorded the whole video in which they hold a demonstration of the remote control of the user's smartphone under the guise of interaction with the screen. This attack is simple because the primary exchange of identification data allows you to determine the type of device, the model and the installed OS. And then it’s already a matter of preliminary preparation for “blind” orientation. Here is how it looks in the console from the side of the attacker and how the device attacked in this way behaves:
What threatens this attack users?
In fact, the ability to use AT commands to gain access to the screen under the guise of a living person gives attackers complete control over the device. This means that through harmless-looking USB charging from your smartphone, you can send messages, make a call, sign you up for services, send all your mail, enter your Internet bank and steal 3d-Secure codes, turn on the camera and take a photo, use any application on the smartphone at all, enable developer-mode and even reset the device “to the factory”. Simply put, it all depends on the attacker's fantasy.
Butler and the team previously reported on their discovery, and LG released the corresponding patches in Julyclosing a vulnerability. However, in the hands of users are millions of devices that are never updated. Right now, a team of researchers checks for the vulnerability of smartphones of other popular manufacturers, first of all, Apple products, but the fact that AT teams can be used in a similar way already suggests that the “holes” in information security of modern devices are fundamental . The analogy of Specter and Meltdown involuntarily asked , the possibility of their existence, as in the case of AT commands (the standard was developed in the 1970s), arose due to problems with the architecture and the method of development that was once chosen.
Study documentation can be found here.. Also, the sources of undocumented commands are uploaded to the repository on GitHub .
Are you an experienced developer, architect or head of an IT company and are thinking of changing your place of work? Check out our SA , CA , SEM vacancies and positions on My Circle .
Perhaps they will interest you.
