Mikrotik, 3 providers, switching and sharing traffic
Write this post I was prompted by this question habrahabr.ru/qa/38801
Those who are interested please ask for cat.
And so it is given:
1 port - Provider 1
2 port - Provider 2
3 port - Provider 3 (backup)
4 port - Network 1 192.168.101.0
5 port - Network 2 192.168.102.0
Question:
From here it’s a little unclear what to do if the first provider fails, drive traffic from 4 ports to the second provider or immediately to the third.
Suppose that the third provider considers traffic for us and therefore we will have the latest one.
And so here are our interfaces.
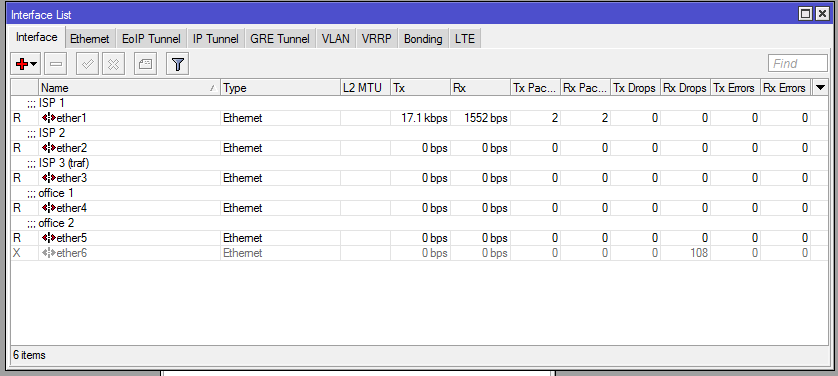
Further, our IP addresses.

And finally, our routing table.
Explanations are needed here. For each provider we created a default route with a route marking.
I need the first route in order to configure MikroTik itself.

That's all. Our MikroTik is ready for further fine-tuning.
In the next step, we will configure the responsiveness of MikroTik from all providers.
Our task is to make it possible to reach MikroTik through all three providers.
To do this, we must catch incoming connections and mark connections, the next rule is for a marked connection to make a return to the provider from which the connection came.
I’ll try to decrypt humanly
Rule 0
If the packet that came to the first interface (ISP 1) has the IP address 172.25.25.247 (ISP 1) in the destination address, then mark the connection with the name (ISP 1 -> Input)
Rule 1
If the outgoing packet belongs to the connection with marked (ISP 1 -> Input), then we use the ISP 1 route for it.
Thus, the router knows that if it (ping or any incoming traffic) is from ISP 1, it will return the answer through ISP 1 provider
. And understanding.

Well, now we can access MikroTik through any provider.
It is time for each office to deal with traffic from the fourth port. But first, we will prudently prepare one small but subtle nuance, since we will use prerouting then the traffic before the “Hit” in the routing table must be filtered.
It is necessary to create address sheets with networks that should not be marked.
I usually call it LocalNet and this time do the same.
And so we created the sheets of local networks, now we will proceed with the routing of traffic.
Before the packet leaves the router: if the sender address is on the network 192.168.101.0/24 and the destination address is not listed, then we mark the route with the name office 1
Quite simply, this is all traffic that belongs to office 1 and does not go to our other local subnets .
Next, we need to create three routes for office traffic 1
A little clarification check-gateway is a procedure for automatically checking the availability of a gateway, since I have this L2 connection, in my case arp is better than ping, if you have L3 (pptp etc) then put ping.
It is also necessary to pay attention to the distance, it’s just on it that the router determines with the same destination address what priority routes are.
Well, now the final part of our "Marleson ballet."
Since the check-gateway only checks the availability of the gateway, this categorically does not suit us.
Our task is to determine whether the channel is live on the Internet through each provider and depending on livestock enable or disable routes.
In this case, we have two networks
office1 ISP1-> ISP2-> ISP3
office2 ISP2-> ISP1-ISP3
As you can see, in any case, the final result will be ISP3, naturally, we don’t need to check the ISP3 channel.
And so first we need to set the date and time on MikroTik. I hope you do it without my help.
We will use the MikroTik functionality. NetWatch
Let's create two rules.
Netwacth works as a trigger.
If the state has changed, the script specified in the current trigger value is executed.
In our case, if ping until 8.8.8.8 does not pass, the status changes to down and the ISP1-DOWN script is executed, as soon as the value becomes up, then the ISP1-UP script is executed.
We will write scripts for our events.
ISP1-UP
In my case, I'm looking for someone who determines by the comments on the routes.
But so far I have only met once where a distance greater than 10 was actually used.
ISP1-DOWN
In order for our entire netwatch to work fully, we need to add two routes that will send traffic to 8.8.8.8 through ISP1, and traffic to 8.8.4.4 through ISP2
Actually everything.
Those who are interested please ask for cat.
And so it is given:
1 port - Provider 1
2 port - Provider 2
3 port - Provider 3 (backup)
4 port - Network 1 192.168.101.0
5 port - Network 2 192.168.102.0
Question:
- On port 4, the network, with its DHCP server on MikroTik, should go to the Internet through provider 1.
- On port 5 there is also a separate network with its DHCP server and they should go to the Internet through provider 2.
- 3 provider turns out to be backup, if 1 or 2 fails, MikroTik should switch the Internet to it, and then return everything to its place when the channel is restored.
From here it’s a little unclear what to do if the first provider fails, drive traffic from 4 ports to the second provider or immediately to the third.
Suppose that the third provider considers traffic for us and therefore we will have the latest one.
And so here are our interfaces.

Further, our IP addresses.

And finally, our routing table.
Explanations are needed here. For each provider we created a default route with a route marking.
I need the first route in order to configure MikroTik itself.

That's all. Our MikroTik is ready for further fine-tuning.
In the next step, we will configure the responsiveness of MikroTik from all providers.
First, let's set up a masquerade for all three interfaces.
[admin@kirilka] /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade comment="ISP 1"
[admin@kirilka] /ip firewall nat add chain=srcnat out-interface=ether2 action=masquerade comment="ISP 2"
[admin@kirilka] /ip firewall nat add chain=srcnat out-interface=ether3 action=masquerade comment="ISP 3"
Now, probably the most interesting Mangle
Our task is to make it possible to reach MikroTik through all three providers.
To do this, we must catch incoming connections and mark connections, the next rule is for a marked connection to make a return to the provider from which the connection came.
[admin@kirilka] /ip firewall mangle> print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=input action=mark-connection new-connection-mark=ISP 1 -> Input passthrough=no dst-address=172.25.25.247 in-interface=ether1
1 chain=output action=mark-routing new-routing-mark=ISP 1 passthrough=no connection-mark=ISP 1 -> Input
2 chain=input action=mark-connection new-connection-mark=ISP 2 -> Input passthrough=no dst-address=192.168.99.2 in-interface=ether2
3 chain=output action=mark-routing new-routing-mark=ISP 2 passthrough=no connection-mark=ISP 2 -> Input
4 chain=input action=mark-connection new-connection-mark=ISP 3 -> Input passthrough=no dst-address=192.168.100.2 in-interface=ether3
5 chain=output action=mark-routing new-routing-mark=ISP 3 passthrough=no connection-mark=ISP 3 -> Input
I’ll try to decrypt humanly
Rule 0
If the packet that came to the first interface (ISP 1) has the IP address 172.25.25.247 (ISP 1) in the destination address, then mark the connection with the name (ISP 1 -> Input)
Rule 1
If the outgoing packet belongs to the connection with marked (ISP 1 -> Input), then we use the ISP 1 route for it.
Thus, the router knows that if it (ping or any incoming traffic) is from ISP 1, it will return the answer through ISP 1 provider
. And understanding.

Well, now we can access MikroTik through any provider.
It is time for each office to deal with traffic from the fourth port. But first, we will prudently prepare one small but subtle nuance, since we will use prerouting then the traffic before the “Hit” in the routing table must be filtered.
It is necessary to create address sheets with networks that should not be marked.
I usually call it LocalNet and this time do the same.
[admin@kirilka] /ip firewall address-list> print
Flags: X - disabled, D - dynamic
# LIST ADDRESS
0 LocalNet 192.168.101.0/24
1 LocalNet 192.168.102.0/24
And so we created the sheets of local networks, now we will proceed with the routing of traffic.
6 chain=prerouting action=mark-routing new-routing-mark=office 1 passthrough=no src-address=192.168.101.0/24
dst-address-list=!LocalNet
Before the packet leaves the router: if the sender address is on the network 192.168.101.0/24 and the destination address is not listed, then we mark the route with the name office 1
Quite simply, this is all traffic that belongs to office 1 and does not go to our other local subnets .
Next, we need to create three routes for office traffic 1
dst-address=0.0.0.0/0 gateway=172.25.25.1 check-gateway=arp distance=10 routing-mark=office 1
dst-address=0.0.0.0/0 gateway=192.168.99.1 check-gateway=arp distance=11 routing-mark=office 1
dst-address=0.0.0.0/0 gateway=192.168.100.1 check-gateway=arp distance=12 routing-mark=office 1
A little clarification check-gateway is a procedure for automatically checking the availability of a gateway, since I have this L2 connection, in my case arp is better than ping, if you have L3 (pptp etc) then put ping.
It is also necessary to pay attention to the distance, it’s just on it that the router determines with the same destination address what priority routes are.
Well, now the final part of our "Marleson ballet."
Since the check-gateway only checks the availability of the gateway, this categorically does not suit us.
Our task is to determine whether the channel is live on the Internet through each provider and depending on livestock enable or disable routes.
In this case, we have two networks
office1 ISP1-> ISP2-> ISP3
office2 ISP2-> ISP1-ISP3
As you can see, in any case, the final result will be ISP3, naturally, we don’t need to check the ISP3 channel.
And so first we need to set the date and time on MikroTik. I hope you do it without my help.
Digression: There are many different scripts on the Internet, but most of them execute the script in a given period of time that changes the distance values in the routes. This option does not suit us, since MikroTik has NAND memory and it has its own recording limit. We will save it. Of course, it was possible to edit the script and do a check, but this is not our method. )
We will use the MikroTik functionality. NetWatch
Let's create two rules.
[admin@kirilka] /tool netwatch> print detail
Flags: X - disabled
0 host=8.8.8.8 timeout=1s interval=1m status=up up-script=ISP1-UP down-script=ISP1-DOWN
1 host=8.8.4.4 timeout=1s interval=1m status=up up-script=ISP2-UP down-script=ISP2-DOWN
Netwacth works as a trigger.
If the state has changed, the script specified in the current trigger value is executed.
In our case, if ping until 8.8.8.8 does not pass, the status changes to down and the ISP1-DOWN script is executed, as soon as the value becomes up, then the ISP1-UP script is executed.
We will write scripts for our events.
ISP1-UP
/ip route enable [find dst-address=0.0.0.0/0 and gateway=172.25.25.1 and distance >= 10];
In my case, I'm looking for someone who determines by the comments on the routes.
But so far I have only met once where a distance greater than 10 was actually used.
ISP1-DOWN
/ip route disable [find dst-address=0.0.0.0/0 and gateway=172.25.25.1 and distance >= 10];
In order for our entire netwatch to work fully, we need to add two routes that will send traffic to 8.8.8.8 through ISP1, and traffic to 8.8.4.4 through ISP2
[admin@kirilka] > ip route add dst-address=8.8.8.8 gateway=172.25.25.1
[admin@kirilka] > ip route add dst-address=8.8.4.4 gateway=192.168.99.1
Actually everything.
Leftovers
Mangle:
Route:
Script:
[admin@kirilka] > ip firewall mangle print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=input action=mark-connection new-connection-mark=ISP 1 -> Input passthrough=no dst-address=172.25.25.247
in-interface=ether1
1 chain=output action=mark-routing new-routing-mark=ISP 1 passthrough=no connection-mark=ISP 1 -> Input
2 chain=input action=mark-connection new-connection-mark=ISP 2 -> Input passthrough=no dst-address=192.168.99.2
in-interface=ether2
3 chain=output action=mark-routing new-routing-mark=ISP 2 passthrough=no connection-mark=ISP 2 -> Input
4 chain=input action=mark-connection new-connection-mark=ISP 3 -> Input passthrough=no dst-address=192.168.100.2
in-interface=ether3
5 chain=output action=mark-routing new-routing-mark=ISP 3 passthrough=no connection-mark=ISP 3 -> Input
6 chain=prerouting action=mark-routing new-routing-mark=office 1 passthrough=no src-address=192.168.101.0/24
dst-address-list=!LocalNet
7 chain=prerouting action=mark-routing new-routing-mark=office 2 passthrough=no src-address=192.168.102.0/24
dst-address-list=!LocalNet
Route:
[admin@kirilka] > ip route print detail
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme,
B - blackhole, U - unreachable, P - prohibit
0 A S dst-address=0.0.0.0/0 gateway=172.25.25.1 gateway-status=172.25.25.1 reachable via ether1 distance=1 scope=30
target-scope=10 routing-mark=ISP 1
1 A S dst-address=0.0.0.0/0 gateway=192.168.99.1 gateway-status=192.168.99.1 reachable via ether2 distance=1 scope=30
target-scope=10 routing-mark=ISP 2
2 A S dst-address=0.0.0.0/0 gateway=192.168.100.1 gateway-status=192.168.100.1 reachable via ether3 distance=1 scope=3>
target-scope=10 routing-mark=ISP 3
3 A S dst-address=0.0.0.0/0 gateway=172.25.25.1 gateway-status=172.25.25.1 reachable via ether1 check-gateway=arp
distance=10 scope=30 target-scope=10 routing-mark=office 1
4 S dst-address=0.0.0.0/0 gateway=192.168.99.1 gateway-status=192.168.99.1 reachable via ether2 check-gateway=arp
distance=11 scope=30 target-scope=10 routing-mark=office 1
5 S dst-address=0.0.0.0/0 gateway=192.168.100.1 gateway-status=192.168.100.1 reachable via ether3 check-gateway=arp
distance=12 scope=30 target-scope=10 routing-mark=office 1
6 A S dst-address=0.0.0.0/0 gateway=192.168.99.1 gateway-status=192.168.99.1 reachable via ether2 check-gateway=arp
distance=10 scope=30 target-scope=10 routing-mark=office 2
7 S dst-address=0.0.0.0/0 gateway=172.25.25.1 gateway-status=172.25.25.1 reachable via ether1 check-gateway=arp
distance=11 scope=30 target-scope=10 routing-mark=office 2
8 S dst-address=0.0.0.0/0 gateway=192.168.100.1 gateway-status=192.168.100.1 reachable via ether3 check-gateway=arp
distance=12 scope=30 target-scope=10 routing-mark=office 2
9 A S dst-address=0.0.0.0/0 gateway=172.25.25.1 gateway-status=172.25.25.1 reachable via ether1 distance=1 scope=30
target-scope=10
10 A S ;;; Netwatch ->ISP2
dst-address=8.8.4.4/32 gateway=192.168.99.1 gateway-status=192.168.99.1 reachable via ether2 distance=1
scope=30 target-scope=10
11 A S ;;; Netwatch ->ISP1
dst-address=8.8.8.8/32 gateway=172.25.25.1 gateway-status=172.25.25.1 reachable via ether1 distance=1 scope=30
target-scope=10
12 ADC dst-address=172.25.25.0/24 pref-src=172.25.25.247 gateway=ether1 gateway-status=ether1 reachable distance=0
scope=10
13 ADC dst-address=192.168.99.0/24 pref-src=192.168.99.2 gateway=ether2 gateway-status=ether2 reachable distance=0
scope=10
14 ADC dst-address=192.168.100.0/24 pref-src=192.168.100.2 gateway=ether3 gateway-status=ether3 reachable distance=0
scope=10
15 ADC dst-address=192.168.101.0/24 pref-src=192.168.101.1 gateway=ether4 gateway-status=ether4 reachable distance=0
scope=10
16 ADC dst-address=192.168.102.0/24 pref-src=192.168.102.1 gateway=ether5 gateway-status=ether5 reachable distance=0
scope=10
Script:
[admin@kirilka] /system script> print
Flags: I - invalid
0 name="ISP1-UP" owner="admin" policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api
last-started=jul/11/2013 05:07:34 run-count=9
source=/ip route enable [find dst-address=0.0.0.0/0 and gateway=172.25.25.1 and distance >= 10];
1 name="ISP1-DOWN" owner="admin" policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api
last-started=jul/11/2013 04:47:03 run-count=2
source=/ip route disable [find dst-address=0.0.0.0/0 and gateway=172.25.25.1 and distance >= 10];
2 name="ISP2-UP" owner="admin" policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api
last-started=jul/11/2013 05:08:01 run-count=1
source=/ip route enable [find dst-address=0.0.0.0/0 and gateway=192.168.99.1 and distance >= 10];
3 name="ISP2-DOWN" owner="admin" policy=ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api
last-started=jul/11/2013 05:07:36 run-count=1
source=/ip route disable [find dst-address=0.0.0.0/0 and gateway=192.168.99.1 and distance >= 10];
