RiSCiSO - another group of sceners who came under the blow of the FBI

On June 29, 2005 during Operation Site Down , among others, a broad-based scene group RiSCiSO was attacked, working with almost all types of warez: programs, games and films. Of the participants in the group, 19 people were arrested.
The group leader, 27-year-old Australian Sean O'Toole, was due to appear in Chicago on February 22, 2006. At the request of the FBI, his home in Perth, Australia, where he lived with his parents, was searched and numerous equipment seized. He was threatened with up to 5 years in prison, a fine of 250 thousand and a claim for damages of one million dollars. However, on the appointed day he did not appear in court, and, despite the international wanted list, was never found .
In the indictment, which is still available today on the website of the US Department of Justice, you can read more about the identities of the suspects (most of them were IT specialists), their roles in the group, the top sites they used, and even how they were discovered.
At the very beginning of the document is a list of the accused, indicating their place of work and role in the group. People from different small cities throughout America, and not only, aged 22 to 57 years (average age 34 years), some have very interesting posts.
full accused list
Sean Patrick O'Toole, 26 years old, known as “chucky” from Perth, Australia, was the leader of the group, led all activities, provided access to servers, uploaded pirated content from remote servers that he personally controlled.
Vahid Pazirandeh, 25, known as “vman,” from San Diego, California, worked at a university in the technical field. He was a site manager, responsible for the installation, maintenance, and support of many of the group's servers. Also provided equipment.
Linda Waldron, 57, known as “bajantara”, from the island of Barbados, works as a broadcaster for a television and radio company. Helped the leader interact with other members of the group, and recruit new members.
Jeremiah Stevens, 27, known as “^ mort ^”, from Jasper, Indiana, works for a software company developing the US Navy.
Paul Yau, 32, known as “ann,” lives in Houston, Texas, and works as a system administrator for an Internet service provider. He was a siteer.
Sandy Fury, 39, known as “asylum,” based in West Hollywood, California, works in computer security.
Marc Bartel, 33, known as “biosprint”, is from Overland Park, Kansas, an IT manager for a law firm. Saytop.
Tu Nguyen, 29, known as “dray,” from Chicago, Illinois, software consultant, Ph.D., working on a doctorate.
Richard Balter, 46, known as “ducky”, from Middle Island, NY. Received equipment from other members of the group for use in the servers of the group.
Danny Lee, 31, known as “messy”, from Rosemead, California, is a free web developer.
Peter Andrew Holland, 22, known as “thebinary,” is a college student from Middletown, Ohio. Was recently admitted to the group.
Jason Dobyns, 26, known as “supafly” from Tustin, California, works as a system administrator for an Internet service provider. Provided space on the servers of his employer to distribute pirated content.
David Lewis, 33, known as “keymaster”, from Costa Mesa, California, is an IT administrator for an architecture firm. He was a tester of the group, checked the operability of pirated programs before they were posted on the server. He gave his password to the accused Matthew Cittell, who also went to the server under the nickname “keymaster”.
Matthew Cittell, 27, from Costa Mesa, California, is a tech support specialist for a marketing company.
Matthew Ploessel, 24, known as “kkits” and “stikk”, from Seattle, Washington, is the owner of a computer security consulting firm. He was a siteer.
Joseph Toland, 44, known as “anim8,” is from Rochester Hills, Michigan, an IT director for a telecommunications company. Provided the group with pirated software.
Fred Amaya, 41, known as “audiovox,” from Chino Hills, California, is a data entry operator at the county government office. He was a siteer, also provided equipment for servers.
Lance Warner, 29, known as “transform," from Portola Hills, California, works in the IT department of the largest US company.
Gregg Piecyhna, 51 years old, from New York. He was a longtime member of the group, and had high-level access to all the servers of the group.
Vahid Pazirandeh, 25, known as “vman,” from San Diego, California, worked at a university in the technical field. He was a site manager, responsible for the installation, maintenance, and support of many of the group's servers. Also provided equipment.
Linda Waldron, 57, known as “bajantara”, from the island of Barbados, works as a broadcaster for a television and radio company. Helped the leader interact with other members of the group, and recruit new members.
Jeremiah Stevens, 27, known as “^ mort ^”, from Jasper, Indiana, works for a software company developing the US Navy.
Paul Yau, 32, known as “ann,” lives in Houston, Texas, and works as a system administrator for an Internet service provider. He was a siteer.
Sandy Fury, 39, known as “asylum,” based in West Hollywood, California, works in computer security.
Marc Bartel, 33, known as “biosprint”, is from Overland Park, Kansas, an IT manager for a law firm. Saytop.
Tu Nguyen, 29, known as “dray,” from Chicago, Illinois, software consultant, Ph.D., working on a doctorate.
Richard Balter, 46, known as “ducky”, from Middle Island, NY. Received equipment from other members of the group for use in the servers of the group.
Danny Lee, 31, known as “messy”, from Rosemead, California, is a free web developer.
Peter Andrew Holland, 22, known as “thebinary,” is a college student from Middletown, Ohio. Was recently admitted to the group.
Jason Dobyns, 26, known as “supafly” from Tustin, California, works as a system administrator for an Internet service provider. Provided space on the servers of his employer to distribute pirated content.
David Lewis, 33, known as “keymaster”, from Costa Mesa, California, is an IT administrator for an architecture firm. He was a tester of the group, checked the operability of pirated programs before they were posted on the server. He gave his password to the accused Matthew Cittell, who also went to the server under the nickname “keymaster”.
Matthew Cittell, 27, from Costa Mesa, California, is a tech support specialist for a marketing company.
Matthew Ploessel, 24, known as “kkits” and “stikk”, from Seattle, Washington, is the owner of a computer security consulting firm. He was a siteer.
Joseph Toland, 44, known as “anim8,” is from Rochester Hills, Michigan, an IT director for a telecommunications company. Provided the group with pirated software.
Fred Amaya, 41, known as “audiovox,” from Chino Hills, California, is a data entry operator at the county government office. He was a siteer, also provided equipment for servers.
Lance Warner, 29, known as “transform," from Portola Hills, California, works in the IT department of the largest US company.
Gregg Piecyhna, 51 years old, from New York. He was a longtime member of the group, and had high-level access to all the servers of the group.
After listing the accused, the act states that
RISCISO was an underground organization, founded around 1993, that was involved in the illegal distribution of large volumes of copyrighted programs, games and films on the Internet, especially freshly released ones.
the above individuals intentionally violated copyright in order to obtain personal financial gain.
Everything was a bit wrong. Here I want to return to the past for a moment and see some historical files.

The history of the RiSCiSO began around 1993, when the BBS-ok RiSC network was established. In one of the early nfo files, you can see the phone in clear text and an invitation to join them.
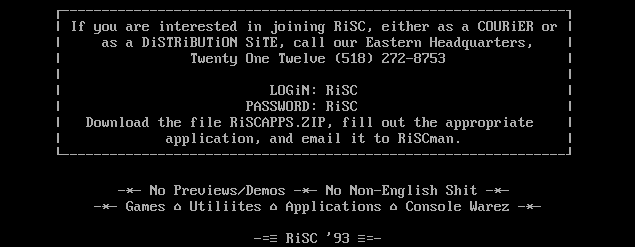
full .nfo file

A few years later, when the network expanded, all phones and some city codes were already replaced by X. In 1998, BBSs still existed, but were quickly replaced by Internet sites. It was then, in January 98th, that it was announced the formation of a unit called RiSCiSO, dealing exclusively with iso images. Those wishing to join them were invited to write to email:

full .nfo file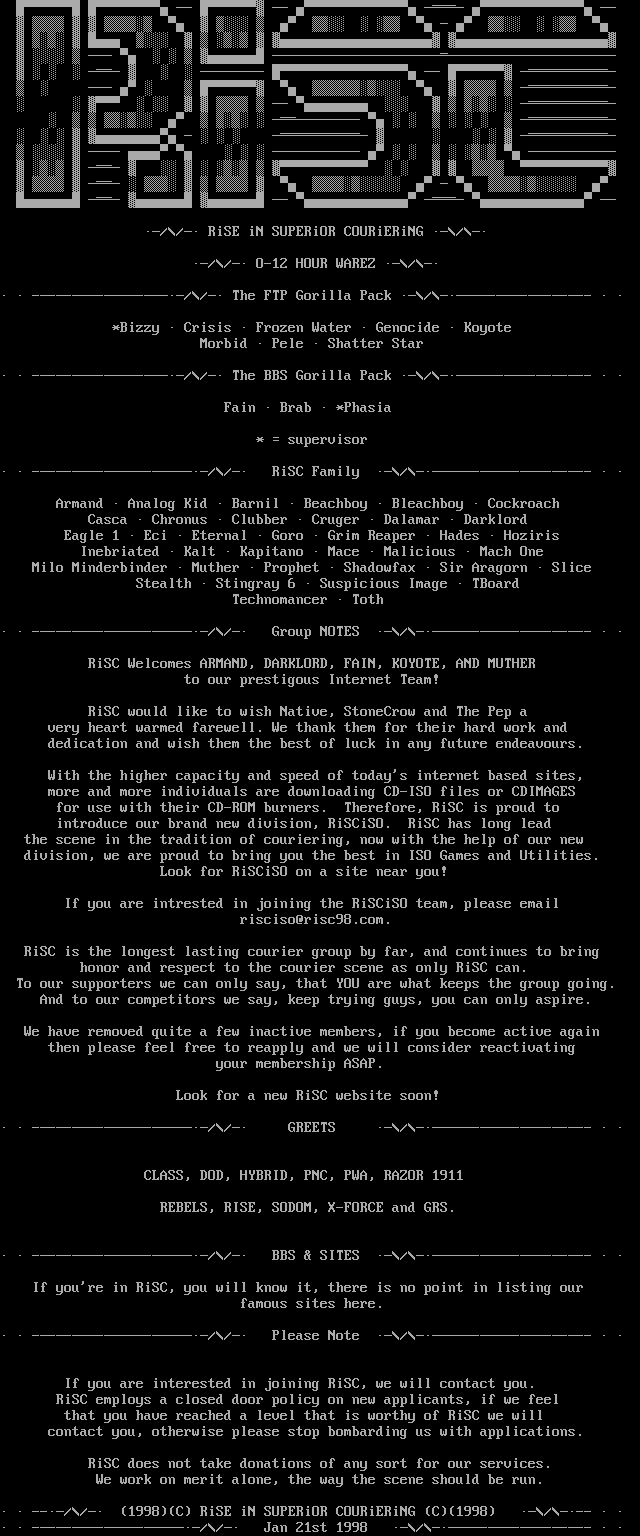

At the end of the file, you can see the copyright icons next to the name of the RiSC association and a declaration that they, like befitting scenes, do not pursue any financial benefits, and do not accept donations.
Let's go back to the official document. On the charges of criminal conspiracy, the history of the creation of the top sites that the group used was described.
Around 1998 biosprint secretly installed a server in the offices of a telecommunications company in Kansas, they called it the RM1 top-site. A few years later this server was discovered.
Around 2002 chucky, vman and stikk installed another server to replace him, also calling it RM1, in a large data center in Los Angeles. The server was part of the data center infrastructure.
In July 2003 in addition to RM1, they installed a server, originally called RM2, at the facilities of an Internet service provider in Houston, where ann worked. When the server in Los Angeles became unavailable, they used it as a replacement. We will call it Houston RM1.
Further, in December 2003. they started using a new server called RM2.
To do this, vman sent a computer and 17 hard drives to Garden City by federal express, as he said, this was the equipment originally used in Los Angeles. They installed software to prevent server discovery. However, the members of the group did not know that the computer on which RM2 was running was administered by an “informant” - a person collaborating with the investigation. The group’s leader, chucky, provided physical and remote access to the server to this person.
Around the end of 2004 Houston RM1 began to show technical problems, and in April 2005. he finally failed. As a result, the RM2 server became the group’s primary server for storing and distributing pirated material.
Apparently, to reinforce the allegations, lists for each participant are lists of programs and films downloaded or uploaded to the server. Also for this purpose, numerous descriptions of IRC chats on the group’s private channel are presented. I translated only some of them.
IRC chats
On July 25, 2004, the accused audiovox chatted on the #risciso IRC channel, where he asked for a copy of the film “The Bourne Conspiracy” to be uploaded to the RM2 server.
On July 24, 2004, the accused biosprint took part in a chat on the #risciso IRC channel, where he informed the group that he could not access the “SVCD” and “SVCD2” subdirectories on the RM2 server and asked for help to figure it out.
On August 24, 2004, the accused asylum and the leader of the chucky group on the #risciso IRC channel discussed the group’s security policy, including a more secure password system and how to make sure that new people accepted into the group do not steal content from them to organize their own warez sites.
On December 8, 2004, the group members gathered to discuss how to find new members, especially with the ability to “open” programs, as well as the adequacy of existing security measures for accessing the server. The accused ^ mort ^ stated that the RiSCiSO should be removed from the list of roles of group members so that law enforcement agencies could not find out what each of them does. He also warned that you should not write to nfo exactly who provided them with pirated programs.
On January 5, 2005, the accused anim8 asked on the IRC channel #risciso why no new programs were uploaded to the RM2 server.
On January 11, 2005, the accused vman on the #risciso IRC channel asked about software for removing data from hard drives.
On January 11, 2005, the accused bajantara on the #risciso IRC channel suggested that a request directory be created on the server, in which applicants for joining the group could upload pirated materials.
On January 27, 2005, the accused stikk on the IRC channel #risciso discussed with the accused ann and members of the RiSCiSO group “qm” and “max” how best to archive the accumulated pirated materials and how to find a new server for the group.
On May 31, 2005, the accused biosprint on the #risciso IRC channel talked with other members of the group, trying to find out which of them has rights to give him access to the new RM2 server.
On July 24, 2004, the accused biosprint took part in a chat on the #risciso IRC channel, where he informed the group that he could not access the “SVCD” and “SVCD2” subdirectories on the RM2 server and asked for help to figure it out.
On August 24, 2004, the accused asylum and the leader of the chucky group on the #risciso IRC channel discussed the group’s security policy, including a more secure password system and how to make sure that new people accepted into the group do not steal content from them to organize their own warez sites.
On December 8, 2004, the group members gathered to discuss how to find new members, especially with the ability to “open” programs, as well as the adequacy of existing security measures for accessing the server. The accused ^ mort ^ stated that the RiSCiSO should be removed from the list of roles of group members so that law enforcement agencies could not find out what each of them does. He also warned that you should not write to nfo exactly who provided them with pirated programs.
On January 5, 2005, the accused anim8 asked on the IRC channel #risciso why no new programs were uploaded to the RM2 server.
On January 11, 2005, the accused vman on the #risciso IRC channel asked about software for removing data from hard drives.
On January 11, 2005, the accused bajantara on the #risciso IRC channel suggested that a request directory be created on the server, in which applicants for joining the group could upload pirated materials.
On January 27, 2005, the accused stikk on the IRC channel #risciso discussed with the accused ann and members of the RiSCiSO group “qm” and “max” how best to archive the accumulated pirated materials and how to find a new server for the group.
On May 31, 2005, the accused biosprint on the #risciso IRC channel talked with other members of the group, trying to find out which of them has rights to give him access to the new RM2 server.
At the end is a list of confiscated equipment, a total of 172 items, computers, laptops, hard drives, all with neatly recorded serial numbers. But there are such entries:
- one ASUS CPU with a power cord
- silver computer without side cover
- Homemade CPU (no serial number)
- Toshiba PCX 1000 modem, Serial # 301456532-71, Mac # 00-00-83-33-6A-67
- multiple cell phones with chargers
- Motorola pager AR # AC111804017
- IBM Deskstar Hard Drive Bad
- Sony tape marked “Danny Backup”
- Two Xbox Machines
- Cobalt Server RAQ3 Serial # 4C03BM0036985
This concludes the indictment. What happened to these people later? The escaped Sean O'Toole was apparently never found. And since the violation of copyright in the United States is a less serious crime than in Russia, the statute of limitations, which is only 5 years, has long passed.
We could not find any information about the conviction of other participants, but such documents are carefully published in the US, so I decided that they managed to agree with the investigation and get off with fines. Adding to their age of 8 years, and google, I found that most of them still live in the same small cities throughout America, many still work in IT, and some are even registered on Github.
I don’t think that any of them would now have the urge to share their memories of the good old days, but they probably didn’t forget them. The world is small.