How do they do it? Overview of cryptocurrency anonymization technologies
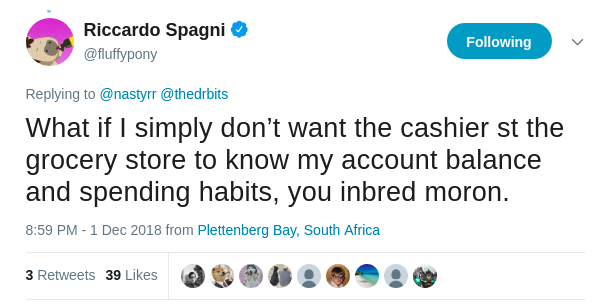
Surely you, as a user of Bitcoin, ether or any other cryptocurrency, were concerned that anyone can see how many coins you have in your wallet, to whom you transferred them and from whom you received. Around anonymous cryptocurrency walking a lot of controversy, but with something we can not agree - as the said project manager Monero Ricardo Spano (Riccardo Spagni) in his Twitter-account: "What if I just do not want the cashier in the supermarket knew how much money I have on balance and what do I spend them on? ”
In this article we will look at the technological aspect of anonymity - how they do it, and give a brief overview of the most popular methods, their pros and cons.
Today, there are about a dozen blockchains that allow anonymous transactions. At the same time, for some anonymity of transfers is obligatory, for others it is optional, some hide only recipients and recipients, others do not allow third parties to see even the amount of transfers. Almost all the technologies we consider give complete anonymity - neither the balance sheets, nor the recipients, nor the transaction history can be analyzed by an outsider. But we will begin our review with one of the pioneers in this area, in order to trace the evolution of approaches to anonymity.
The currently existing anonymization technologies can be divided into two groups: based on mixing - where the used coins are mixed with other coins from the blockchain - and technologies that use evidence based on polynomials. Next we will focus on each of these groups and consider their pros and cons.
CoinJoin does not anonymize user translations, but only complicates their tracking. But we decided to include this technology in our review, as it was one of the first attempts to increase the level of confidentiality of transactions on the Bitcoin network. This technology impresses with its simplicity and does not require changing the rules of the network, so it can be easily used in many blockchains.
It is based on a simple idea - what if users fold and make their payments in a single transaction? It turns out that if Arnold Schwarzenegger and Barack Obama threw off and made two payments to Charlie Sheen and Donald Trump in one transaction, it becomes harder to understand who financed Trump's election campaign - Arnold or Barak.
But the main advantage of CoinJoin is its main disadvantage - weak security. To date, there are already ways to identify CoinJoin transactions on the network and compare sets of inputs to output sets by comparing the amounts of spent and generated coins. An example of a tool for such an analysis is CoinJoin Sudoku .
Pros:
• Simplicity
Cons:
• Demonstrated the possibility of hacking
The first association that occurs with the words “anonymous cryptocurrency” is Monero. This coin proved its stability and privacy under the microscope of the special services:

In one of our recent articles, we very thoroughly described the Monero protocol, and today we summarize what was said.
In the Monero protocol, every output spent in a transaction is mixed with at least 11 (at the time of writing) arbitrary exits from the blockchain, thereby complicating the translation graph in the network and making the task of tracking transactions computationally complex. The entangled entrances are signed with a ring signature, which ensures that the owner of one of the mixed coins has signed, but does not make it possible to determine who is.
To hide recipients, each newly generated coin uses a one-time address, which makes it impossible for an observer (just as complex as the task of breaking encryption keys, of course) to associate any output with a public address. And since September 2017, Monero began to support the Confidential Transactions (CT) protocol with some additions, thus also hiding the amount of transfers. A little later, cryptocurrency developers replaced Borromean ring signatures (Borromean signatures) with Bulletproofs, thereby significantly reducing the size of the transaction.
Pros:
• Tested by time
• Relative simplicity
Cons:
• Proof generation and verification slower than ZK-SNARKs and ZK-STARKs
• Not resistant to cracking using quantum computers.
Mimblewimble (MW) was coined as a scalable technology to anonymize transfers on the Bitcoin network, but found its implementation as a standalone blockchain. Used in Grin and BEAM cryptocurrencies .
MW is remarkable in that it does not have public addresses, and in order to send a transaction, users exchange outputs directly, thus excluding the possibility for an outside observer to analyze transfers from the addressee to the addressee.
The rather common protocol proposed by Greg Maxwell (Greg Maxwell) in 2015 — Confidential Transactions (CT) —is used to conceal the amounts of inputs and outputs . That is, the amounts are encrypted (or rather, the scheme of obligations is used), and instead, the network operates with the so-called commitment. For a transaction to be considered valid, it is necessary that the amounts of the spent coins and the generated plus commission are equal. Since the network does not operate directly with numbers, equality is provided by the equation of these very commitment, which is called commitment to zero.
In the original CT, Borromean Signatures (Borromeo ring signatures), which took up a lot of space in the blockchain (about 6 kilobytes per output), are used to guarantee non-negativity of values (so-called range proof). In this regard, the disadvantages of anonymous currencies that use this technology, attributed the large transaction size, but now decided to abandon these signatures in favor of a more compact technology - Bulletproofs.
In the MW block itself, there is no concept of a transaction; there are only exits spent and generated in it. No transaction - no problem!
To prevent the transfer participant from deanonimizing at the stage of sending a transaction to the network, the Dandelion protocol is used , which uses a network of proxy nodes of arbitrary length that send the transaction to each other before it is actually distributed to all participants, thus confusing the trajectory of the transaction to the network.
Pros:
• Small blockchain size
• Relative simplicity
Minuses:
• Proof generation and verification slower than ZK-SNARKs and ZK-STARKs
• Support for features such as scripts and multi-signatures is difficult to implement
• Not resistant to cracking using quantum computers.
The intricate name of this technology stands for " Zero-Knowledge Succinct Non-Interactive Argument of Knowledge", which can be translated as "Compressed non-interactive evidence with zero disclosure." It became a continuation of the zerocoin protocol, which further evolved into zerocash and was first implemented in the cryptocurrency Zcash.
In general, zero-knowledge proof allows one side to prove the second truth of a certain mathematical statement without revealing any information about it. Regarding cryptocurrency, such methods are used to prove that, for example, a transaction does not produce more coins than it spends without disclosing the amounts of transfers.
ZK-SNARKs are very difficult to understand, and more than one article is required to describe the principles of its work. On the official page of Zcash, the first currency implementing this protocol, 7 articles are devoted to the description of its work . Therefore, in this chapter we limit ourselves to a superficial description.
Using algebraic polynomials, ZK-SNARKs proves that the sender of the payment owns the coins that he spends, and that the amount of coins spent does not exceed the amounts generated.
This protocol was created with the aim of reducing the size of the proof of validity of the statement and at the same time its quick verification. So, according to the presentationZuko Wilcox, CEO of Zcash, the proof size is only 200 bytes, and you can verify its correctness within 10 milliseconds. Moreover, in the latest version of Zcash, developers managed to reduce the time for generating a proof to about two seconds.
However, before using this technology, a complicated setup by the trusted setup of the “public parameters”, which is called “ The Ceremony ”, is required . The whole difficulty lies in the fact that during the installation of these parameters, none of the parties have left private keys to them, called "toxic waste", otherwise it will be able to generate new coins. How this procedure takes place can be found in the video on YouTube .
Pros:
• Small proof size
• Rapid verification
• Relatively fast proof generation
Minuses:
• Difficult procedure for setting public parameters
• Toxic waste
• Relative complexity of technology
• Not resistant to cracking using quantum computers
The authors of the last two technologies are good at playing with acronyms, and the next acronym stands for “Zero-Knowledge Scalable Transparent ARguments of Knowledge”. This method was designed to solve the ZK-SNARKs shortcomings at that time: the need for a trusted installation of public parameters, the presence of toxic waste, the instability of cryptography to cracking using quantum algorithms and insufficiently fast generation of evidence. However, the developers of the ZK-SNARK have coped with the last drawback.
ZK-STARKs also use evidence based on polynomials. The technology does not imply the use of public-key cryptography, instead relying on hashing and information transfer theory. Rejection of these cryptographic tools makes the technology resistant to quantum algorithms. But it has its price - the proof can be as high as several hundred kilobytes.
Now ZK-STARK have no implementation in any of the cryptocurrencies, but exist only in the form of the library libSTARK . However, the developers have plans for it that go far beyond the blockchains (in their White Paper, the authors give an example of proving the presence of DNA in the police database). For this purpose, StarkWare Industries was created .which at the end of 2018 raised $ 36 million investment from the largest companies in the industry.
The structure of ZK-STARK can be found in more detail in the posts of Vitalik Buterin ( part 1 , part 2 , part 3 ).
Pros:
• Resistance to hacking by quantum computers
• Relatively fast proof generation
• Relatively fast proof verification
• No toxic waste
Cons:
• Technology complexity
• Large proof size
Blockchain and the growing demand for anonymity put new demands on cryptography. Thus, the cryptography section, born in the mid-1980s — evidence with zero disclosure — was added in just a few years with new dynamically developing methods.
Thus, the flight of scientific thought made CoinJoin obsolete, and MimbleWimble - a promising newcomer with fairly fresh ideas. Monero always remains an unshakable giant to guard our privacy. And SNARKs and STARKs, although they have flaws, can become leaders in the region. It is possible that in the coming years, the points we have indicated in the “Minuses” column of each of the technologies will become irrelevant.

In this article we will look at the technological aspect of anonymity - how they do it, and give a brief overview of the most popular methods, their pros and cons.
Today, there are about a dozen blockchains that allow anonymous transactions. At the same time, for some anonymity of transfers is obligatory, for others it is optional, some hide only recipients and recipients, others do not allow third parties to see even the amount of transfers. Almost all the technologies we consider give complete anonymity - neither the balance sheets, nor the recipients, nor the transaction history can be analyzed by an outsider. But we will begin our review with one of the pioneers in this area, in order to trace the evolution of approaches to anonymity.
The currently existing anonymization technologies can be divided into two groups: based on mixing - where the used coins are mixed with other coins from the blockchain - and technologies that use evidence based on polynomials. Next we will focus on each of these groups and consider their pros and cons.
Based on kneading
Coinjoin
CoinJoin does not anonymize user translations, but only complicates their tracking. But we decided to include this technology in our review, as it was one of the first attempts to increase the level of confidentiality of transactions on the Bitcoin network. This technology impresses with its simplicity and does not require changing the rules of the network, so it can be easily used in many blockchains.
It is based on a simple idea - what if users fold and make their payments in a single transaction? It turns out that if Arnold Schwarzenegger and Barack Obama threw off and made two payments to Charlie Sheen and Donald Trump in one transaction, it becomes harder to understand who financed Trump's election campaign - Arnold or Barak.
But the main advantage of CoinJoin is its main disadvantage - weak security. To date, there are already ways to identify CoinJoin transactions on the network and compare sets of inputs to output sets by comparing the amounts of spent and generated coins. An example of a tool for such an analysis is CoinJoin Sudoku .
Pros:
• Simplicity
Cons:
• Demonstrated the possibility of hacking
Monero
The first association that occurs with the words “anonymous cryptocurrency” is Monero. This coin proved its stability and privacy under the microscope of the special services:

In one of our recent articles, we very thoroughly described the Monero protocol, and today we summarize what was said.
In the Monero protocol, every output spent in a transaction is mixed with at least 11 (at the time of writing) arbitrary exits from the blockchain, thereby complicating the translation graph in the network and making the task of tracking transactions computationally complex. The entangled entrances are signed with a ring signature, which ensures that the owner of one of the mixed coins has signed, but does not make it possible to determine who is.
To hide recipients, each newly generated coin uses a one-time address, which makes it impossible for an observer (just as complex as the task of breaking encryption keys, of course) to associate any output with a public address. And since September 2017, Monero began to support the Confidential Transactions (CT) protocol with some additions, thus also hiding the amount of transfers. A little later, cryptocurrency developers replaced Borromean ring signatures (Borromean signatures) with Bulletproofs, thereby significantly reducing the size of the transaction.
Pros:
• Tested by time
• Relative simplicity
Cons:
• Proof generation and verification slower than ZK-SNARKs and ZK-STARKs
• Not resistant to cracking using quantum computers.
Mimblewimble
Mimblewimble (MW) was coined as a scalable technology to anonymize transfers on the Bitcoin network, but found its implementation as a standalone blockchain. Used in Grin and BEAM cryptocurrencies .
MW is remarkable in that it does not have public addresses, and in order to send a transaction, users exchange outputs directly, thus excluding the possibility for an outside observer to analyze transfers from the addressee to the addressee.
The rather common protocol proposed by Greg Maxwell (Greg Maxwell) in 2015 — Confidential Transactions (CT) —is used to conceal the amounts of inputs and outputs . That is, the amounts are encrypted (or rather, the scheme of obligations is used), and instead, the network operates with the so-called commitment. For a transaction to be considered valid, it is necessary that the amounts of the spent coins and the generated plus commission are equal. Since the network does not operate directly with numbers, equality is provided by the equation of these very commitment, which is called commitment to zero.
In the original CT, Borromean Signatures (Borromeo ring signatures), which took up a lot of space in the blockchain (about 6 kilobytes per output), are used to guarantee non-negativity of values (so-called range proof). In this regard, the disadvantages of anonymous currencies that use this technology, attributed the large transaction size, but now decided to abandon these signatures in favor of a more compact technology - Bulletproofs.
In the MW block itself, there is no concept of a transaction; there are only exits spent and generated in it. No transaction - no problem!
To prevent the transfer participant from deanonimizing at the stage of sending a transaction to the network, the Dandelion protocol is used , which uses a network of proxy nodes of arbitrary length that send the transaction to each other before it is actually distributed to all participants, thus confusing the trajectory of the transaction to the network.
Pros:
• Small blockchain size
• Relative simplicity
Minuses:
• Proof generation and verification slower than ZK-SNARKs and ZK-STARKs
• Support for features such as scripts and multi-signatures is difficult to implement
• Not resistant to cracking using quantum computers.
Proofs on polynomials
ZK-SNARKs
The intricate name of this technology stands for " Zero-Knowledge Succinct Non-Interactive Argument of Knowledge", which can be translated as "Compressed non-interactive evidence with zero disclosure." It became a continuation of the zerocoin protocol, which further evolved into zerocash and was first implemented in the cryptocurrency Zcash.
In general, zero-knowledge proof allows one side to prove the second truth of a certain mathematical statement without revealing any information about it. Regarding cryptocurrency, such methods are used to prove that, for example, a transaction does not produce more coins than it spends without disclosing the amounts of transfers.
ZK-SNARKs are very difficult to understand, and more than one article is required to describe the principles of its work. On the official page of Zcash, the first currency implementing this protocol, 7 articles are devoted to the description of its work . Therefore, in this chapter we limit ourselves to a superficial description.
Using algebraic polynomials, ZK-SNARKs proves that the sender of the payment owns the coins that he spends, and that the amount of coins spent does not exceed the amounts generated.
This protocol was created with the aim of reducing the size of the proof of validity of the statement and at the same time its quick verification. So, according to the presentationZuko Wilcox, CEO of Zcash, the proof size is only 200 bytes, and you can verify its correctness within 10 milliseconds. Moreover, in the latest version of Zcash, developers managed to reduce the time for generating a proof to about two seconds.
However, before using this technology, a complicated setup by the trusted setup of the “public parameters”, which is called “ The Ceremony ”, is required . The whole difficulty lies in the fact that during the installation of these parameters, none of the parties have left private keys to them, called "toxic waste", otherwise it will be able to generate new coins. How this procedure takes place can be found in the video on YouTube .
Pros:
• Small proof size
• Rapid verification
• Relatively fast proof generation
Minuses:
• Difficult procedure for setting public parameters
• Toxic waste
• Relative complexity of technology
• Not resistant to cracking using quantum computers
ZK-STARKs
The authors of the last two technologies are good at playing with acronyms, and the next acronym stands for “Zero-Knowledge Scalable Transparent ARguments of Knowledge”. This method was designed to solve the ZK-SNARKs shortcomings at that time: the need for a trusted installation of public parameters, the presence of toxic waste, the instability of cryptography to cracking using quantum algorithms and insufficiently fast generation of evidence. However, the developers of the ZK-SNARK have coped with the last drawback.
ZK-STARKs also use evidence based on polynomials. The technology does not imply the use of public-key cryptography, instead relying on hashing and information transfer theory. Rejection of these cryptographic tools makes the technology resistant to quantum algorithms. But it has its price - the proof can be as high as several hundred kilobytes.
Now ZK-STARK have no implementation in any of the cryptocurrencies, but exist only in the form of the library libSTARK . However, the developers have plans for it that go far beyond the blockchains (in their White Paper, the authors give an example of proving the presence of DNA in the police database). For this purpose, StarkWare Industries was created .which at the end of 2018 raised $ 36 million investment from the largest companies in the industry.
The structure of ZK-STARK can be found in more detail in the posts of Vitalik Buterin ( part 1 , part 2 , part 3 ).
Pros:
• Resistance to hacking by quantum computers
• Relatively fast proof generation
• Relatively fast proof verification
• No toxic waste
Cons:
• Technology complexity
• Large proof size
Conclusion
Blockchain and the growing demand for anonymity put new demands on cryptography. Thus, the cryptography section, born in the mid-1980s — evidence with zero disclosure — was added in just a few years with new dynamically developing methods.
Thus, the flight of scientific thought made CoinJoin obsolete, and MimbleWimble - a promising newcomer with fairly fresh ideas. Monero always remains an unshakable giant to guard our privacy. And SNARKs and STARKs, although they have flaws, can become leaders in the region. It is possible that in the coming years, the points we have indicated in the “Minuses” column of each of the technologies will become irrelevant.
