Vulnerability on Habrahabr or how to steal an invite
It all started with an attempt to get an invite to the hub with white methods, but, alas, it turned out differently and the invite got in a completely dishonest way, I would like to tell the brave readers about this story.
I apologize in advance to the user who was unlucky and whose invite was used by me.
As always, I was in search of an interesting topic for an article that I would pay attention to and send an invitation to the Habr, and I got an interesting idea: “What if you find some kind of vulnerability on the Habr and write about this article?”
That's all, the goal was selected, and I proceeded to search for bottlenecks of the site:
After long attempts, I settled on the invitation download page, here after several experiments it became clear that the image should be in PNG format (because the form did not respond to other formats), I downloaded the first image that came in and saw that the ajax returned some then the ID
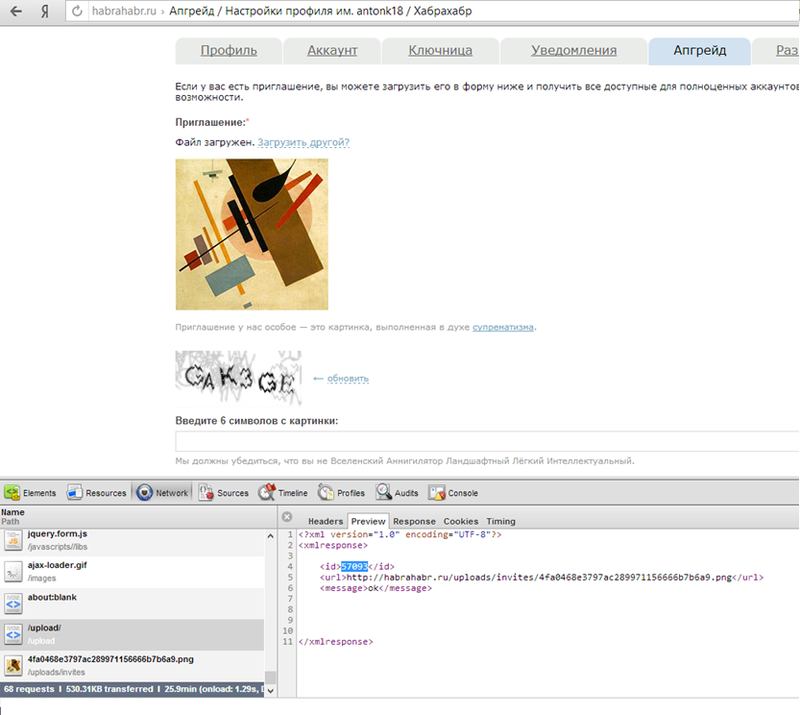
that was substituted into the hidden form field as a kind of invite_code
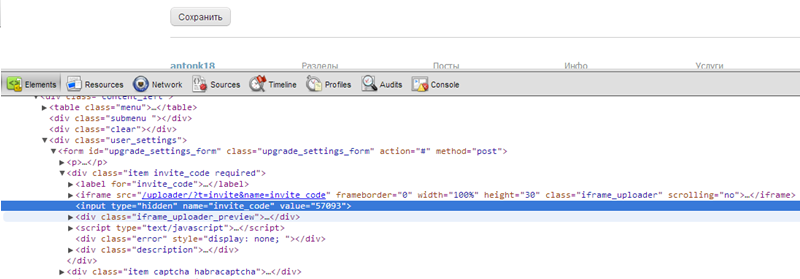
After experimenting, I realized that this is a kind of counter for downloaded files, I suggested: “what if I substitute this ID in the field, just change the value to +2 or +3”, it turned out that when I submitted the form with a false id, the system would perceive as if I uploaded an invitation to the site. Indeed, after 10 minutes of diligent input captcha I managed to intercept id invitations I've found another man, and of course before it could enter the captcha and voila !!!, issued a message that the settings are saved, then once I go to my page and I see
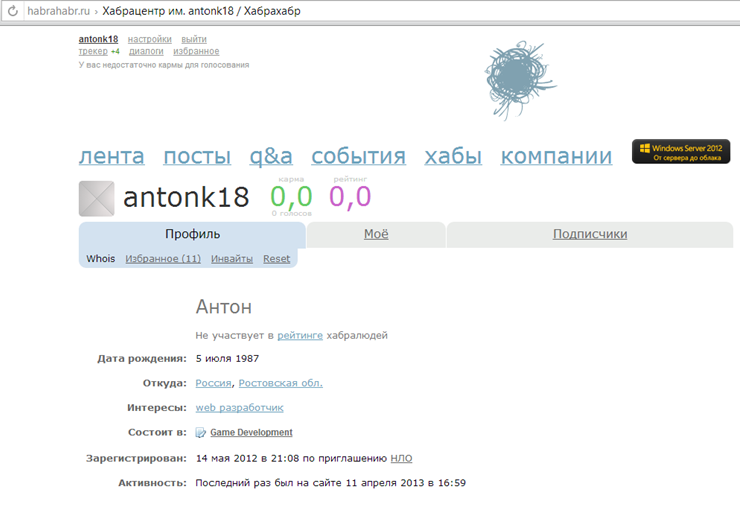
my joy knew no bounds Finally, I am a full member of the community.
I immediately unsubscribed to the support, even called the TM company by phone number, within half an hour those contacted me by mail. I explained the vulnerability in detail to a company specialist. An hour later, the vulnerability was localized, I received thanks from the company in the form of an invite, which actually stole.
Once again, I apologize to the victim.
I apologize in advance to the user who was unlucky and whose invite was used by me.
As always, I was in search of an interesting topic for an article that I would pay attention to and send an invitation to the Habr, and I got an interesting idea: “What if you find some kind of vulnerability on the Habr and write about this article?”
That's all, the goal was selected, and I proceeded to search for bottlenecks of the site:
After long attempts, I settled on the invitation download page, here after several experiments it became clear that the image should be in PNG format (because the form did not respond to other formats), I downloaded the first image that came in and saw that the ajax returned some then the ID

that was substituted into the hidden form field as a kind of invite_code

After experimenting, I realized that this is a kind of counter for downloaded files, I suggested: “what if I substitute this ID in the field, just change the value to +2 or +3”, it turned out that when I submitted the form with a false id, the system would perceive as if I uploaded an invitation to the site. Indeed, after 10 minutes of diligent input captcha I managed to intercept id invitations I've found another man, and of course before it could enter the captcha and voila !!!, issued a message that the settings are saved, then once I go to my page and I see

my joy knew no bounds Finally, I am a full member of the community.
I immediately unsubscribed to the support, even called the TM company by phone number, within half an hour those contacted me by mail. I explained the vulnerability in detail to a company specialist. An hour later, the vulnerability was localized, I received thanks from the company in the form of an invite, which actually stole.
Once again, I apologize to the victim.
