PVS-Studio as SAST solution
Until recently, in our articles we positioned PVS-Studio as a tool for detecting errors in the code. At the same time, we almost did not consider PVS-Studio in the security context. Let's try to correct this situation a bit and take a look at the tool in terms of testing application security and DevSecOps practices.
PVS-Studio is a tool for static testing of application security (Static Application Security Testing, SAST). In other words, the PVS-Studio analyzer reveals not only typos, dead code and other errors, but also potential vulnerabilities.
The tool works in the Windows, Linux, macOS environment and analyzes the code of programs in C, C ++ and C #. By the end of 2018, it is planned to support the Java language.
For the convenience of specialists who will use PVS-Studio as a SAST tool, the analyzer displays its warnings on the Common Weakness Enumeration , SEI CERT Coding Standards , and also supports the MISRA standard (currently being implemented). Diagnostic
Correspondence Tables PVS-Studio to various standards:
- CWE compliance
- SEI CERT Compliance
- MISRA support (we plan to implement until the end of 2018)
The most common classification for SAST tool alerts is Common Weakness Enumeration (CWE). Let's see, using the CWE language, how the PVS-Studio analyzer helps to prevent vulnerabilities.
If you refer to the database of well-known information security vulnerabilities ( CVE ), it turns out that often the cause of vulnerabilities in programs are not some security flaws, but ordinary software errors. The National Institute of Standards and Technology (NIST) confirms this by stating that 64% of vulnerabilities in programs are related to errors in the code.
These are the errors that could potentially lead to vulnerabilities, and are described in the CWE. Accordingly, if the error can be classified as CWE, it is likely that it can be exploited as a vulnerability and eventually add to the CVE list. For clarity, you can use the image of the funnel:
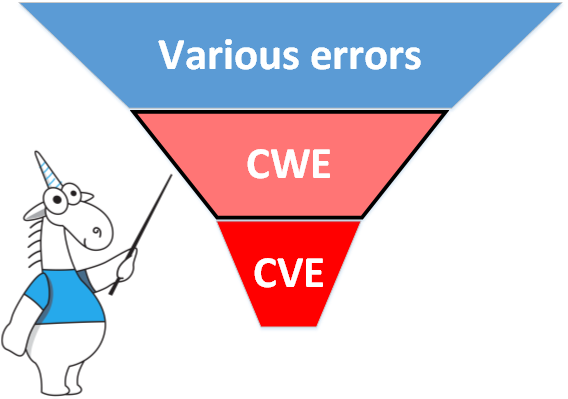
There are many mistakes. Some of these are hazardous from a safety point of view and therefore are classified according to CWE. Some CWE errors can be exploited and they are vulnerabilities.
Yes, in practice, only a very small part of the CWE errors found is dangerous and is a vulnerability. However, if you are developing security-critical applications and are concerned about user security, you should take these errors very seriously. By eliminating CWE errors, you protect your application from many vulnerabilities.
Now the relationship between bugs, PVS-Studio and vulnerabilities becomes apparent. The PVS-Studio analyzer finds errors and classifies many of them as CWE. By correcting these errors, you make your application more reliable. Finding a vulnerability in a product can seriously affect its reputation. By correcting the errors of the analyzer, you significantly reduce this risk at the earliest stage of development - writing code.
The PVS-Studio analyzer, like any other tool, does not guarantee that the code has no vulnerabilities. However, if PVS-Studio prevents, for example, 50% of potential vulnerabilities, this is already wonderful.
Additionally, we suggest reading the article " How can PVS-Studio help in finding vulnerabilities?"where errors that lead to vulnerabilities are shown and which could have been avoided when using the PVS-Studio tool in the development process.
Start using PVS-Studio as an SAST solution: download PVS-Studio .
