Attackers use the game "Clash of Clans" for money laundering from stolen credit cards

Online games are not only entertainment, but also an opportunity to earn money. Many gamers trade in “gear”, characters, pump over other people's characters for money, sell and buy in-game currencies. In general, the possibilities are really a lot. Some of the ways to earn are quite honest, others are on the verge of honesty, and still others are far beyond the limits.
German network security company Kromtech Security has found evidence that carders use stolen credit cards to purchase in-game currencies and things in mobile games like Clash of Clans, Clan Royale, and Marvel Contest of Champions. Then they resell all this already for real money with the help of various services.
“A group of intruders using complex automated systems to acquire in-game resources launders money from stolen credit cards,” the Kromtech report says.
And this is hardly something that can be done, since trading in game currencies, things, and various kinds of services is a solid source of income for many companies and individuals. For example, the company Electronic Arts has earned about $ 787 million on Star Wars: Battlefront II - this is only in-game purchases, not the sale of the game itself.
Network security experts have previously stated that in-game currencies and everything connected with them are a great way for intruders to launder “dirty” money without much risk and danger to themselves. All this has been called the "cybercriminal dream". To track such transactions, and even more so to block them is extremely difficult. Moreover, in most cases, it is also not possible to identify an attacker.
Interestingly, back in 2011, FBI representatives conducted several raids.in the student dormitories, suspecting them of being abused in World of Warcraft. Then it ended in nothing, but the epic trade with all sorts of gaming things and currency continues. The infrastructure of trading virtual goods and currencies is especially well developed in EVE Online where there is also an in-game currency and the ability to launder money.
Fraud attackers company Kromtech discovered, one might say, by chance. Employees of the company have identified the MongoDB database. She was not protected at all, and the base was opened without any problems. As it turned out, it contained more than 37 thousand records with credit card data. This database was created by cybercriminals who created automatic tools for stealing credit card numbers and entering them into the database with further use of this data to buy game currency and goods. Further, all this was sold, as mentioned above. And all this is automatic and semi-automatic, so the authors of this whole scam did not waste too much time.
So far, the creators of games where money is laundered from stolen credit cards have not commented on what happened.
And it would be worthwhile to comment, since the method described above is far from new. Now the machinations of cybercriminals were discovered only by chance - it’s not every day that hackers leave credit card data, which they obtain in various ways, completely unprotected.
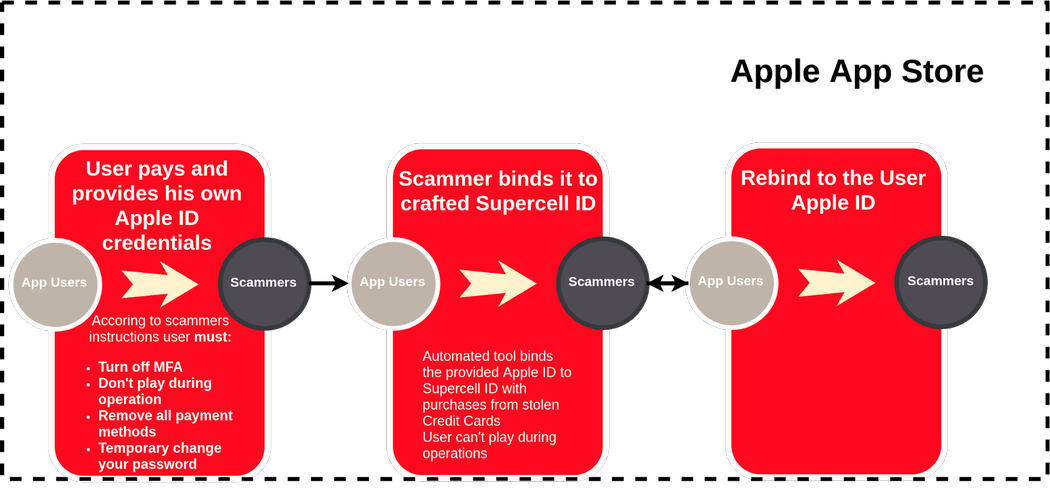
Work with game accounts is conducted with specially created Apple accounts. Such records are generated in large numbers using jailbroken iPhones of various models.
After the account is created, the validation of credit cards begins. As soon as the “good” card is found, it leaves money for the purchase of in-game currency and other resources. Then everything purchased is offered on other resources - and such ads are also generated automatically. The result is a real “washing machine” for money laundering.
Resources come true on the “gray” market g2g.com - a platform where resources of the most different games are sold and bought, from World of Warcraft to the same Clash of Clans. The cost of resources in a single ad rarely exceeds $ 90. But carders have many thousands of such accounts. According to information workers, out of 37,000 credit cards, they managed to use about 20,000.

It is not clear how much money the attackers got as a result of turning their scheme. But I managed to find out that she worked for only about a month. After its identification, the experts handed over a report to the US Department of Justice, as well as to the developers of the games themselves.
It is worth noting that cybercriminals also used Android, but the system used by Google made it difficult to automatically launder funds, so it was mainly used by the iPhone and iTunes. If you introduce more stringent security measures, then attackers will complicate the implementation of the voiced scheme.
