VPN for iPhone
Organization of a VPN server for use with iOS devices
After reading the article Warm and Tube Internet, I was worried about the problem of raising the VPN server, which can be used from iOS devices.
To use OpenVPN, you need a Jailbreak. I have not considered this option.
iOS supports L2TP, PPTP, Cisco IPSec.
Cisco IPSec works with the appropriate equipment. PPTP is sometimes cut by mobile operators. Based on this, L2TP was selected.
I already had a VQ7 server from Hetzner with Ubuntu 12.04 32 bit installed, so all the experiments were carried out on this server.
IPsec Installation
Installs OpenSwan
sudo aptitude install openswan
During installation, you will be prompted to create an x509 certificate. This is not necessary, as access will be used by keyword.
IPsec setup:
sudo nano /etc/ipsec.conf
The configuration is as follows:
version 2.0
config setup
nat_traversal=yes # Позволяет подключаться клиентам расположенным за NAT
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12
oe=off
protostack=netkey
conn L2TP-PSK-NAT
rightsubnet=vhost:%priv
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=YOUR.SERVER.IP.ADDRESS
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
Configure access to the server via IPSec:
sudo nano /etc/ipsec.secrets
The file should contain one line:
YOUR.SERVER.IP.ADDRESS %any: PSK "YourSharedSecret"
The link to the pre-shared key must be deleted , otherwise IPSec will not be able to initialize.
YOUR.SERVER.IP.ADDRESS in both files is the IP address of your server.
% any in /etc/ipsec.secrets determines which addresses can be accessed. In this case, access is allowed from all addresses.
YourSharedSecret - the key that will be used for access via IPSec.
In order for IPSec to work properly, additional settings are made:
sudo nano /root/ipsec
Content:
iptables --table nat --append POSTROUTING --jump MASQUERADE
echo 1 > /proc/sys/net/ipv4/ip_forward
for each in /proc/sys/net/ipv4/conf/*
do
echo 0 > $each/accept_redirects
echo 0 > $each/send_redirects
done
/etc/init.d/ipsec restart
The first two lines are actually used for L2TP.
We make the script executable:
sudo chmod +x /root/ipsec
Add it to rc.local
Install L2TP:
Xl2tpd is installed:
sudo aptitude install xl2tpd
Configure L2TP:
sudo nano /etc/xl2tpd/xl2tpd.conf
Content:
[global]
ipsec saref = yes
[lns default]
ip range = 10.1.2.2-10.1.2.255
local ip = 10.1.2.1
refuse chap = yes
refuse pap = yes
require authentication = yes # во время теста можно отключить, тогда все кто пройдет верификация ключом IPSec будут иметь доступ
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
Additional settings:
sudo nano /etc/ppp/options.xl2tpd
Content:
require-mschap-v2
ms-dns 8.8.8.8 # Публичный DNS Google
ms-dns 8.8.4.4 # Публичный DNS Google
asyncmap 0
auth
crtscts
lock
hide-password
modem
debug
name l2tpd # Имя сервиса, используется в настройках
proxyarp
lcp-echo-interval 30
lcp-echo-failure 4
Adding Users:
sudo nano /etc/ppp/chap-secrets
File format
# user server password ip
test l2tpd testpassword *
test - username
l2tpd - service name from /etc/ppp/options.xl2tpd
testpassword - password for the user
* - range of allowed addresses for the login of this user (format 10.254.253.128/25)
After that, restart IPSec and L2TPD should activate the whole system:
sudo /etc/init.d/ipsec restart
sudo /etc/init.d/xl2tpd restart
IPhone setup:
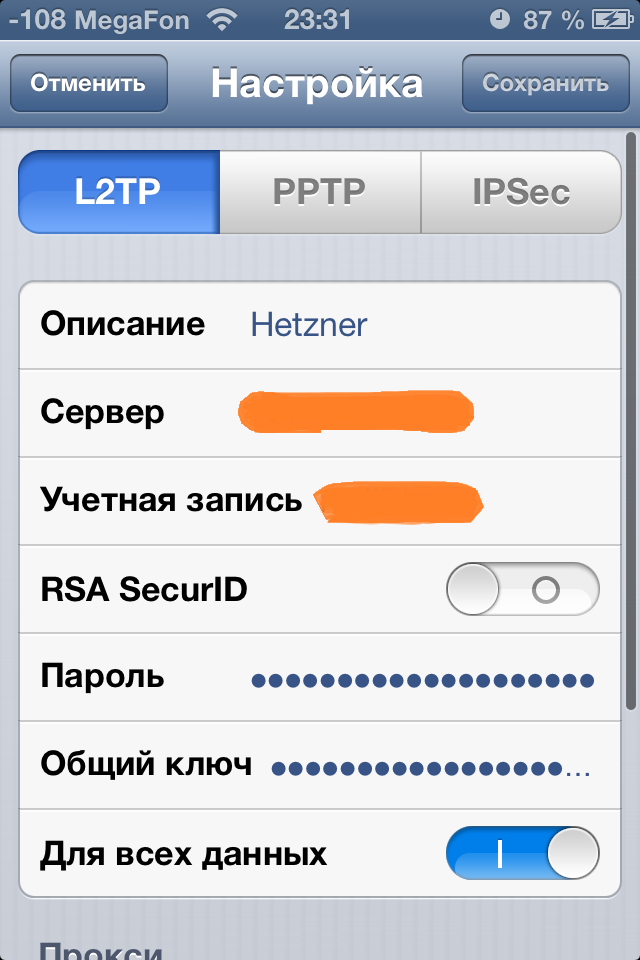
Settings> General> VPN> Add VPN Configuration.

Description - Connection name
Server - IP address of your server
The account is the user from the file / etc / ppp / chap-secrets
Password is the password from / etc / ppp / chap-secrets
The public key is YourSharedSecret from /etc/ipsec.secrets
After that in the Settings menu and in the menu Settings> General> VPN, you can enable VPN. If everything goes well, the corresponding icon will appear.


VPN will need to be turned on manually, with each use.
Setting up a connection in Windows 7
In the network and sharing control center, establishing a new network connection, creating a new connection:
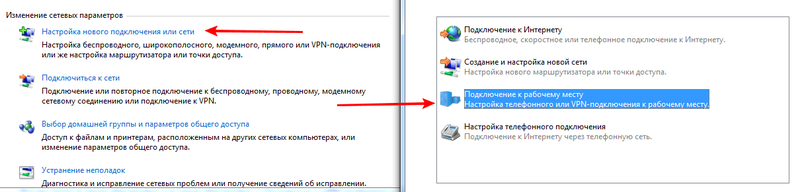
Create a new VPN connection:
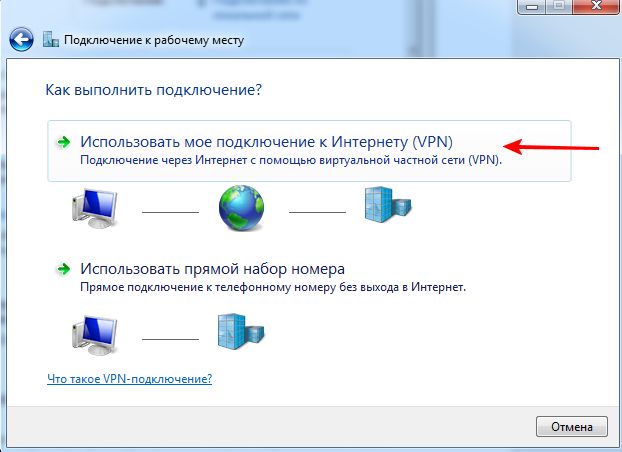
In the “Internet address” field, enter the IP of your server. Do not connect immediately.
After that, go into the properties of the new connection and in the settings indicate the use of L2TP, enter the YourSharedSecret key from /etc/ipsec.secrets

When connecting, specify the username and password from / etc / ppp / chap-secrets.
When writing the article were used materials link1 , link2
