PRTG: Monitoring System and Some Tips

There are a huge number of monitoring systems on the market, ranging from the simplest and most free to expensive solutions from well-known manufacturers such as Hewlett-Packard and Microsoft.
In this article, I will tell you about the PRTG Network Monitor from Paessler AG . I want to make a reservation right away that I am not a serious IT specialist, but I work in the field of security, although I work quite closely with the departments of IT and IT Security.
The choice of software was made by me based on a superficial analysis of manufacturers' websites.
Introduction: Why PRTG?
In June 2011, I was given a fairly simple task - it was necessary to monitor the work of computers of security officers and employees of my department in all offices of the organization in the following areas:
• Is the computer turned on?
• Have you logged into at least one domain account on your computer?
• Is a corporate antivirus installed on the PC?
• Are anti-virus databases updated?
And it was necessary to automate the release of reports from the monitoring system, in order to provide management on a weekly basis.
It was necessary to do this independently without the intervention of IT employees and without resorting to their help.
I did not have any experience in monitoring at that time and I had to analyze for several days what Google and Yandex offered me. In the search results, I found PRTG, which was offered absolutely free, but with a limited number of sensors that can be installed.
This option was quite fine with me, because if necessary, there was money to buy a commercial version. I realized that 10 sensors would not be enough for me even to demonstrate the capabilities of the system to management, and I bought the cheapest paid version (the price list below is presented in June 2011 - now the prices are higher), which includes 100 sensors:









It’s after that and My acquaintance with the system began.
General system functionality
The system over the past almost a year and a half of my acquaintance with her has improved significantly (builds are released stably once a month, and sometimes more often). I will try to describe its capabilities in as much detail as possible, as well as talk about some interesting things that I learned to do in this software.
(Fig. 1 - Login Screen)
In this case, the login to the system through the Web-interface is shown. If you’re not used to using a browser to work with the system, you can use applications for your mobile devices (only for Android so far) or install Enterprise Console on your PC, which almost 100% repeats the interface via the Web.
As I have already shown in the screenshot above, the system supports authorization for domain accounts, but you can create KMs manually, if you have such a desire.
Immediately after logging in, you will be taken to the welcome screen:

(Fig. 2 - Welcome screen)
If this is your first login, after installation, I recommend that you click on the Run Configuration Guru link , which will help you configure most of the initial configs immediately:
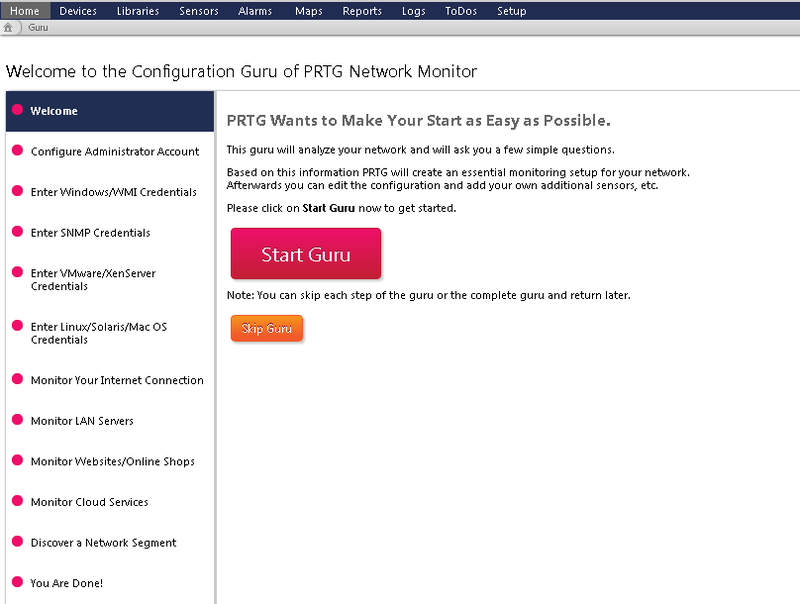
(Fig. 3 - Configuration Guru)
This is where you configure:
• Username and password of your root administrator account (core admin)
• Data for use with WMI sensors (usually an account with administrator privileges in the domain)
• If you use UNIX or LINUX systems, you you can also register yes data of your ultrasound.
• Data for connecting to the Internet (for example, if your organization uses a proxy server) - access to the Internet is useful at least in that you can activate the system without sending codes to paessler’s mail, but directly, but of course With a stable Internet connection, the system itself will be able to download and install updates.
• You will find a PC, server and other peripheral equipment in automatic mode (if the network or network segment is small and several hundred machines will not be searched).
After the basic setup, you will be taken to a page where all your devices and sensors are displayed:

(Fig. 4 - Device main page)
Indicators of different colors mean the following:
Red- error \ unavailable \ excess of the specified parameter \ deficiency to the specified parameter
Orange - atypical behavior of the sensor (Example: Ping at the moment 200 ms, with an average ping on this device at this time of the day / week 110 ms)
Yellow - warning (the sensor is approaching critical to the boundaries of the given parameter or became unavailable at the time of the last check)
Green - normal behavior of the sensor
Blue- pause (set either manually or automatically). Both the administrator and the system can pause the sensor for several reasons: the main sensor for the device is unavailable and all other device sensors are set to pause mode; too many requests at the same time - the sensor will be restarted after receiving data from other sensors.
Gray - no data was received from the sensor (they just turned it on, only the pause mode ended)
Hint:As I wrote above, the pause mode can be set automatically. In my installation of the system, the following logic is written in each device - if the ping sensor (the main one on each device) is unavailable, then all other sensors on the device automatically go into pause mode so as not to send requests in vain (anyway, the device is most likely unavailable).
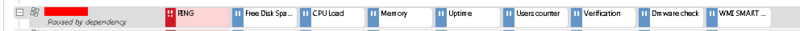
(Fig. 5 - Device behavior when the main sensor is paused)
Next, we will consider a typical solution (created as a template) that I use for newly added computers:
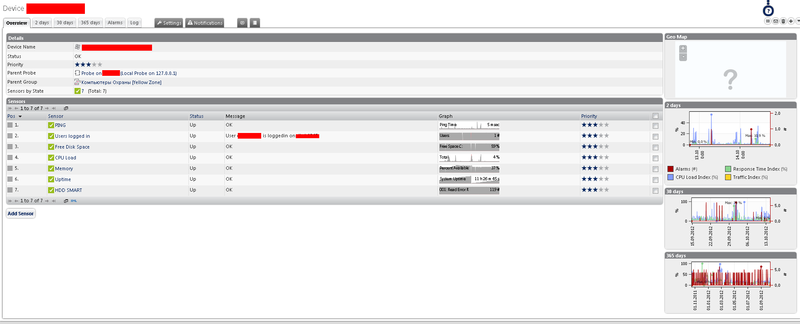
(Fig. 6 - Typical PC)
Ping - standard ping to the machine. The main sensor on the device.
Users logged in - who is logged in on this particular machine.
Free disk space-% free hard disk space.
CPU Load -% CPU utilization (s).
Memory -% memory usage.
Uptime - the time since the last reboot of the PC. A manual warning has been set - over 14 days - to notify the administrator.
HDD Smart - checks several parameters of reading / writing to the hard disk.
If we talk about the presentation of devices, then there are 2 options:
1.) The option of grouping sensors inside the devices already presented above.
2.) Map mode - you yourself draw / simulate a map of the location of your devices for more convenient visual perception.
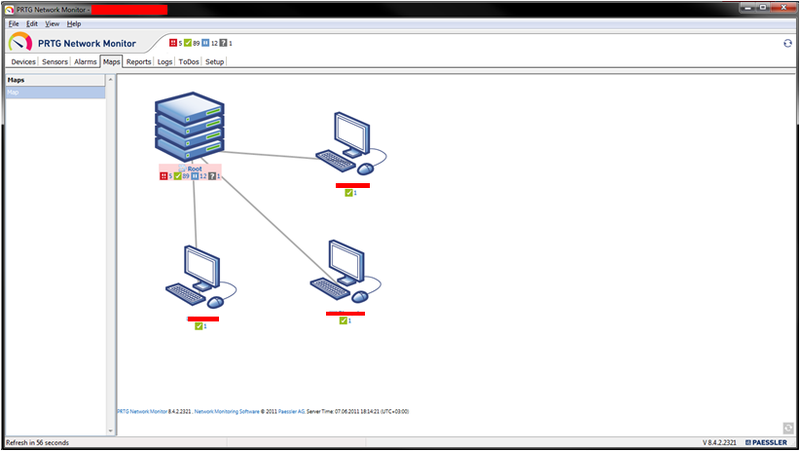
(Fig. 7 - Map)
With this I will finish showing the basic functionality of the system, and we will move on to what sensors can be configured in the system and what interesting solutions I have already managed to design.
A bit about sensors
Currently, the system has over 130 different sensors available. You can read more about each of them on the Sensor Description page .
Sensors fall into the following conditional categories:
• Common Sensors
• Bandwidth Monitoring Sensors
• Web Servers (HTTP) Sensors
• SNMP Sensors
• Windows / WMI Sensors
• Linux / Unix / OS X Sensors
• Virtual Servers Sensors
• Mail Servers Sensors
• SQL Database Servers Sensors
• File Servers Sensors
• Various Servers Sensors
• VoIP and QoS Sensors
• Hardware Parameter Sensors
• Custom Sensors The
menu for adding sensors starting from version 11 of the software has become extremely convenient and understandable:
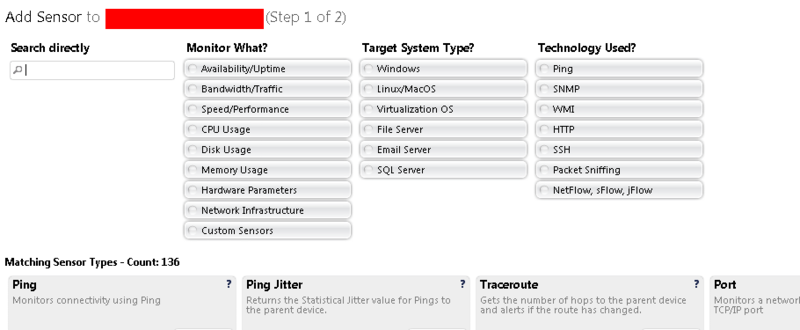
(Fig. 8 - Adding a new sensor)
You can either select a category and then select the desired sensor, or search for the sensor in the list below, or enter part of the name and select the sensor from the already sorted list.
I use less than half of the sensor types proposed by the developer, but this is enough for me to keep the servers and PCs entrusted to me under full control and to be sure that everything works properly.
It would be boring to read about the basic description of sensors, so I prefer to describe some interesting examples from my experience with the system.
Wait! Who goes?
The first successful example was the search for violators. In this particular case, we consider a violator any user who is not the "owner" of a particular PC.
To search for the intruder, we will use 2 sensors of the type Users logged in . The first sensor will show us the real picture - who is currently logged in to the machine (and whether it is logged in at all), and the second sensor will have a filter with the logins of authorized employees (i.e. these logins will not be reflected).
We set an alert on the second sensor - if the number of users is more than 0 (and we remember that the logins we need simply will not be displayed), then immediately notify the administrator by mail. You will receive the violator’s login in a letter along with the name and IP address of the machine where the employee tried to enter.
Very effective if you really need to evaluate who logged on to the PC quite quickly.
IT assistant
In our organization, 100% of remote assistance to employees is provided through DMWare. To track remote inputs on a PC, I installed a process sensor that monitors the DMWare Mini Remote Control process and as soon as the process begins to take up more than 10 MB of memory, it displays an alert with the name \ IP of the machine. Regularly, in my case, the process takes 6-7 MB, and in working condition (when someone uses remote login) about 20 MB. So far, for half a year of using this trick, there has not been a single failure / false positive.
The third useful example I have already described previously is the pause of all sensors after not receiving a response from the ping sensor.
In addition, I set up sms notifications in case any of the servers (ping server) is unavailable for more than 10 minutes. Configured on the bulksms resource. The only minus is that the names should be exclusively in Latin, otherwise in SMS you will get that your server is inaccessible ??????.
Important: If you have not found a sensor that meets your requirements, this is not a reason to abandon the system - you have the option to manually load scripts / write a sensor. This makes the system even more customized.
At the end of this chapter, I note that the touch functionality is really very rich and can perform many different actions - it's up to you. The above are just examples of how I am currently using the system and maybe inspired by these examples, you will want to see if this system is better than what you are currently using.
Reports
At the moment, 4 reports have been set in my installation for automatic generation: weekly reports on Moscow PCs and PCs in the regions, as well as their monthly counterparts.
On a manual start, reports on the availability of servers and specific processes / services on these same servers are installed.
As an example, I will show the menu of the monthly regional report:
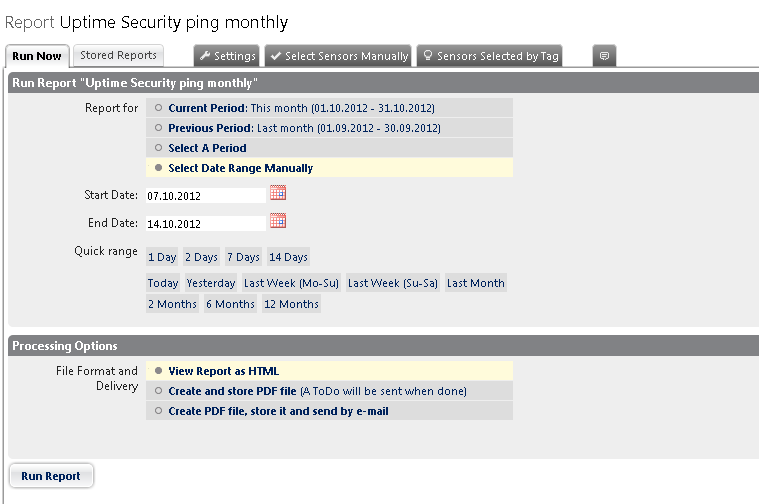
(Fig. 9 - Report)
Despite the fact that the report is set to automatic mode, you still have the option of manually starting the process.
As you can see from the screenshot, you have 3 options for issuing reports: view the report page in html online, save the report as a PDF file on the server and notify when the report is completed by mail, or send the PDF file to the end user.
On the bookmarkStored Reports you will find all the files stored on your server.
If you save the report in PDF, it will look something like this:
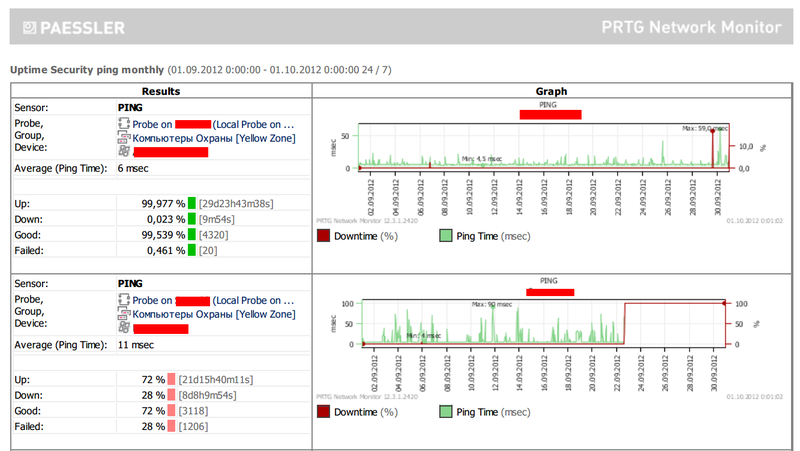
(Fig. 10 - PDF Report)
In this case, a graphical representation of the data is used. If you are interested in specifics, then you can generate reports in a textual form in a section, for example 5 minutes. Then you will receive lines instead of the picture:
01/01/2012 09:00:00 - 01/01/2012 09:05:00 Ping 100% Available
Most of the reports you just need to configure 1 time, test it with the user who will use it and forget it. The presentation format in my case really liked even those who are afraid of the computer like fire and usually resort to questions like "I entered the password incorrectly 10 times, and for some reason the computer was blocked "
Logs
The logging system in this software product certainly exists and it logs absolutely everything, starting from the behavior of sensors and ending with the formation of reporting and sending SMS messages.

(Fig. 11 - An example of a log)
For those who like to delve into the details, this tab will certainly be useful, and even more so it is visually pleasant, since the log is painted in different colors depending on the criticality and type of event.
Conclusion
At the moment, I and my employee completed 3 phases of improving the system. With each phase, we add and find for ourselves more and more functions and tricks in the settings. Back in August last year, when I installed the system purchased after the presentation to the management, I did not suspect that I could bring it to the state in which it is currently located.
The process of improving the monitoring system can last for years and still will not be brought to perfection. In this review, I tried to show the most relevant things in my opinion that I found in this software product, as well as some tricks that I currently use.
After reading this article, I hope that at least a few people will find for themselves something interesting, and perhaps very necessary in their work.
List of useful sites on the subject
• Developer site - Paessler AG
• Additional sensors, add-ons and programs for PRTG
