How to make friends Truecrypt loader and Grub 2?
Today I will tell you how to make friends the bootloader from the Truecrypt encryption program and the Nix bootloader Grub 2. Such a need may arise (and inevitably arises) when you try to install the Windows OS encrypted by the free Truecrypt program and a unix-like operating system on the same hard drive as, for example Ubuntu
The main problem is that Grub does not know how to work with truecrypt keys and cannot decrypt a Windows partition, and truecrypt loader is not [always] able to load other operating systems. There are two main approaches to solving the problem.
The first approach. Master boot record (MBR) contains Truecrypt bootloader
In principle, this option would have to work out of the box (because the Truecrypt bootloader can transfer downloads to other bootloaders on different sections of the hard drive) and not require any extra gestures from the user, but there are several pitfalls.
The problems are mainly related to the fact that during installation, Windows 7 creates for itself a small boot partition of 100 megabytes (it is necessary for encryption using BitLocker), and in this situation, the trukript refuses to install the multiboot bootloader “out of the box” when encrypting the system section ... At least this behavior is true for Truecrypt version 7.1a. Thus, you have to install the usual bootloader loader, which looks like this:

As you can see, it is possible to refuse to enter a password by pressing the Esc key. In this case, we will be offered a list of hard disk partitions to which you can transfer control for further download.
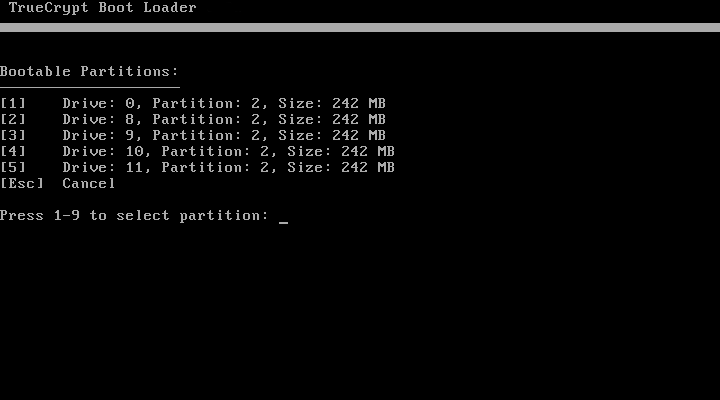
The pitfall is that the Linux / boot partition is not always present on this list. For him to appear there, several conditions must be met. The boot * nix partition must be the primary partiton, and not part of the extended (non extended patition), must have a “bootable” flag, and also have a bootloader on it, to which control can be transferred.
If everything is clear with the first two conditions, and when installing the same Ubuntu, you can immediately correctly configure the hard drive, then the latter condition may cause difficulties. The fact is that Grub version 2 does not like to be installed not in MBR, because this uses a fault-tolerant system and there is a possibility that the bootloader will “fly off” from time to time. You will see a message about this when you try to execute the command to install the bootloader on the partition. In order for everything to work out, you must use the --force switch.
sudo grub-install /dev/sda6 --force
where / dev / sda6 is the / boot partition of your Ubuntu.
Algorithm
Thus, the installation and configuration of everything can be described as follows:
- Install windows
- Install Ubuntu by creating a / boot partition for it on a separate primary partition by setting the boot flag
- Download Ubuntu and install Grub in the / boot partition (as described above)
- Reboot into windows, install Truecrypt, encrypt the system partition
Now we have the Truecrypt bootloader in the MBR.
- In order to boot into windows just enter the correct password from the system partition
- In order to load Ubuntu, press Esc to refuse to enter a password and select the / boot section
Troubleshooting
In some cases, Ubuntu may overwrite the bootloader in the MBR on Grub and you will lose the ability to boot Windows. To avoid this, you should create a backup copy of the bootloader and the keys necessary to decrypt the system disk.
Create a backup:
dd if=/dev/sda of=~/truecrypt.mbr count=1 bs=512
dd if=/dev/sda of=~/truecrypt.backup count=8 bs=32256
Restore from the backup (where / dev / sda6 is your / boot partition!) In case of failure:
sudo dd if=~/truecrypt.mbr of=/dev/sda count=1 bs=512
sudo dd if=~/truecrypt.backup of=/dev/sda count=8 bs=32256
sudo grub-install /dev/sda6 --force
The second approach. Master boot record (MBR) contains Grub 2 bootloader
But how do you transfer control to the Truecrypt bootloader from Grub 2? It would be possible to save the bootloader and keys as a file and try to transfer control to it ... It would be possible to use iso Truecrypt Recue CD if Grub 2 could load iso images like its younger brother Grub4Dos does (but it doesn’t! It can only mount the file system iso ..) I was already completely desperate in the search, but suddenly I came across a fairly simple and elegant solution.
Thanks to the wonderful people who are developing the " Grub2 loves TrueCrypt " project , it has become possible to convert the Truecrypt bootable rescue iso image into a format that Grub2 can work with.
So, install git to clone the repository with grub2tc, as well as ruby for the program to work:
sudo -i
apt-get install git ruby
git clone git://gitorious.org/grub2tc/grub2tc.git
After that, copy the image “TrueCrypt Rescue Disk.iso” to the program folder and rename it to “tcrescue.iso”. Execute the command
make
The “tcloader” file appears in the folder, which must be copied to / boot
Now it remains to edit the bootloader menu so that the Truecrypt boot point appears in it. Add to the /etc/grub.d/40_custom file :
menuentry "Windows via TrueCrypt" {
insmod multiboot
multiboot /tcloader
}
Then do:
update-grub2
grub-install /dev/sda
where / dev / sda is your hard drive
Now, another important point. The last command (when you reinstalled Grub in the MBR of the hard drive) you most likely damaged the Truecrypt keys needed to decrypt the system partition. From now on, when you try to enter a password, you will receive the message “Incorrect password”. To fix this, we will restore the keys from the backup file that we carefully created for us in our grub2tc volhead directory :
dd if=volhead of=/dev/sda bs=512 seek=62
if = volhead is the file where the backup of the keys
of = / dev / sda is stored - the device where this backup should be written sector-by-sector
bs = 512 - the block size
seek = 62 - how many blocks to backtrack from the start of the device / dev / sda (there the Grub bootloader )
Now you can boot!
Algorithm
Thus, the installation and configuration of everything for this method can be described as follows:
- Install windows
- Install Ubuntu
- Reboot into windows, install Truecrypt, encrypt the system partition
- Somehow we load Ubuntu :) (for example, from a bootable USB flash drive / disk) and do the above manipulations using the grub2tc program
Now we have the Grub2 bootloader in the MBR.
- In order to boot into Ubuntu just select this item at boot time
- In order to boot Windows, select the item “Windows via TrueCrypt” and enter the correct password
Troubleshooting
If the Truecrypt bootloader for some reason stops recognizing your password (keys are damaged), then you can always restore them from a backup in the grub2tc folder with the command:
dd if=volhead of=/dev/sda bs=512 seek=62
PS
Both methods are suitable for use with Linux encryption dm-crypt and LVM, which allows you to have both two operating systems fully encrypted :)
