EAP-SIM authentication in WLAN
The main idea of EAP-SIM authentication in WLAN (802.1X) networks is the use of authentication parameters and SIM card algorithms for user authentication and traffic encryption in WLAN networks. At the same time, the user does not have to enter a username and password, all authentication is transparent.
1) EAP-SIM authentication scheme
Legend:
EAP - Enhanced Authentication Protocol (Advanced Authentication Protocol)
SIM - Subscriber Identity Module (GSM Subscriber Identity Module)
MAC - Message Authentication Code
IMSI - International Mobile Subscriber Identifier
Nonce - Random value generated by client side
GSM triplet - RAND and Kc and SRES values calculated on the basis of this RAND according to A3 / A8 algorithms
AuC - Authentication center of GSM operator. One of the tasks is to calculate the GSM triplet.
The basic authentication scheme using EAP-SIM is given below.
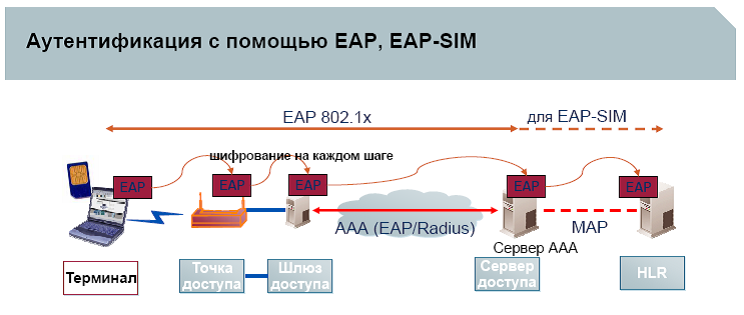
EAP-SIM authentication according to this scheme requires the following components:
- Client device (Terminal) with support for a regular GSM SIM card and corresponding software. It is possible to use a specific SIM card, in this case the security will be higher
- 802.1X compatible WLAN access point with EAP-SIM support
- Access controller / gateway with support for DHCP (Dynamic Host Configuration Protocol) and EAP-SIM protocol on the WLAN network side to highlight dynamic IP addresses for network users and interaction with AAA RADIUS server WLAN network via EAP protocol
- AAA RADIUS server used to authenticate the user of the WLAN network using EAP-SIM / AKA algorithms (in traditional WLAN networks, this is an authentication server that in the simplest case checks the entered login & password and charges the subscriber)
- SS7 gateway for the interaction of the AAA RADIUS server of the WLAN network with HLR (Home Location Register) / Authentication Center (AuC) operator. In the diagram, for simplicity, not indicated.
- HLR / AuC - home register of GSM subscribers
2) The principle of operation of EAP-SIM authentication
A timing diagram explaining the principle of EAP-SIM authentication is given below.
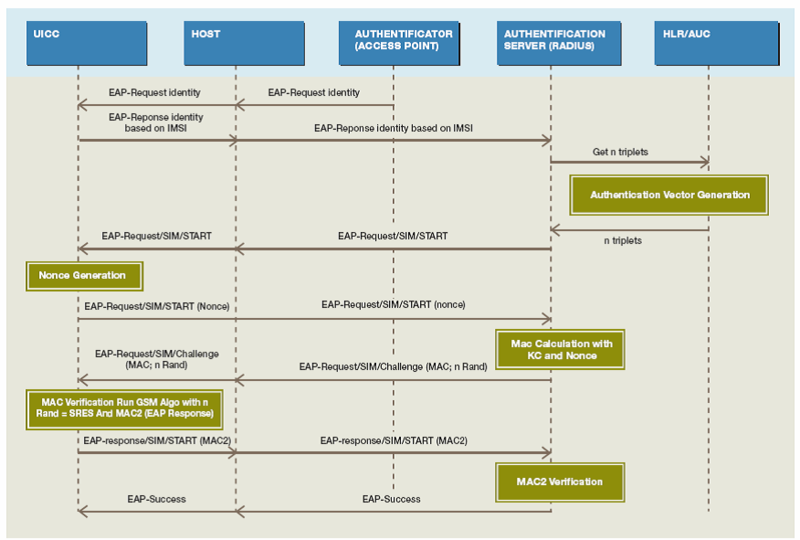
If the PIN code is entered correctly (or the request is turned off) and the subscriber has selected the appropriate WLAN network, EAP-SIM authentication starts on his terminal. During the authentication process, the following steps are performed:
a) the EAP Identity Request message is sent to the user terminal via the EAPOL protocol from the WLAN side of the access point (in the Access Point diagram)
b) the user terminal sends an MSISDN in the EAP Identity Response message (as an NAI, for example 250097000000001 @ eapsim.mobile_carrier.ru) used SIM card or pseudonym. Pseudonym (temporary identity), an analog of temporary IMSI, is designed to increase security by hiding the real IMSI.
c) The WLAN access point in the EAP SIM Start Request message informs the user terminal about the supported versions of EAP-SIM authentication, and also requests the parameters of the terminal equipment.
d) the user terminal selects one of the supported authentication algorithms, which is reported to the access point in the EAP SIM Start response message. This message also contains the value of the required number of GSM triplets per session (see clause 3.1).
e) The WLAN access point transforms the 802.1X protocols into RADIUS compatible protocols and sends the MSISDN + parameters from the EAP SIM Start response to the AAA RADIUS server. In turn, the AAA RADIUS server through the SS7 gateway (via MAP) transmits the MSISDN value of the terminal to AuC and requests standard GSM triplets (RAND, Kc, SRES).
d) two or three RAND values received from AuC and Kc & SRES values are used by the WLAN AAA RADIUS server to calculate EAP-SIM authentication keys (K_aut), EAP-SIM encryption keys (K_encr), session keys MSK & EMSK and EAP-SIM additional authentication parameters. Next, an EAP packet is generated containing: RAND values (in clear text), encrypted additional authentication parameters (AT_ENCR_DATA). Next, the EAP packet and the hash of the packet amount (value AT_MAC = SHA1 (EAP packet, NONCE_MT)) are transmitted to the terminal in the EAP SIM Challenge Request message.
e) the RAND values received by the terminal are transmitted to the SIM card for calculating, according to the A3 / A8 algorithms, the SRES and Kc values, which are then used by the terminal to decrypt the “additional authentication parameters” received in the previous step “EAP-SIM”. Further, if the decryption on the terminal side is successful and the “EAP-SIM additional authentication parameters” are correct, the terminal transmits to the network an EAP SIM Challenge Response message indicating a successful “terminal authentication” and a hash of the calculated SRES value (AT_MAC = SHA1 (SRES) ) Otherwise, the SRES hash is not sent.
d) if the WLAN AAA RADIUS server confirms receipt of a sign of successful authentication and if the hash of the SRES sum from the terminal matches the calculated one, the access point starts providing the service and the message “successful authentication server” is sent to the terminal. The provision of the service is possible using standard WPA / WPA2 (WLAN Access Protection) encryption.
The protocols used in each section are shown in the figure below.
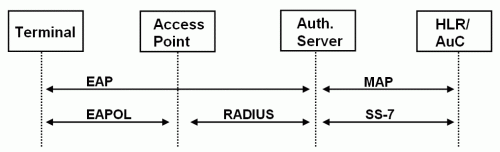
It should be noted that for EAP mode, there are two main authentication methods in WLAN networks: EAP-AKA and EAP-SIM. The first is more reliable, but requires a USIM card with Milenage support, in addition, Milenage support must be present on the side of the AuC / HLR operator. The second method indicated is less reliable, requires 2G SIM cards (COMP128v1-4) and standard 2G authentication on the side of the AuC / HLR operator. It should also be noted that authentication by EAP-SIM / AKA is mutual, and is carried out by analyzing the AT_MAC value received from the access point on the terminal side - if the parameters in AT_MAC do not match the parameters of the SIM card, then authentication is terminated and the SRES hash is not transferred to the access point .
Also, when setting up a WLAN network, you must set the user reauthentication mode when a data transfer session is interrupted. Two options are possible here:
- repeated EAP-SIM / AKA authentication
- use of client access parameters (MSISDN, MAC) stored in the AAA RADIUS server and do not re-request triplets from the side of the operator’s AuC server. The second method will reduce the load on the operator’s network, however this method is less secure in the issue of illegal access under the client’s name.
The advantage of EAP-SIM / AKA authentication is the authentication transparent for the subscriber while maintaining data confidentiality, since the Ki secret key is not transmitted to the IP network. As stated in RFC 4186, the reliability of EAP-SIM / AKA authentication is no worse than in GSM.
3) GSM network security when using EAP-SIM authentication
Due to the fact that a SIM card is involved in EAP-SIM authentication, it is necessary to carefully analyze the confidentiality of sensitive data for various EAP-SIM usage schemes. For now, let us turn to RFC 4186, from which two remarks follow:
3.1. As stated in RFC 4186: “The derived 64-bit cipher key (Kc) is not strong enough for data networks in which stronger and longer keys are required.” Kc length is not enough for reliable encryption of user data in a WLAN network. To eliminate this, an algorithm for obtaining 2-3 Kc can be applied with subsequent integration on the client side and AAA RADIUS server WLAN network. When using the algorithm of using 2-3 Ks keys, the reliability of the encryption of the data transmission channel increases.
3.2. The second question is the transfer of the SRES hash from the terminal to the AAA RADIUS server via the WLAN IP network. In the standard case, SRES is not explicitly transmitted and cannot be obtained by an attacker. However, there is a possibility of the presence of “Trojans” on the side of the terminal / PC in order to illegally obtain SRES and Kc. After receiving a sufficiently large number of triplets, it is possible to calculate the Ki key and further clone the GSM SIM card. This method allows you to receive triplets without physical access to the SIM card, which increases the risk of cloning SIM cards. It should also be noted that the algorithm for calculating the hash of the SRES sum through SHA1 is unreliable and has already been hacked (http://www.schneier.com/blog/archives/2005/02/sha1_broken.html). Thus, by listening to a Wi-Fi network, attackers can get real SRES and RAND values. Kc, however,
4) Analysis of solutions for EAP-SIM authentication
Depending on the requirements for the coverage of the terminal base and the level of security, there are three options for implementing EAP-SIM with a mobile operator.
a) Calculation of the MAC and MAC2 values inside the SIM card. Formation of EAP packets inside the SIM card.
Pluses of the solution:
- High degree of security when calculating GSM triplets
- Work on various WLAN terminals, including PCs with different operating systems, but provided that the installed third-party software will be developed. WLAN requirements are minimal, since all calculations go on the side of the SIM card.
Cons of the solution:
- It is necessary to create a new profile of SIM cards, to finance the development of an applet on a SIM card
- It is necessary to create third-party software for various OS phones and PCs. Given that the OS is constantly updated, it will be necessary to periodically release new versions of software or updates.
- The need to configure the software in the WLAN device
- If the subscriber wants to take advantage of the EAP-SIM, he will need to change the SIM card

b) Calculation of the MAC and MAC2 values inside the SIM card. The formation of EAP on the side of the WLAN terminal.
Pluses of the solution:
- High degree of security when calculating GSM triplets
- Work on various WLAN terminals, including PCs with different operating systems, but provided that the installed third-party software will be developed.
Cons of the decision:
- Since EAP packets will be formed and decrypted on the terminal side, there are some performance requirements, but given the modern hardware base of the terminals, these risks are minimized.
- It is necessary to create a new profile of SIM cards, to finance the development of the applet on the SIM card
- It is necessary to create third-party software for various OS phones and PCs. Given that the OS is constantly updated, it will be necessary to periodically release new versions of software or updates.
- The need to configure the software in the WLAN device
- If the subscriber wants to take advantage of the EAP-SIM, he will need to change the SIM card
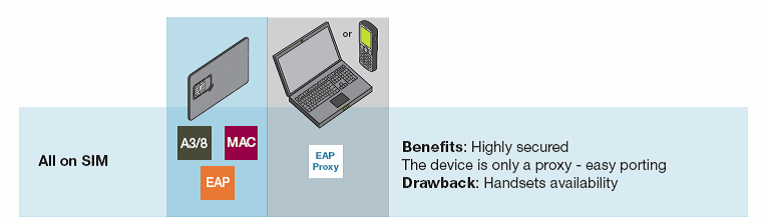
c) Calculation of MAC & MAC2 & EAP packets on the WLAN terminal side.
Advantages of the solution:
- There are no specific requirements for the SIM card, existing SIM cards
are suitable - No additional software needs to be installed on the terminal
- Before connecting to the WLAN network, the subscriber does not need to configure anything on the terminal side (except for iphone).
Cons of the solution:
- An average degree of security when calculating GSM triplets. It should be noted that it is not difficult for a hacker to get GSM triplets even without EAP-SIM technology, but simply by writing software with the RUN GSM Algorithm function. Therefore, the main risks are associated with the possible penetration of trojans on the WLAN terminal, which will intercept data for an already authorized session and use them in a relatively short period of time and at the same access point.
- Requires support for EAP-SIM on the side of the terminal. At the beginning of 2012, of the major vendors, EAP-SIM was supported only by some Nokia, iPhone, and blackberry phones.

5) Equipment requirements for the operation and development of EAP-SIM authentication.
If EAP-SIM authentication is successfully implemented, users get the advantage of transparent and reliable authentication (without entering a username and password) and the ability to use corporate resources (without organizing a VPN channel). The following are the requirements necessary for the operation of EAP-SIM / AKA authentication and the conditions for rapid development:
a) The need to use specific software on a computer and WLAN communicators that do not support EAP-SIM / AKA at the software and hardware level.
b) Although there are several WLAN modems supporting EAP-SIM at the hardware and software level (see the section below), their number is very limited. For WLAN modems with built-in EAP-SIM support, there is no need to use specific software.
c) For WLAN terminals that do not support EAP-SIM / AKA technology, you will have to use additional equipment in the form of a SIM reader, which greatly affects the usability of the service.
d) The limiting factor of using WLAN networks on equipment that does not support EAP-SIM / AKA authentication is the need to remove the SIM card from a standard GSM phone. Telephone communication, in this case, will be unavailable to the subscriber. When using 2 SIM cards, this is not a limiting factor.
e) AAA RADIUS guest WLAN servers and home networks must support EAP-SIM / AKA authentication (as recommended by RFC 4186 and RFC 4187) and IRAP (International Roaming Access Protocols), which is not always guaranteed. In the absence of this functionality, EAP-SIM / AKA roaming is not possible.

f) With a large number of WLAN users, the load on the Auc / HLR operator will increase
g) For each EAP-SIM authentication on the Auc / HLR server, two or three standard GSM authentications are performed, which increases the load on the GSM network equipment (see RFC 4686 chapter 10)
h ) Auc / HLR operator must be able to connect (via SS7 / MAP) to the AAA RADUIS server WLAN home provider
i) The provider WLAN access controller / gateway must support EAP-SIM / AKA (in accordance with the recommendations of RFC 4186 and RFC 4187)
j) EAP-SIM / AKA protocol support will be required on the operator's AuC / HLR side, in accordance with RFC 4186. This the issue needs to be further explored.
k) For the organization of interworking roaming, i.e. in order for the visiting WLAN network to serve any subscriber, it is necessary that roaming agreements are concluded between the visiting providers and the home WLAN provider
l) Since the terminal uses the standard RUN GSM ALGORITHM request when working with the SIM / USIM card, the WLAN, there are no specific SIM / USIM card requirements for implementing EAP-SIM and EAP-AKA. But when using the promising method EAP-SIM inside and EAP-SmartCard, the EAP-SIM protocol and associated cryptographic primitives will be executed in a protected area, so a special SIM card will be required.
6) Standards
- RFC 4186 EAP mechanism for GSM
ftp.isi.edu/in-notes/rfc4186.txt (Recommendations)
- RFC 4187 EAP mechanism for 3rd generation
ftp.isi.edu/in-notes/rfc4187.txt (Recommendations)
- RFC 2284: PPP Extensible Authentication Protocol (EAP)
- WLAN-SIM Specification V 1.0 was released in 2004, however, is not currently available for reading on the site
- WBA: Wireless Broadband Alliance
www.wballiance.net
- FMCA: Fixed-Mobile Convergence Alliance
www.thefmca.com
- Wireless -Link French Hot Spots Operators industry body
www.w-link.org/public/wlink/html/fr/home/home.php
- WLAN Alliance
www.WLAN.org
Conclusions
1. The main constraint to the development of EAP-SIM / AKA authentication is a very small base of user terminals with support for EAP-SIM / AKA protocols. Pressure is required from international alliances to implement the EAP-SIM / AKA functionality in WLAN devices by vendors.
2. The subscriber’s work in roaming is not guaranteed and depends on the support on the AAA RADIUS side of the server of the visiting WLAN of the IRAP network and EAP-SIM / AKA authentication. An additional condition for the subscriber to work in roaming is the availability of roaming agreements.
3. The specifications are very limited. At the same time, specifications for EAP-SIM / AKA implementation available for free reading exist in the form of recommendations (RFC). Other types of documents are either not available outside the alliances or do not exist.
4. At the network levels, for the implementation of the EAP-SIM / AKA functionality additional settings or installations are required on the WLAN side of the AAA RADUIS server and AuC / HLR.
5. In terms of security, two authentication methods are possible using SIM: EAP-SIM inside and EAP-SIM. For EAP-SIM inside, the formation of EAP packets occurs inside the SIM card, which is safer, but requires special SIM cards and special terminals. For EAP-SIM, the formation of EAP packets during authentication is performed on the side of the terminal, therefore triplets of GSM triplets can leak, however, standard SIM cards and any WLAN terminal with installed EAP software can be used for this method.
6. As indicated in the RFC, authentication reliability when using EAP-SIM is no worse than in GSM.
7. The security of the GSM network when using EAP-SIM is quite high, since the Kc values in EAP-SIM are not transmitted to the network. SRES is transmitted to the network in encrypted form. If there is hacker software on the WLAN terminal, occasional cases of leakage of confidential authentication data are possible. Also, in connection with the presence of the final authentication counter on the SIM card, in the presence of hacker software, cases of SIM card blocking are possible.
8. The successful launch of EAP-SIM authentication with the Swiss Mobile operator allows us to talk about the emergence of interest in this technology.
1) EAP-SIM authentication scheme
Legend:
EAP - Enhanced Authentication Protocol (Advanced Authentication Protocol)
SIM - Subscriber Identity Module (GSM Subscriber Identity Module)
MAC - Message Authentication Code
IMSI - International Mobile Subscriber Identifier
Nonce - Random value generated by client side
GSM triplet - RAND and Kc and SRES values calculated on the basis of this RAND according to A3 / A8 algorithms
AuC - Authentication center of GSM operator. One of the tasks is to calculate the GSM triplet.
The basic authentication scheme using EAP-SIM is given below.

EAP-SIM authentication according to this scheme requires the following components:
- Client device (Terminal) with support for a regular GSM SIM card and corresponding software. It is possible to use a specific SIM card, in this case the security will be higher
- 802.1X compatible WLAN access point with EAP-SIM support
- Access controller / gateway with support for DHCP (Dynamic Host Configuration Protocol) and EAP-SIM protocol on the WLAN network side to highlight dynamic IP addresses for network users and interaction with AAA RADIUS server WLAN network via EAP protocol
- AAA RADIUS server used to authenticate the user of the WLAN network using EAP-SIM / AKA algorithms (in traditional WLAN networks, this is an authentication server that in the simplest case checks the entered login & password and charges the subscriber)
- SS7 gateway for the interaction of the AAA RADIUS server of the WLAN network with HLR (Home Location Register) / Authentication Center (AuC) operator. In the diagram, for simplicity, not indicated.
- HLR / AuC - home register of GSM subscribers
2) The principle of operation of EAP-SIM authentication
A timing diagram explaining the principle of EAP-SIM authentication is given below.

If the PIN code is entered correctly (or the request is turned off) and the subscriber has selected the appropriate WLAN network, EAP-SIM authentication starts on his terminal. During the authentication process, the following steps are performed:
a) the EAP Identity Request message is sent to the user terminal via the EAPOL protocol from the WLAN side of the access point (in the Access Point diagram)
b) the user terminal sends an MSISDN in the EAP Identity Response message (as an NAI, for example 250097000000001 @ eapsim.mobile_carrier.ru) used SIM card or pseudonym. Pseudonym (temporary identity), an analog of temporary IMSI, is designed to increase security by hiding the real IMSI.
c) The WLAN access point in the EAP SIM Start Request message informs the user terminal about the supported versions of EAP-SIM authentication, and also requests the parameters of the terminal equipment.
d) the user terminal selects one of the supported authentication algorithms, which is reported to the access point in the EAP SIM Start response message. This message also contains the value of the required number of GSM triplets per session (see clause 3.1).
e) The WLAN access point transforms the 802.1X protocols into RADIUS compatible protocols and sends the MSISDN + parameters from the EAP SIM Start response to the AAA RADIUS server. In turn, the AAA RADIUS server through the SS7 gateway (via MAP) transmits the MSISDN value of the terminal to AuC and requests standard GSM triplets (RAND, Kc, SRES).
d) two or three RAND values received from AuC and Kc & SRES values are used by the WLAN AAA RADIUS server to calculate EAP-SIM authentication keys (K_aut), EAP-SIM encryption keys (K_encr), session keys MSK & EMSK and EAP-SIM additional authentication parameters. Next, an EAP packet is generated containing: RAND values (in clear text), encrypted additional authentication parameters (AT_ENCR_DATA). Next, the EAP packet and the hash of the packet amount (value AT_MAC = SHA1 (EAP packet, NONCE_MT)) are transmitted to the terminal in the EAP SIM Challenge Request message.
e) the RAND values received by the terminal are transmitted to the SIM card for calculating, according to the A3 / A8 algorithms, the SRES and Kc values, which are then used by the terminal to decrypt the “additional authentication parameters” received in the previous step “EAP-SIM”. Further, if the decryption on the terminal side is successful and the “EAP-SIM additional authentication parameters” are correct, the terminal transmits to the network an EAP SIM Challenge Response message indicating a successful “terminal authentication” and a hash of the calculated SRES value (AT_MAC = SHA1 (SRES) ) Otherwise, the SRES hash is not sent.
d) if the WLAN AAA RADIUS server confirms receipt of a sign of successful authentication and if the hash of the SRES sum from the terminal matches the calculated one, the access point starts providing the service and the message “successful authentication server” is sent to the terminal. The provision of the service is possible using standard WPA / WPA2 (WLAN Access Protection) encryption.
The protocols used in each section are shown in the figure below.

It should be noted that for EAP mode, there are two main authentication methods in WLAN networks: EAP-AKA and EAP-SIM. The first is more reliable, but requires a USIM card with Milenage support, in addition, Milenage support must be present on the side of the AuC / HLR operator. The second method indicated is less reliable, requires 2G SIM cards (COMP128v1-4) and standard 2G authentication on the side of the AuC / HLR operator. It should also be noted that authentication by EAP-SIM / AKA is mutual, and is carried out by analyzing the AT_MAC value received from the access point on the terminal side - if the parameters in AT_MAC do not match the parameters of the SIM card, then authentication is terminated and the SRES hash is not transferred to the access point .
Also, when setting up a WLAN network, you must set the user reauthentication mode when a data transfer session is interrupted. Two options are possible here:
- repeated EAP-SIM / AKA authentication
- use of client access parameters (MSISDN, MAC) stored in the AAA RADIUS server and do not re-request triplets from the side of the operator’s AuC server. The second method will reduce the load on the operator’s network, however this method is less secure in the issue of illegal access under the client’s name.
The advantage of EAP-SIM / AKA authentication is the authentication transparent for the subscriber while maintaining data confidentiality, since the Ki secret key is not transmitted to the IP network. As stated in RFC 4186, the reliability of EAP-SIM / AKA authentication is no worse than in GSM.
3) GSM network security when using EAP-SIM authentication
Due to the fact that a SIM card is involved in EAP-SIM authentication, it is necessary to carefully analyze the confidentiality of sensitive data for various EAP-SIM usage schemes. For now, let us turn to RFC 4186, from which two remarks follow:
3.1. As stated in RFC 4186: “The derived 64-bit cipher key (Kc) is not strong enough for data networks in which stronger and longer keys are required.” Kc length is not enough for reliable encryption of user data in a WLAN network. To eliminate this, an algorithm for obtaining 2-3 Kc can be applied with subsequent integration on the client side and AAA RADIUS server WLAN network. When using the algorithm of using 2-3 Ks keys, the reliability of the encryption of the data transmission channel increases.
3.2. The second question is the transfer of the SRES hash from the terminal to the AAA RADIUS server via the WLAN IP network. In the standard case, SRES is not explicitly transmitted and cannot be obtained by an attacker. However, there is a possibility of the presence of “Trojans” on the side of the terminal / PC in order to illegally obtain SRES and Kc. After receiving a sufficiently large number of triplets, it is possible to calculate the Ki key and further clone the GSM SIM card. This method allows you to receive triplets without physical access to the SIM card, which increases the risk of cloning SIM cards. It should also be noted that the algorithm for calculating the hash of the SRES sum through SHA1 is unreliable and has already been hacked (http://www.schneier.com/blog/archives/2005/02/sha1_broken.html). Thus, by listening to a Wi-Fi network, attackers can get real SRES and RAND values. Kc, however,
4) Analysis of solutions for EAP-SIM authentication
Depending on the requirements for the coverage of the terminal base and the level of security, there are three options for implementing EAP-SIM with a mobile operator.
a) Calculation of the MAC and MAC2 values inside the SIM card. Formation of EAP packets inside the SIM card.
Pluses of the solution:
- High degree of security when calculating GSM triplets
- Work on various WLAN terminals, including PCs with different operating systems, but provided that the installed third-party software will be developed. WLAN requirements are minimal, since all calculations go on the side of the SIM card.
Cons of the solution:
- It is necessary to create a new profile of SIM cards, to finance the development of an applet on a SIM card
- It is necessary to create third-party software for various OS phones and PCs. Given that the OS is constantly updated, it will be necessary to periodically release new versions of software or updates.
- The need to configure the software in the WLAN device
- If the subscriber wants to take advantage of the EAP-SIM, he will need to change the SIM card

b) Calculation of the MAC and MAC2 values inside the SIM card. The formation of EAP on the side of the WLAN terminal.
Pluses of the solution:
- High degree of security when calculating GSM triplets
- Work on various WLAN terminals, including PCs with different operating systems, but provided that the installed third-party software will be developed.
Cons of the decision:
- Since EAP packets will be formed and decrypted on the terminal side, there are some performance requirements, but given the modern hardware base of the terminals, these risks are minimized.
- It is necessary to create a new profile of SIM cards, to finance the development of the applet on the SIM card
- It is necessary to create third-party software for various OS phones and PCs. Given that the OS is constantly updated, it will be necessary to periodically release new versions of software or updates.
- The need to configure the software in the WLAN device
- If the subscriber wants to take advantage of the EAP-SIM, he will need to change the SIM card

c) Calculation of MAC & MAC2 & EAP packets on the WLAN terminal side.
Advantages of the solution:
- There are no specific requirements for the SIM card, existing SIM cards
are suitable - No additional software needs to be installed on the terminal
- Before connecting to the WLAN network, the subscriber does not need to configure anything on the terminal side (except for iphone).
Cons of the solution:
- An average degree of security when calculating GSM triplets. It should be noted that it is not difficult for a hacker to get GSM triplets even without EAP-SIM technology, but simply by writing software with the RUN GSM Algorithm function. Therefore, the main risks are associated with the possible penetration of trojans on the WLAN terminal, which will intercept data for an already authorized session and use them in a relatively short period of time and at the same access point.
- Requires support for EAP-SIM on the side of the terminal. At the beginning of 2012, of the major vendors, EAP-SIM was supported only by some Nokia, iPhone, and blackberry phones.

5) Equipment requirements for the operation and development of EAP-SIM authentication.
If EAP-SIM authentication is successfully implemented, users get the advantage of transparent and reliable authentication (without entering a username and password) and the ability to use corporate resources (without organizing a VPN channel). The following are the requirements necessary for the operation of EAP-SIM / AKA authentication and the conditions for rapid development:
a) The need to use specific software on a computer and WLAN communicators that do not support EAP-SIM / AKA at the software and hardware level.
b) Although there are several WLAN modems supporting EAP-SIM at the hardware and software level (see the section below), their number is very limited. For WLAN modems with built-in EAP-SIM support, there is no need to use specific software.
c) For WLAN terminals that do not support EAP-SIM / AKA technology, you will have to use additional equipment in the form of a SIM reader, which greatly affects the usability of the service.
d) The limiting factor of using WLAN networks on equipment that does not support EAP-SIM / AKA authentication is the need to remove the SIM card from a standard GSM phone. Telephone communication, in this case, will be unavailable to the subscriber. When using 2 SIM cards, this is not a limiting factor.
e) AAA RADIUS guest WLAN servers and home networks must support EAP-SIM / AKA authentication (as recommended by RFC 4186 and RFC 4187) and IRAP (International Roaming Access Protocols), which is not always guaranteed. In the absence of this functionality, EAP-SIM / AKA roaming is not possible.

f) With a large number of WLAN users, the load on the Auc / HLR operator will increase
g) For each EAP-SIM authentication on the Auc / HLR server, two or three standard GSM authentications are performed, which increases the load on the GSM network equipment (see RFC 4686 chapter 10)
h ) Auc / HLR operator must be able to connect (via SS7 / MAP) to the AAA RADUIS server WLAN home provider
i) The provider WLAN access controller / gateway must support EAP-SIM / AKA (in accordance with the recommendations of RFC 4186 and RFC 4187)
j) EAP-SIM / AKA protocol support will be required on the operator's AuC / HLR side, in accordance with RFC 4186. This the issue needs to be further explored.
k) For the organization of interworking roaming, i.e. in order for the visiting WLAN network to serve any subscriber, it is necessary that roaming agreements are concluded between the visiting providers and the home WLAN provider
l) Since the terminal uses the standard RUN GSM ALGORITHM request when working with the SIM / USIM card, the WLAN, there are no specific SIM / USIM card requirements for implementing EAP-SIM and EAP-AKA. But when using the promising method EAP-SIM inside and EAP-SmartCard, the EAP-SIM protocol and associated cryptographic primitives will be executed in a protected area, so a special SIM card will be required.
6) Standards
- RFC 4186 EAP mechanism for GSM
ftp.isi.edu/in-notes/rfc4186.txt (Recommendations)
- RFC 4187 EAP mechanism for 3rd generation
ftp.isi.edu/in-notes/rfc4187.txt (Recommendations)
- RFC 2284: PPP Extensible Authentication Protocol (EAP)
- WLAN-SIM Specification V 1.0 was released in 2004, however, is not currently available for reading on the site
- WBA: Wireless Broadband Alliance
www.wballiance.net
- FMCA: Fixed-Mobile Convergence Alliance
www.thefmca.com
- Wireless -Link French Hot Spots Operators industry body
www.w-link.org/public/wlink/html/fr/home/home.php
- WLAN Alliance
www.WLAN.org
Conclusions
1. The main constraint to the development of EAP-SIM / AKA authentication is a very small base of user terminals with support for EAP-SIM / AKA protocols. Pressure is required from international alliances to implement the EAP-SIM / AKA functionality in WLAN devices by vendors.
2. The subscriber’s work in roaming is not guaranteed and depends on the support on the AAA RADIUS side of the server of the visiting WLAN of the IRAP network and EAP-SIM / AKA authentication. An additional condition for the subscriber to work in roaming is the availability of roaming agreements.
3. The specifications are very limited. At the same time, specifications for EAP-SIM / AKA implementation available for free reading exist in the form of recommendations (RFC). Other types of documents are either not available outside the alliances or do not exist.
4. At the network levels, for the implementation of the EAP-SIM / AKA functionality additional settings or installations are required on the WLAN side of the AAA RADUIS server and AuC / HLR.
5. In terms of security, two authentication methods are possible using SIM: EAP-SIM inside and EAP-SIM. For EAP-SIM inside, the formation of EAP packets occurs inside the SIM card, which is safer, but requires special SIM cards and special terminals. For EAP-SIM, the formation of EAP packets during authentication is performed on the side of the terminal, therefore triplets of GSM triplets can leak, however, standard SIM cards and any WLAN terminal with installed EAP software can be used for this method.
6. As indicated in the RFC, authentication reliability when using EAP-SIM is no worse than in GSM.
7. The security of the GSM network when using EAP-SIM is quite high, since the Kc values in EAP-SIM are not transmitted to the network. SRES is transmitted to the network in encrypted form. If there is hacker software on the WLAN terminal, occasional cases of leakage of confidential authentication data are possible. Also, in connection with the presence of the final authentication counter on the SIM card, in the presence of hacker software, cases of SIM card blocking are possible.
8. The successful launch of EAP-SIM authentication with the Swiss Mobile operator allows us to talk about the emergence of interest in this technology.
