New Android RAT uses Telegram protocol
The ESET Virus Lab discovered a new Android RAT (Remote Administration Tool) that uses the Telegram protocol to control and exfiltrate data. Initially, we paid attention to increasing the activity of already known IRRAT and TeleRAT , but then, having understood what is happening, we found a completely new family. The new RAT has been active at least since August 2017. In March 2018, the source code of Malvari was distributed via hacker telegram channels, as a result of which hundreds of modifications are in effect today in the wild.

One of the versions is different from the rest. Despite the availability of the source code, it is sold under the commercial name HeroRat through a special Telegram channel. The authors offer HeroRat for use on the model of Malware-as-a-Service. Malware is available in three trim levels with different functions and video support channel. It is not clear whether this version was written on the basis of the merged code or, on the contrary, is the original, the source code of which then appeared on the network.
Attackers distribute RAT through informal Android application stores, social networks and instant messengers. We have seen how a malware is disguised as applications that promise bitcoins as a gift, free mobile Internet, or subscribers to social networks. This Malvar was not found on Google Play. Most of the infections are recorded in Iran.
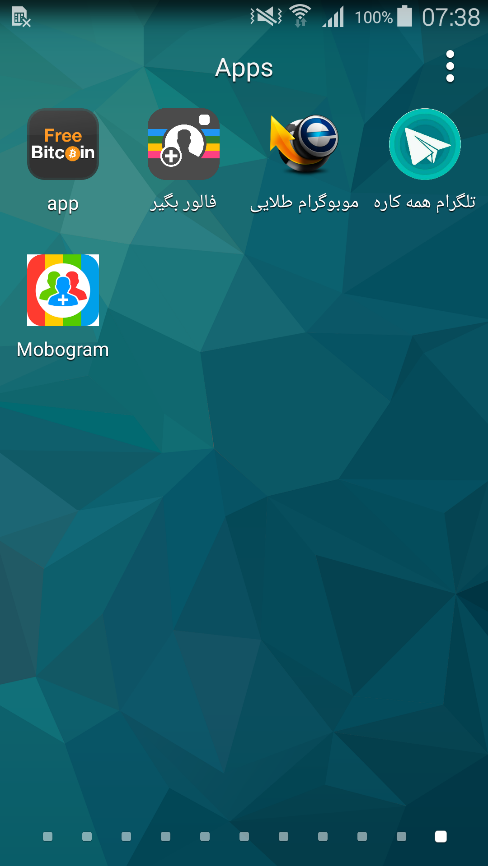
Figure 1. Several applications used to distribute RAT
Malware is compatible with all versions of Android. The user is required to accept a permission request (sometimes including activating the application as a device administrator), for which social engineering is used.
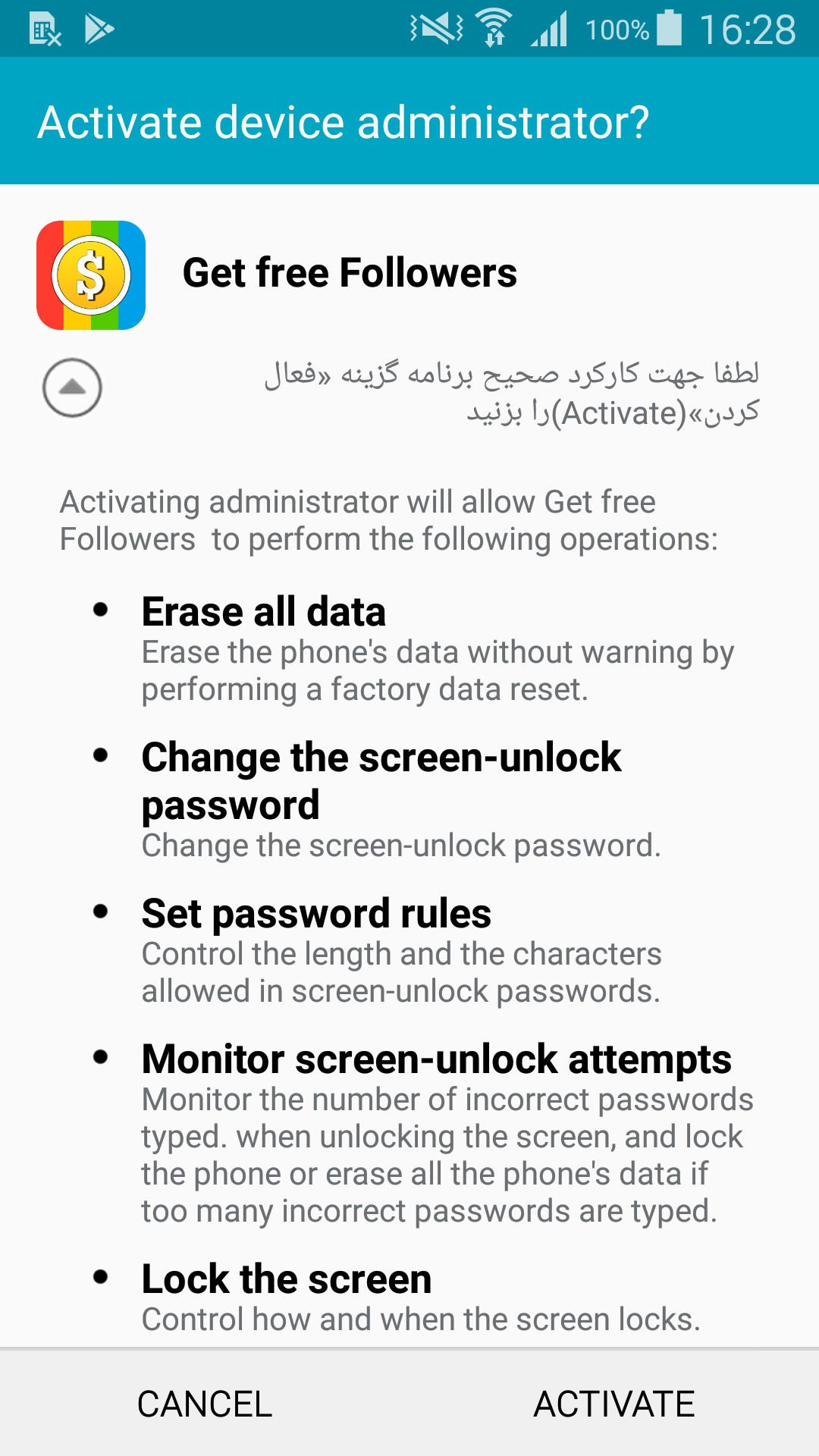
Figure 2. RAT Requests Device Administrator Rights
After installing and running the malicious application, a small pop-up window appears on the screen. It states that the program cannot work on the device and will be deleted. We saw samples with messages in English and Persian (depending on the device language settings).
When deletion is complete, the application icon will disappear. At the same time, a new infected device will be registered on the attacking side.
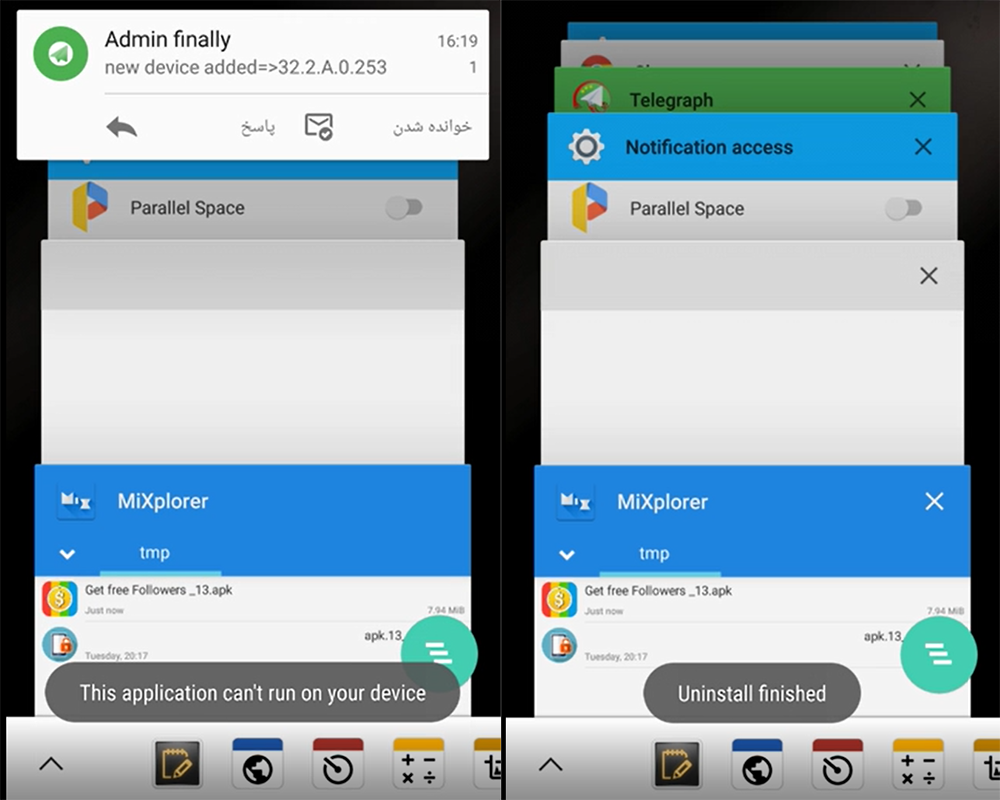
Figure 3. Demonstration of installing HeroRat on the device (screenshots from the Malvari authors' training video)
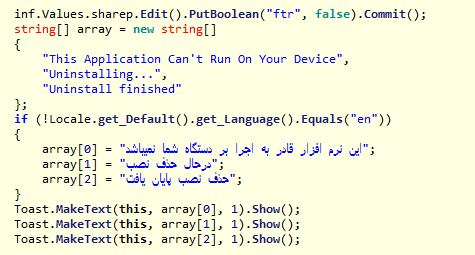
Figure 4. Malvari source code with a fake message about deletion in English and Persian
Having gained access to the compromised device, the attacker uses the capabilities of Telegram botto manage the new device. Each infected device is controlled by a bot, configured and monitored via the Telegram application.
The malware has a wide range of spying and exfiltration tools, including intercepting text messages and contacts, sending text messages and calls, recording audio and creating screenshots, determining the location of the device and managing its settings.
HeroRat is sold in three trim levels (bronze, silver and gold packages) for $ 25, $ 50 and $ 100, respectively. The source code from the author HeroRat is offered to buy for $ 650.
HeroRat functions are accessed via interactive buttons in the Telegram bot interface. Attackers can control infected devices by pressing the buttons that are available in the version of RAT that they paid for and use.
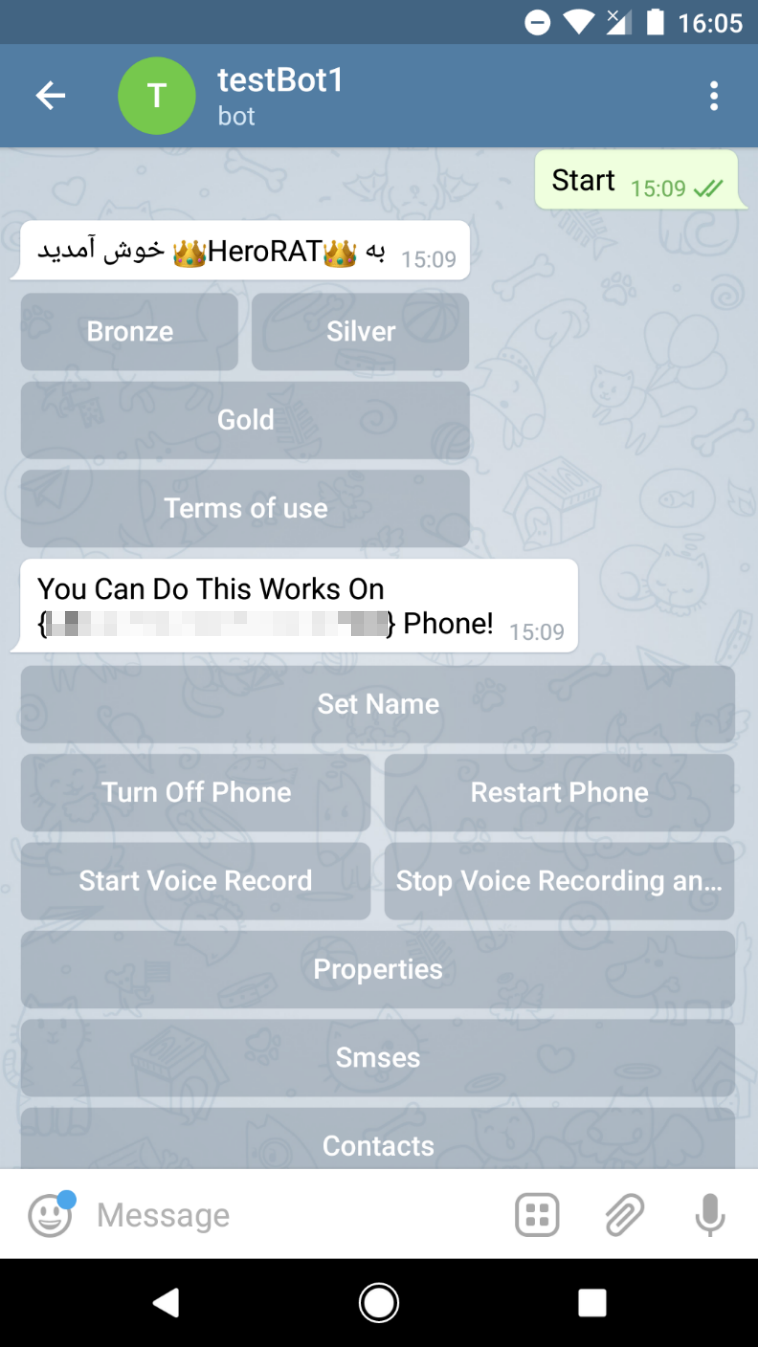
Figure 5. HeroRat Control Panel
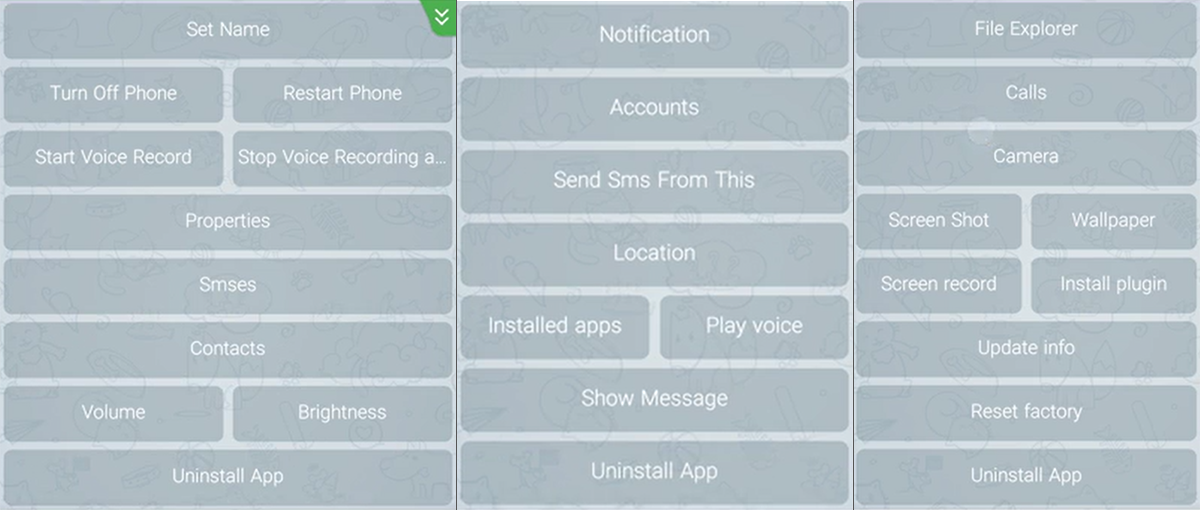
Figure 6. HeroRat Functions (from left to right): Bronze, Silver and Gold Packages (screenshots from the Malvari authors' training video)
In contrast to previously studied Android RATs using Telegram, which are written in standard Android Java, the new family developed from scratch in C # using the Xamarin framework - a rare combination for Android-Malvari.
The communication method via the Telegram protocol is adapted to the programming language - instead of the Telegram Bot API, which was previously used by RAT, the new family uses Telesharp , a library to create Telegram bots in C #.
Transmission of commands and exfiltration of data from infected devices are fully covered by the Telegram protocol - this measure is aimed at countering traffic-based detection to known download servers.
System.OS - 896FFA6CB6D7789662ACEDC3F9C024A0 - Android / Agent.AQO
Andro.OS - E16349E8BB8F76DCFF973CB71E9EA59E - Android / Spy.Agent.AMS
FreeInterNet.OS - 0E6FDBDF1FBEefa.Esche.Agent.AMS FreeInterNet.OS - 0E6FDBDF1FBEefa.EscF.Agent.AMS FreeInterNet.OS - 0E6FDBDF1FBEefa.ch.

One of the versions is different from the rest. Despite the availability of the source code, it is sold under the commercial name HeroRat through a special Telegram channel. The authors offer HeroRat for use on the model of Malware-as-a-Service. Malware is available in three trim levels with different functions and video support channel. It is not clear whether this version was written on the basis of the merged code or, on the contrary, is the original, the source code of which then appeared on the network.
How it works
Attackers distribute RAT through informal Android application stores, social networks and instant messengers. We have seen how a malware is disguised as applications that promise bitcoins as a gift, free mobile Internet, or subscribers to social networks. This Malvar was not found on Google Play. Most of the infections are recorded in Iran.

Figure 1. Several applications used to distribute RAT
Malware is compatible with all versions of Android. The user is required to accept a permission request (sometimes including activating the application as a device administrator), for which social engineering is used.

Figure 2. RAT Requests Device Administrator Rights
After installing and running the malicious application, a small pop-up window appears on the screen. It states that the program cannot work on the device and will be deleted. We saw samples with messages in English and Persian (depending on the device language settings).
When deletion is complete, the application icon will disappear. At the same time, a new infected device will be registered on the attacking side.

Figure 3. Demonstration of installing HeroRat on the device (screenshots from the Malvari authors' training video)

Figure 4. Malvari source code with a fake message about deletion in English and Persian
Having gained access to the compromised device, the attacker uses the capabilities of Telegram botto manage the new device. Each infected device is controlled by a bot, configured and monitored via the Telegram application.
The malware has a wide range of spying and exfiltration tools, including intercepting text messages and contacts, sending text messages and calls, recording audio and creating screenshots, determining the location of the device and managing its settings.
HeroRat is sold in three trim levels (bronze, silver and gold packages) for $ 25, $ 50 and $ 100, respectively. The source code from the author HeroRat is offered to buy for $ 650.
HeroRat functions are accessed via interactive buttons in the Telegram bot interface. Attackers can control infected devices by pressing the buttons that are available in the version of RAT that they paid for and use.

Figure 5. HeroRat Control Panel

Figure 6. HeroRat Functions (from left to right): Bronze, Silver and Gold Packages (screenshots from the Malvari authors' training video)
In contrast to previously studied Android RATs using Telegram, which are written in standard Android Java, the new family developed from scratch in C # using the Xamarin framework - a rare combination for Android-Malvari.
The communication method via the Telegram protocol is adapted to the programming language - instead of the Telegram Bot API, which was previously used by RAT, the new family uses Telesharp , a library to create Telegram bots in C #.
Transmission of commands and exfiltration of data from infected devices are fully covered by the Telegram protocol - this measure is aimed at countering traffic-based detection to known download servers.
Infection indicators
System.OS - 896FFA6CB6D7789662ACEDC3F9C024A0 - Android / Agent.AQO
Andro.OS - E16349E8BB8F76DCFF973CB71E9EA59E - Android / Spy.Agent.AMS
FreeInterNet.OS - 0E6FDBDF1FBEefa.Esche.Agent.AMS FreeInterNet.OS - 0E6FDBDF1FBEefa.EscF.Agent.AMS FreeInterNet.OS - 0E6FDBDF1FBEefa.ch.
