Viral analysis for beginners - we analyze Virus.Win32.MTV
I finally found the time not only to analyze malware, but also to write another article on this topic. Let's start. Today we will analyze the virus Virus.Win32.MTV.4608.a detected in 2000. Let the date of detection of the virus do not bother you - the analysis of the virus even of such a limitation will never interfere. You can take it at vx.netlux.org.
Tools Required: Any disassembler or debugger of your choice.
So, load our test file into any disassembler or debugger. We see a very nice code for analysis - no packaging, no obfuscation, no anti-debugging - everything can be seen clearly. Immediately struck by the line: "Copyright 1989-2000 Borland Inc. Borland C ++ run-time library ”, which defines the language and version of the compiler on which the virus was written. We begin, directly, the analysis of the functionality of this virus in the most detailed way. The program starts from the following location:
00401000> MOV ESI, Virus.004032A8
00401005 MOV ECX, 2D
0040100A> MOV AL, BYTE PTR DS: [ESI]
0040100C XOR AL, 3
0040100E MOV BYTE PTR DS: [ESI], AL
00401010 INC ESI
00401011 ^ LOOPD SHORT Virus.0040100A
This loop decrypts string constants located at 0x004032A8 at 0x2D bytes in size. After decryption, we get this:
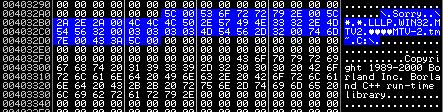
Next, the following code will be executed:
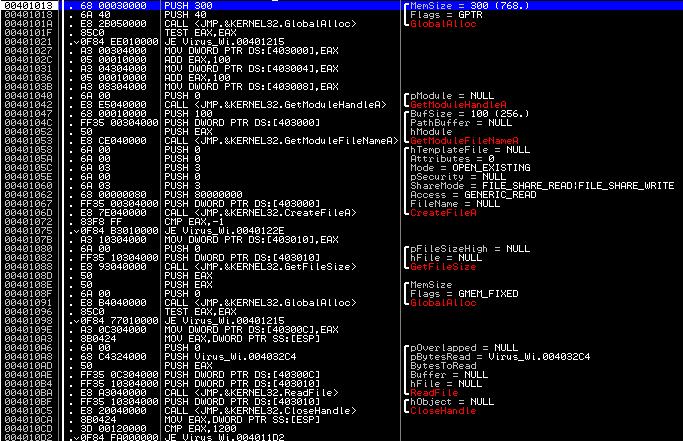
It is easy to see that the program determines its location on the disk, opens its own file for reading, recognizes its size and loads it into a specially allocated memory area. What for? We will understand further. And now we note that in case of any adverse events for the program, it displays a message box and shuts down Windows:
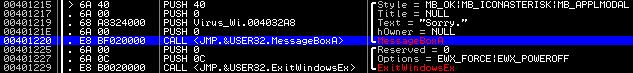
Now let's pay attention to the following place:
004010CD CMP EAX, 1200
004010D2 JE Virus.004011D2
Here the program compares its physical size with the constant 0x1200 and, depending on this operation, continues to execute it in various ways. The size of the current file is also 0x1200. It can be assumed that this instance of the program is the source file of the virus, which will subsequently be confirmed. We look at what to execute if the file size is different from 0x1200:

First, the program creates a temporary file, and then decrypts some memory area in the following cycle:
00401152> MOV AL, BYTE PTR DS: [ESI]
00401154 XOR AL, 3
00401156 MOV BYTE PTR DS: [ESI], AL
00401158 INC ESI
00401159 ^ LOOPD SHORT Virus.00401152
Encryption is a simple byte XOR. What memory area does the program decrypt? This area is a buffer in which the program previously wrote down the contents of the current executable file, and decryption starts at offset 0x1200. You have not guessed what is happening? We look further - after this, the program writes the decrypted data to a temporary file and launches the latter for execution, passing the current command line parameters. Now we can confidently say that this program infects executable files in the most primitive way, encrypting their contents and dumping the received encrypted data into the overlay of its own file, which is written instead of the infected program. And when launched, the virus decrypts the overlay, saves it to a temporary file and launches the original program for execution.
We now find out what happens next:
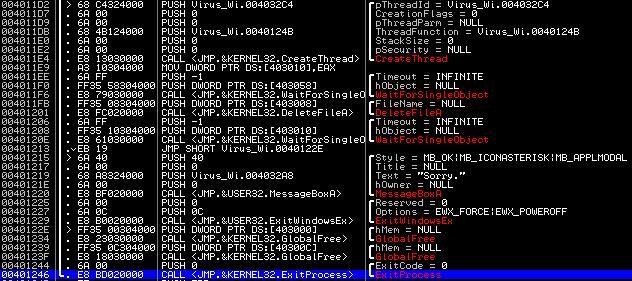
Then the program starts another thread and waits for the completion of both the original program and the created thread. What happens in the created thread?

The program determines whether a copy of the virus is already running in the system by checking the existence of the global identifier “MTV-2” - if it exists, then a copy of the virus is already running, otherwise this identifier is created, after which another virus function is called. Let's see what she does:

As expected, this is a function of recursively traversing folders on a disk that infects all found executable files. I was interested in two points here. First, the function proceeds to processing the next file after only 5 seconds due to the WinAPI delay by the Sleep function. It follows that the virus will very, very slowly sort through all the files and hang all the time in the list of tasks. So the following code:
004013C6 the PUSH Virus.004032D6
004013CB the CALL the JMP & KERNEL32.GetSystemTime.
004013D0 CMP WORD the PTR the DS: [4032DC], 0D
004013D8 JNZ SHORT Virus_Wi.004013E6
004013DA the PUSH Virus.004031A6
004013DF the CALL the JMP & KERNEL32.DeleteFileA.
If today is the 13th day of any month, then the function deletes all the files found ... This is where all the poor functionality of this virus ends.
Conclusions: today we have analyzed a virus that is easy to use and fast to write, the creation of which does not require special knowledge and can be done by almost any novice programmer. Moreover, the functionality of the virus is also extremely poor. It can be seen that the programmer had no craving for creativity - everything was aimed at a quick result. Although ... I absolutely can not understand for what purpose this virus, in general, is intended? Nevertheless, over 10 years, malware has taken a big step in its development.
Tools Required: Any disassembler or debugger of your choice.
So, load our test file into any disassembler or debugger. We see a very nice code for analysis - no packaging, no obfuscation, no anti-debugging - everything can be seen clearly. Immediately struck by the line: "Copyright 1989-2000 Borland Inc. Borland C ++ run-time library ”, which defines the language and version of the compiler on which the virus was written. We begin, directly, the analysis of the functionality of this virus in the most detailed way. The program starts from the following location:
00401000> MOV ESI, Virus.004032A8
00401005 MOV ECX, 2D
0040100A> MOV AL, BYTE PTR DS: [ESI]
0040100C XOR AL, 3
0040100E MOV BYTE PTR DS: [ESI], AL
00401010 INC ESI
00401011 ^ LOOPD SHORT Virus.0040100A
This loop decrypts string constants located at 0x004032A8 at 0x2D bytes in size. After decryption, we get this:

Next, the following code will be executed:

It is easy to see that the program determines its location on the disk, opens its own file for reading, recognizes its size and loads it into a specially allocated memory area. What for? We will understand further. And now we note that in case of any adverse events for the program, it displays a message box and shuts down Windows:

Now let's pay attention to the following place:
004010CD CMP EAX, 1200
004010D2 JE Virus.004011D2
Here the program compares its physical size with the constant 0x1200 and, depending on this operation, continues to execute it in various ways. The size of the current file is also 0x1200. It can be assumed that this instance of the program is the source file of the virus, which will subsequently be confirmed. We look at what to execute if the file size is different from 0x1200:

First, the program creates a temporary file, and then decrypts some memory area in the following cycle:
00401152> MOV AL, BYTE PTR DS: [ESI]
00401154 XOR AL, 3
00401156 MOV BYTE PTR DS: [ESI], AL
00401158 INC ESI
00401159 ^ LOOPD SHORT Virus.00401152
Encryption is a simple byte XOR. What memory area does the program decrypt? This area is a buffer in which the program previously wrote down the contents of the current executable file, and decryption starts at offset 0x1200. You have not guessed what is happening? We look further - after this, the program writes the decrypted data to a temporary file and launches the latter for execution, passing the current command line parameters. Now we can confidently say that this program infects executable files in the most primitive way, encrypting their contents and dumping the received encrypted data into the overlay of its own file, which is written instead of the infected program. And when launched, the virus decrypts the overlay, saves it to a temporary file and launches the original program for execution.
We now find out what happens next:

Then the program starts another thread and waits for the completion of both the original program and the created thread. What happens in the created thread?

The program determines whether a copy of the virus is already running in the system by checking the existence of the global identifier “MTV-2” - if it exists, then a copy of the virus is already running, otherwise this identifier is created, after which another virus function is called. Let's see what she does:

As expected, this is a function of recursively traversing folders on a disk that infects all found executable files. I was interested in two points here. First, the function proceeds to processing the next file after only 5 seconds due to the WinAPI delay by the Sleep function. It follows that the virus will very, very slowly sort through all the files and hang all the time in the list of tasks. So the following code:
004013C6 the PUSH Virus.004032D6
004013CB the CALL the JMP & KERNEL32.GetSystemTime.
004013D0 CMP WORD the PTR the DS: [4032DC], 0D
004013D8 JNZ SHORT Virus_Wi.004013E6
004013DA the PUSH Virus.004031A6
004013DF the CALL the JMP & KERNEL32.DeleteFileA.
If today is the 13th day of any month, then the function deletes all the files found ... This is where all the poor functionality of this virus ends.
Conclusions: today we have analyzed a virus that is easy to use and fast to write, the creation of which does not require special knowledge and can be done by almost any novice programmer. Moreover, the functionality of the virus is also extremely poor. It can be seen that the programmer had no craving for creativity - everything was aimed at a quick result. Although ... I absolutely can not understand for what purpose this virus, in general, is intended? Nevertheless, over 10 years, malware has taken a big step in its development.
