How to get access to other people's mail.ru mailboxes
The other day, a friend asked me to see what kind of strange letters were being poured into his inbox.
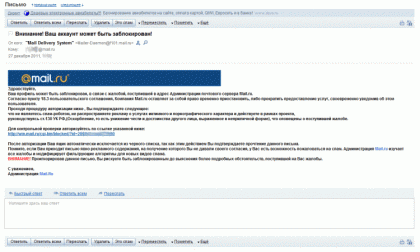
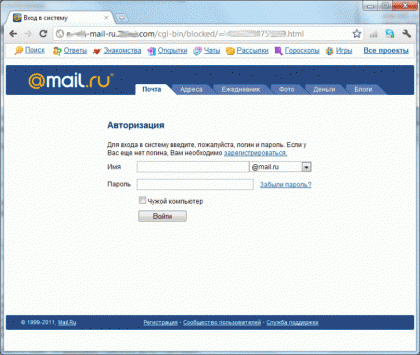
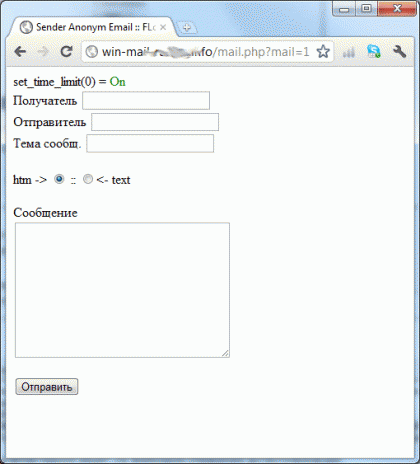
We open his mail, I see a letter: the details of the letter are hidden so that the attacker does not chase a friend. The link naturally leads to a fake authentication page: this would end if the heading of the letter and I didn’t find the host and the script from which the newsletter was sent : Google gave the sources of this script, and the log file name is log.txt. The IP addresses of the person who sent the fakes turned out to be in the log - 78.36.109.183 , 209.73.132.218 A little google on the intitle header : “Sender Anonym Email” I found more “live” version of the script, and on them the logs: anonim-servis.hak-club.ru/log.txt (
mirror )
newamn.h18.ru/log.txt
and they also have ip 78.36.109.183 and 213.87.128.72 in them , most likely the bad guy walks directly.
Having studied the logs, it became clear to me that the “cracker” uses alinashevchykova@mail.ru as a test mail before sending fakes to the victims.
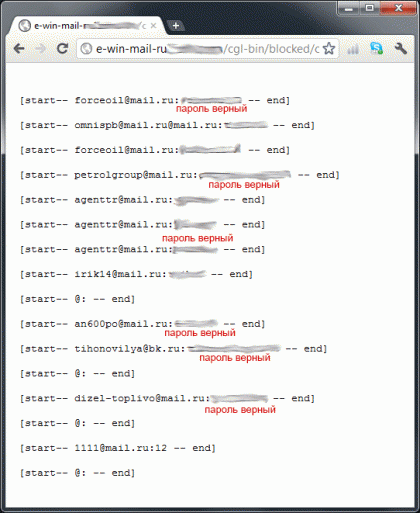
Further it turned out that the folder index was not closed on the fake host: and the file c contains the passwords of the users that had fallen on the fake: list of victims: No morale. There is no point in warning users - they are again pecking at another “fake”. There is no point in writing to the hoster - the scripts will simply move to other free hosting. Calculate by ip? There is no date and time in the log.

We open his mail, I see a letter: the details of the letter are hidden so that the attacker does not chase a friend. The link naturally leads to a fake authentication page: this would end if the heading of the letter and I didn’t find the host and the script from which the newsletter was sent : Google gave the sources of this script, and the log file name is log.txt. The IP addresses of the person who sent the fakes turned out to be in the log - 78.36.109.183 , 209.73.132.218 A little google on the intitle header : “Sender Anonym Email” I found more “live” version of the script, and on them the logs: anonim-servis.hak-club.ru/log.txt (



mirror )
newamn.h18.ru/log.txt
and they also have ip 78.36.109.183 and 213.87.128.72 in them , most likely the bad guy walks directly.
Having studied the logs, it became clear to me that the “cracker” uses alinashevchykova@mail.ru as a test mail before sending fakes to the victims.
Further it turned out that the folder index was not closed on the fake host: and the file c contains the passwords of the users that had fallen on the fake: list of victims: No morale. There is no point in warning users - they are again pecking at another “fake”. There is no point in writing to the hoster - the scripts will simply move to other free hosting. Calculate by ip? There is no date and time in the log.


forceoil@mail.ru
omnispb@mail.ru
petrolgroup@mail.ru
agenttr@mail.ru
irik14@mail.ru
an600po@mail.ru
tihonovilya@bk.ru
dizel-toplivo@mail.ru