Second World War Mechanical Encryption Device

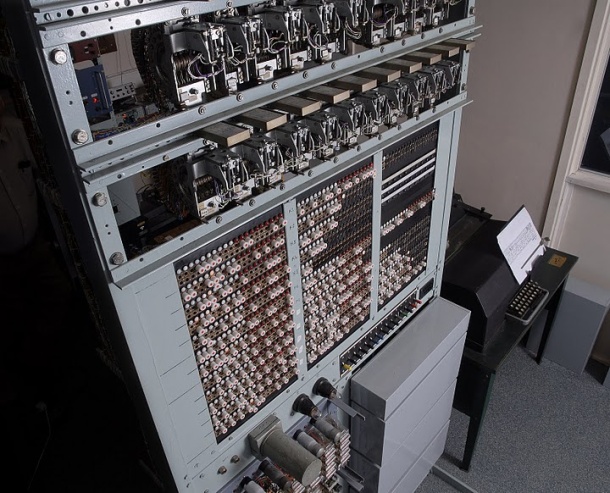
Engineers at the Bletchley Park Computer Science Museum recreated and presented to the general public the Tunny computer, which during the Second World War was used by the armed forces of the anti-Hitler coalition to decrypt Nazi radio communications. Work on the machine lasted three years and was seriously hampered by the fact that after the end of the war Tunny was disassembled, its components were lost, and the original drawings were destroyed or hidden, despite the fact that in May 1945 there were 15 operational devices.
To encrypt messages, the Germans used Lorenz teleprinters with encryption prefixes, the results of which could not be decrypted. However, as often happens, chance played a key role - on August 30, 1941, the German operator broadcast two almost identical messages (the first was delivered incorrectly, the second was slightly changed), using the same key twice. The radio interception service worked perfectly and this error was enough for John Tiltman, head of the Bletchley cryptanalysts department, so that the Allies could successfully read German radiograms using Tunny until the end of the war.
Thanks for clarification to habruyzer SCoon .
Under the cat more photos recreated Tunny.