Security analysis of Kaspersky Lab product removal utility
The overall reliability of system protection is determined by its least resistant component. If the protection designer forgets about this rule, it sooner or later collapses ...
The other day there was a problem - remove the jammed Kaspersky. The old one did not want to leave at all, the new one did not want to be set. The great and powerful Google issued a solution to the problem - “Kaspersky Lab Product Removal Utility”, in fact, the authorship of the Lab itself. The program turned out to be extremely interesting, so immediately there was a desire to dig it ...
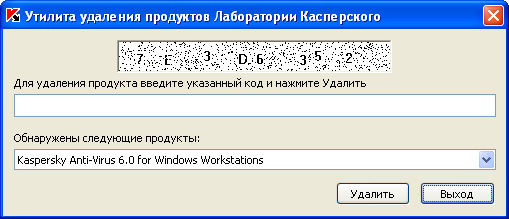
As it turned out, this wonderful utility in one fell swoop demolishes all the world-famous products from Kaspersky Lab (for Windows, of course), moreover, the paranoid configurations, including password-protected ones, are deleted without unnecessary conversations! The utility is digitally signed by the Laboratory and automatically falls into the “Trusted” groups, and even if the checkbox “Put in“ Trusted ”programs with a digital signature is unchecked, here, apparently, the antivirus senses a native blood and claps its ears warmly when meeting with Remuver. For all this happiness, they demand from us to introduce some kind of listless captcha, which you won’t look at without tears ...
To get the coordinates of the captcha picture's field, we find the Remuver window, look at the list of window elements, look for an element of the “STATIC” class and empty text. Having the coordinates, we cut out this area from the screenshot of the screen and pass it to the recognition algorithm. It wasn’t possible to take a copy of the client area of the active window of Rumuver, either his hands were crooked (although everything worked with other applications), or the guys from the Laboratory nevertheless had something there to protect, I had to cut the captcha area from a screenshot of the entire screen. We drive the finished line into the clipboard and paste it into the code input field in the utility window, and then you can emulate pressing the “Delete” and “Exit” buttons. The window itself can be hidden, pushed off the screen or hung on top of your own. A program using Remover from the point of view of the antivirus, it does not do anything illegal and falls into the group “Weak restrictions”. Remuver itself, launched by this program, ends up in Trusted.
It was experimentally found that the captcha uses only 16 characters (where does Uncle Zhenya get such greed?). These are single digits (0-9) and the first 6 letters of the Latin alphabet (A, B, C, D, E, F). The font does not change, tilt and distortion are not used. As a “protection”, a slight change in the position of each symbol and random point noise are applied.
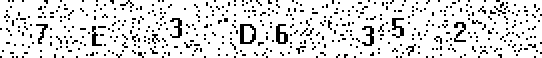
Single and some other groups of filled pixels are removed. As it turned out, the recognition algorithm works fine even without cleaning the image, so I did not bother with noise reduction so as not to damage the characters themselves.
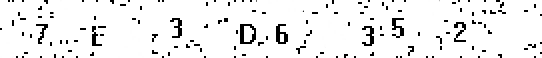
The statistics of the distribution of filled pixels are used, roughly speaking, where the concentration is stronger, there, apparently, is a symbol. The 8 areas with the highest concentration are selected.
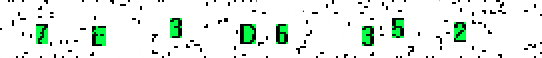
Because symbols on the captcha are not subject to geometric deformations, it was decided to simply collect a collection of 16 reference images, when recognizing them pixel by pixel, compare with areas presumably containing symbols. That standard, for which there will be the most matches, will be considered the right decision.
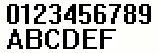
In my demo , the recognition efficiency for a single character is 99%, for the entire captcha of 8 characters, respectively 92%. I immediately warn you that it does not delete anything, it simply recognizes the captcha and inserts the code into the input field.
It would not be difficult for an attacker to covertly use the Kaspersky Lab product removal utility (for example, embed it in a trojan), because protection mechanisms implemented in it are too primitive.
1. The guys from the Laboratory can buy beer, or how they stimulate the brain, bring the complexity of captcha to an acceptable level and generally think about protecting the utility. Release a new, stable version of Remover.
2. Blacklist old versions, or at least make sure that they do not automatically fall into trusted ones. Ordinary users will not suffer because they can always download the new version, and the attacker will not be able to quietly launch the old one.
3. Well, or you can just get into this business and hope that virus writers will be able to embed recognizers into trojans, although chatbots are already using it ...
In general, I have great respect for Kaspersky Lab, I myself actually use only their products all my conscious life, so I just want the quality of protection to become even higher. I recommend using my lotion only for acute attacks of laziness and myopia, and not for destructive purposes;) By the way, Dr.Web also has a similar utility, but it has a more serious captcha. I will try to talk about it next time if this topic is interesting to someone.
The other day there was a problem - remove the jammed Kaspersky. The old one did not want to leave at all, the new one did not want to be set. The great and powerful Google issued a solution to the problem - “Kaspersky Lab Product Removal Utility”, in fact, the authorship of the Lab itself. The program turned out to be extremely interesting, so immediately there was a desire to dig it ...

As it turned out, this wonderful utility in one fell swoop demolishes all the world-famous products from Kaspersky Lab (for Windows, of course), moreover, the paranoid configurations, including password-protected ones, are deleted without unnecessary conversations! The utility is digitally signed by the Laboratory and automatically falls into the “Trusted” groups, and even if the checkbox “Put in“ Trusted ”programs with a digital signature is unchecked, here, apparently, the antivirus senses a native blood and claps its ears warmly when meeting with Remuver. For all this happiness, they demand from us to introduce some kind of listless captcha, which you won’t look at without tears ...
So let's get started
To get the coordinates of the captcha picture's field, we find the Remuver window, look at the list of window elements, look for an element of the “STATIC” class and empty text. Having the coordinates, we cut out this area from the screenshot of the screen and pass it to the recognition algorithm. It wasn’t possible to take a copy of the client area of the active window of Rumuver, either his hands were crooked (although everything worked with other applications), or the guys from the Laboratory nevertheless had something there to protect, I had to cut the captcha area from a screenshot of the entire screen. We drive the finished line into the clipboard and paste it into the code input field in the utility window, and then you can emulate pressing the “Delete” and “Exit” buttons. The window itself can be hidden, pushed off the screen or hung on top of your own. A program using Remover from the point of view of the antivirus, it does not do anything illegal and falls into the group “Weak restrictions”. Remuver itself, launched by this program, ends up in Trusted.
Captcha Recognition
It was experimentally found that the captcha uses only 16 characters (where does Uncle Zhenya get such greed?). These are single digits (0-9) and the first 6 letters of the Latin alphabet (A, B, C, D, E, F). The font does not change, tilt and distortion are not used. As a “protection”, a slight change in the position of each symbol and random point noise are applied.
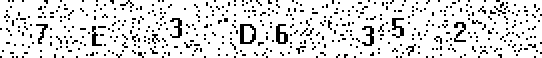
1. Noise cleaning
Single and some other groups of filled pixels are removed. As it turned out, the recognition algorithm works fine even without cleaning the image, so I did not bother with noise reduction so as not to damage the characters themselves.
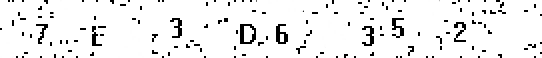
2. Highlight areas containing characters
The statistics of the distribution of filled pixels are used, roughly speaking, where the concentration is stronger, there, apparently, is a symbol. The 8 areas with the highest concentration are selected.
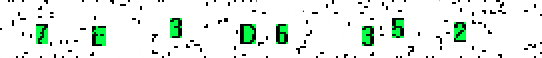
3. Recognition of each character by comparison with a standard
Because symbols on the captcha are not subject to geometric deformations, it was decided to simply collect a collection of 16 reference images, when recognizing them pixel by pixel, compare with areas presumably containing symbols. That standard, for which there will be the most matches, will be considered the right decision.
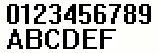
In my demo , the recognition efficiency for a single character is 99%, for the entire captcha of 8 characters, respectively 92%. I immediately warn you that it does not delete anything, it simply recognizes the captcha and inserts the code into the input field.
Conclusion
It would not be difficult for an attacker to covertly use the Kaspersky Lab product removal utility (for example, embed it in a trojan), because protection mechanisms implemented in it are too primitive.
What to do?
1. The guys from the Laboratory can buy beer, or how they stimulate the brain, bring the complexity of captcha to an acceptable level and generally think about protecting the utility. Release a new, stable version of Remover.
2. Blacklist old versions, or at least make sure that they do not automatically fall into trusted ones. Ordinary users will not suffer because they can always download the new version, and the attacker will not be able to quietly launch the old one.
3. Well, or you can just get into this business and hope that virus writers will be able to embed recognizers into trojans, although chatbots are already using it ...
PS
In general, I have great respect for Kaspersky Lab, I myself actually use only their products all my conscious life, so I just want the quality of protection to become even higher. I recommend using my lotion only for acute attacks of laziness and myopia, and not for destructive purposes;) By the way, Dr.Web also has a similar utility, but it has a more serious captcha. I will try to talk about it next time if this topic is interesting to someone.
