Already 2500 online stores mine on visitors' computers
Information security experts are paying attention to the growing popularity of cryptodikeking (cryptojacking) - imperceptible mining of cryptocurrency on the computers of site visitors. You go to a website, the laptop starts to heat up and buzz a little. It's okay, but the owners will get some kind of penny: such a microtransaction.
In such a micropayment business model, there would be nothing reprehensible if it were not for two facts. First, visitors are not notified about mining, so the use of computer computing resources occurs without the knowledge of the owner. Secondly, in the absolute majority of cases, mining occurs, apparently, even without the knowledge of the owners of the site itself.
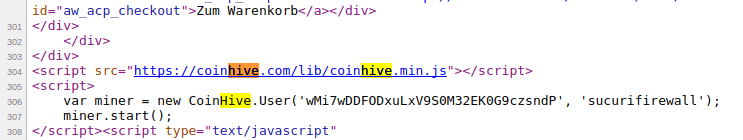
To date, the most popular script for cryptodikeking Coinhive is installed on 2496 e-commerce sites .
As the study by Willem de Grot showed , in 80% of cases, on these sites not only the Coinhive script was installed, but also various malware for skimming - copying the details of bank payment cards of store customers.
Malicious users steal a bank card a little, they also want to remember a little on the computer. Literally squeezed out of the victim to the last penny, more precisely, to the last Monero coin, since Coinhive mines precisely this cryptocurrency.
Among the infected sites there are quite popular resources. For example, the official representative of the automaker Subaru in Australia - shop shop.subaru.com.au .
Willem de Groot found out that most of these 2,496 scripts were installed by only a few intruders. The fact is that each Coinhive user has a unique identifier on which funds are charged. So, 85% of the scripts are associated with only two Coinhive identifiers. The remaining 15% is distributed among a large number of other IDs. However, in this entire group with different link IDs, the site name is the same. That is, it can be assumed that these 15% are also created by one person or group. In other words, all infections of online stores are made by three groups of intruders.
The expert notes that in some cases the crypto miner is well hidden in the code of the pages. Although some sites contain a link to the official file coinhive.jsothers are trying to hide. Here, mining takes place through the built-in frame, which loads the contents of siteverification.online . This site demonstrates the standard installation page for the Debian distribution, but it still contains a crypto liner. Other inline frames load content from a site that impersonates the Sucuri Firewall page.
As has been said before, in order to protect against a crypto miner, you should install a plug-in in your browser to block ads or write down the Coinhive servers in the hosts file.
127.0.0.1 coin-hive.com coinhive.comBut in any case, there is nothing to fear. Cryptodikeking is a completely harmless kind of cybercrime that doesn’t do much harm. Even if you leave the page with the miner open for a whole month, then the electricity bill will increase except for a couple of hundred rubles. Actually, such crypto miners are not much more harmful than animated flash banners, which also do not burden the CPU.
According to Trustwave , the average computer consumes 1212 Wh more electricity than usual per day for the Coinhive script. For a month out 36.36 kWh. According to Moscow tariffs (5.38 rubles / kWh), 195 rubles 62 kopecks are obtained. In principle, not so little, but hardly anyone will leave open the tab with crypto miner for a whole month. And not all electricity rates are as high as in Moscow.
It can be assumed that no one uses the Coinhive service voluntarily. But no, there are still websites that install a miner and even openly report this to users (and give each user the opportunity to choose exactly how many hashes are allowed to be calculated on his processor). But such sites are very few. Most miners are still installed by attackers.
Mining Monero on the Mac Book Air gives about 25 hashes / s Mining on an ordinary desktop computer - about 80 hashes / s smartphone OnePlus 3t - about 12 hashes / s, so a lot of attackers money still will not earn (see. Calculator Mining Monero ), especially since Coinhive takes 30% of the coins.
However, a business can make a good profit if you manage to infect millions of smartphones. Although there the mining speed is several times less, but there is an opportunity to launch it for a long time. Recently, Ixia specialists have found two popular applications with built-in cryptomines in the Google Play directory . They have a total of 6 million to 15 million downloads.
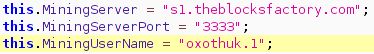
The specialists studied the code of one of the infected applications (“Scanward”) and determined the name of the user to whose account coins are credited in the mining pool (a certain “HUNTER”) and even found some of his messages on the forums. The same developer posted another infected application (English Book) on Google Play, which also has millions of downloads.
