SSH VPN over Internet (SSH tun tunneling)
There was a need to organize a tunnel between your work computer and your home server, with subsequent transport of all work traffic through your home server to the Internet.
To solve this problem, Vitual Private Network (VPN) technology is best suited. But with what help to implement this technology?
- I chose SSH.
The fact is that OpenSSH since version 4.3 supports tun tunneling. I took advantage of this ...
Schematically, it will look as follows:
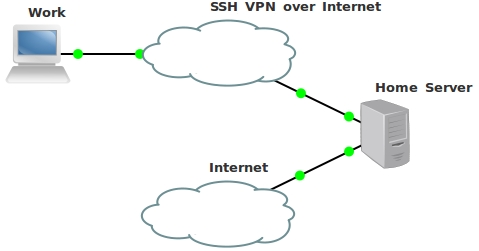
First you need to install OpenSSH on the server. I have Ubuntu Server, and I do it this way: Although, most likely, it is already installed. At me - it is precisely established;) Let's take a look at a more detailed scheme, and discuss it.
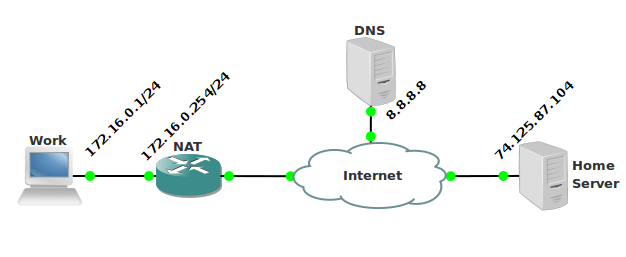
As you can see from the figure, the working computer has IP 172.16.0.1 with a mask of 255.255.255.0 and a default gateway of 172.16.0.254, and IP 8.8.8.8 client routing table (Work) is specified as DNS :
To set up a tunnel, tunneling must be enabled in the OpenSSH configuration file. In
Nuances:
Connecting to the server and creating a tunnel is done using the command
The -w switch will create tun0 devices on the server and client, combining them together.
Here is a description from man. Configure tun devices. On the server On the client You can test using ping (from the client computer):
Now you need to start all traffic through tun0, for this you just need to specify tun0 as the default gateway, but at the same time you will lose connection with the server (Home Server) and the DNS server. Therefore, before deleting the current default gateway (172.16.0.254), it is necessary to add routes to the server and DNS server in the routing table. What can be done as follows: After that, delete the current default gateway (172.16.0.254) and specify as the gateway the IP address that we assigned on the server tun0 interface (10.0.0.1) After performing the above steps, the client routing table (Work) takes the following form :
Now, all traffic that is routed to unknown subnets, and all unknowns except addresses 8.8.8.8 and 74.125.87.104, are routed through 10.0.0.1, that is, through an encrypted SSH tunnel. But the server does nothing with it, traffic. Because you need to configure NAT for the client. To do this, add the rule in iptables. Enable ip forward-ing in the kernel. Do not forget to make it turn on when the system boots ...
Find the commented out line
That's it, mission complete , now all traffic is routed through the ssh tunnel and NATed on the Internet. The tunnel is encrypted, the traffic to the server is protected!
To solve this problem, Vitual Private Network (VPN) technology is best suited. But with what help to implement this technology?
- I chose SSH.
The fact is that OpenSSH since version 4.3 supports tun tunneling. I took advantage of this ...
Schematically, it will look as follows:

First you need to install OpenSSH on the server. I have Ubuntu Server, and I do it this way: Although, most likely, it is already installed. At me - it is precisely established;) Let's take a look at a more detailed scheme, and discuss it.
sudo aptitude install openssh-server

As you can see from the figure, the working computer has IP 172.16.0.1 with a mask of 255.255.255.0 and a default gateway of 172.16.0.254, and IP 8.8.8.8 client routing table (Work) is specified as DNS :
Компьютер Work:
IP address: 172.16.0.1
Netmask: 255.255.255.0
Default Gateway: 172.16.0.254
DNS: 8.8.8.8
172.16.0.0 0.0.0.0 255.255.255.0 U 1 0 0 eth0 169.254.0.0 0.0.0.0 255.255.0.0 U 1000 0 0 eth0 0.0.0.0 172.16.0.254 0.0.0.0 UG 0 0 0 eth0
169.254.0.0 is the zeroconf route.
To set up a tunnel, tunneling must be enabled in the OpenSSH configuration file. In
/etc/ssh/sshd_configyou need to add a line PermitTunnel point-to-pointand restart the OpenSSH serverservice ssh restartNuances:
The fact is that in order to organize a tunnel, you need to log in to the server under the root account, which is not good! Therefore, there are two options for solving the problem:
1. We put on root a complex password like md5 hash.
2. We configure authorization by keys.
Which method to choose is up to you. For the example I am describing, this does not matter.
If you want to use password authentication, enable PermitRootLogin yes in the config so that you can log in as root.
Connecting to the server and creating a tunnel is done using the command
sudo ssh root@74.125.87.104 -w 0:0Be sure to do it through sudo or root. Tun devices will be created, which requires privileges.
The -w switch will create tun0 devices on the server and client, combining them together.
Here is a description from man. Configure tun devices. On the server On the client You can test using ping (from the client computer):
-w local_tun[:remote_tun]
Requests tunnel device forwarding with the specified tun(4) devices between the client (local_tun) and the server(remote_tun)
ifconfig tun0 10.0.0.1/30 pointopoint 10.0.0.2ifconfig tun0 10.0.0.2/30 pointopoint 10.0.0.1 user @ host: ~ $ ping 10.0.0.1 -c 2
PING 10.0.0.1 (10.0.0.1) 56 (84) bytes of data.
64 bytes from 10.0.0.1: icmp_seq = 1 ttl = 64 time = 5.80 ms
64 bytes from 10.0.0.1: icmp_seq = 2 ttl = 64 time = 8.61 ms
--- 10.0.0.1 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min / avg / max / mdev = 5.800 / 7.209 / 8.618 / 1.409 ms
Now you need to start all traffic through tun0, for this you just need to specify tun0 as the default gateway, but at the same time you will lose connection with the server (Home Server) and the DNS server. Therefore, before deleting the current default gateway (172.16.0.254), it is necessary to add routes to the server and DNS server in the routing table. What can be done as follows: After that, delete the current default gateway (172.16.0.254) and specify as the gateway the IP address that we assigned on the server tun0 interface (10.0.0.1) After performing the above steps, the client routing table (Work) takes the following form :
route add -host 74.125.87.104 gw 172.16.0.254
route add -host 8.8.8.8 gw 172.16.0.254
route del default
route add default gw 10.0.0.1
74.125.87.104 172.16.0.254 255.255.255.255 UGH 0 0 0 eth0
8.8.8.8 172.16.0.254 255.255.255.255 UGH 0 0 0 eth0
10.0.0.0 0.0.0.0 255.255.255.252 U 0 0 0 tun0
172.16.0.0 0.0.0.0 255.255.255.0 U 1 0 0 eth0
169.254.0.0 0.0.0.0 255.255.0.0 U 1000 0 0 eth0
0.0.0.0 10.0.0.1 0.0.0.0 UG 0 0 0 tun0
Now, all traffic that is routed to unknown subnets, and all unknowns except addresses 8.8.8.8 and 74.125.87.104, are routed through 10.0.0.1, that is, through an encrypted SSH tunnel. But the server does nothing with it, traffic. Because you need to configure NAT for the client. To do this, add the rule in iptables. Enable ip forward-ing in the kernel. Do not forget to make it turn on when the system boots ...
iptables -t nat -A POSTROUTING -s 10.0.0.2 -j MASQUERADE
sysctl -w net.ipv4.ip_forward=1
mcedit /etc/sysctl.conf
PS> mcedit is a text editor. You can use any other.
Find the commented out line
net.ipv4.ip_forward=1and uncomment it. That's it, mission complete , now all traffic is routed through the ssh tunnel and NATed on the Internet. The tunnel is encrypted, the traffic to the server is protected!
