Spyware quietly turns headphones into a microphone

Schematic diagram of the microphone, headphones and speakers
Information security specialists from the Computer Security Research Center at Ben-Gurion University have developed the spyware program SPEAKE (a) R , which turns the headphone into a microphone unnoticed by the user.
At the hardware level, the microphone and speakers / headphones work on a similar principle. A microphone converts sound into electrical signals, and passive speakers or headphones perform the reverse operation. In both devices there is a small diaphragm that oscillates in a magnetic field to generate / detect sound waves. A similar hardware device allows you to use a microphone instead of headphones or headphones instead of a microphone. This is a well-known fact.long described in professional literature . High-quality speakers record sound even better than cheap Chinese microphones!
To use speakers or headphones as a microphone, simply change the audio jack — insert the headphones into the microphone jack, and vice versa.
The peculiarity of the program SPEAKE (a) R is that it imperceptibly changes the assignment of the audio connector to which the headphones are connected. Instead of audio output (line out), the connector starts working on data reception (line in).
The option to change the functionality of the connector is maintained at the level of the sound card chipset, and it can be activated programmatically. The corresponding option is usually called jack retasking or jack remapping.. For example, such a function exists in Realtek Semiconductor Corp. chipsets, which are integrated into a large number of modern motherboards. Here is a list of Realtek chipsets with support for this feature: ALC892, ALC889, ALC885, ALC888, ALC663, ALC662, ALC268, ALC262, ALC267, ALC272, ALC269, ALC3220. In these chipsets, both audio connectors are connected simultaneously to the ADC and DAC, so that they can work in both modes.
Moreover, a software change in audio assignment is part of the official Intel High Definition Audio specifications .
The option is little known, until today only a small number of developers and specialists knew about it. For example, several years ago I mentioned this feature.In his blog, David Henningson (David Henningsson) is one of the developers of the Linux kernel.
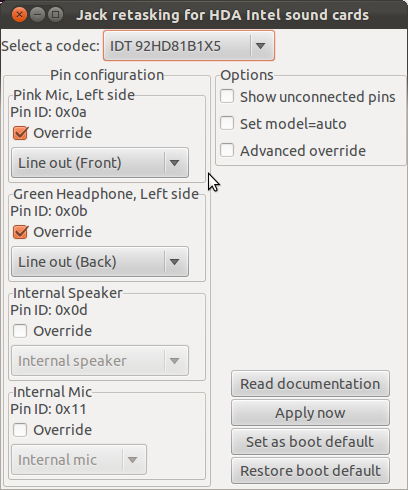
Such a change in functionality was probably made for the convenience of computer assemblers, as well as for the users themselves. Indeed, it is very convenient: you insert a microphone or headphones into any jack without bothering to read the inscriptions or study the color of the connectors (usually the green connector is for speakers, and the pink one is for microphone). If it doesn't work, you just change the connector assignment in the settings, as shown in the screenshot from Ubuntu 11.10.
Five years ago, David Henningson remarked that most of the current integrated cards support plug-in software replacement, but almost no one uses this function and does not even know about it.
There is also a paranoid version that the programmatic change in the functionality of audio connectors was done in secret at the request of the special services. At least, the document of the NSA from 1995 (!) Indicates that the secret services knew and used this method of remote wiretapping ( RED / BLACK INSTALLATION GUIDANCE , technical document of the NSA from 1995).
Threat
The threat is that headphones or speakers are installed on a large number of computers. Many are accustomed to using them without even realizing the possibility of eavesdropping conversations in the room. But the enemy does not necessarily install listening equipment for espionage, if the victim voluntarily uses headphones or speakers on his computer.
Microphones and webcams are not commonly found on every PC, but headphones and speakers are much more common.
In a published scientific paper, the authors published a technical description of the spying program SPEAKE (a) R and showed how it can be used in various situations. They also appreciated the quality of the sound being recorded by the microphone and passive speakers operating in microphone mode.
Chipset manufacturers provide drivers through which the assignment of the audio jack is changed. For example, in the case of the Realtek driver for Windows, this is done by changing the value in the Windows registry .
Here is the corresponding value in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{4D36E96C-E325-11CE-BFC1-08002BE10318}\00XX\Settings\DrvYYYY_DevType_YYYY_SSYYYYYYYY
In Linux, access to the Advanced Linux Sound Architecture (ALSA) is done through a program
hda-jack-retaskthat also changes the assignment of audio connectors. Thus, a spyware program after installation in the system can wiretap the user through headphones using the standard tools of the Windows and Linux operating systems.
Testing has shown that headphones record sound worse than a microphone, but still provide fairly good quality at mid frequencies, at which human speech is heard. In particular, the SAR index for headphones when recording at a distance of 3-5 meters corresponds approximately to the SAR index for a microphone when recording from 9 meters. This is important because the meaning of SAR usually correlates with the ability to distinguish between human speech.

Sound quality values for audio files are obtained using SNReval tools using a standard technique .
To protect against this kind of wiretapping, experts recommend not using microphones, headphones and speakers in workplaces where high security is required, or only allowing active speakers that cannot work in reverse mode to be used. Passive speakers and headphones should be considered as analog microphones with the use of appropriate safety rules. At the program level, you can disable the sound card in the UEFI / BIOS settings.
