Network for small businesses using Cisco equipment. Part 1
Greetings, dear habrozhitel and casual guests. In this series of articles, we will focus on building a simple network for a company that is not too demanding on its IT infrastructure, but at the same time has the need to provide its employees with a high-quality Internet connection, access to shared file resources, and provide employees with VPN access to the workplace and connecting a video surveillance system, access to which would be available from anywhere in the world. For a small business segment, rapid growth and, accordingly, re-planning of the network is very characteristic. In this article, we will start from one office with 15 workplaces and then we will expand the network. So, if any topic is interesting, write in comments, we will try to introduce it into the article. I’ll assume that the reader is familiar with the basics of computer networks,
So, let's begin. Any network begins with a tour of the area and obtaining customer requirements, which will later be formed in the statement of work. Often, the customer himself does not fully understand what he wants and what he needs for this, so he needs to be led to what we can do, but this is more than a sales representative, we will provide the technical part, so we assume that we got such initial requirements:
I will not delve into the selection of a vendor, since this is a question that generates centuries of controversy, we will focus on the fact that the brand has already been decided, this is Cisco.
The core of the network is the router(router). It is important to assess our needs, as in the future we plan to expand the network. Obviously, the purchase of a router with a reserve for this will save money for the customer during expansion, although it will be a little more expensive in the first stage. Cisco for the small business segment offers the Rvxxx series, which presents routers for home offices (RV1xx, most often with a built-in Wi-Fi module), which are designed to connect several workstations and network storage. But they don’t interest us, because they have rather limited VPN capabilities and a fairly low bandwidth. Also, we are not interested in the built-in wireless module, since it is supposed to be placed in a technical room in a rack, Wi-Fi will be organized using AP ( Access Point’s) Our choice will fall on the RV320, which is the youngest model of the older series. We do not need a large number of ports in the built-in switch, since we will have a separate switch in order to provide a sufficient number of ports. Among the main advantages of the router are the rather high throughput of the VPN server (75 Mbit / s), the availability of a license for 10 VPN tunnels, the ability to raise the Site-2-site VPN tunnel. Another important point is the presence of a second WAN port to provide a backup Internet connection.
The router is followed by a switch (switch). The most important switch parameter is the set of functions it possesses. But first, let's count the ports. In our case, we plan to connect to the switch: 17 PCs, 2 APs (Wi-Fi access points), 8 IP cameras, 1 NAS, 3 network printers. Using arithmetic, we get the number 31, which corresponds to the number of devices that are initially connected to the network, add 2 uplinks to this (we plan to expand the network) and stop at 48 ports. Now about the functionality: our switch must be able to VLAN , preferably all 4096, SFP mines will not interfere , since it will be possible to connect the switch to the other end of the building using optics, it must be able to work in a vicious circle, which allows us to reserve links ( STP-Spanning Tree protocol), also APs and cameras will be powered through a twisted pair cable, so PoE is required (you can read more about the protocols in the wiki, the names are clickable). We do not need too complex L3 functionality, so our choice will be on the Cisco SG250-50P, since it has enough functionality for us and at the same time does not include redundant functions. We will talk about Wi-Fi in the next article, since this is a rather extensive topic. There we dwell on the choice of AR. We do not choose NAS and cameras, we assume that other people are doing this, but we are only interested in the network.
To begin with, we will determine what virtual networks we need (what virtual VLANs can be found on Wikipedia). So, we have several logical network segments:
Also, according to the rules of good form, we will transfer the device management interface to a separate VLAN. You can number VLANs in any order, I will choose this:
Next, we will make an IP plan, we will use a 24-bit mask and a 192.168.x.x subnet. Let's get started.
The redundant pool will contain addresses that will be configured statically (printers, servers, management interfaces, etc., a dynamic address will be issued for DHCP clients ).
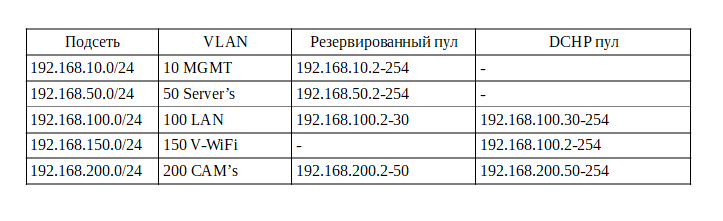
So we figured IP, there are a couple of points that I would like to pay attention to:
Well, finally, let's move on to setting up. We take a patch cord and connect to one of the four LAN ports of the router. By default, a DHCP server is enabled on the router and it is available at 192.168.1.1. You can check this with the ipconfig console utility, in the output of which our router will be the default gateway. Check:

In the browser, go to this address, confirm the unsafe connection and log in with the username / password cisco / cisco. Immediately change the password to secure. And first of all we go to the Setup tab, the Network section, here we assign the name and domain name for the router

Now we will add VLANs to our router. Go to Port Management / VLAN Membership. We will be greeted by the default VLAN-ok label
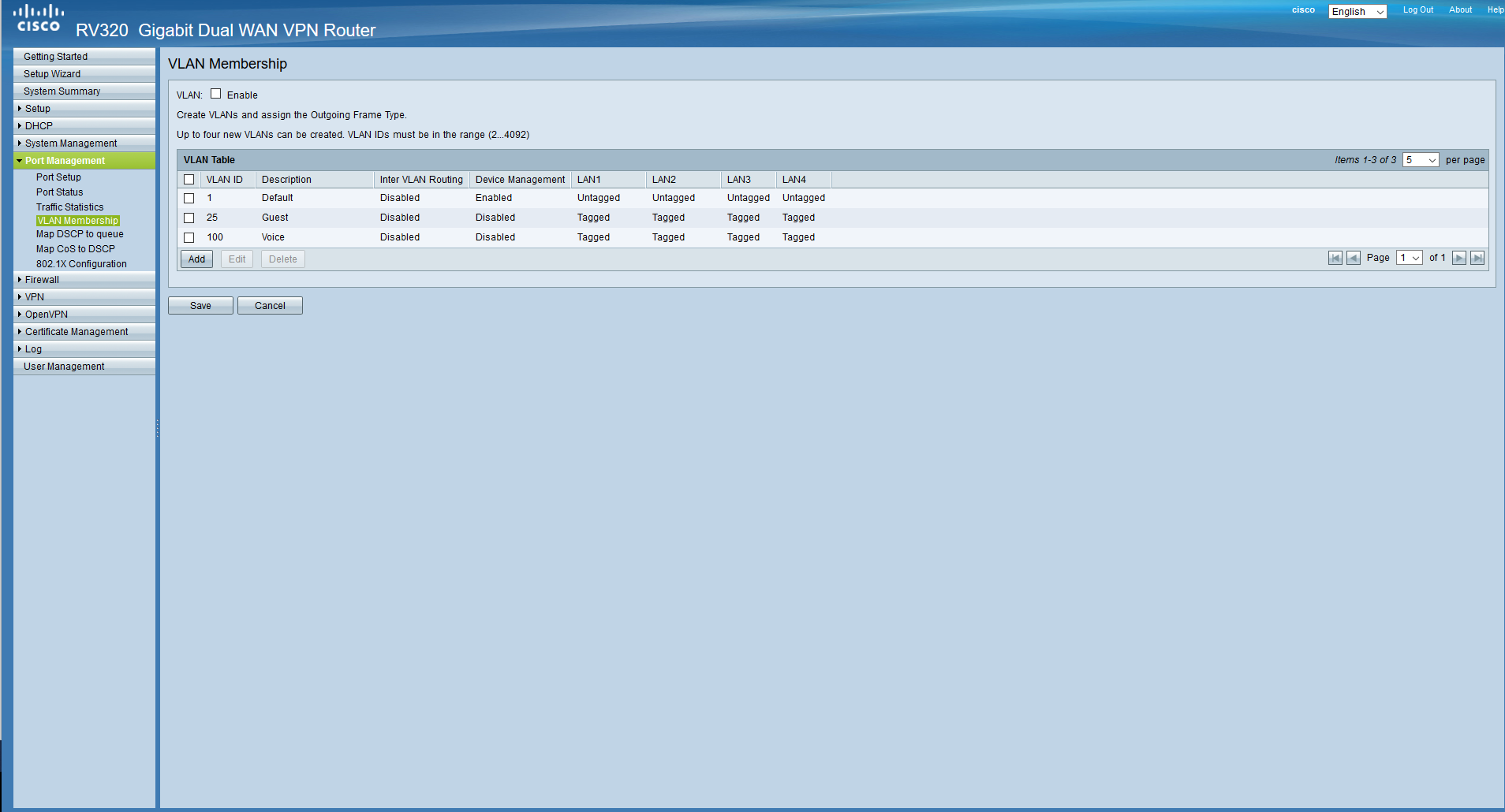
We do not need them, we will delete everything except the first one, since it is defaulted and cannot be deleted, we will immediately add the VLANs that we planned. Do not forget to check the box at the top. Also, device management is allowed only from the management network, and routing between networks is allowed everywhere except for the guest network. We will configure the ports a bit later.
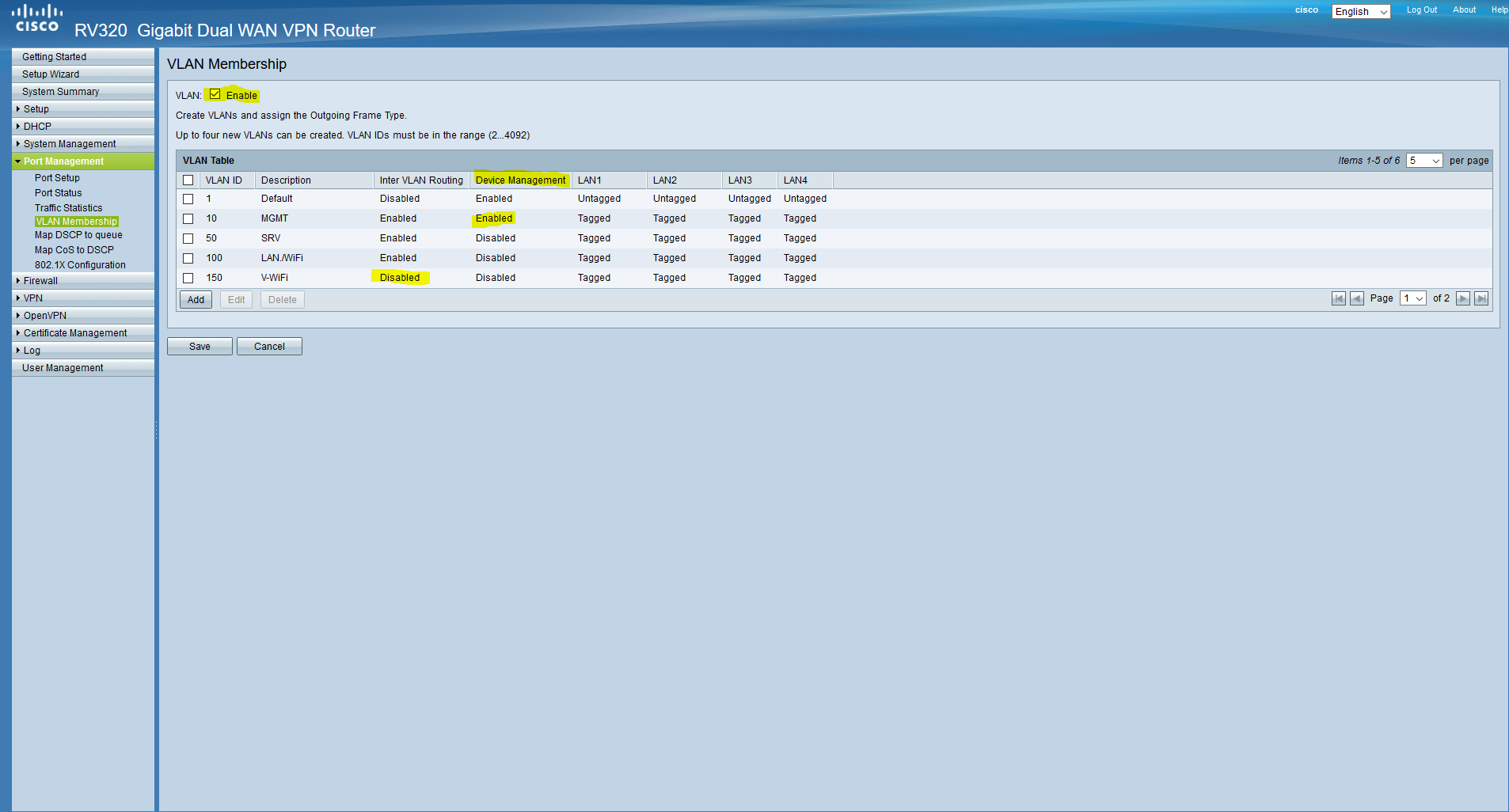
Now configure the DHCP server according to our table. To do this, go to DHCP / DHCP Setup.
For networks in which DHCP will be disabled, configure only the gateway address, which will be the first in the subnet (respectively, the mask).

In networks with DHCP, everything is quite simple, we also configure the gateway address, and below we specify the pools and DNS-ki:
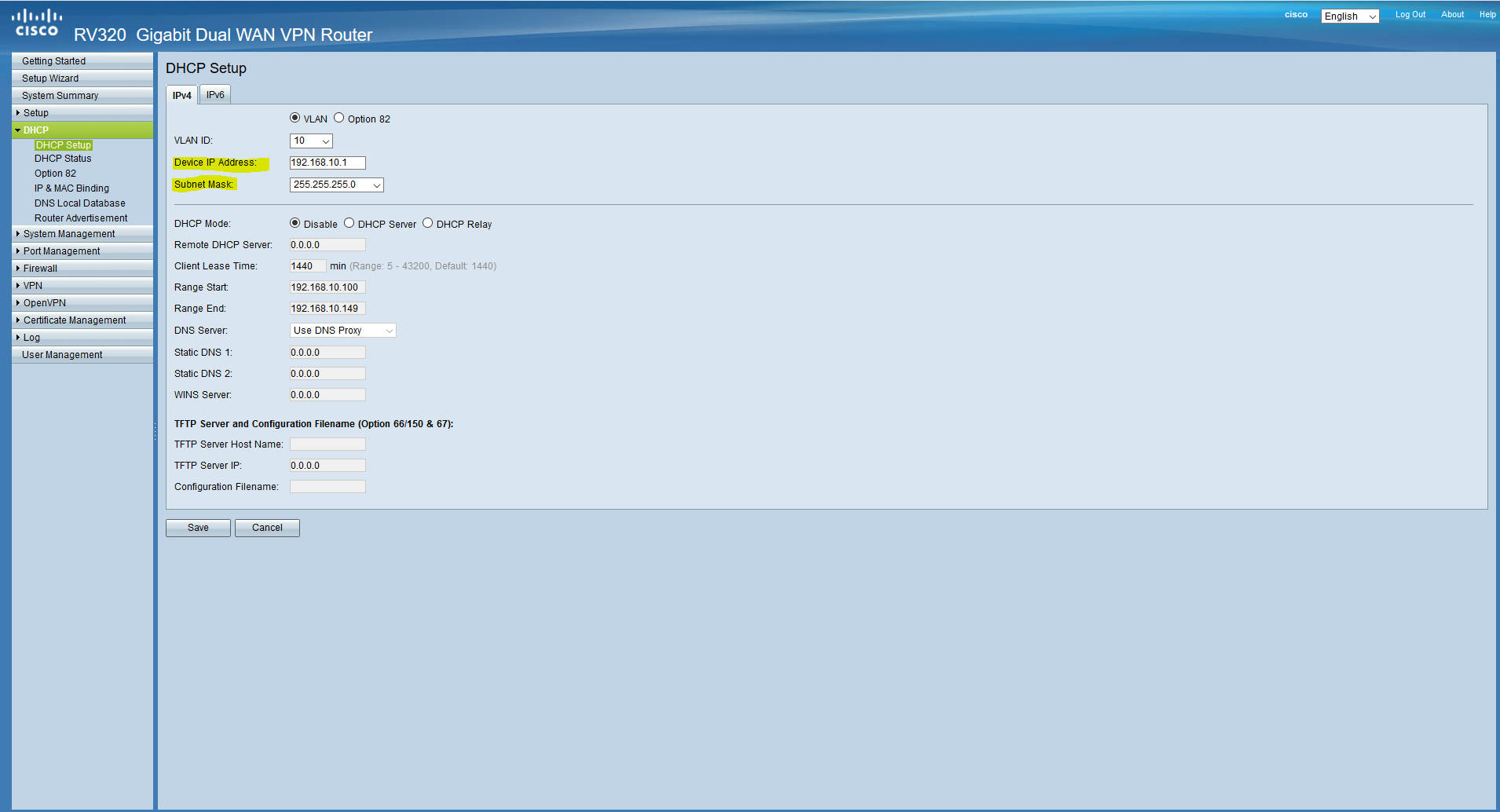
We figured this out with DHCP, now clients connected to the local network will receive the address automatically. Now we will configure the ports (the ports are configured according to the 802.1q standard , the link is clickable, you can familiarize yourself with it). Since it is assumed that all clients will be connected via managed switches of an untagged (native) VLAN, MGMT will be on all ports, this means that any device connected to this port will get into this network (more details here). Go back to the Port Management / VLAN Membership and configure it. We leave VLAN1 on all ports Excluded, we do not need it.

Now, on our network card, we need to configure a static address from the management subnet, since we got into this subnet after clicking “save”, and the DHCP server is not here. We go to the settings of the network adapter and configure the address. After that, the router will be available at the address 192.168.10.1.

Configure our connection to the Internet. Suppose we got a static address from a provider. Go to Setup / Network, mark WAN1 below, click Edit. Select Static IP and configure your address.

And the last for today - we configure remote access. To do this, go to Firewall / General and check the Remote Management checkbox, configure the port as necessary

That's probably all for today. As a result of the article, we have a basic configured router with which we can access the Internet. The volume of the article is more than I expected, so in the next part we will finish configuring the router, raise the VPN-ku, configure the firewall and logging, and configure the switch and will already be able to start our office. I hope that the article was at least a little useful and informative for you. I am writing for the first time, I will be very happy with constructive criticism and questions, I will try to answer everyone and take into account your comments. Also, as I wrote at the beginning, your thoughts are welcomed about what else might appear in the office and what else we will configure.
My contacts:
Telegram: hebelz
Skype / mail: kashuba@antik.sk
Add, talk.
So, let's begin. Any network begins with a tour of the area and obtaining customer requirements, which will later be formed in the statement of work. Often, the customer himself does not fully understand what he wants and what he needs for this, so he needs to be led to what we can do, but this is more than a sales representative, we will provide the technical part, so we assume that we got such initial requirements:
- 17 jobs for desktop PCs
- Network Attached Storage ( NAS )
- Surveillance system using NVR and IP cameras (8 pieces)
- Wi-Fi office coverage, the presence of two networks (internal and guest)
- You can add network printers (up to 3 pieces)
- The prospect of opening a second office on the other side of the city
Equipment selection
I will not delve into the selection of a vendor, since this is a question that generates centuries of controversy, we will focus on the fact that the brand has already been decided, this is Cisco.
The core of the network is the router(router). It is important to assess our needs, as in the future we plan to expand the network. Obviously, the purchase of a router with a reserve for this will save money for the customer during expansion, although it will be a little more expensive in the first stage. Cisco for the small business segment offers the Rvxxx series, which presents routers for home offices (RV1xx, most often with a built-in Wi-Fi module), which are designed to connect several workstations and network storage. But they don’t interest us, because they have rather limited VPN capabilities and a fairly low bandwidth. Also, we are not interested in the built-in wireless module, since it is supposed to be placed in a technical room in a rack, Wi-Fi will be organized using AP ( Access Point’s) Our choice will fall on the RV320, which is the youngest model of the older series. We do not need a large number of ports in the built-in switch, since we will have a separate switch in order to provide a sufficient number of ports. Among the main advantages of the router are the rather high throughput of the VPN server (75 Mbit / s), the availability of a license for 10 VPN tunnels, the ability to raise the Site-2-site VPN tunnel. Another important point is the presence of a second WAN port to provide a backup Internet connection.
The router is followed by a switch (switch). The most important switch parameter is the set of functions it possesses. But first, let's count the ports. In our case, we plan to connect to the switch: 17 PCs, 2 APs (Wi-Fi access points), 8 IP cameras, 1 NAS, 3 network printers. Using arithmetic, we get the number 31, which corresponds to the number of devices that are initially connected to the network, add 2 uplinks to this (we plan to expand the network) and stop at 48 ports. Now about the functionality: our switch must be able to VLAN , preferably all 4096, SFP mines will not interfere , since it will be possible to connect the switch to the other end of the building using optics, it must be able to work in a vicious circle, which allows us to reserve links ( STP-Spanning Tree protocol), also APs and cameras will be powered through a twisted pair cable, so PoE is required (you can read more about the protocols in the wiki, the names are clickable). We do not need too complex L3 functionality, so our choice will be on the Cisco SG250-50P, since it has enough functionality for us and at the same time does not include redundant functions. We will talk about Wi-Fi in the next article, since this is a rather extensive topic. There we dwell on the choice of AR. We do not choose NAS and cameras, we assume that other people are doing this, but we are only interested in the network.
Planning
To begin with, we will determine what virtual networks we need (what virtual VLANs can be found on Wikipedia). So, we have several logical network segments:
- Client Workstations (PCs)
- Server (NAS)
- CCTV
- Guest devices (WiFi)
Also, according to the rules of good form, we will transfer the device management interface to a separate VLAN. You can number VLANs in any order, I will choose this:
- VLAN10 Management (MGMT)
- VLAN50 Server's
- VLAN100 LAN + WiFi
- VLAN150 Visitor's WiFI (V-WiFi)
- VLAN200 CAM's
Next, we will make an IP plan, we will use a 24-bit mask and a 192.168.x.x subnet. Let's get started.
The redundant pool will contain addresses that will be configured statically (printers, servers, management interfaces, etc., a dynamic address will be issued for DHCP clients ).

So we figured IP, there are a couple of points that I would like to pay attention to:
- In the management network, it makes no sense to raise DHCP, exactly the same as in the server network, since all addresses are assigned manually when configuring the equipment. Some leave a small DHCP pool in case of connecting new equipment for its initial configuration, but I'm used to it and I advise you to configure the equipment not at the customer, but on your desk, so I don’t do this pool here.
- Some camera models may require a static address, but we assume that cameras receive it automatically.
- In the local network, we leave the pool for printers, since the network printing service does not work reliably with dynamic addresses.
Router setup
Well, finally, let's move on to setting up. We take a patch cord and connect to one of the four LAN ports of the router. By default, a DHCP server is enabled on the router and it is available at 192.168.1.1. You can check this with the ipconfig console utility, in the output of which our router will be the default gateway. Check:

In the browser, go to this address, confirm the unsafe connection and log in with the username / password cisco / cisco. Immediately change the password to secure. And first of all we go to the Setup tab, the Network section, here we assign the name and domain name for the router

Now we will add VLANs to our router. Go to Port Management / VLAN Membership. We will be greeted by the default VLAN-ok label

We do not need them, we will delete everything except the first one, since it is defaulted and cannot be deleted, we will immediately add the VLANs that we planned. Do not forget to check the box at the top. Also, device management is allowed only from the management network, and routing between networks is allowed everywhere except for the guest network. We will configure the ports a bit later.

Now configure the DHCP server according to our table. To do this, go to DHCP / DHCP Setup.
For networks in which DHCP will be disabled, configure only the gateway address, which will be the first in the subnet (respectively, the mask).

In networks with DHCP, everything is quite simple, we also configure the gateway address, and below we specify the pools and DNS-ki:

We figured this out with DHCP, now clients connected to the local network will receive the address automatically. Now we will configure the ports (the ports are configured according to the 802.1q standard , the link is clickable, you can familiarize yourself with it). Since it is assumed that all clients will be connected via managed switches of an untagged (native) VLAN, MGMT will be on all ports, this means that any device connected to this port will get into this network (more details here). Go back to the Port Management / VLAN Membership and configure it. We leave VLAN1 on all ports Excluded, we do not need it.

Now, on our network card, we need to configure a static address from the management subnet, since we got into this subnet after clicking “save”, and the DHCP server is not here. We go to the settings of the network adapter and configure the address. After that, the router will be available at the address 192.168.10.1.

Configure our connection to the Internet. Suppose we got a static address from a provider. Go to Setup / Network, mark WAN1 below, click Edit. Select Static IP and configure your address.

And the last for today - we configure remote access. To do this, go to Firewall / General and check the Remote Management checkbox, configure the port as necessary

That's probably all for today. As a result of the article, we have a basic configured router with which we can access the Internet. The volume of the article is more than I expected, so in the next part we will finish configuring the router, raise the VPN-ku, configure the firewall and logging, and configure the switch and will already be able to start our office. I hope that the article was at least a little useful and informative for you. I am writing for the first time, I will be very happy with constructive criticism and questions, I will try to answer everyone and take into account your comments. Also, as I wrote at the beginning, your thoughts are welcomed about what else might appear in the office and what else we will configure.
My contacts:
Telegram: hebelz
Skype / mail: kashuba@antik.sk
Add, talk.
