Security Week 24: factory backdoors on Android smartphones
 Last week was rich in news about the security of Android smartphones. Many media outlets (for example, ArsTechnica ) wrote that Google “confirmed” the fact of selling smartphones with a backdoor pre-installed “at the factory”. The reason for such headlines was a completely technical article by Google expert Lukasz Siverski with an analysis of the Triada family of mobile malware.
Last week was rich in news about the security of Android smartphones. Many media outlets (for example, ArsTechnica ) wrote that Google “confirmed” the fact of selling smartphones with a backdoor pre-installed “at the factory”. The reason for such headlines was a completely technical article by Google expert Lukasz Siverski with an analysis of the Triada family of mobile malware. Triada has been known to researchers (including, of course, the Google team) since 2016. For the first time, a backdoor was described by Kaspersky Lab experts ( here and here) These two materials detail the introduction of malicious code into the operating system (as early as Android 4.x), the collection and sending of user data, and the modification of several browsers to display banner ads.
What is really interesting in the post of the representative of the Android Security Team is the answer to the question of exactly how the malicious code got into the firmware of the phones. Developers of Chinese budget devices have contacted contractors to develop additional features. Through such a contractor, a backdoor was built into the system.
A 2016 Kaspersky Lab study describes the Triada variant, which could be preinstalled on phones from Chinese manufacturers, but was also able to attack any other smartphones. Triada exploited vulnerabilities in the current version of Android 4.x. A unique feature of the backdoor was the ability to integrate into a key Android process known as Zygote.
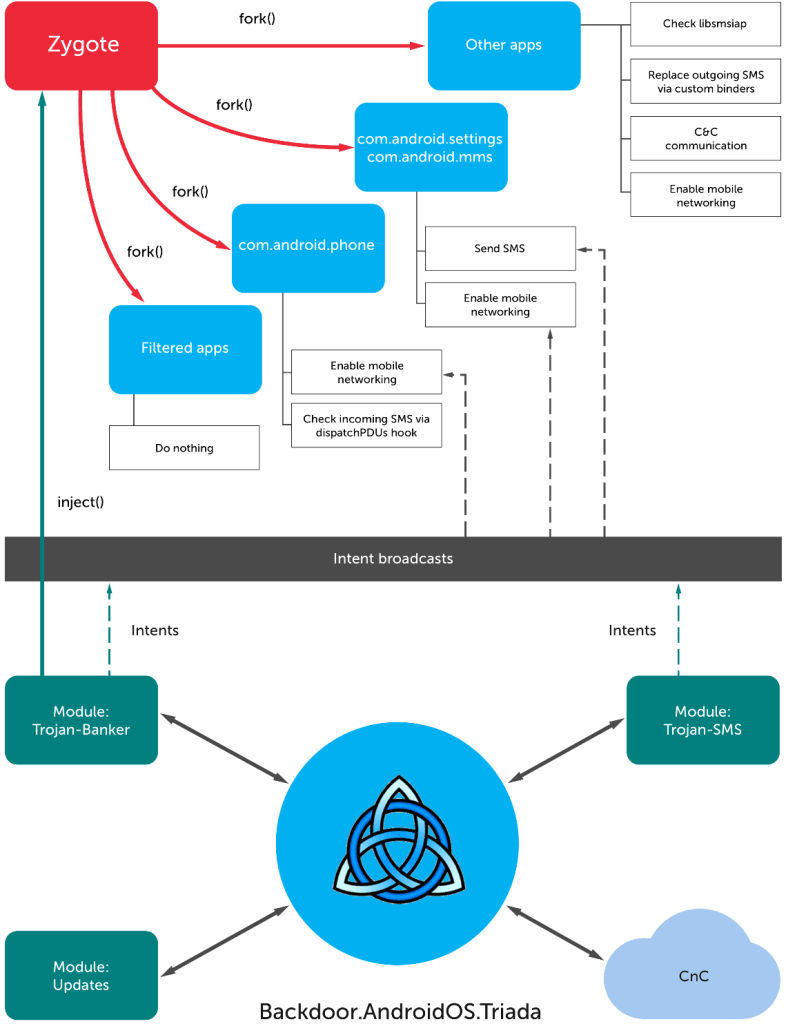
This approach provided the Trojan with almost complete control over the device. An article from the Android Security Team details one more detail: Triada used a modified su binary to gain control over system processes. He gave applications superuser privileges only if they made a request with the correct password.
Also, in a post by Lukasz Siverski, it tells how the backdoor tracked which application the user opened. If it was a browser, advertisements were displayed on top of it. If the Google Play store opened, Triada in the background downloaded and installed applications from its own command server.
In 2017, Dr.Web in its studygave examples of smartphones infected with the factory backdoor: Leagoo M5 Plus, Leagoo M8, Nomu S10 and S20. Inexpensive (about $ 100) devices were sold in both China and the West, some of which can still be found in Chinese online stores.

In a recent article, Google reveals a scheme for implementing the “factory" version of Triada (see image above). Apparently, smartphone providers turned to third-party companies to include additional functionality in the device’s firmware that was not available in the Android Open Source project. For this, a system image was sent to the contractor (mentioned by Yehuo and Blazefire). He returned with an appendage - both legitimate (unlocking in the face of the owner) and malicious. Google reported that, together with device developers, they removed the backdoor traces from the firmware.
But, apparently, only this backdoor. Representatives of the Information Security Administration (BSI) of Germany reported on June 7 ( news) about the discovery of the Xgen2-CY backdoor in four budget smartphones. Doogee BL7000, M-Horse Pure 1, Keecoo P11 and VKworld Mix Plus models collect user information and send it to the command server, they are able to install applications and open pages in a browser without the user's knowledge. Only for the Keecoo P11 model (5.7 inches, 4 cores, 2 gigabytes of memory, $ 110 on GearBest) an updated version of the firmware without a backdoor is available. According to BSI, up to 20 thousand devices access C & C-servers of attackers from German IP.
In general, the problem is not completely resolved, and the recommendation for consumers will probably be this: think twice before buying a cheap smartphone of a dubious brand. Last July, we cited an article by Motherboard that describedpenny replica iPhone X from China. The device sent user information right and left. Such crafts usually do not fall outside of China, but some “international” devices are no better. While we are discussing privacy issues and the practice of collecting user data by all market participants, tens of thousands of people around the world are becoming victims of outright cybercriminals.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend treating any opinions with healthy skepticism.
