How car sharing service works and works
Currently, car-sharing services are rapidly gaining momentum and even capture regions. Someone refused a personal car in favor of a car-sharing, while someone still bypasses these cars. Let's try to figure out what kind of a foreign word it is, which everyone is already hearing, how the car sharing service works and how it functions?

As an example, take a certain car sharing service “N” and consider the interaction of all the components of this complex mechanism.

All cars are displayed on the map in real time, both at the client and at the call center operator. In order for the information to be constantly updated and updated, the server “polls” machines with a specific timeout. The operator sees the entire fleet in CRM and can control absolutely any car, regardless of whether this car is in the current lease or in the “free” status. In the screenshot below - an example of CRM:

Just click on the car and an instant dialog box with management capabilities opens:
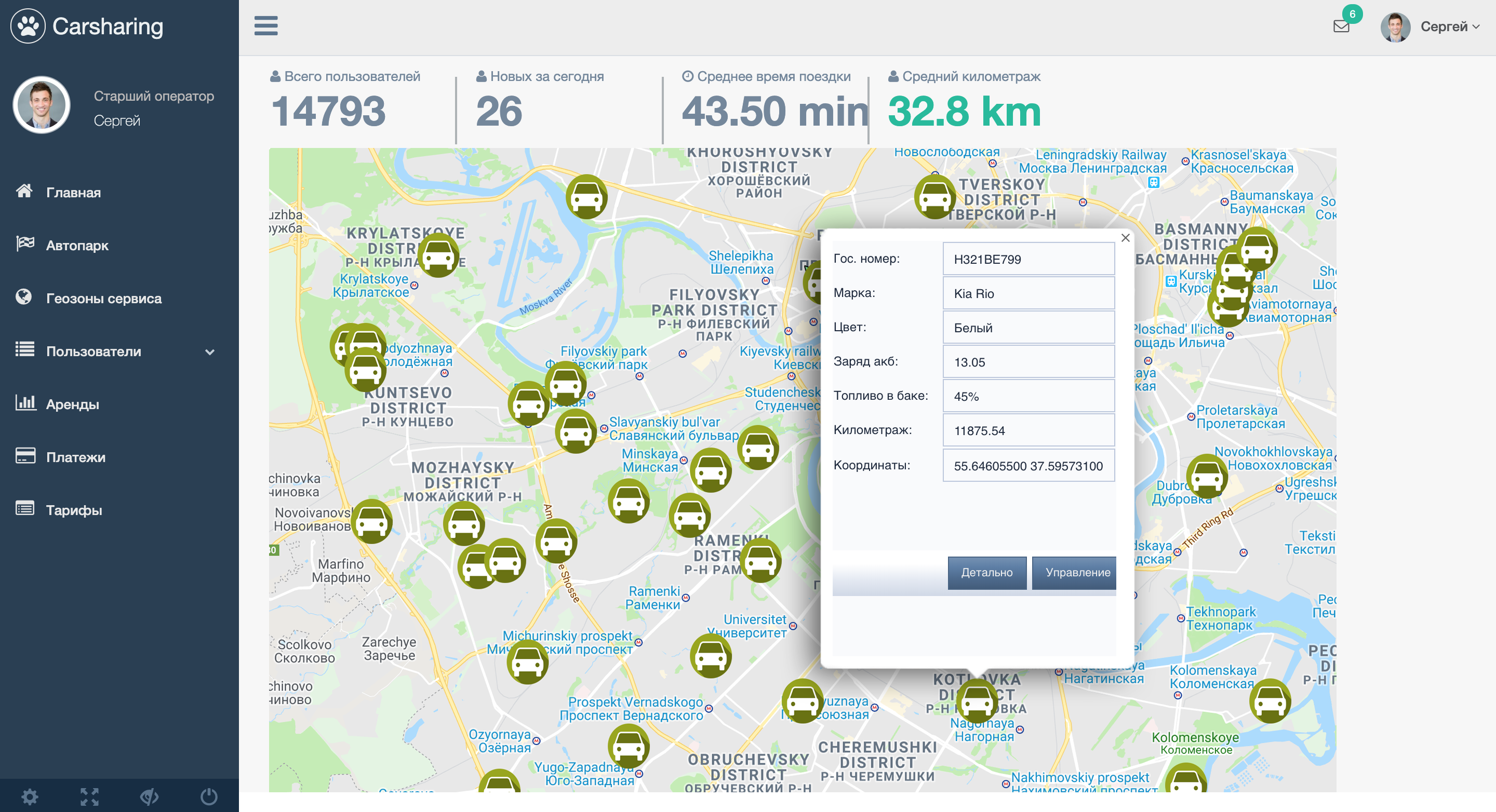
For CRM users, the following options are available (the set of options depends on the configuration and modification of the telematics equipment installed in it):
- remote door lock / unlock;
- remote engine lock / unlock;
- opening the window of the car;
- remote autostart of the car;
- control the sound signal of the car.
Service geofence - the area indicated on the map, within which a specific car-sharing provider operates. That is, within this zone, the operator guarantees that the client application and telematic equipment will work correctly. How is tracking that the car left the geofence?
Everything is very simple! Geofence - a polygon of points. A certain specified area (in the screenshot below is the city of Perm). He left the car in the geofence or vice versa returned - it is determined by the Latitude & Longitude coordinates entering the specific area. It looks something like this:
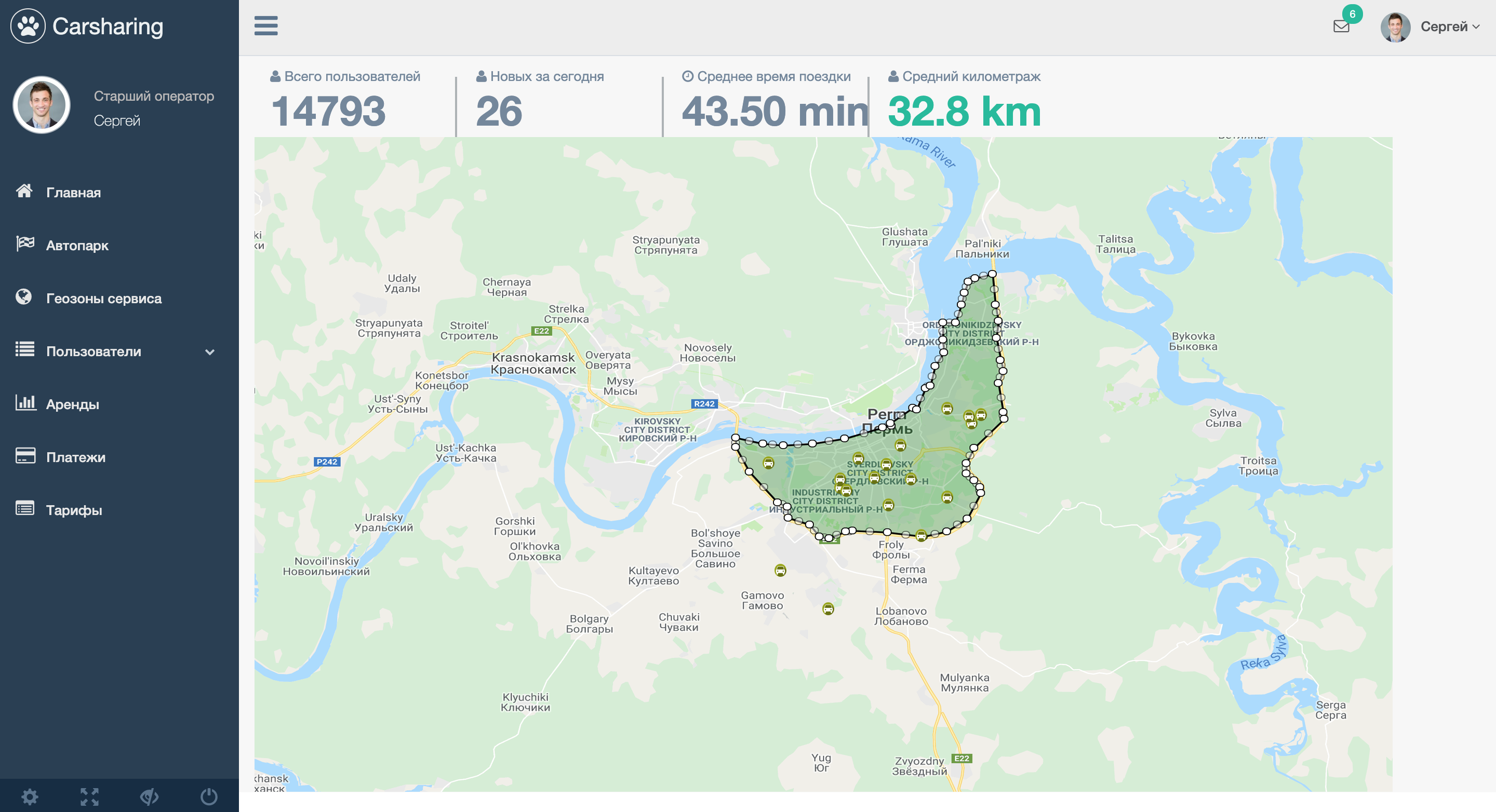
Many car sharing operators have established a rule - travel outside the geofence must be agreed with the call center operator. Completing a lease outside the zone is prohibited, or even limited at the program level.
In order for the car to be able to be controlled remotely, special telematics equipment is connected via the CAN bus, as shown below:

The device looks like a normal satellite alarm that car owners install on their personal cars. The built-in CAN transceiver serves to interact with the vehicle network, allowing you to request data on the remaining fuel, the condition of the nodes, receive data on doors, hood, trunk, engine and other information. Data, in turn, is transmitted through regular 3G / 4G networks. Each device has an average of two SIM cards that make the signal for transmitting telematic data more stable. Conventional equipment is installed behind the dashboard and is hidden from the user. In fact, this is the "brain" of a car sharing car.
The interaction of the machine with the server occurs at the software level. Data packets are transferred from telematics equipment to the server and vice versa.
During each of the “polls” of the machine, approximately the following information comes from telematics equipment:
From this example of a response from a car, we see that absolutely all information on the current state of the car is transmitted: sensors, location, door statuses, etc. Where does this information come from and what kind of device transmits it?
An ordinary user to use the car sharing service uses a special mobile application issued by a particular operator to access the fleet. However, often in the news, in various Telegram channels we hear about fake accounts. In the screenshot below is an example of one of the Telegram channels where anyone can buy an account:

The principle of registering fake accounts is simple! The data necessary for registration (passport, driver's license), the attackers take from various sources. Sometimes the “victims” themselves transmit their data. After receiving the data, the attackers register an account, the security service of the car-sharing operator approves this account and then puts it up for sale. Riding under such an account is a criminal offense. Security services actively monitor almost every current trip.
The second way that cybercriminals use to register an account is to exploit software vulnerabilities. So relatively recently the user database of the car-sharing operator TimCar was stolen. And just the other day - to gain access to the account of one of the metropolitan operators, it was not even necessary to enter a confirmation code, which comes via SMS. The operator’s server itself sent it to the client in response to a request:
By entering the code from the "veryfy_code" field, we could easily enter the victim’s account, knowing only the phone number.
I think that this article will help ordinary users understand the basic principles of the short-term car rental services. And also answer many questions that were previously incomprehensible.

As an example, take a certain car sharing service “N” and consider the interaction of all the components of this complex mechanism.

Remote fleet management as it happens through the operator’s CRM
All cars are displayed on the map in real time, both at the client and at the call center operator. In order for the information to be constantly updated and updated, the server “polls” machines with a specific timeout. The operator sees the entire fleet in CRM and can control absolutely any car, regardless of whether this car is in the current lease or in the “free” status. In the screenshot below - an example of CRM:

Just click on the car and an instant dialog box with management capabilities opens:

For CRM users, the following options are available (the set of options depends on the configuration and modification of the telematics equipment installed in it):
- remote door lock / unlock;
- remote engine lock / unlock;
- opening the window of the car;
- remote autostart of the car;
- control the sound signal of the car.
Service Geofences
Service geofence - the area indicated on the map, within which a specific car-sharing provider operates. That is, within this zone, the operator guarantees that the client application and telematic equipment will work correctly. How is tracking that the car left the geofence?
Everything is very simple! Geofence - a polygon of points. A certain specified area (in the screenshot below is the city of Perm). He left the car in the geofence or vice versa returned - it is determined by the Latitude & Longitude coordinates entering the specific area. It looks something like this:

Many car sharing operators have established a rule - travel outside the geofence must be agreed with the call center operator. Completing a lease outside the zone is prohibited, or even limited at the program level.
Secret equipment
In order for the car to be able to be controlled remotely, special telematics equipment is connected via the CAN bus, as shown below:

The device looks like a normal satellite alarm that car owners install on their personal cars. The built-in CAN transceiver serves to interact with the vehicle network, allowing you to request data on the remaining fuel, the condition of the nodes, receive data on doors, hood, trunk, engine and other information. Data, in turn, is transmitted through regular 3G / 4G networks. Each device has an average of two SIM cards that make the signal for transmitting telematic data more stable. Conventional equipment is installed behind the dashboard and is hidden from the user. In fact, this is the "brain" of a car sharing car.
Machine-server interaction
The interaction of the machine with the server occurs at the software level. Data packets are transferred from telematics equipment to the server and vice versa.
During each of the “polls” of the machine, approximately the following information comes from telematics equipment:
{
"success": true,
"total": "1",
"car": [
{
"date": "2019-03-01 12:00:19.306955",
"id": "124",
"id_category": "2",
"id_emi": "295",
"id_status": "9",
"vendor": "Kia Rio",
"marka": "",
"year": "",
"id_modification": "",
"vin": "WF0DXXGTB60052135",
"numberplate": "У111ЕУ799",
"color": "",
"descr": "",
"emi": "580855023425759",
"data_fuel": "50",
"data_voltage": "12.6400000000000000",
"fuel_by_can": "1",
"onoffdirect": "1",
"insurance_card": null,
"id_typefuel": "1",
"name_typefuel": "АИ-95",
"id_typetransmission": "1",
"name_typetransmission": "АКПП",
"is_agg_car": null,
"odometer": "22471",
"clat": "55.61313000",
"clng": "37.61698000",
"plat": "55.61321100",
"plng": "37.61700000",
"doors": [
"0"
],
"sensor": [
"0",
"0",
"0",
"0",
"0",
"0"
]
}
]
}
From this example of a response from a car, we see that absolutely all information on the current state of the car is transmitted: sensors, location, door statuses, etc. Where does this information come from and what kind of device transmits it?
Client-server interaction
An ordinary user to use the car sharing service uses a special mobile application issued by a particular operator to access the fleet. However, often in the news, in various Telegram channels we hear about fake accounts. In the screenshot below is an example of one of the Telegram channels where anyone can buy an account:

The principle of registering fake accounts is simple! The data necessary for registration (passport, driver's license), the attackers take from various sources. Sometimes the “victims” themselves transmit their data. After receiving the data, the attackers register an account, the security service of the car-sharing operator approves this account and then puts it up for sale. Riding under such an account is a criminal offense. Security services actively monitor almost every current trip.
The second way that cybercriminals use to register an account is to exploit software vulnerabilities. So relatively recently the user database of the car-sharing operator TimCar was stolen. And just the other day - to gain access to the account of one of the metropolitan operators, it was not even necessary to enter a confirmation code, which comes via SMS. The operator’s server itself sent it to the client in response to a request:
{
"success": 1,
"return": {
"veryfy_code": 3634,
"sms_id": "201907-1000009"
}
}
By entering the code from the "veryfy_code" field, we could easily enter the victim’s account, knowing only the phone number.
I think that this article will help ordinary users understand the basic principles of the short-term car rental services. And also answer many questions that were previously incomprehensible.
