The most expensive mistake in my life: details about the attack on the SIM card port
Hello, Habr! I present to you the translation of the article “The Most Expensive Lesson Of My Life: Details of SIM port hack” by Sean Coonce.
Last Wednesday, I lost over $ 100,000. The money evaporated within 24 hours as a result of the “attack on the SIM card port”, which cleared my Coinbase account. Four days have passed since then, and I am devastated. I have no appetite; I can not fall asleep; I am filled with feelings of anxiety, conscience and shame.
It was the most expensive lesson in my life, and I want to share experiences and lessons learned with as many people as possible. My goal is to increase people's awareness of these types of attacks and motivate you to enhance the security of your online identity.
It's still very damp (I still haven't told my family about this); please keep your condemnation of the naive security practices described in this post.
You may ask: “What kind of attack is this on the SIM card port?” To describe the attack, let's first look at a typical online identity. The chart below should be familiar to most of you.
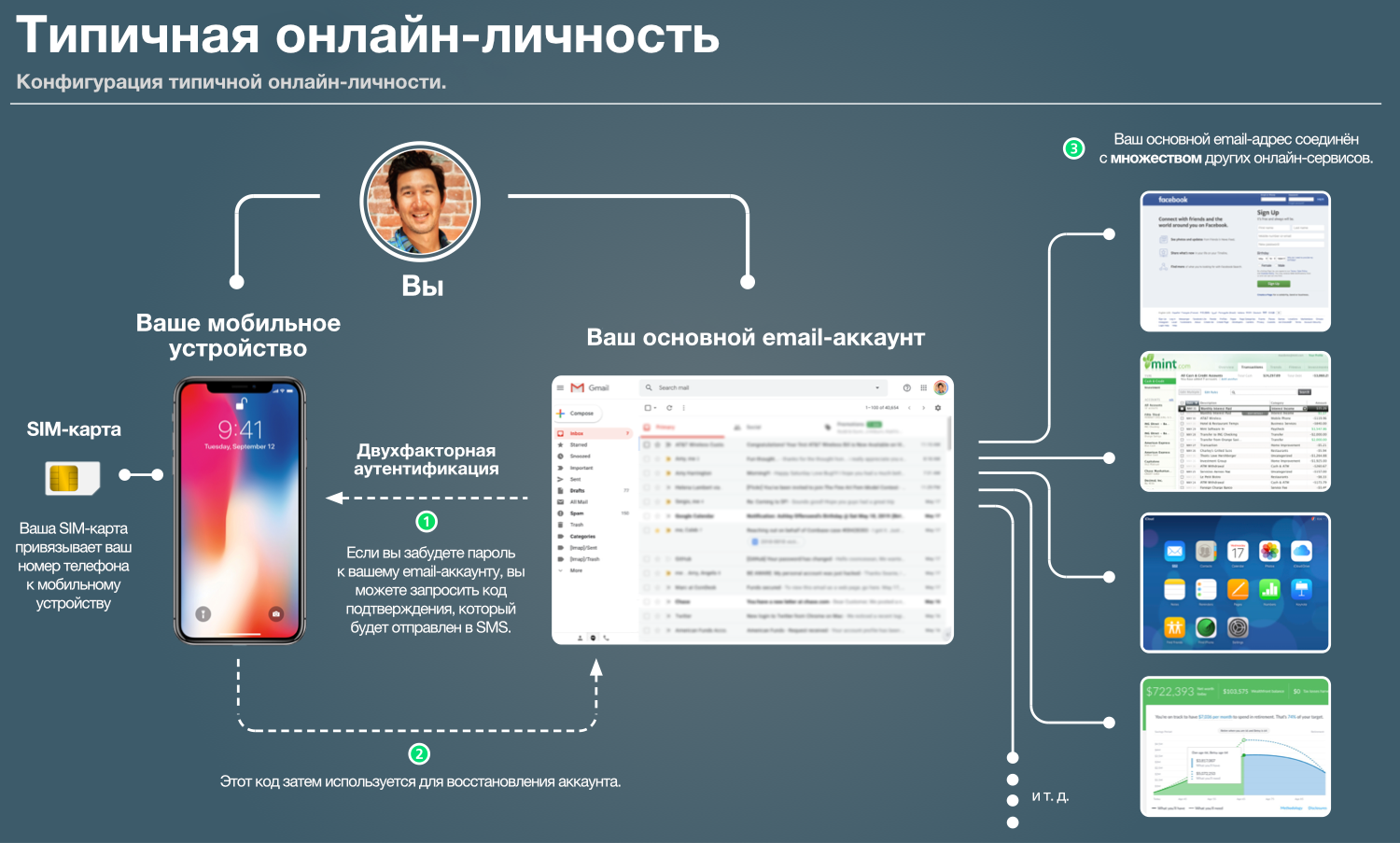
Many of us have a primary email address that is connected to a HUGE amount of other online accounts. Many of us also have a mobile device that can be used to recover a forgotten email password.
One of the services that telecom operators offer customers is the ability to port a SIM card to another device. This allows the client to request the transfer of their phone number to the new device. In most cases, this is an absolutely legal process; this happens when we buy a new phone, change the operator, etc.
However, an “attack on the SIM card port” is a malicious port, produced from an unauthorized source - by an attacker. The attacker will port your SIM card to a phone controlled by him. Then the attacker begins the process of resetting the password on the email account. A confirmation code is sent to your phone number and is intercepted by the attacker, since he now controls your SIM card. The diagram below shows the attack step by step.
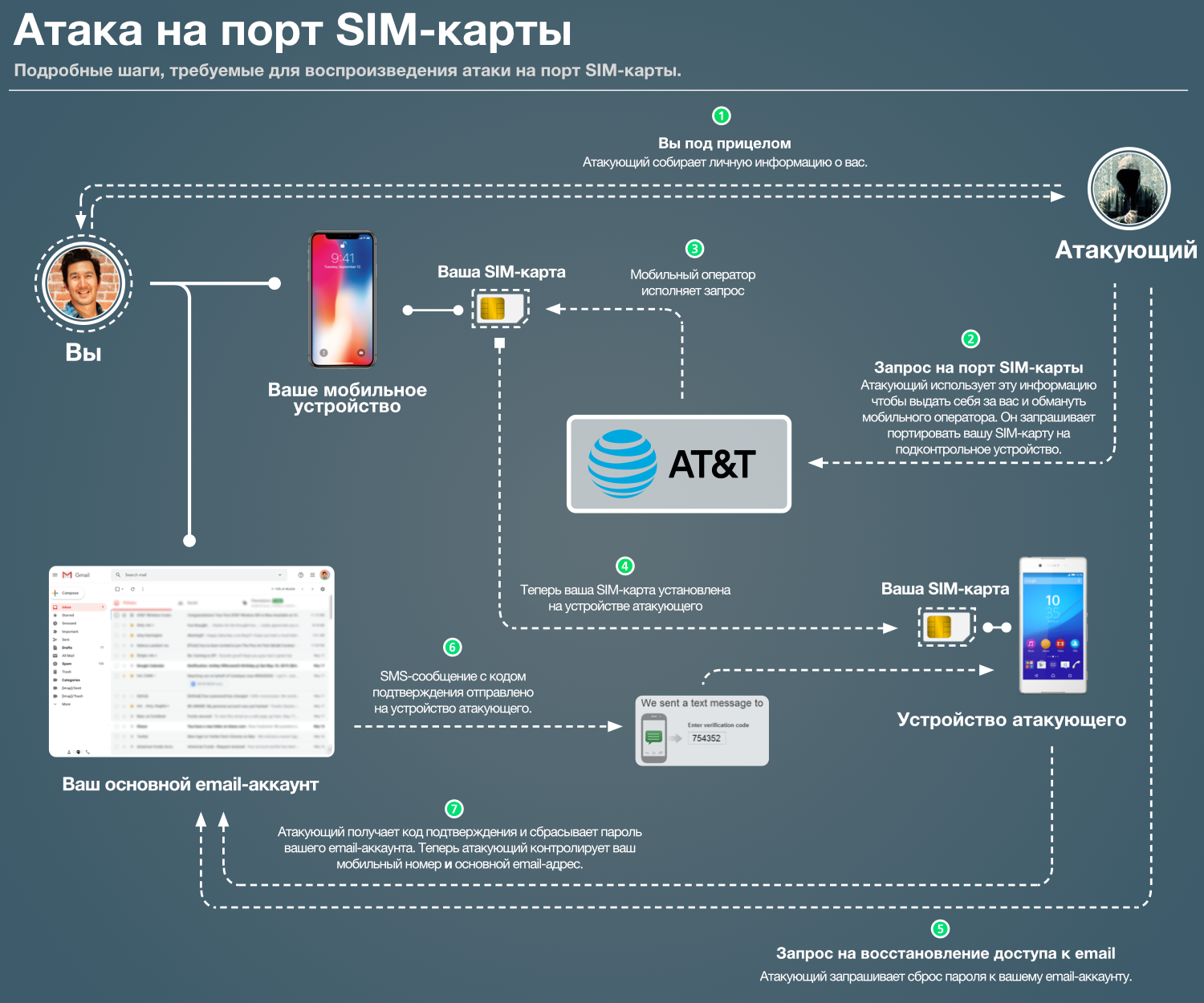
As soon as the attacker gains access to your email address, they begin to switch from service to service, where you use this email address (banks, social networks, etc.) If the attacker is particularly harmful, he may block your access to your own accounts and request a fee to return access.
Let's digress for a minute and think about the amount of personal information tied to one Google account:
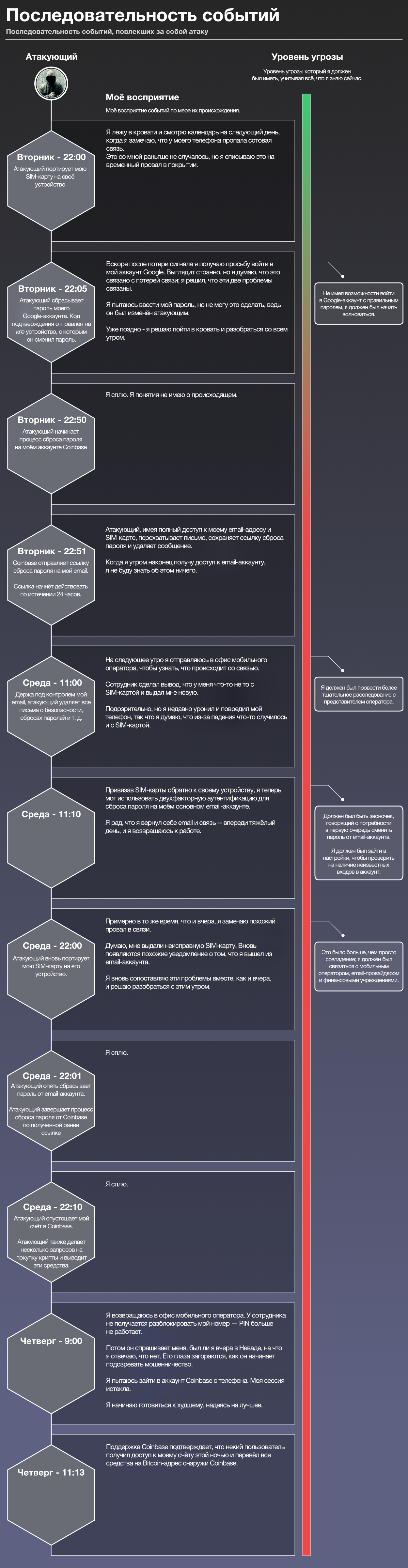
To better understand how the attack occurs and to see its scope, let's plunge into the timeline of this attack itself. I want to show how the attack was carried out, what I was experiencing at this time and what you can do to protect yourself in the event of such symptoms.
The timeline is divided into four parts:
It was the most expensive lesson in my life. I lost a significant share of my capital in 24 hours; irrevocably. Here are some tips to help others better protect themselves:
Given my device security practices, I probably deserve to be hacked - I understand that. This does not make it easier, and condemnation only erodes the meaning of history, which consists in:
I cannot stop thinking about small, simple things that I could do to protect myself. My head is full of thoughts about "what if ..."
However, these thoughts are side by side compared with two intersecting feelings - laziness and a bias of survival. I never took my online security seriously because I never experienced an attack. And although I understood my risks, I was too lazy to protect my assets with the proper rigor.
I urge you to learn from these mistakes.
Last Wednesday, I lost over $ 100,000. The money evaporated within 24 hours as a result of the “attack on the SIM card port”, which cleared my Coinbase account. Four days have passed since then, and I am devastated. I have no appetite; I can not fall asleep; I am filled with feelings of anxiety, conscience and shame.
It was the most expensive lesson in my life, and I want to share experiences and lessons learned with as many people as possible. My goal is to increase people's awareness of these types of attacks and motivate you to enhance the security of your online identity.
It's still very damp (I still haven't told my family about this); please keep your condemnation of the naive security practices described in this post.
Attack Details
You may ask: “What kind of attack is this on the SIM card port?” To describe the attack, let's first look at a typical online identity. The chart below should be familiar to most of you.

Many of us have a primary email address that is connected to a HUGE amount of other online accounts. Many of us also have a mobile device that can be used to recover a forgotten email password.
Authorized SIM Port
One of the services that telecom operators offer customers is the ability to port a SIM card to another device. This allows the client to request the transfer of their phone number to the new device. In most cases, this is an absolutely legal process; this happens when we buy a new phone, change the operator, etc.
SIM port attack
However, an “attack on the SIM card port” is a malicious port, produced from an unauthorized source - by an attacker. The attacker will port your SIM card to a phone controlled by him. Then the attacker begins the process of resetting the password on the email account. A confirmation code is sent to your phone number and is intercepted by the attacker, since he now controls your SIM card. The diagram below shows the attack step by step.

As soon as the attacker gains access to your email address, they begin to switch from service to service, where you use this email address (banks, social networks, etc.) If the attacker is particularly harmful, he may block your access to your own accounts and request a fee to return access.
Let's digress for a minute and think about the amount of personal information tied to one Google account:
- your address, date of birth and other personal information that identifies you;
- access to potentially incriminating photographs of you and / or your partner;
- access to calendar events and vacation dates;
- access to personal emails, documents, search queries;
- access to your personal contacts and their personal information, as well as their attitude to you;
- access to all online services where your primary email address is indicated as a means of entry.
Sequence of events
To better understand how the attack occurs and to see its scope, let's plunge into the timeline of this attack itself. I want to show how the attack was carried out, what I was experiencing at this time and what you can do to protect yourself in the event of such symptoms.
The timeline is divided into four parts:
- What I experienced: how events happened from my point of view - if you experience something like that, then you are most likely under attack.
- What the attacker did: the tactics the attacker used to gain access to my Coinbase account.
- Perceived threat level: The significance I attached to the events.
- Desired threat level: the significance I would have to attach to events.

Lesson learned and recommendations
It was the most expensive lesson in my life. I lost a significant share of my capital in 24 hours; irrevocably. Here are some tips to help others better protect themselves:
- Use a physical cryptocurrency wallet: transfer your crypto stocks to a physical wallet / offline storage / wallet with several signatures whenever you do not complete transactions. Do not leave funds on exchanges. I perceived Coinbase as a bank account, but you will have no way out in case of an attack. I knew about these risks, but I never thought that something like this could happen to me. I very much regret that I did not take more serious measures to ensure the security of my crypt.
- Two-factor authentication based on SMS is not enough: regardless of what you want to protect on the network, switch to hardware protection (for example, something physical that an attacker will have to get to launch an attack). While Google Authenticator or Authy can turn your phone into a kind of hardware protection, I would recommend going further. Get a YubiKey that you control physically and that cannot be swapped.
- Reduce your online footprint: overcome the desire to unnecessarily share personal information that can identify you (date of birth, location, photos with geodata, etc.) All this kind of public data can play a trick on you in the future in case of an attack .
- Google Voice 2FA: in some cases, the service may not support hardware two-factor authentication, relying on weaker SMS messages. Then it would be a good idea to create a virtual phone number in Google Voice (which cannot be ported) and use it as a number for two-factor authentication. (translator's note: this method only works in the USA)
- Create a secondary email address: instead of linking everything to one address, create a secondary email address for critical accounts (banks, social networks, cryptocurrency exchanges ...) Do not use this address for anything else and keep it secret . Remember to protect this address with any form of two-factor authentication.
- Offline password manager: use a password manager. Better yet, use an offline password manager, such as the Password Store. Irvik has an excellent comparison of different password managers as well as recommendations for the more technically savvy.
As for reader comments ...
Given my device security practices, I probably deserve to be hacked - I understand that. This does not make it easier, and condemnation only erodes the meaning of history, which consists in:
- Let others know how easy it is to endanger.
- Use the knowledge and recommendations you have received to prioritize the security of your online identity.
I cannot stop thinking about small, simple things that I could do to protect myself. My head is full of thoughts about "what if ..."
However, these thoughts are side by side compared with two intersecting feelings - laziness and a bias of survival. I never took my online security seriously because I never experienced an attack. And although I understood my risks, I was too lazy to protect my assets with the proper rigor.
I urge you to learn from these mistakes.
