What hackers miss when breaking a bank on PHDays

From year to year, the bank becomes a special entity for the results of the “Confrontation” at PHDays. In 2017, hackers were able to withdraw more money from the bank than there was in it. In 2018, the success of the final attack on the bank with the antifraud turned off (according to the organizers) ensured the victory of one of the teams.
Every year, bank protection systems in virtual city F reflect thousands of attempts to withdraw money from the accounts of "civilian" residents, but each time these attempts are more like brute force on the banking API than an attempt to bypass an antifraud system that every attack team knows about.
What trends can be seen when comparing attacking and “law-abiding citizens” at The Standoff is the topic of this short article. It is a modest hint to the attacking side, although perhaps it will not be read in these busy last days of preparation for all participants :)
Determining the legitimacy of the event, whether it’s just entering the bank’s page or trying to conduct a payment operation, you need to find out who stands behind the commission of this action. This object can be viewed in the following three metrics.
- Static characteristics of the object.
- His behavioral model.
- The overall picture of the operations of the entire bank during the event.
Statics
The attacker always has the advantage - everyone is behind NAT, which means that the chances of identifying an object and building connections, who works with which IP address, are extremely small. Protection is completely unable to block suspicious segments.
It is also worth noting here that attackers mainly use bots to withdraw money, which together with a large number of legal bots of PHDays organizers leads to the task of determining the legitimate bot by the characteristics of operations.
Dynamics
Here the first element of the elimination of simple attempts to attack the bank is hidden. As soon as a set of events with a high frequency comes into view, the activity of such a source is included in the list of special control.
Here is an example of comparing the frequency response of attacking and legal bots (the coefficients and part of the parameters hereinafter, of course, are changed).
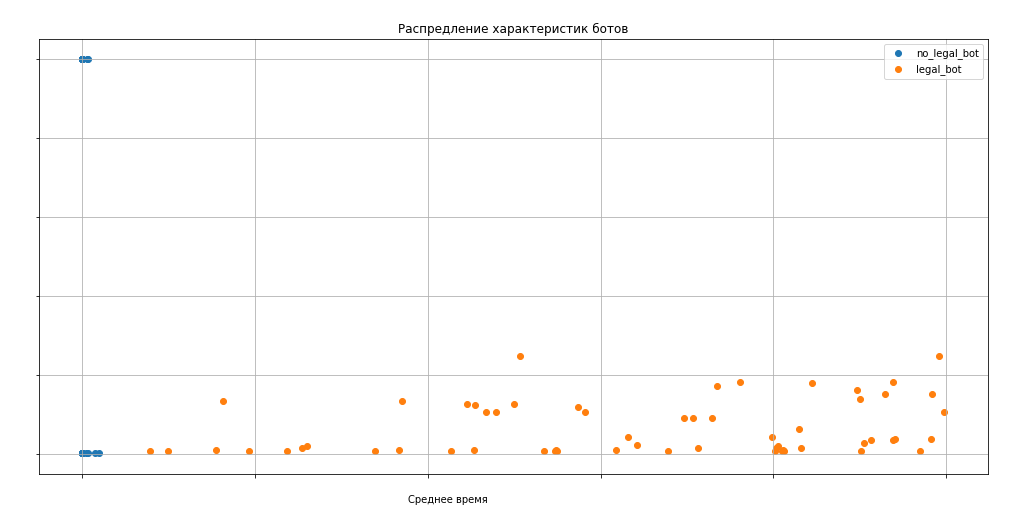
The graph clearly shows that the likelihood assessment, not to mention the ability of a person to perform operations at such a speed in the web interface, the attackers did not.

This graph shows that introducing one additional parameter in the amount makes the identification of fraudsters an even simpler task.
Overall picture
Now a little about how it all looks from the point of view of the bank as a whole, and more precisely, how normal bots differ in connectivity from attacking bots, where profiling works fine.

As you can see, extremely simple statistics on linking to accounts leads to an unambiguous identification of legitimate and fraudulent activity.

And on this graph, all attacking bots as well, with one exception, fall into the conditions with accuracy, and only one team was able to write a slightly more original algorithm, which in general also does not come close to examples of legal activity.
To summarize: taking into account the great capabilities and the complete absence of components of classical information security at PHDays banking services, attackers use the simplest schemes, and their identification is trivial enough for modern analysis tools.
This year we promise not to turn off the antifraud for a minute, not to succumb to provocations and requests and expect more ingenuity from the attacking side)
Alexey Sizov, captain of the Jet Antifraud Team, head of the anti-fraud department at the Jet Infosystems Application Security Center
