Application Centric Infrastructure. Network architecture of the future - from reasoning to business
Over the past few years, Cisco has been actively promoting a new data center network architecture in the data center - Application Centric Infrastructure (or ACI) . Some are already familiar with her. And someone even managed to introduce it at their enterprises, including in Russia. However, for most IT professionals and IT executives, ACI is either an obscure abbreviation or just a discussion of the future.
In this article we will try to bring this future closer. To do this, we will talk about the main architectural components of ACI, as well as illustrate how to put it into practice. In addition, in the near future we will organize a visual demonstration of the work of ACI, which every interested IT specialist can sign up for.
You can learn more about the new network building architecture in St. Petersburg in May 2019. All details are on the link . Sign up!
The traditional and most popular model for building a network is a three-level hierarchical model: core -> distribution (aggregation) -> access. Over the years, this model has been the standard; manufacturers used it to produce various network devices of the corresponding functionality.
Previously, when information technology was a kind of necessary (and, frankly, not always desired) appendage to business, this model was convenient, very static and reliable. However, now that IT is one of the drivers of business development, and in many cases the business itself, the static nature of this model has become a big problem.
Modern business generates a large number of different complex requirements for network infrastructure. The success of the business directly depends on the timing of the implementation of these requirements. Delay in such conditions is unacceptable, and the classical model of building a network often does not allow timely satisfaction of all business needs.
For example, the emergence of a new complex business application involves network administrators performing a large number of routine operations of the same type on a large number of different network devices at different levels. Besides the fact that it takes a lot of time, it also increases the risk of making a mistake that can lead to serious downtime of IT services and, as a result, to financial damage.
The root of the problem is not even the timing itself or the complexity of the requirements. The fact is that these requirements must be "translated" from the language of business applications into the language of network infrastructure. As you know, any translation is always a partial loss of meaning. When the application owner talks about the logic of his application, the network administrator understands the set of VLANs, Access lists on dozens of devices that need to be maintained, updated and documented.
The accumulated experience and constant communication with customers allowed Cisco to design and implement new principles for building a data center data network, which meet modern trends and are based primarily on the logic of business applications. Hence the name - Application Centric Infrastructure.
The ACI architecture is most correctly viewed not from the physical side, but from the logical one. It is based on a model of automated policies, the objects of which at the top level can be divided into the following components:

Consider each level in more detail - while we will move from simple to complex.
The network in the ACI factory is similar to the traditional hierarchical model, but it is much simpler to build. To organize the network, the Leaf-Spine model is used, which has become a generally accepted approach for implementing next-generation networks. This model consists of two levels: Spine and Leaf, respectively.

The Spine level is only responsible for performance. The overall performance of the Spine switches is equal to the performance of the entire factory, therefore, switches with ports 40G or higher should be used at this level.
Spine switches connect to all the next level switches: Leaf switches to which end hosts connect. The main role of Leaf switches is port capacity.
Thus, scaling issues are easily resolved: if we need to increase the throughput of the factory, we add Spine switches, and if we need to increase the port capacity - Leaf.
For both levels, the Cisco Nexus 9000 series switches are used, which for Cisco are the main tool for building data center networks regardless of their architecture. For the Spine level, Nexus 9300 or Nexus 9500 switches are used, and for Leaf only Nexus 9300 switches.
The lineup of Nexus switches used in the ACI factory is shown in the figure below.

APIC controllers are specialized physical servers, and for small deployments it is allowed to use a cluster of one physical APIC controller and two virtual ones.
APIC controllers provide management and monitoring functions. It is important that the controllers never participate in the data transfer, that is, even if all the cluster controllers fail, then this will not affect the stability of the network. It should also be noted that with the help of APICs, the administrator manages absolutely all the physical and logical resources of the factory, and in order to make any changes, it is no longer necessary to connect to a particular device, since the ACI uses a single control point.
Now let's move on to one of the main components of ACI - application profiles.
An Application Network Profile is the logical foundation of ACI. It is application profiles that determine the interaction policies between all network segments and directly describe the network segments themselves. ANP allows you to abstract from the physical layer and, in fact, imagine how to organize the interaction between different segments of the network from the point of view of the application.
An application profile consists of End-point groups (EPGs). A connection group is a logical group of hosts (virtual machines, physical servers, containers, etc.) that are in the same security segment (not a network, namely security). End hosts that belong to a particular EPG can be determined by a large number of criteria. Commonly used are the following:
For the interaction of various EPGs, an entity called contracts is provided. The contract defines the relationship between different EPGs. In other words, the contract determines which service one EPG provides another EPG. For example, we are creating a contract that allows traffic to go over the HTTPS protocol. Next, we connect with this contract, for example, EPG Web (group of web servers) and EPG App (group of application servers), after which these two terminal groups can exchange traffic via the HTTPS protocol.
The figure below describes an example of setting up communication of various EPGs through contracts within the same ANP.
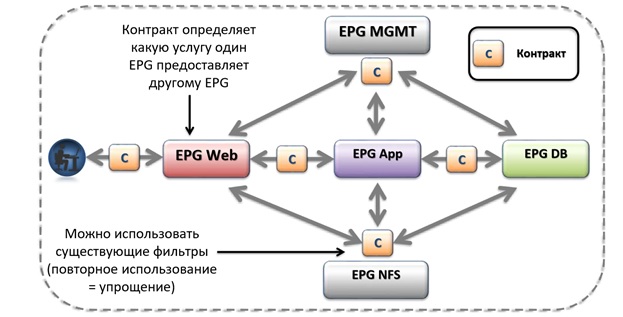
There can be any number of application profiles within an ACI factory. In addition, contracts are not tied to a specific application profile; they can (and should) be used to connect EPGs in different ANPs.
In fact, every application that needs a network in one form or another is described by its own profile. For example, the diagram above shows the standard architecture of a three-tier application, consisting of the N-th number of external access servers (Web), application servers (App) and DBMS servers (DB), and also describes the rules for interaction between them. In a traditional network infrastructure, this would be a set of rules spelled out on various devices in the infrastructure. In the ACI architecture, we describe these rules within a single application profile. ACI using the application profile allows you to greatly simplify the creation of a large number of settings on various devices, grouping them all into a single profile.
The figure below shows a more realistic example. A Microsoft Exchange application profile made from several EPGs and contracts.

Central management, automation and monitoring are one of the key benefits of ACI. ACI factory relieves administrators of the routine of creating a large number of rules on various switches, routers and firewalls (the classic manual configuration method is allowed and can be used). Settings for application profiles and other ACI objects are automatically applied throughout the ACI factory. Even when physically switching servers to other ports of the factory switches, you won’t need to duplicate the settings from the old switches to the new ones and clean up unnecessary rules. Based on the criteria that the host belongs to the EPG, the factory will make these settings automatically and automatically clear unused rules.
Integrated ACI security policies are implemented according to the principle of white lists, that is, what is clearly not allowed is prohibited by default. Together with automatic updating of network equipment configurations (removal of “forgotten” unused rules and permissions), this approach significantly increases the overall level of network security and narrows the surface of a potential attack.
ACI allows you to organize networking between not only virtual machines and containers, but also physical servers, hardware ITUs and third-party network equipment, which makes ACI a unique solution at the moment.
Cisco's new approach to building a data network based on application logic is not only automation, security, and centralized management. It is also a modern horizontally scalable network that meets all the requirements of modern business.
Implementation of ACI-based network infrastructure allows all departments of the enterprise to speak the same language. The administrator is guided only by the logic of the application, which describes the required rules and communications. As well as the logic of the application, the owners and developers of the application, the information security service, economists and business owners are guided.
Thus, Cisco in practice implements the concept of a new generation data center network. Want to see for yourself? Come to the Demonstration Application Centric Infrastructure in St. Petersburg and work with the data center network of the future now.
You can sign up for an event here .
In this article we will try to bring this future closer. To do this, we will talk about the main architectural components of ACI, as well as illustrate how to put it into practice. In addition, in the near future we will organize a visual demonstration of the work of ACI, which every interested IT specialist can sign up for.
You can learn more about the new network building architecture in St. Petersburg in May 2019. All details are on the link . Sign up!
Background
The traditional and most popular model for building a network is a three-level hierarchical model: core -> distribution (aggregation) -> access. Over the years, this model has been the standard; manufacturers used it to produce various network devices of the corresponding functionality.
Previously, when information technology was a kind of necessary (and, frankly, not always desired) appendage to business, this model was convenient, very static and reliable. However, now that IT is one of the drivers of business development, and in many cases the business itself, the static nature of this model has become a big problem.
Modern business generates a large number of different complex requirements for network infrastructure. The success of the business directly depends on the timing of the implementation of these requirements. Delay in such conditions is unacceptable, and the classical model of building a network often does not allow timely satisfaction of all business needs.
For example, the emergence of a new complex business application involves network administrators performing a large number of routine operations of the same type on a large number of different network devices at different levels. Besides the fact that it takes a lot of time, it also increases the risk of making a mistake that can lead to serious downtime of IT services and, as a result, to financial damage.
The root of the problem is not even the timing itself or the complexity of the requirements. The fact is that these requirements must be "translated" from the language of business applications into the language of network infrastructure. As you know, any translation is always a partial loss of meaning. When the application owner talks about the logic of his application, the network administrator understands the set of VLANs, Access lists on dozens of devices that need to be maintained, updated and documented.
The accumulated experience and constant communication with customers allowed Cisco to design and implement new principles for building a data center data network, which meet modern trends and are based primarily on the logic of business applications. Hence the name - Application Centric Infrastructure.
ACI Architecture
The ACI architecture is most correctly viewed not from the physical side, but from the logical one. It is based on a model of automated policies, the objects of which at the top level can be divided into the following components:
- Network based on Nexus switches.
- APIC controller cluster
- Application profiles;

Consider each level in more detail - while we will move from simple to complex.
Nexus Switch Network
The network in the ACI factory is similar to the traditional hierarchical model, but it is much simpler to build. To organize the network, the Leaf-Spine model is used, which has become a generally accepted approach for implementing next-generation networks. This model consists of two levels: Spine and Leaf, respectively.

The Spine level is only responsible for performance. The overall performance of the Spine switches is equal to the performance of the entire factory, therefore, switches with ports 40G or higher should be used at this level.
Spine switches connect to all the next level switches: Leaf switches to which end hosts connect. The main role of Leaf switches is port capacity.
Thus, scaling issues are easily resolved: if we need to increase the throughput of the factory, we add Spine switches, and if we need to increase the port capacity - Leaf.
For both levels, the Cisco Nexus 9000 series switches are used, which for Cisco are the main tool for building data center networks regardless of their architecture. For the Spine level, Nexus 9300 or Nexus 9500 switches are used, and for Leaf only Nexus 9300 switches.
The lineup of Nexus switches used in the ACI factory is shown in the figure below.

APIC cluster (Application Policy Infrastructure Controller)
APIC controllers are specialized physical servers, and for small deployments it is allowed to use a cluster of one physical APIC controller and two virtual ones.
APIC controllers provide management and monitoring functions. It is important that the controllers never participate in the data transfer, that is, even if all the cluster controllers fail, then this will not affect the stability of the network. It should also be noted that with the help of APICs, the administrator manages absolutely all the physical and logical resources of the factory, and in order to make any changes, it is no longer necessary to connect to a particular device, since the ACI uses a single control point.

Now let's move on to one of the main components of ACI - application profiles.
An Application Network Profile is the logical foundation of ACI. It is application profiles that determine the interaction policies between all network segments and directly describe the network segments themselves. ANP allows you to abstract from the physical layer and, in fact, imagine how to organize the interaction between different segments of the network from the point of view of the application.
An application profile consists of End-point groups (EPGs). A connection group is a logical group of hosts (virtual machines, physical servers, containers, etc.) that are in the same security segment (not a network, namely security). End hosts that belong to a particular EPG can be determined by a large number of criteria. Commonly used are the following:
- Physical port
- Logical port (port-group on the virtual switch)
- VLAN ID or VXLAN
- IP address or IP subnet
- Server attributes (name, location, OS version, etc.)
For the interaction of various EPGs, an entity called contracts is provided. The contract defines the relationship between different EPGs. In other words, the contract determines which service one EPG provides another EPG. For example, we are creating a contract that allows traffic to go over the HTTPS protocol. Next, we connect with this contract, for example, EPG Web (group of web servers) and EPG App (group of application servers), after which these two terminal groups can exchange traffic via the HTTPS protocol.
The figure below describes an example of setting up communication of various EPGs through contracts within the same ANP.

There can be any number of application profiles within an ACI factory. In addition, contracts are not tied to a specific application profile; they can (and should) be used to connect EPGs in different ANPs.
In fact, every application that needs a network in one form or another is described by its own profile. For example, the diagram above shows the standard architecture of a three-tier application, consisting of the N-th number of external access servers (Web), application servers (App) and DBMS servers (DB), and also describes the rules for interaction between them. In a traditional network infrastructure, this would be a set of rules spelled out on various devices in the infrastructure. In the ACI architecture, we describe these rules within a single application profile. ACI using the application profile allows you to greatly simplify the creation of a large number of settings on various devices, grouping them all into a single profile.
The figure below shows a more realistic example. A Microsoft Exchange application profile made from several EPGs and contracts.

Central management, automation and monitoring are one of the key benefits of ACI. ACI factory relieves administrators of the routine of creating a large number of rules on various switches, routers and firewalls (the classic manual configuration method is allowed and can be used). Settings for application profiles and other ACI objects are automatically applied throughout the ACI factory. Even when physically switching servers to other ports of the factory switches, you won’t need to duplicate the settings from the old switches to the new ones and clean up unnecessary rules. Based on the criteria that the host belongs to the EPG, the factory will make these settings automatically and automatically clear unused rules.
Integrated ACI security policies are implemented according to the principle of white lists, that is, what is clearly not allowed is prohibited by default. Together with automatic updating of network equipment configurations (removal of “forgotten” unused rules and permissions), this approach significantly increases the overall level of network security and narrows the surface of a potential attack.
ACI allows you to organize networking between not only virtual machines and containers, but also physical servers, hardware ITUs and third-party network equipment, which makes ACI a unique solution at the moment.
Cisco's new approach to building a data network based on application logic is not only automation, security, and centralized management. It is also a modern horizontally scalable network that meets all the requirements of modern business.
Implementation of ACI-based network infrastructure allows all departments of the enterprise to speak the same language. The administrator is guided only by the logic of the application, which describes the required rules and communications. As well as the logic of the application, the owners and developers of the application, the information security service, economists and business owners are guided.
Thus, Cisco in practice implements the concept of a new generation data center network. Want to see for yourself? Come to the Demonstration Application Centric Infrastructure in St. Petersburg and work with the data center network of the future now.
You can sign up for an event here .
