9. Check Point Getting Started R80.20. Application Control & URL Filtering
- Tutorial

Welcome to the 9th lesson! After a short break for the May holidays, we continue our publications. Today we will discuss a no less interesting topic, namely Application Control and URL Filtering . That is why Check Point is sometimes bought. Need to block Telegram, TeamViewer or Tor? This is what Application Control is for. In addition, we will touch upon another interesting blade - Content Awareness , and also discuss the importance of HTTPS inspection . But first things first!
As you recall, in lesson 7 we started discussing Access Control policy, but so far we have only touched on the Firewall blade and played a bit with NAT. Now add three more blades - Application Control , URL Filteringand Content Awareness .
Application Control & URL Filtering
Why am I considering App Control and URL Filtering in one lesson? This is not casual. In fact, it is already quite difficult to clearly distinguish between where there is an application and where there is just a site. The same facebook. What is it? Website? Yes. But it includes many micro applications. Games, videos, messages, widgets, etc. And all this is desirable to manage. That is why App Control and URL filtering always activate together.
Now for the database of applications and sites. You can view them in SmartConsole via the Object Explorer. There is a special filter Applications / Categories for this. In addition, there is a special resource - Check Point AppWiki . There you can always see if there is an application (or a resource) in the checkpoint database.
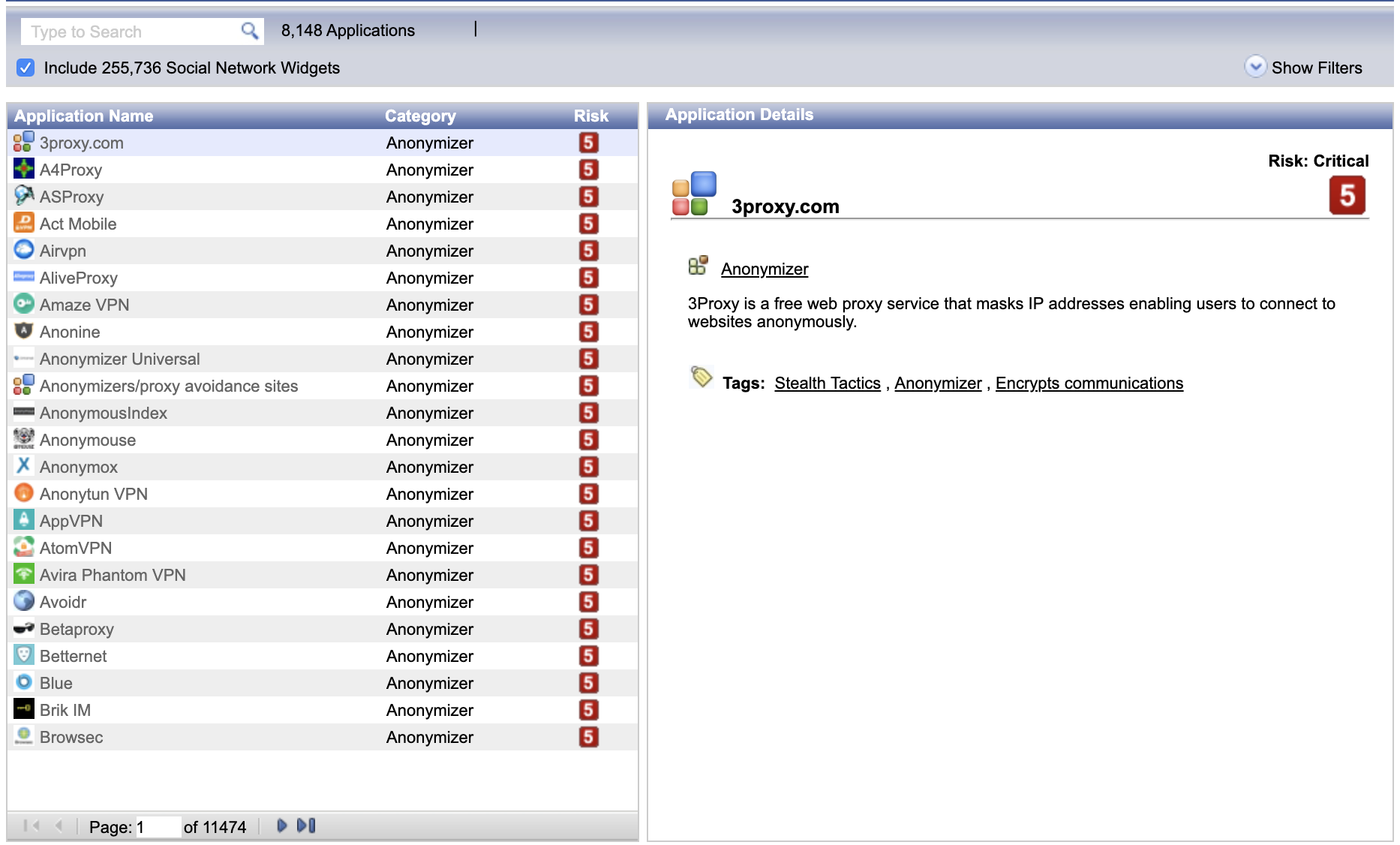
There is also a Check Point URL Categorization service., there you can always check to which "checkpoint" category this or that resource belongs. You can even request a category change if you think that it is defined incorrectly.
Otherwise, with these blades, everything is pretty obvious. Create an access sheet, specify the resource / application that you want to block or vice versa to allow. That's all. A little later we will see this in practice.
Content Awareness
I see no reason to repeat on this topic as part of our course. I painted in great detail and showed this blade in the previous course - 3. Check Point to the maximum. Awareness the Content .
HTTPS Inspection
Similarly with HTTPS inspections. I pretty well painted both the theoretical and practical part of this mechanism here - 2. Check Point to the maximum. HTTPS inspection . However, HTTPS inspection is important not only for security, but also for the accuracy of identifying applications and sites. This is described in the video tutorial below.
Video lesson
In this lesson, I will talk in detail about the new concept of Layer, create a simple Facebook blocking policy, ban the download of executable files (using Content Awaress) and show how to enable HTTPS inspection.
Stay tuned for more and join our YouTube channel :)
