Synchronized Security at Sophos Central
To ensure the high efficiency of information security tools, an important role is played by the connection of its components. It allows you to block not only external, but also internal threats. When designing a network infrastructure, every means of protection is important, be it an antivirus or firewall, so that they function not only within their class (Endpoint security or NGFW), but also have the ability to interact with each other to jointly combat threats.
Bit of theory
It is not surprising that current cybercriminals have become more entrepreneurial. They use a number of network technologies to spread malware:

Phishing emails cause the malware to “cross the threshold” of your network using known attacks, either “zero-day attacks” followed by privilege escalation, or horizontal promotion (lateral movement) over the network. Having one infected device may mean that your network can be used for the mercenary purposes of an attacker.
In some cases, when it is necessary to ensure the interaction of information security components, when conducting an information security audit of the current state of the system, it cannot be described using a single set of measures that are interconnected. In most cases, many technological solutions that focus on countering a specific type of threat do not provide integration with other technological solutions. For example, endpoint protection products use signature-based and behavioral analysis to determine if a file is infected or not. Firewalls use other technologies to stop malicious traffic, including web filtering, IPS, sandboxing, etc.
Heartbeat Technology Trends
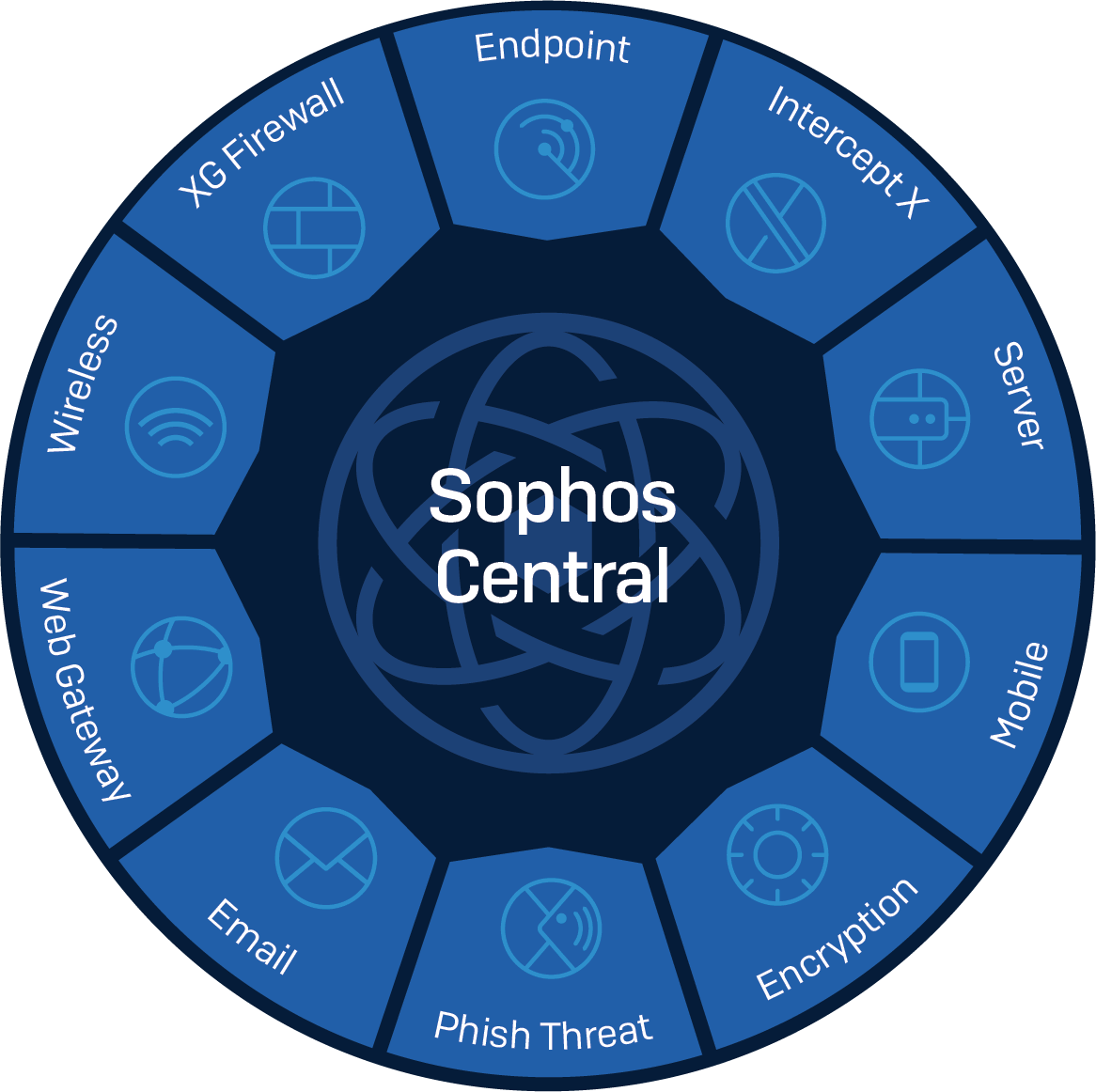
A new approach to ensuring cybersecurity involves protection at every level, in which the solutions used at each of them are interconnected and have the ability to exchange information. This leads to the creation of the Synchronized Security (SynSec) system. SynSec is an information security process as a single system. In this case, each information security component is connected to each other in real time. For example, the Sophos Central solution is implemented according to this principle.

Security Heartbeat technology provides communication between security components, ensuring the joint functioning of the system and its monitoring. The following classes are integrated into Sophos Central :
- Endpoint Protection - a classic signature antivirus;
- Server Protection - a specialized antivirus for servers;
- Intercept-X - a new generation antivirus (without signatures and with artificial intelligence technologies);
- Sophos XG Firewall - Next-Generation Firewall;
- Mobility Management (EMM) - mobile device management and access control to corporate mail and files;
- Data Protection (Encryption) ;
- Secure Wi-Fi - access points managed both from the cloud and locally through Sophos UTM / Sophos XG;
- Web Security - a classic solution for filtering web traffic;
- E-mail Security - cloud / local anti-spam / antivirus solution;
- Phish Threat - raising employee awareness, conducting test phishing emails;
- Cloud Optix - audit of cloud infrastructures.

It is easy to see that Sophos Central supports a fairly wide range of information security solutions. At Sophos Central, the SynSec concept is based on three important principles: detection, analysis and response. For a detailed description of them, let us dwell on each of them.
SynSec Concepts
DETECTION (identification of unknown threats)
Sophos products under the control of Sophos Central automatically share information among themselves to identify risks and unknown threats, which includes:
- network traffic analysis with the ability to identify high-risk applications and malicious traffic;
- Detection of users with a high risk group through a correlation analysis of their actions on the network.
ANALYSIS (instant and intuitive)
Real-time incident analysis provides an instant understanding of the current situation in the system.
- Displays the complete chain of events that led to the incident, including all files, registry keys, URLs, etc.
RESPONSE (automatic response to incidents)
Setting security policies allows you to automatically respond to infections and incidents in a matter of seconds. This is provided by:
- instant isolation of infected devices and stopping the attack in real time (even within the same network / broadcast domain);
- restricting access to company network resources for devices that do not meet policies;
- remote start of device scan when outgoing spam is detected.
We reviewed the basic security principles on which Sophos Central works. Now let's move on to a description of how SynSec technology works in action.
From theory to practice
To get started, let’s explain how SynSec establishes device interaction using Heartbeat technology. The first step is to register Sophos XG with Sophos Central. At this stage, he receives a certificate for self-identification, IP address and port through which end devices will communicate with him using Heartbeat technology, as well as a list of end device IDs managed through Sophos Central and their client certificates.
Shortly after Sophos XG enrollment occurs, Sophos Central will transmit information to end devices to initiate Heartbeat communications:
- List of certification authorities used to issue Sophos XG certificates
- a list of device IDs that are registered with Sophos XG;
- Heartbeat IP address and port for communication.
This information is stored on the computer in the following way:% ProgramData% \ Sophos \ Hearbeat \ Config \ Heartbeat.xml and is regularly updated.
Heartbeat technology communicates by sending endpoint messages to magic IP address 52.5.76.173:8347 and vice versa. The analysis revealed that packets are sent with a period of 15 seconds, as announced by the vendor. It is worth noting that Heartbeat messages are processed directly by the XG Firewall - it intercepts packets and monitors the status of the endpoint. If you capture packets on the host, the traffic flow will be similar to communicating with an external IP address, although in fact the endpoint communicates directly with the XG firewall.
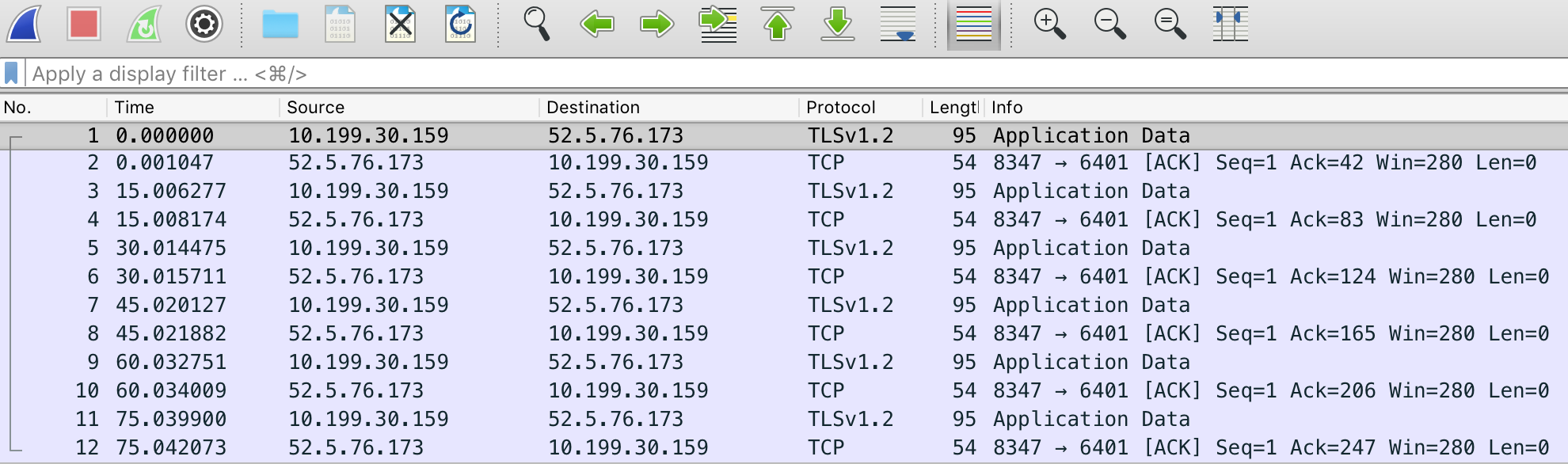
Let a malicious application get onto the computer in some way. Sophos Endpoint detects this attack, or we stop receiving Heartbeat from this system. The infected device automatically sends information about the infection of the system, causing an automatic chain of actions. XG Firewall instantly isolates the computer, preventing the spread of attacks and interaction with C&C servers.
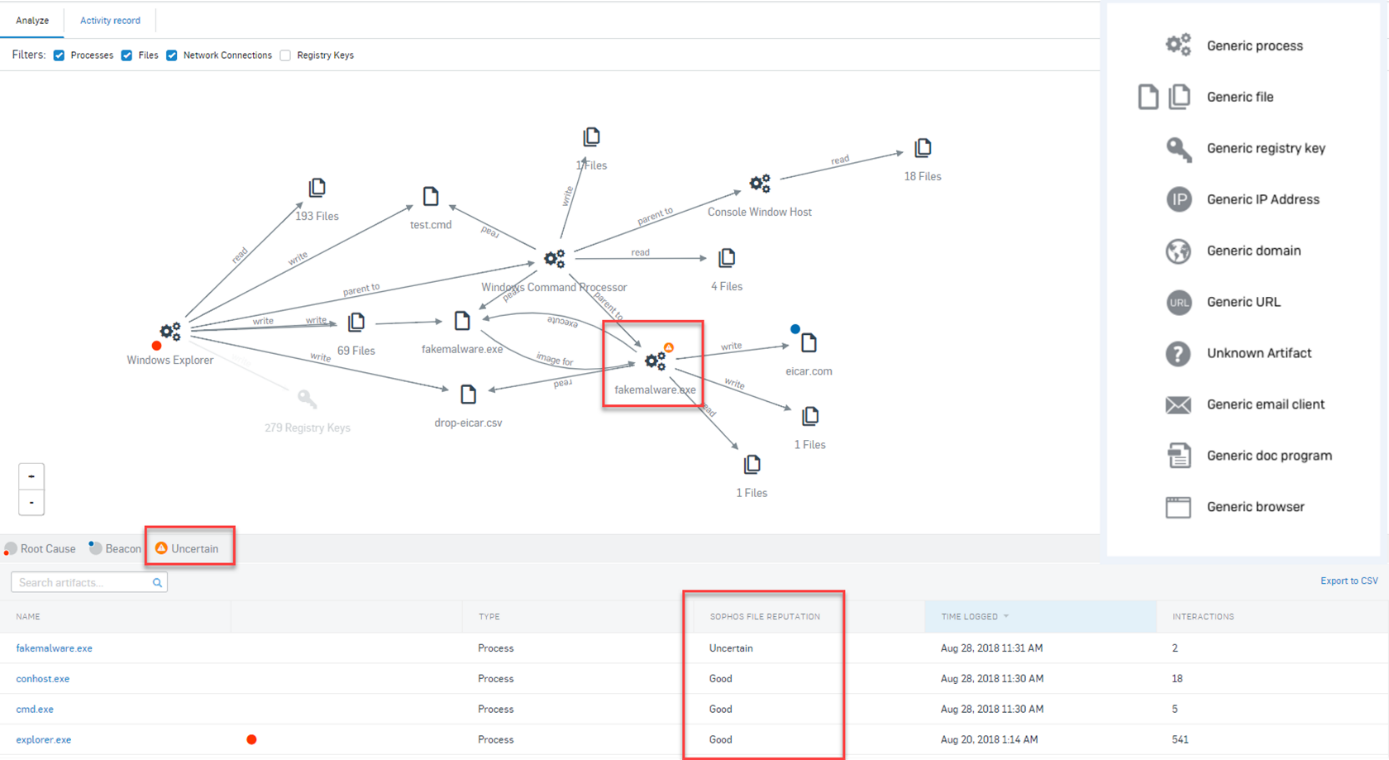
Sophos Endpoint automatically removes malware. After its removal, the end device is synchronized with Sophos Central, then the XG Firewall restores access to the network. Root Cause Analysis (RCA or EDR - Endpoint Detection and Responce) provides a detailed idea of what happened.
Assuming corporate resources are accessed using mobile devices and tablets, is it possible to provide SynSec in this case?
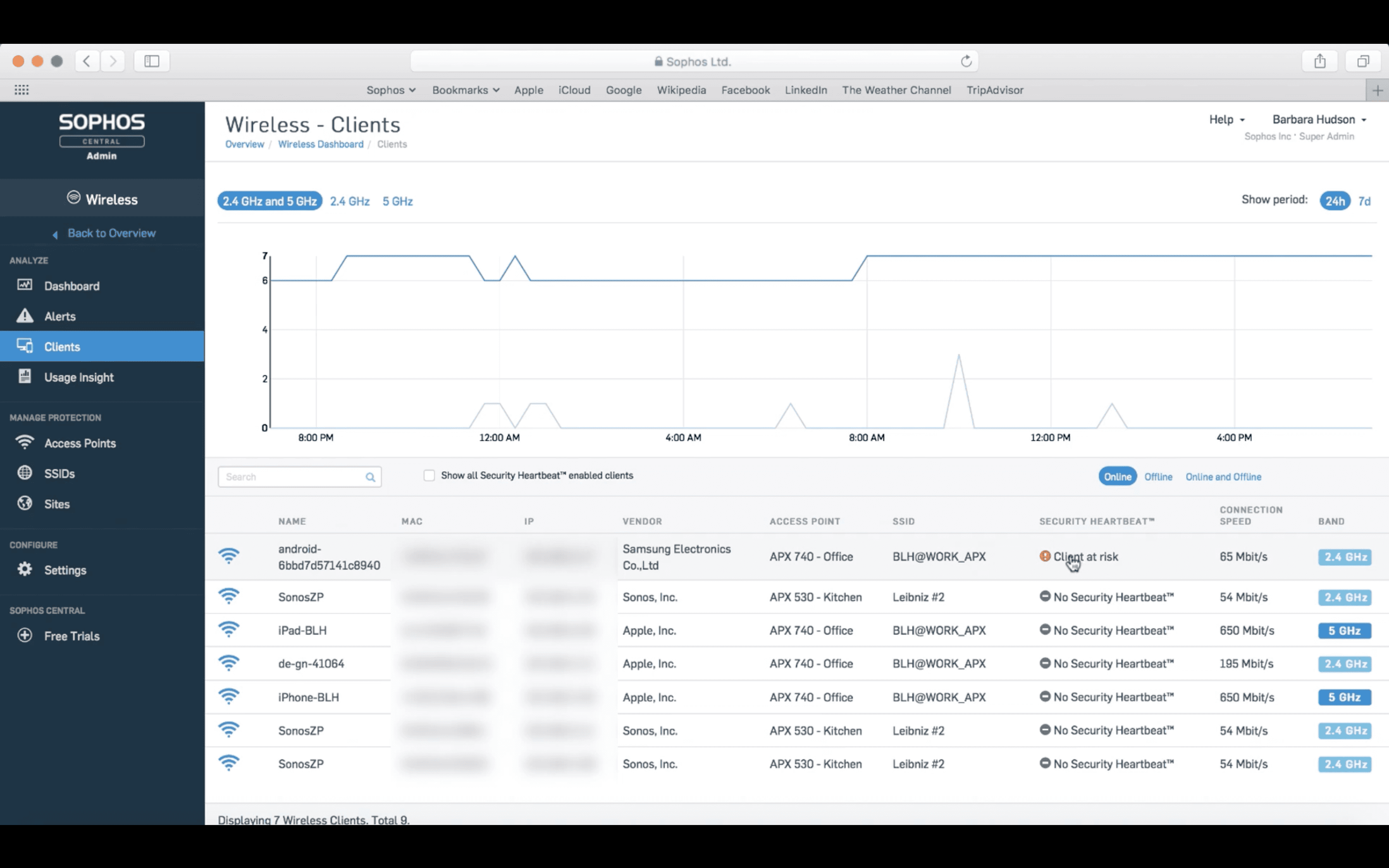
Sophos Central provides support for Sophos Mobile and Sophos Wireless for this scenario.. Suppose a user attempts to violate a security policy on a mobile device protected by Sophos Mobile. Sophos Mobile detects a security policy violation and sends notifications to the rest of the system, triggering a pre-configured response to the incident. If Sophos Mobile has a “prohibit network connectivity” policy, then Sophos Wireless will restrict network access for this device. The Sophos Central toolbar on the Sophos Wireless tab displays a notification that the device is infected. At the time when the user tries to access the network, a splash screen will appear on the screen, informing that access to the Internet is limited.
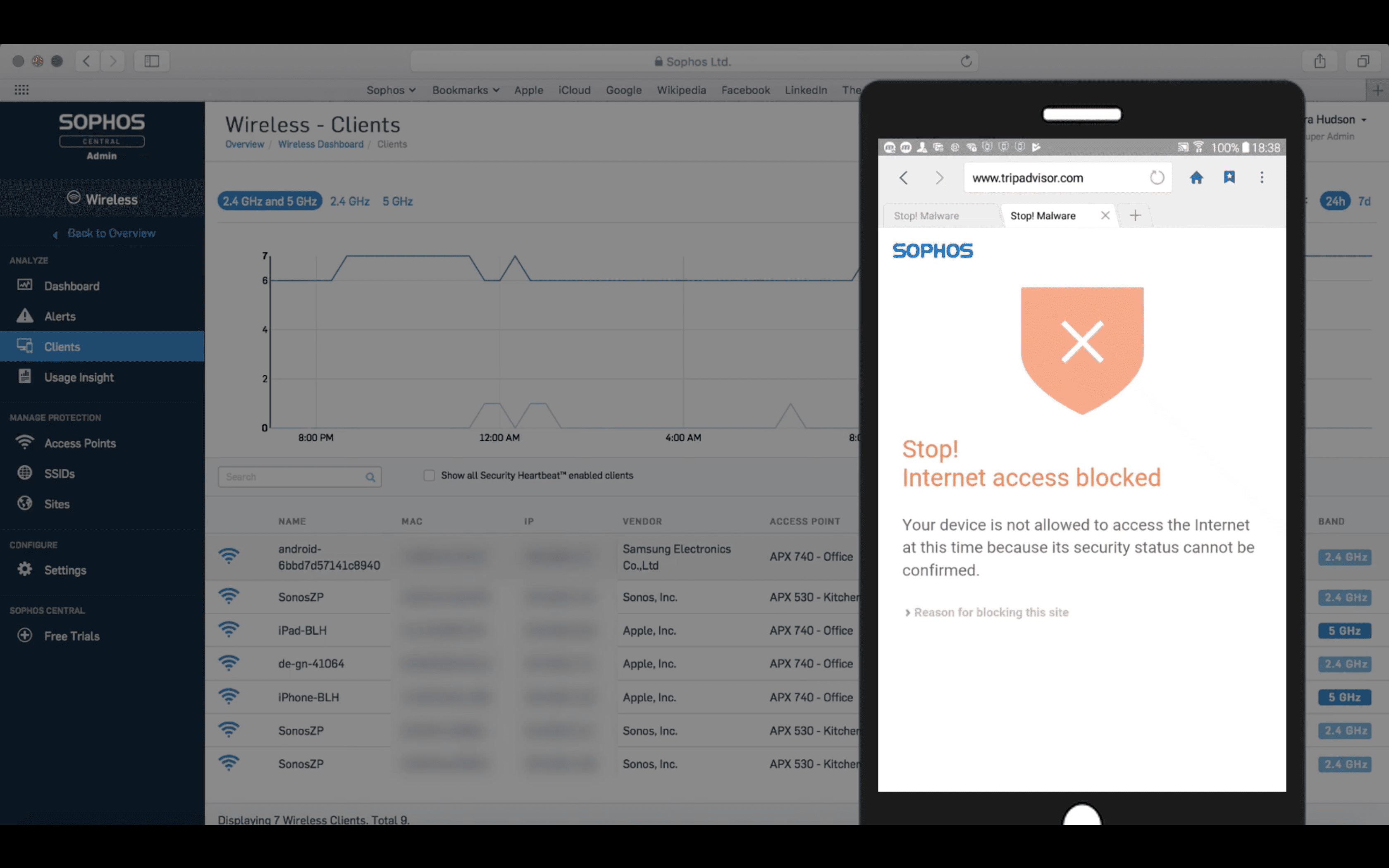
An endpoint has several Heartbeat status statuses: red, yellow, and green.
Red status occurs in the following cases:
- Active malware detected
- An attempt was made to launch malware;
- Malicious network traffic detected
- malware has not been removed.
A yellow status means that inactive malware was detected at the endpoint, or an PUP (potentially unwanted program) was detected. A green status indicates that none of the above problems have been detected.
Having examined some of the classic scenarios of the interaction of protected devices with Sophos Central, we will go on to describe the graphical interface of the solution and consider the basic settings and supported functionality.
GUI
The control panel displays the latest notifications. Also, in the form of diagrams, a summary characteristic for various protection components is displayed. In this case, summary data for protecting personal computers is displayed. This panel also contains summary information about attempts to visit dangerous resources with inappropriate content, and email analysis statistics.
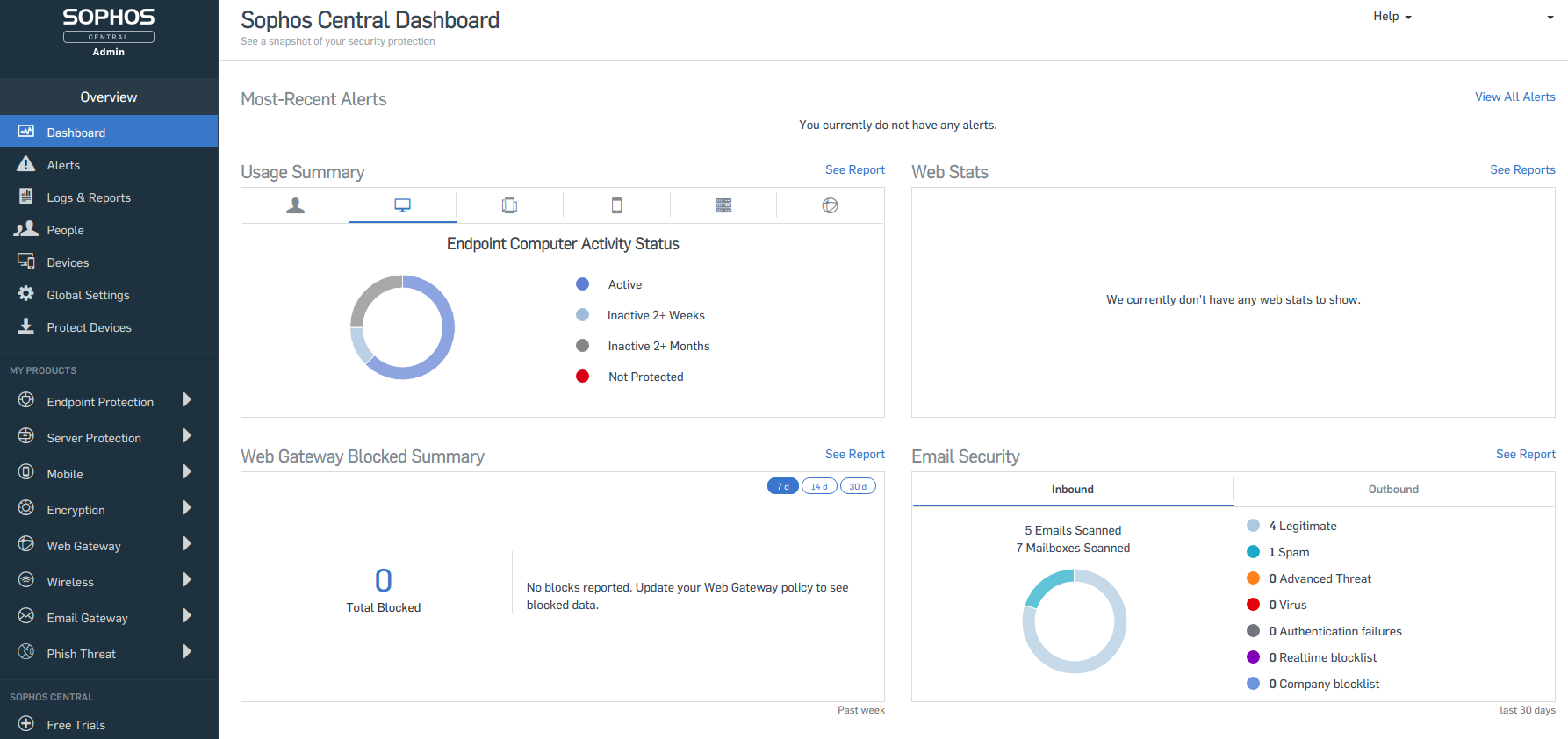
Sophos Central supports the display of alerts by severity, which prevents the user from skipping critical security alerts. In addition to concisely displayed summary information about the status of the security system, Sophos Central supports event logging, integration with SIEM systems. For many companies, Sophos Central is a platform for both internal SOC and for providing services to its customers - MSSP.
One important feature is the support for the update cache for endpoint clients. This saves the bandwidth of external traffic, since in this case updates are downloaded once to one of the endpoint clients, and then other end devices download updates from it. In addition to the feature described, the selected endpoint can relay security policy messages and information reports to the Sophos cloud. This function will be useful if there are end devices that do not have direct access to the Internet, but require protection. Sophos Central has an option (tamper protection) that prohibits changing computer protection settings or deleting an endpoint agent.
One of the components of endpoint protection is the next generation antivirus (NGAV) - Intercept X. Using deep machine learning technologies, the antivirus can detect previously unknown threats without the use of signatures. Detection accuracy is comparable to signature counterparts, but unlike them it provides proactive protection, preventing zero-day attacks. Intercept X is able to work in parallel with signature antiviruses of other vendors.
In this article, we briefly talked about the concept of SynSec, which is implemented in Sophos Central, as well as some of the features of this solution. We will talk about how each of the security components integrated into Sophos Central functions in the following articles. You can get a demo version of the solution here .
If the solution interests you, you can contact us - Factor Group, distributor of Sophos. It is enough to write in free form to sophos@fgts.ru .
