Pandora's Box: we analyze the exploitation of the WinRAR vulnerability using the NeoQUEST-2019 job as an example

How often the good old WinRAR comes to our aid! From time to time, he carefully and unselfishly unpacks our archives, and packs them back. But we got older, and now I want to try something more interesting, right? And just then they found a 19-year-old vulnerability that allows saving malware extracted from the archive to an arbitrary location. Let's see how this can be done, using the example of task number 9 from the online stage of NeoQUEST-2019 .
According to legend, we have two servers. The first server (http://213.170.100.213:800/) allows you to send a gift to Pandora, who loves to unpack all unidentified objects that caught her eye. The “gift” format is known: the server downloads only rar archives. Download an arbitrary rar archive. In response, we see the following:

It is not very likely that our archive is interested in Pandora. Let's try to learn a little more about the server using nmap:

Now we know that the first server:
- allows to load rar-archives;
- raised on Windows.
Win + rar = WinRar! Probably, archives are processed by this archiver, in which (more precisely - in the UNACEV2.DLL library) they found a vulnerability that has existed for 19 years. This "hole" allows you to unzip the contents of the archive into an arbitrary directory, regardless of where the user is extracting files. We find a detailed description of the vulnerability exploitation mechanism here . We proceed to the production of the archive, which
First of all, get the WinAceArchiver utility. According to the instructions given at the link above, we create a primitive archive containing the hello.txt file. In WinAceArchiver, click on the Create button, on the Options tab set Compression to Store, then return to the Selection tab, select the hello.txt file, specify the path to save our archive, and most importantly! - set the option "store full path":

Next, click on the “Add” button and get the Hello.ace archive. It remains to slightly adjust the path and correct the checksum. Any binary editor and acefile.py script will help us with this , which helpfully will calculate actual values by itself.
To exploit the vulnerability, you must add the volume label before the absolute path of the file, which will be dropped by the archiver. Then the rest of the path will be taken as “safe” relative. So, open the editor and modify the path so that it starts with C: \ C: \ .
It was:

It became:

Now check the checksums using the acefile.py script:
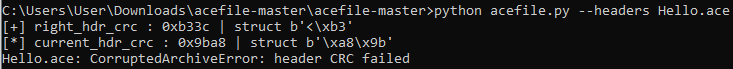
Correct the value to the current:

It remains only to rename our archive to Hello.rar. Done. Check how Pandore such a gift?
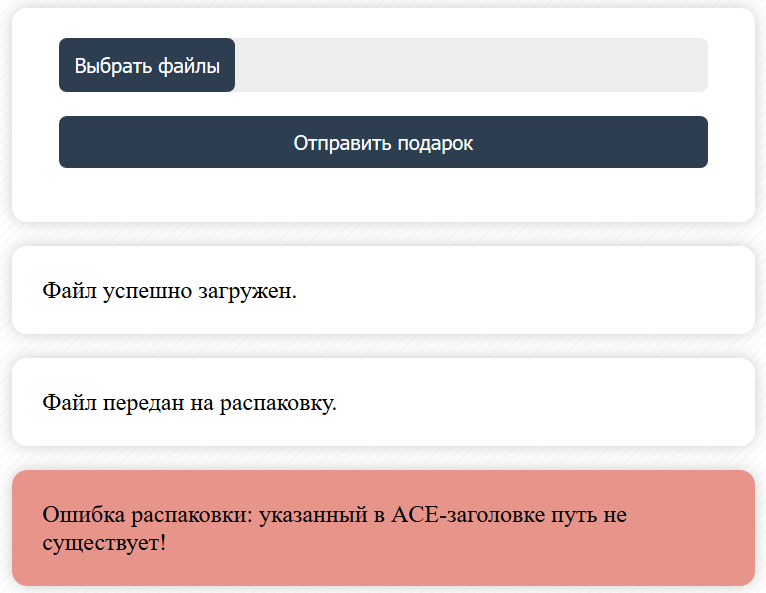
Excellent! Expectations coincided with reality, and WinRar processed the archive exactly as we needed. It remains to find out one thing: which path do we need?
According to legend, we know that treasures can be "viewed" on the second server (http://213.170.100.213:900/). How is this easiest to do? Of course, by running your php script, which will produce, for example, listing the server root directory. We confirm our guess:
Great, the server is ready to execute our php script! It's time to figure out exactly where to put this script. So far we know that the server is up on Windows - therefore, most likely the path starts with C: \ . What next? Learn a little more about the treasure server.
On the server nginx is lifted. Surely the environment of Pandora follows the last word of technological progress (in everything that does not concern archivers) and uses the latest version of nginx, that is 1.15.9 (you can check here ). It remains to add the root directory of the server specified in the default nginx configuration file:
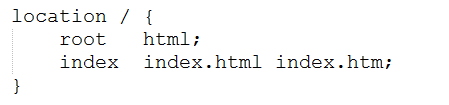
The result is as follows: C: \ nginx-1.15.9 \ html . What will Pandora answer this time?
Access to the directory is prohibited ... But we could not be mistaken! We are definitely on the right track, as access is denied, but the directory exists. There is probably something we don’t know about yet. We continue to collect information about the server using the directory scanner:

Yeah, there it is. The admin / directory sounds promising. Let's try to send Pandora an ace archive, in which C: \ nginx-1.15.9 \ html \ admin acts as the absolute path :

Success! Finally, we execute our script in which the server root directory is listed: 213.170.100.213 : 800 / admin / test34852ED2-8996-4F81-A919-30B6FE9F03AB.php . The script may look something like this:
";
}
}
closedir($handle);
}
?>
The result is as follows:

In the near future, articles will be published with analysis of the remaining several tasks. And still very soon there will be a “Confrontation” NeoQUEST 2019! All news - on the event website , do not miss!
