Supply Chain Security: "If I were a Nation State ..."

Have you ever wondered how many different organizations, companies, services, people took part in the creation and transportation of your computer, router and any other device that you use in everyday life or at work? And how is this dangerous? If not, then welcome under the cat for thought from Andrew 'bunnie' Huang .
At the beginning of 2019, a report by Andrew Huang of the Supply Chain Security: “If I were a Nation State ...” was presented at the BlueHat IL conference from Microsoft . But first, let's get acquainted with the speaker to understand why it is worth listening to his opinion, as to the opinion of a specialist in this matter.
Andrew Huang is a security researcher with a degree in electrical engineering. Known for his studies of the security of the Xbox and the hardware components of various devices, he participated in the creation of a fully integrated silicon photon chip, an activist of the open source community. The author of several books on hacking and security: Hacking the Xbox , Hardware Hacker and maintains a blog about his activities in the field of hardware.
In his report, Supply Chain Security: “If I were a Nation State ...”, he describes the insecurity of supply chains in terms of introducing backdoors into the hardware component of many electronic devices.
We did a short review of the report, and for those who want to familiarize themselves with this topic in more detail, you can watch the original video of the report.
In his report, the author gives the following examples:
there are cases of delivery and sale of test samples (with corresponding security flaws) of device components instead of final ones. The author came across an FPGA that erased marks that this is a test sample;
an additional element can be added to the device, expanding its functionality, for example, to exfiltrate the data stored on it. Already there were unrest associated with Chinese chips and internal developments of the special services;

- at the design or creation stage, “superfluous” elements can be added to the chip, or under the same chip there may appear a second, of exactly the same size, but with completely different functionality - this can be done to attack “a man in the middle”;
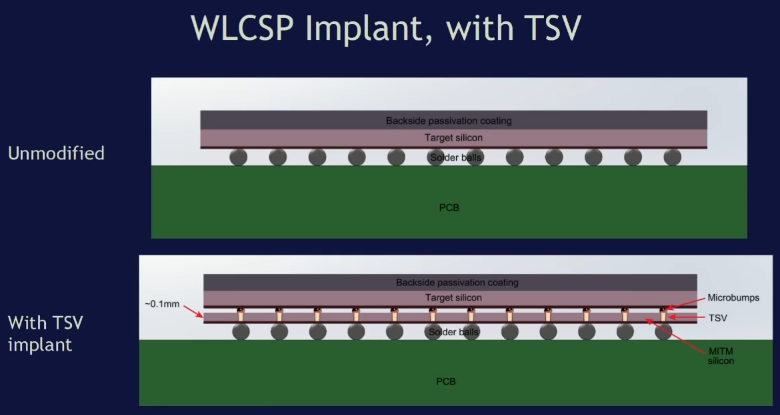
- another chip can be attached to the chip used in the device, the purpose of which is known only to the one who did it.

The figure below shows a diagram illustrating both the degree of difficulty in introducing backdoors and their detection. It is not difficult to trace the dependence - the more complicated the implementation process, the more difficult the detection.

The introduction of one chip under another or changes directly inside the chip is difficult to notice even using x-rays and an electron microscope. But sometimes a visual inspection is enough to understand that something is definitely wrong, for example, if the backdoor was embedded in an already finished device and looks like a separate chip.
All of the above may appear in your device on any of the links in the supply chain, which is not always possible to trace. In most cases, serious structures are involved in the appearance of such backdoors and bookmarks in the imported iron. Because of this, the problem is difficult to fight, and the only way out is independent development and design.

The figure shows several options for the supply chain from the moment the chip is developed to before the user already has it in the device. Dangers "await" him at each link of the chain, and sometimes outside it. There is an option when devices are bought by attackers, backdoors are built into them, and then the attacker returns them to the seller under some pretext. After that, the seller can sell this device again, and thereby expose the new owner to danger.
This is a big security issue worth knowing and remembering. And even buying a device or its parts from well-known vendors that you could trust, you can get not only what you wanted, but also an unpleasant surprise in the form of surveillance and gaining access to personal data.
In the Russian-speaking community of security researchers, the topic of backdoors in iron has also recently been raised. Offer to listen to podcast "Fiction and Reality: backdoors in hardware and firmware" from Noise Security Bit and read an article on the protection of chips from the reverse engineering of amartology .
And in your opinion, how acute is this problem today?
