The cat under the hood. Part 1

In our work, we actively use hashcat, but we began to miss some features in this product. For example: the ability to send notifications, the presence of a unified interface for managing cracking hashes, convenient storage of "cracked" hashes (after a while, looking at hashcat.potfile hurts your eyes). In some situations, it is necessary to perform parallel cracking of hashes, that is, to distribute cracking tasks between several hosts.
In this series of articles, we want to share our "finds" on the topic of management interfaces and / or the distributed launch of the hashcat program, storing statistics on "cracked" hashes. In the first part, we’ll look at some existing solutions, then we’ll take a closer look at the Hashtopolis product.
In general, if the topic is close to you - we ask "under the cut" and in the comments.
Let's talk about cats
A bit about hashcat itself (hashcat)
Hashcat is, according to the creators, the world's fastest password recovery tool. Versions are available for Linux, macOS and Windows, and can be presented in versions based on CPU or GPU.
Hashcat gained its popularity due to the shortcomings found by its creator in other programs that use data encryption. Currently, Hashcat is actively used to select WPA / WPA2 passwords, crack passwords from MS Office documents, PDF, 7-Zip, RAR, TrueCrypt.
A source
The authentication mechanism on the Web is summarized here: https://habr.com/en/post/28534/, and in detail here: https://habr.com/ru/company/dataart/blog/262817/
Before the security researcher (or by the auditor) another task arises - pick up / guess passwords, intercept or bypass authentication passwords.
In case of attacks on passwords, it is possible to divide into two categories (and everything else in the third, for example, the attack "spy on user input"):
- online attacks: multiple authentication attempts by guessing the password, which can "make a lot of noise" or cause account lockout. This is similar to “picking” with master keys in a keyhole - the owners can call the police, or even cause injuries;
- Offline attacks: the attacker managed to get hashes, and a more targeted system is not required for password guessing, the whole process goes on the side of the attacker. As if they managed to get a "cast" of the lock and "pick" away from the guarded door.
Situations may arise such as the selection of passwords for archives, protected documents or private keys, but in general this is a password attack, i.e. you need to pick up the key / combination to the lock.
Most attacks on passwords and hashes can be divided into:
- "Dictionary" (English "dictionary", "wordlist")
- “Forehead” (or “bruteforce” from the English “bruteforce”, ie “brute force”)
- “Hybrid” (dictionary + some brute force mask)
As a result of searching the network for ready-made “interfaces” for working with hashcat, we came across the following solutions:
The names begin with the word 'hash' - from English this word is translated as “hash”, “confusion”, “a dish of finely chopped meat and vegetables”. If you literally translate these names into Russian, the resulting phrases create a mess in the reader’s brain. The name “Hashtopussy” is especially wildly perceived (smile)
Let's start the review with Hashpass . He was interested in the richness of functions (at first glance): the queue of hashes for hacking, visualization of the caught WPA-handshakes on the global map, C2C for “spyware” raspberries, support for SMS informing, beautiful wallpaper, an interesting interface with visualization. The Hashpass job status bar looks like this:
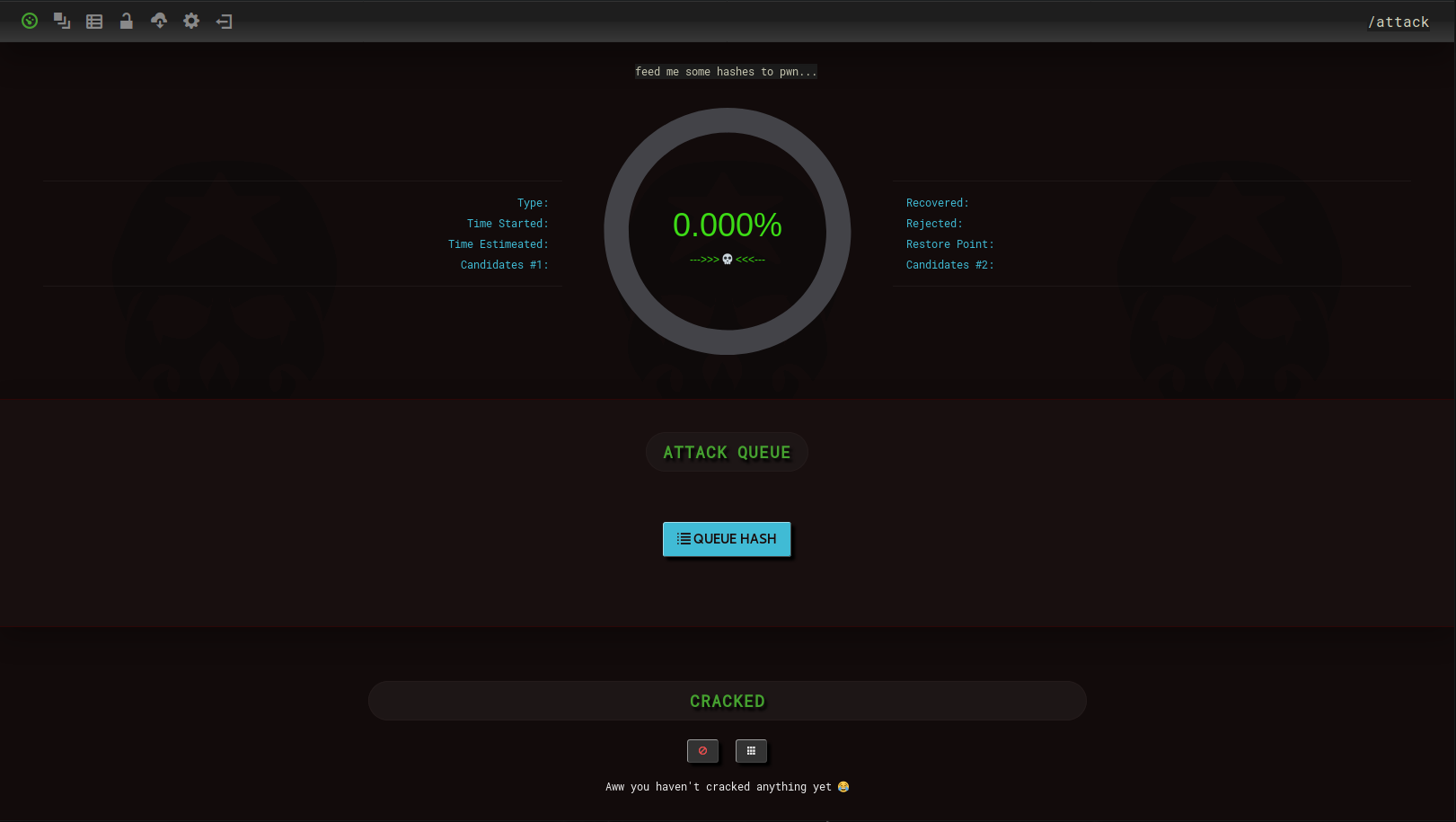
When immersed in the description of the project on GitHub, it was found that for distributed cracking of hashes, dj-zombie developed a separate project, Hive. We were not able to find relevant information about this project. Those. “Out of the box” you cannot get a “conductor’s stick” for parallel hacking on several hosts. As a stand-alone solution, Hashpass is very interesting, and given the Rotten Pi project associated with it, Hashpass is definitely worth paying attention to.
This is where the acquaintance with Hashpass ended, perhaps we will return to its detailed review in a series of articles.
The Hashview project is not inferior to its brother Hashpass in terms of rich functionality, and the approach to the "visual component" of the interface, in our opinion, is better implemented.
Statistics screen example:
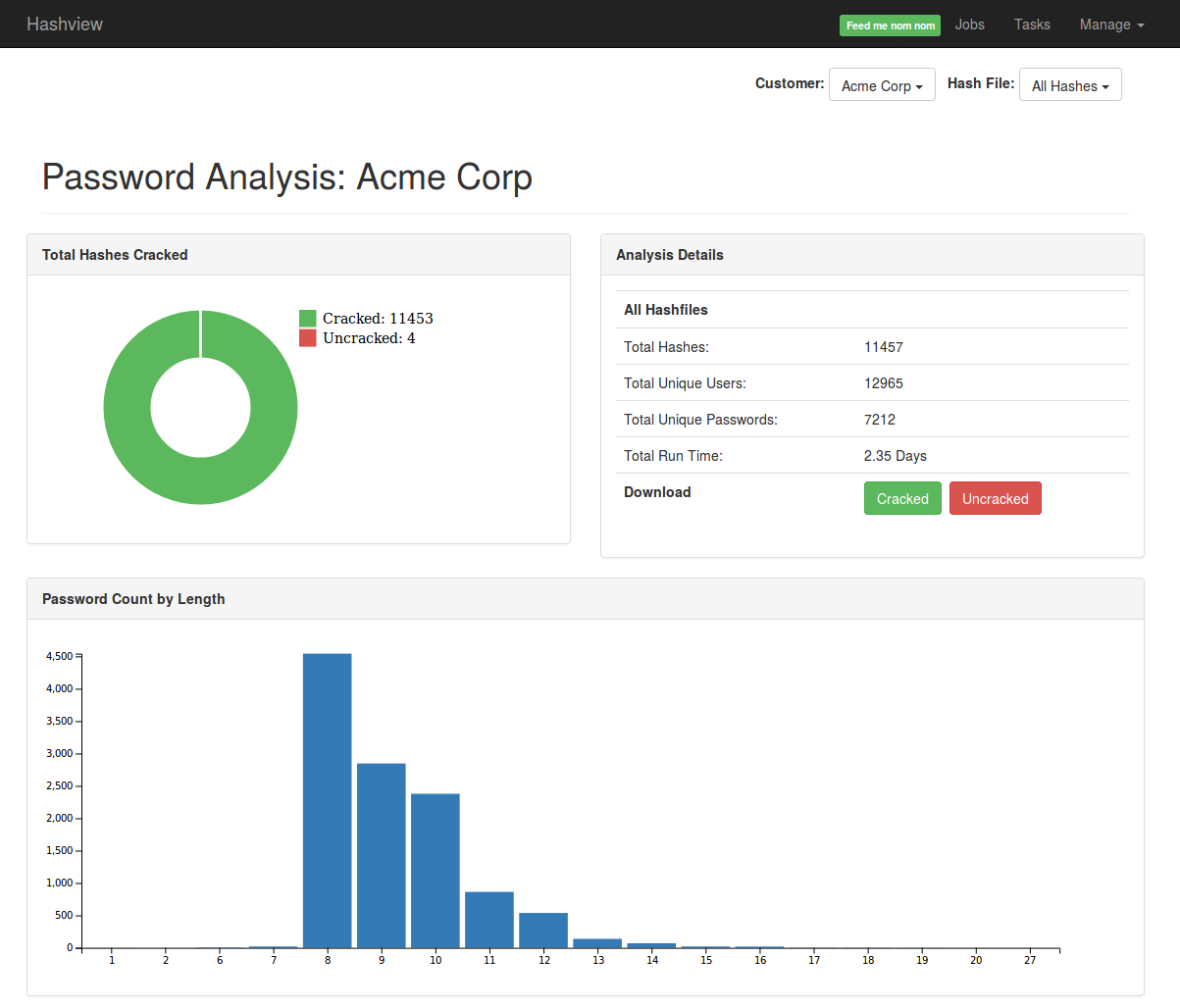
Here is what Hashview has to offer:
- Collaboration - the application supports the creation of separate accounts and the distribution of roles
- OTP (One Time Password) support for user authentication
- Direct access to instance hashcat command line interface
- Create hash cracking task queues
- Event Email Notifications
- Search internal hash database, username, password
- Metrics visualization and reporting system
To install the Hashview server, you need a running hashcat on the host, a valid RVM, MySQL, Redis environment. Officially declared support for Ubuntu versions 14.04 and 16.04, in other Linux distributions, the work of Hashview has been confirmed by the community.
And now about the "cons":
- The project officially supports hashcat 4.x, it is not known about the 5th version support (there is a ticket https://github.com/hashview/hashview/issues/448)
- Agent support is still officially in the "Alpha" version, and in our case, support for Windows agents is important (https://github.com/hashview/hashview/wiki/04-Distributed-Cracking)
Both projects, Hashpass and Hashview, give the impression of abandonment, commits in the repository were long ago, and the documentation is not updated.
We decided to put Hashview on one shelf with Hashpass and move on to the next project.
Hashtopolis was released in 2016 as the development of a “wrapper” for hashcat - Hashtopus (https://github.com/curlyboi/hashtopus). At first it was called “Hashtopussy”, but for reasons of “political correctness” it was renamed “Hashtopolis”. Official project page: https://hashtopolis.org. In fact, this is a forum where you can grab bits of useful information about the product. A channel was also found on Discord: https://discord.gg/S2NTxbz
Hashtopolis features and features:
- Easy + convenient to install and use server / agents
- Access from anywhere via the web interface
- Server-side responsiveness with common web hosting configurations
- Autonomous agents at controlled crack stations
- Manage dictionaries and rules files
- Hashtopolis and Hashcat Auto Update
- Hacking multiple hash lists of the same type as if they were a single list
- A single file to run the agent on Windows, Linux, and OS X
- Files and hashes marked as “secret” are distributed only to agents marked as “trusted”
- Many options for importing and exporting data
- Rich statistics on hashes and running tasks
- Visual representation of the distribution of "portions of hashes" (chunk distribution)
- Multi-user application
- Support user access levels
- Different types of notifications
- Ability to create mini-tasks for cracking hashes by CPU
- Granular distribution of access through the use of groups in the appointment of agents and users
The most “captivating” Hashtopolis feature for us was the support of notifications in Telegram directly out of the box. We use this messenger every day. It seemed extremely attractive to receive timely notifications of “cracked” hashes. Of course, this functionality can be implemented with scripts, but this feature was not the only one that attracted to Hashtopolis.
Hashtopolis can manage hashcat instances starting with version 4.0.0. Also implemented support for "generic crackers" (a common command line interface to the software for "cracking hashes"). More information about “generic crackers” here.
The appearance of the Hashtopolis interface is pleasant, and the navigation becomes clear after a few minutes of acquaintance.
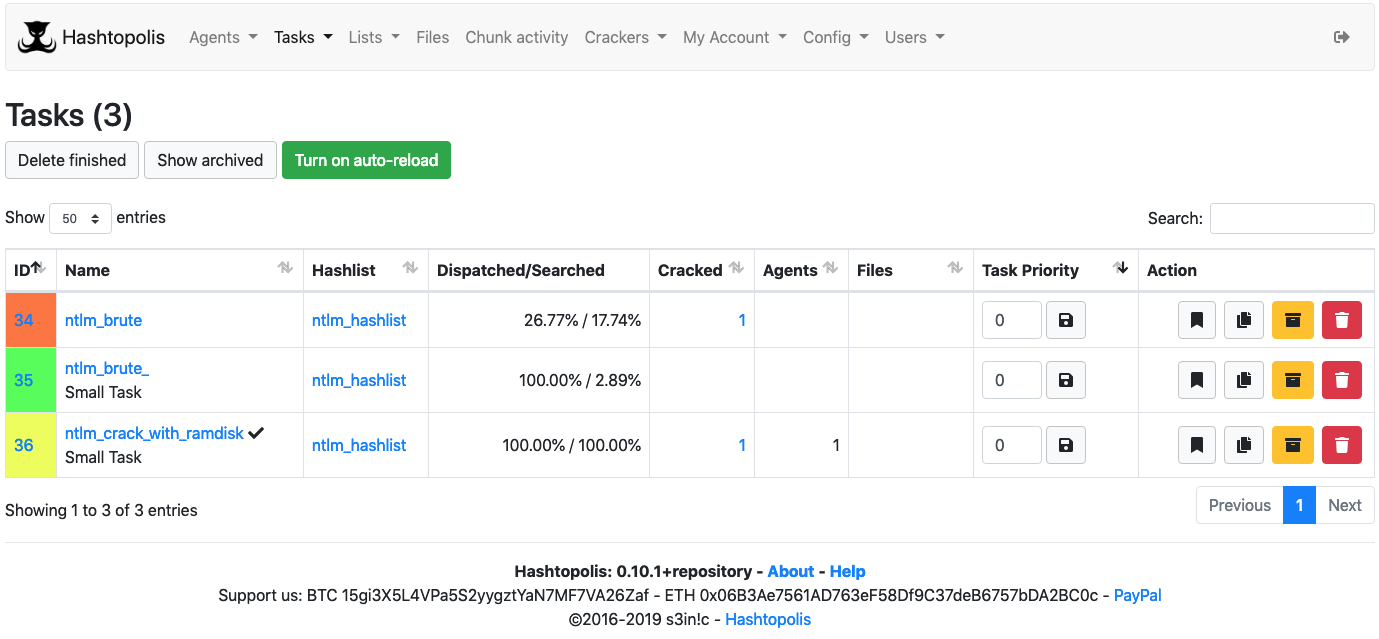
List of tasks:
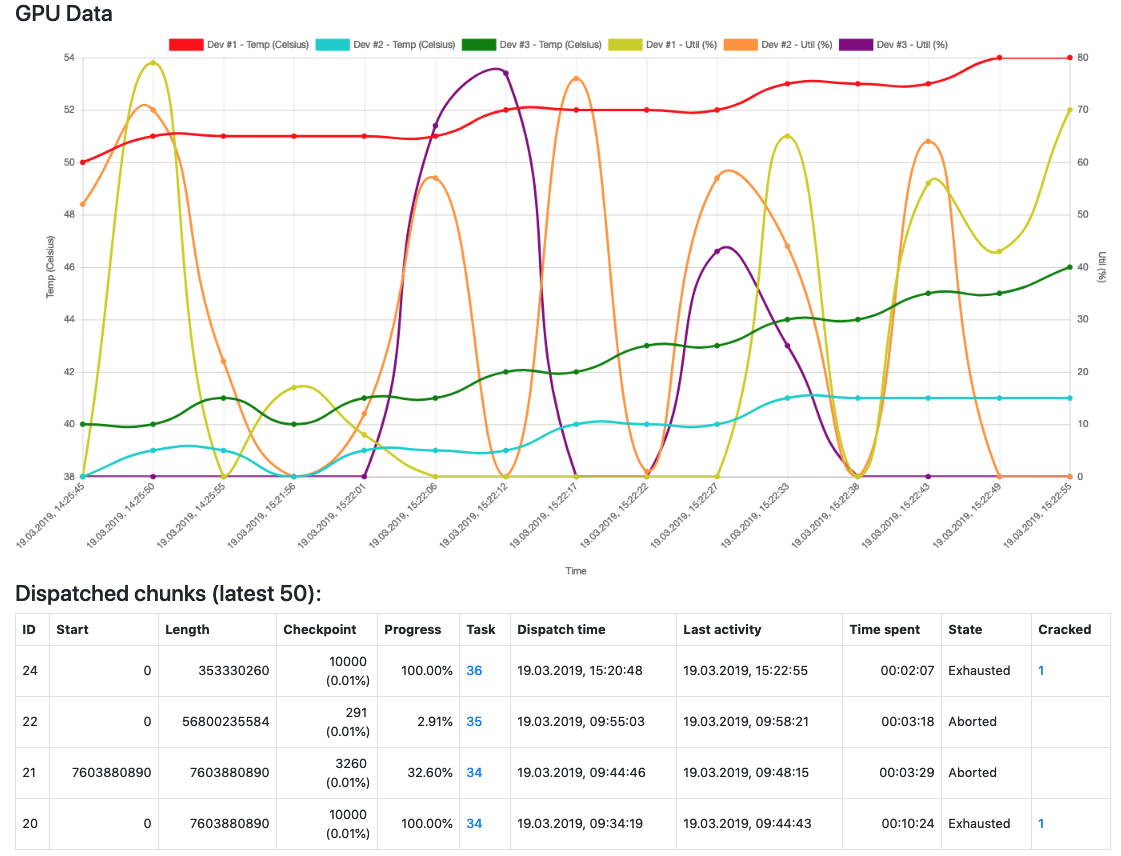
Beautiful statistics on the work of the agent:
Additional sources of information that we have addressed on the topic of Hashtopolis:
- Project repository on GitHub: https://github.com/s3inlc/hashtopolis
- GitHub project wiki page: https://github.com/s3inlc/hashtopolis/wiki
- Blog of one of the project developers (s3inlc): https://s3inlc.wordpress.com
- The Hashtopolis API documentation is provided in a PDF document: https://github.com/s3inlc/hashtopolis/blob/master/doc/protocol.pdf
This concludes the introductory part, we shared our “first impression”. Unfortunately, the reviewed projects do not have the best quality documentation, the information is scattered and presented very concisely.
We hope that we were able to arouse the reader’s interest in the products under consideration, because the more users there are, the better projects will become and, as a result, more information on use will appear.
In the next part, we will analyze the installation and configuration of the Hashtopolis product.
