How to crack a self-service terminal and why 80% of them are under threat
- Translation
Author of the original post in Russian: frsamara
I always loved playing with things and testing them under all sorts of wacky conditions as a kid and even considered getting a job as a tester, but I never did. Nevertheless, I still like taking things made by someone else and poking them for vulnerabilities.
I remember, when first self-service payment terminals started popping around town, I saw one of them put up a browser window while updating, and the game was on — I broke it almost immediately. There’s been a lot of discussion about it since then and developers have started to pay a lot more attention towards security in these machines.
Recently, fast-food joints have started installing these terminals. Obviously, it’s quite convenient: just tap a couple of virtual buttons, place an order, pay with a bank card and wait for your number to show on the screen.
Also, nearly every big mall has these interactive boards with floor plans and information on various sales and discounts.
How secure are they? I decided to find out by breaking one of them, and very quickly I was successful!
The first victim was this innocent terminal at a local Burger King.
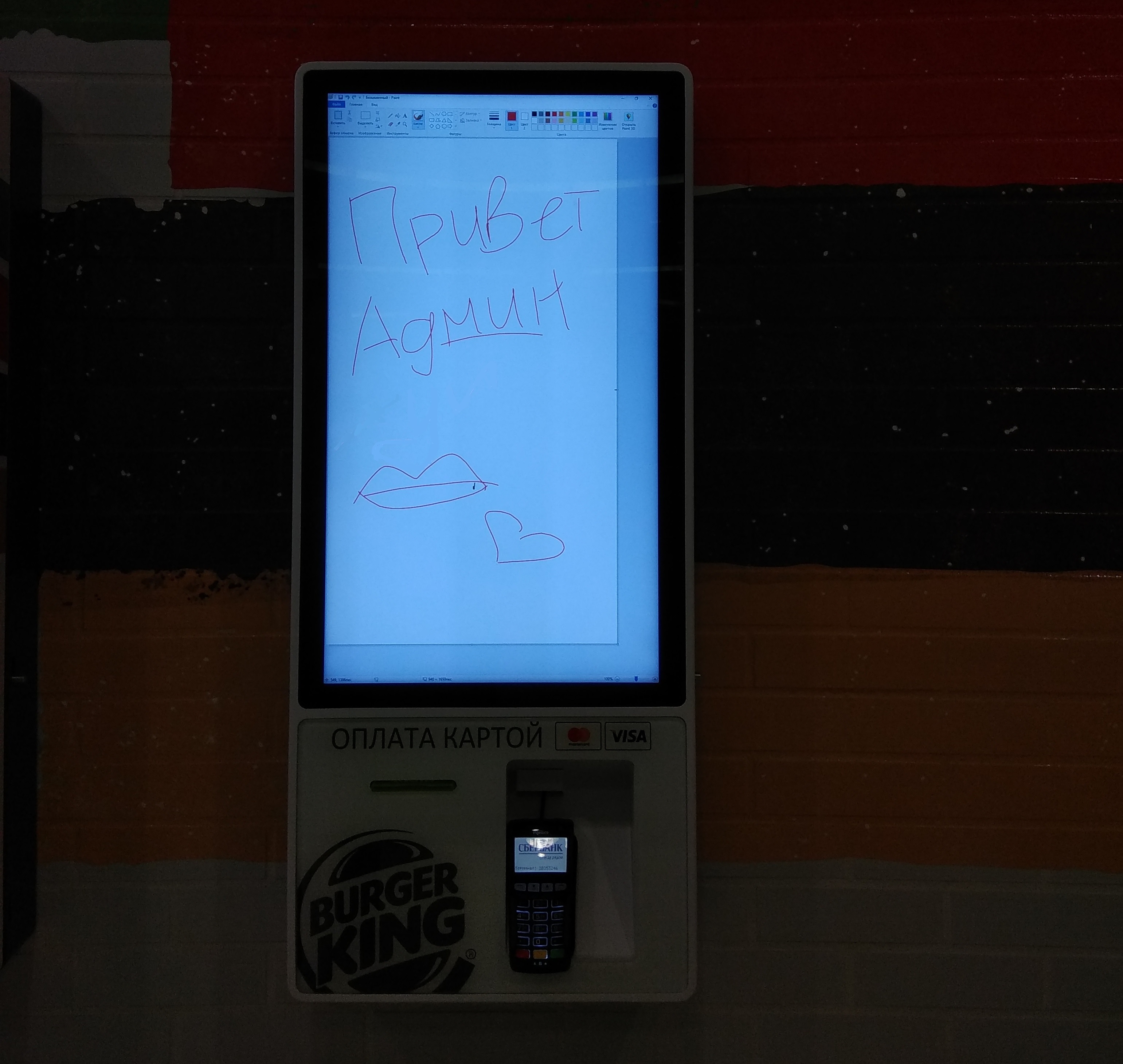
«Hello admin!» in Russian
Simple enough. But the second one has a rather amusing store behind it. I saw this spanking-new terminal at a mall, I poked around and eventually it gave in too.
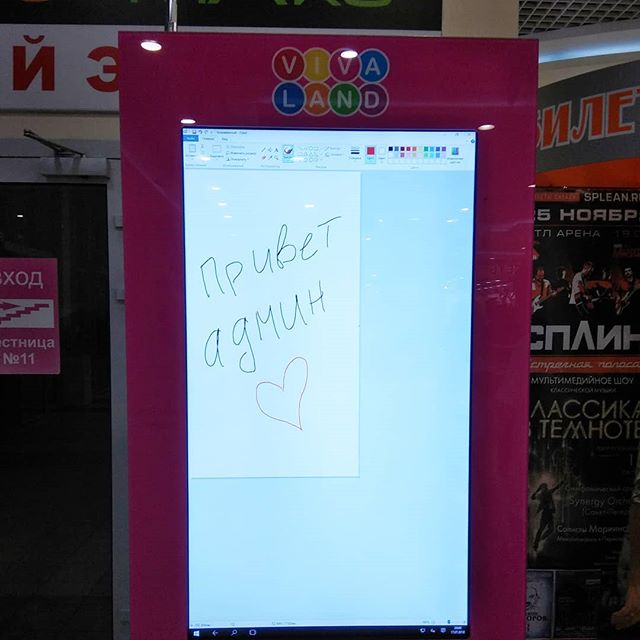
«Hello admin!» in Russian
Very quickly I had mall security up my alley. They told me, not mincing words, how terrible of a person I am for destroying private property, though they couldn’t quite explain how exactly I “destroyed” anything. After a long, winded monologue, the security guard compared it to Hiroshima bombings and how Russia helped Japan to recover… again, I don’t quite understand what Hiroshima and especially Russia’s help have anything to do with it… eventually he compared it to a break-in, on which I told him that opening an app on a terminal isn’t a “break-in”, but a security vulnerability, on which he threatened to “exploit a vulnerability” in my head by putting a bullet through it. :D
And finally, my third victim — another fast-food joint. This time, to avoid any trouble, I quickly put up the Windows control panel, took a photo and left immediately.

To be perfectly fair, the software itself is done pretty well and it’s not to blame for what happened — it was the fault of Windows 10, and to be precise — its gesture features and negligence on behalf of the admins configuring the terminal.
So what happened?
Well, as I said above, WIndows 10 introduced gestures for touch screens, so if you slide your finger from left to right, it opens a notification panel, which then allows you to go anywhere and open anything you want.
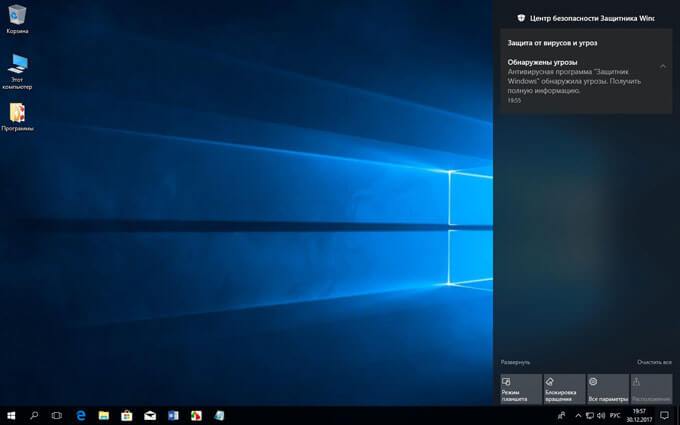
It unlocks everything: Windows Explorer, the registry, the command prompt… and Paint.
So here it is: an easy way to hack 80% of touch-panel terminals and do anything with them.
P.S. No terminal was harmed in the making of this article. No application except Microsoft Paint was ever opened.
I always loved playing with things and testing them under all sorts of wacky conditions as a kid and even considered getting a job as a tester, but I never did. Nevertheless, I still like taking things made by someone else and poking them for vulnerabilities.
I remember, when first self-service payment terminals started popping around town, I saw one of them put up a browser window while updating, and the game was on — I broke it almost immediately. There’s been a lot of discussion about it since then and developers have started to pay a lot more attention towards security in these machines.
Recently, fast-food joints have started installing these terminals. Obviously, it’s quite convenient: just tap a couple of virtual buttons, place an order, pay with a bank card and wait for your number to show on the screen.
Also, nearly every big mall has these interactive boards with floor plans and information on various sales and discounts.
How secure are they? I decided to find out by breaking one of them, and very quickly I was successful!
The first victim was this innocent terminal at a local Burger King.

«Hello admin!» in Russian
Simple enough. But the second one has a rather amusing store behind it. I saw this spanking-new terminal at a mall, I poked around and eventually it gave in too.

«Hello admin!» in Russian
Very quickly I had mall security up my alley. They told me, not mincing words, how terrible of a person I am for destroying private property, though they couldn’t quite explain how exactly I “destroyed” anything. After a long, winded monologue, the security guard compared it to Hiroshima bombings and how Russia helped Japan to recover… again, I don’t quite understand what Hiroshima and especially Russia’s help have anything to do with it… eventually he compared it to a break-in, on which I told him that opening an app on a terminal isn’t a “break-in”, but a security vulnerability, on which he threatened to “exploit a vulnerability” in my head by putting a bullet through it. :D
And finally, my third victim — another fast-food joint. This time, to avoid any trouble, I quickly put up the Windows control panel, took a photo and left immediately.

To be perfectly fair, the software itself is done pretty well and it’s not to blame for what happened — it was the fault of Windows 10, and to be precise — its gesture features and negligence on behalf of the admins configuring the terminal.
So what happened?
Well, as I said above, WIndows 10 introduced gestures for touch screens, so if you slide your finger from left to right, it opens a notification panel, which then allows you to go anywhere and open anything you want.

It unlocks everything: Windows Explorer, the registry, the command prompt… and Paint.
So here it is: an easy way to hack 80% of touch-panel terminals and do anything with them.
P.S. No terminal was harmed in the making of this article. No application except Microsoft Paint was ever opened.
