Safety is paramount. Latest developments for Google Chrome
Hello GT! Not so long ago we talked (albeit on Habré) about the so-called “Red cards” - a system that helps protect users of our search from dangerous content. Today we continue the theme of secure browsing. Filtering search results is relatively easy, but you don’t always go to a new site with Google. A hyperlink leading to a site with dangerous content can be found anywhere, which means that the browser itself must protect users.

We’ll talk about security technologies in Google Chrome today.
We launched the secure browsing program in 2007, when Google Chrome was not yet officially released and worked in beta. The main objective of this system was to protect users from widespread network threats: phishing and various malware. Nevertheless, the complaints of users in the style of: “Everything has broken down for me, instead of the Internet, there is only one advertisement of means to increase the length of sales”, they have not gone away. New threats have been added to familiar threats. Replacing the settings of search engines, start pages, plug-ins, fake software, theft of sessions and other delights of computer malware spread with terrifying speed along with the global spread of broadband Internet access. At that time, our systems were simply not ready to repel so many threats.
About a year ago, we launched a full-scale campaign against such threats, which in general can be called “Unwanted software” or simply “UwS” ( note: pronounced “uz”, from the English Unwanted Software). Well, today is the time to share the results achieved and our vision for the development of protective measures.
First step: before you start the fight with the enemy, you must clearly understand who he is. In our understanding, UwS is a many-sided and inventive Fantomas. He can hide and disguise as much as he wants, but insidious plans will sooner or later surface. So, software should be considered undesirable if it meets one, or better, several of these criteria:
Of course, almost anything can fall under these criteria. We hope that suspicious names like “Sombrero Browser” or “Improver-3000” will make you think that something is wrong here.
Step two: determine how this “infection” spreads. In this case, there are a lot of options, but all of them relate either to misleading the user, or to the inability to “miss” the link. For example, through Javascript, which by any click opens a tab with dangerous content or directly redirects to an infected page.
All sorts of “download” buttons, scrolling through dozens of file hosting services in dozens (and there may be one “correct” of them, and not at all the fact that it managed to appear and was not obscured by the banner); advertisements with a choice of “Yes, continue” and “No, continue”; popup windows; simulations of the play button on videos or dual-resolution files like CelebrityNude.mp4.exe ... There are many options, the essence is the same. Force the user to click on the link, download, install or open a suspicious file.

The enemy has a thousand faces
Having decided on the types of threats and methods of distribution, we were able to effectively counter unwanted software.
We worked on combating UwS on several fronts at once: we trained our Safe Browsing system to respond to such problems, created effective and noticeable warnings for users, and set up the collection of information and statistics. In order not to be limited to empty words, here is a list of "good deeds" that we managed to accomplish.

Despite the fact that the list is not very long, the effect of such events is noticeable. Here is what we have achieved:
The results are more than worthy, but we are still at the beginning of our journey. The ultimate goal - a safe and clean Internet - is still far away: about 20% of the problems with Google Chrome are related specifically to UwS. In addition, according to our data, at least 1 user of our browser out of 10 has encountered (and continues to encounter) reassignment of settings and undesirable software that introduces or replaces advertising on sites.
With desktops, everything is more or less clear. The openness and prevailing methods of software distribution, user habits and the high distribution of computers have led to the situation that we now have. And what about mobile devices? Modern smartphones (running any OS) were initially built on the basis of a rather “closed” platform: the main way to acquire new applications is through an online repository in the form of a store in which moderation is present. At the same time, Android is an open and freedom-loving OS that allows you to install programs in a more “classic” way, although for this you need to manually enable certain settings.
The stores themselves are pretty well protected: Google Play automatically checks applications, but attackers sometimes find a way to leak even with such a strict code review.
A similar “arms race” in the form of defense mechanisms and sophisticated methods of circumventing them will continue for a long time (if not forever), and history knows a lot of examples: from the sword and armor to the thickness of armor plates and the diameter of tank guns. However, not all dangers come to mobile users from applications.
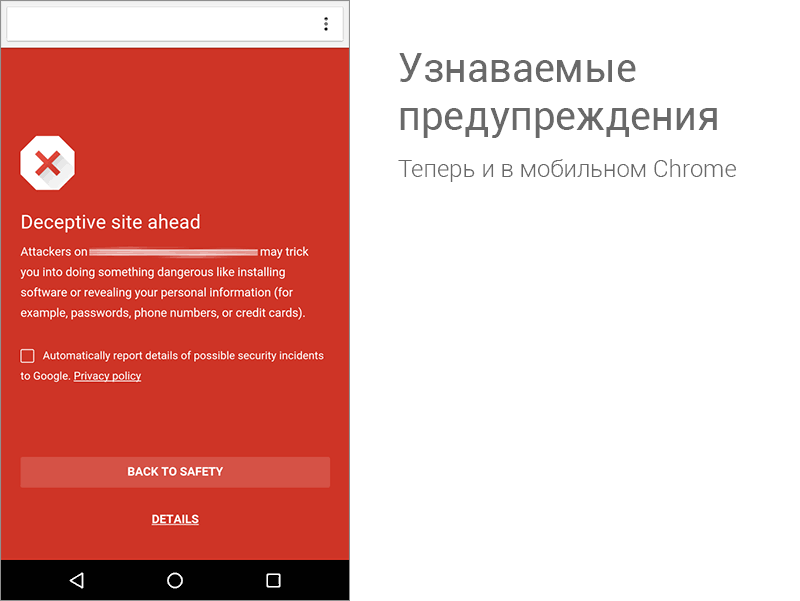
Social engineering (in particular, phishing) requires completely different approaches to protection. Here you can’t simply “prohibit” or “limit”, since the principle of attack is invisibility and mimicry under legal services. To counter such an attack can only be timely collecting relevant information and constantly updating the list of resources with potentially dangerous content. Then the security system will be able to warn the user before he gets into well-placed networks.
Considering not the most comfortable working conditions of mobile devices (network connection can be slow or unstable), unnecessary requests to servers will negatively affect the user experience, which poses additional challenges in the field of ensuring the security of mobile users.
Even the simplest (and obvious!) Solution - storing data on a user device - can be a lot of trouble.
Of course, there are problems, but if you use the Android OS and regularly update available software from Google Play, then most likely you are already protected. Safe Browsing has been part of Google Play Services since version 8.1. The first application that gained access to the database of dangerous sites, of course, was Google Chrome. Since version 46, all users of the Android version of Google Chrome have security enabled by default. You can verify this as follows: open your browser settings, go to the "privacy" tab. It will be indicated below that the Safe Browsing system is active and you are protected. Chrome will now be able to warn you of visits to dangerous sites.
This is exactly the phrase we have heard many times from the developers of the mobile version of Safe Browsing. They were firmly convinced that in this case it is possible and necessary to save at the lowest level. The battery charge and the bandwidth of the mobile Internet are the key characteristics of a smartphone, and the user simply should not notice interference in everyday work and at the same time be as protected as possible from possible threats on the Internet. Therefore, the Safe Browsing mobile system does not transmit a single bit of unnecessary information.
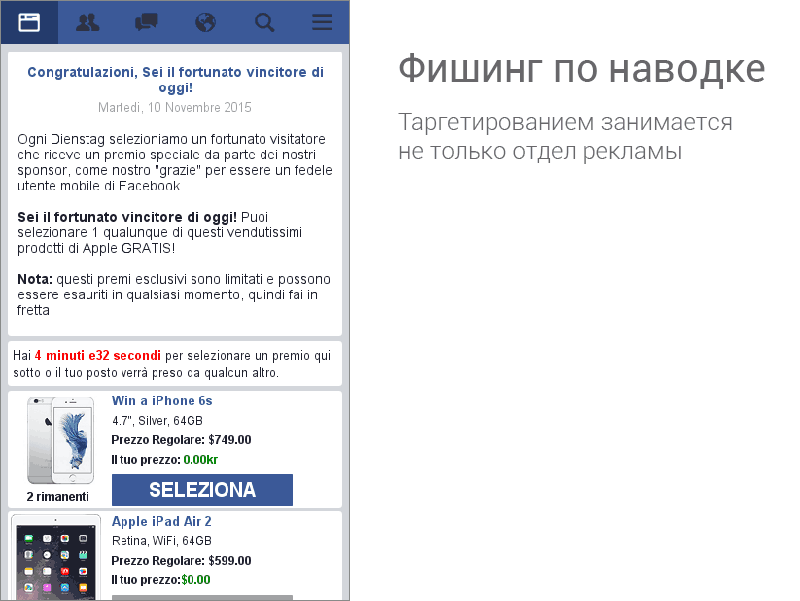
For example, many phishing attacks are concentrated on a specific group of users. It is unlikely that any fake site aimed at the inhabitants of Mexico will be interested in the personal data of Vasya Pupkin from Uryupinsk. And Vasya Pupkin is unlikely to get to the site of the Mexican lottery, especially from the phone. Therefore, lists of dangerous sites contain geolocation information. First of all, only the information relevant to your location comes to your phone.
The second "expense item" on which we tried to "save" is updating lists of dangerous sites. The window of a stable and fast connection can last only a few seconds, and in some countries (for example, in North Africa) they did not even hear about a fast and accessible Internet. So the most relevant and important information to ensure security is sent first.
We also joined forces with the Google team to compress traffic, so the list of dangerous sites update system uses as little CPU time, smartphone resources and, most importantly, traffic as possible. Thus, the real effect of Safe Browsing on the duration of battery life or the bill you set for traffic can be seen only by studying this issue under a microscope.
We are well aware of how important it is to ensure the safety of users of mobile devices. At the same time, we wanted to build a system whose operation the user simply did not notice. Now the share of mobile traffic on the planet is growing every day, and we want to be sure that every user of Android devices is protected as much as possible.
UwS problems are hard to solve by acting alone. We plan to engage key players in the Internet industry in the confrontation with black technologies, join forces and make the Internet safer. Unfortunately, comprehensively solving the problem of unwanted software can only close the ecosystem very much, which contradicts the very spirit of the open Web. In addition, this can be negatively received by users. Therefore, the only acceptable way is to unite and develop strict, transparent and effective policies in the field of confronting various malware.
By teaming up and developing a unified strategy, we will be able to effectively raise the level of user security, regardless of whose final technologies they will use. We gladly met the news that FTK ( Note:The U.S. Federal Trade Commission ) launched a campaign to notify users of the dangers of UwS, and characterizes UwS as malware: that is, unwanted software, the creation of which is often prosecuted by law.
The war against unwanted software has just begun, but we are moving in the right direction and will continue to step on the tail of the authors and distributors of such programs, protecting the personal data of our users.

We’ll talk about security technologies in Google Chrome today.
Google Chrome on desktops
We launched the secure browsing program in 2007, when Google Chrome was not yet officially released and worked in beta. The main objective of this system was to protect users from widespread network threats: phishing and various malware. Nevertheless, the complaints of users in the style of: “Everything has broken down for me, instead of the Internet, there is only one advertisement of means to increase the length of sales”, they have not gone away. New threats have been added to familiar threats. Replacing the settings of search engines, start pages, plug-ins, fake software, theft of sessions and other delights of computer malware spread with terrifying speed along with the global spread of broadband Internet access. At that time, our systems were simply not ready to repel so many threats.
About a year ago, we launched a full-scale campaign against such threats, which in general can be called “Unwanted software” or simply “UwS” ( note: pronounced “uz”, from the English Unwanted Software). Well, today is the time to share the results achieved and our vision for the development of protective measures.
What is Unwanted Software and how does it get onto my computer?
First step: before you start the fight with the enemy, you must clearly understand who he is. In our understanding, UwS is a many-sided and inventive Fantomas. He can hide and disguise as much as he wants, but insidious plans will sooner or later surface. So, software should be considered undesirable if it meets one, or better, several of these criteria:
- It offers the user something that 100% cannot do. For example, speed up the computer 5 times;
- Uses tricks and hacks during installation: sticks to other installers, hides under the guise of another program, does not show that the option can be removed, etc .;
- During installation, the user does not disclose all operating principles and main tasks, as well as software functions;
- Interacts with the operating system in an unexpected way. For example, you put a video player, and he put a search everywhere that you never used and were not going to try, and it also shows ads on your desktop;
- Collects and transfers personal information without the knowledge of the user;
- It is bundled with other software, and no one talks about the presence of a “gift” to the user;
- And, finally, 100% software is undesirable if its removal is fraught with any difficulties or complications.
Of course, almost anything can fall under these criteria. We hope that suspicious names like “Sombrero Browser” or “Improver-3000” will make you think that something is wrong here.
Step two: determine how this “infection” spreads. In this case, there are a lot of options, but all of them relate either to misleading the user, or to the inability to “miss” the link. For example, through Javascript, which by any click opens a tab with dangerous content or directly redirects to an infected page.
All sorts of “download” buttons, scrolling through dozens of file hosting services in dozens (and there may be one “correct” of them, and not at all the fact that it managed to appear and was not obscured by the banner); advertisements with a choice of “Yes, continue” and “No, continue”; popup windows; simulations of the play button on videos or dual-resolution files like CelebrityNude.mp4.exe ... There are many options, the essence is the same. Force the user to click on the link, download, install or open a suspicious file.

The enemy has a thousand faces
Having decided on the types of threats and methods of distribution, we were able to effectively counter unwanted software.
One year later
We worked on combating UwS on several fronts at once: we trained our Safe Browsing system to respond to such problems, created effective and noticeable warnings for users, and set up the collection of information and statistics. In order not to be limited to empty words, here is a list of "good deeds" that we managed to accomplish.
- We have added unwanted software lists to the Safe Browsing system and its open API, so users of Chrome and other browsers receive a warning that the site is unsafe and spreads nasty things:

- We launched a special utility called Chrome Cleanup Tool , which in one click kills all currently known malware from the browser;
- We also hit financing one of the largest UwS categories: website advertising injectors. To do this, we found out exactly what the attackers earn and upgraded DoubleClick Bid Manager . The new filter removes views generated by unwanted software before bidding;
- Sites that distribute UwS get a black mark , which lowers their position in the search results. The longer the site distributes unwanted software, the further it “falls through” in the search results down;
- And finally, we turn off ads in our ad network if we find that unwanted software is being distributed on the target site.
Despite the fact that the list is not very long, the effect of such events is noticeable. Here is what we have achieved:
- The number of complaints related to unwanted software has halved. A year ago, before the launch of the program to combat UwS, complaints about such software accounted for up to 40% of the total. Now the indicators have fallen - now UwS accounts for no more than 20%;
- Every day we show more than 5 million warnings about unwanted software in the Chrome browser;
- We have helped over 14 million users remove more than 190 different malicious extensions for Chrome;
- Compared to last year, the number of warnings about unwanted software from the AdWords network has decreased by 95%. In general, no more than 1% of the total number of UwS come from Adwords.
The results are more than worthy, but we are still at the beginning of our journey. The ultimate goal - a safe and clean Internet - is still far away: about 20% of the problems with Google Chrome are related specifically to UwS. In addition, according to our data, at least 1 user of our browser out of 10 has encountered (and continues to encounter) reassignment of settings and undesirable software that introduces or replaces advertising on sites.
Protecting Mobile Users
With desktops, everything is more or less clear. The openness and prevailing methods of software distribution, user habits and the high distribution of computers have led to the situation that we now have. And what about mobile devices? Modern smartphones (running any OS) were initially built on the basis of a rather “closed” platform: the main way to acquire new applications is through an online repository in the form of a store in which moderation is present. At the same time, Android is an open and freedom-loving OS that allows you to install programs in a more “classic” way, although for this you need to manually enable certain settings.
The stores themselves are pretty well protected: Google Play automatically checks applications, but attackers sometimes find a way to leak even with such a strict code review.
A similar “arms race” in the form of defense mechanisms and sophisticated methods of circumventing them will continue for a long time (if not forever), and history knows a lot of examples: from the sword and armor to the thickness of armor plates and the diameter of tank guns. However, not all dangers come to mobile users from applications.

Actual problems
Social engineering (in particular, phishing) requires completely different approaches to protection. Here you can’t simply “prohibit” or “limit”, since the principle of attack is invisibility and mimicry under legal services. To counter such an attack can only be timely collecting relevant information and constantly updating the list of resources with potentially dangerous content. Then the security system will be able to warn the user before he gets into well-placed networks.
Considering not the most comfortable working conditions of mobile devices (network connection can be slow or unstable), unnecessary requests to servers will negatively affect the user experience, which poses additional challenges in the field of ensuring the security of mobile users.
Even the simplest (and obvious!) Solution - storing data on a user device - can be a lot of trouble.
- Mobile data charges may apply. Not everyone has unlimited, so the size of the base matters;
- The data transfer speed in mobile networks can be excellent (in large cities with developed 4G infrastructure) and depressing (hi, grandmother’s village and barely alive Edge), so again, the size of the database matters;
- The time of an active session and reliable connection can also vary within wide limits. So urgent delivery of critical updates can turn into problems. Again, the size of the base is of great importance.
How did we deal with this?
Of course, there are problems, but if you use the Android OS and regularly update available software from Google Play, then most likely you are already protected. Safe Browsing has been part of Google Play Services since version 8.1. The first application that gained access to the database of dangerous sites, of course, was Google Chrome. Since version 46, all users of the Android version of Google Chrome have security enabled by default. You can verify this as follows: open your browser settings, go to the "privacy" tab. It will be indicated below that the Safe Browsing system is active and you are protected. Chrome will now be able to warn you of visits to dangerous sites.
You have bold bytes
This is exactly the phrase we have heard many times from the developers of the mobile version of Safe Browsing. They were firmly convinced that in this case it is possible and necessary to save at the lowest level. The battery charge and the bandwidth of the mobile Internet are the key characteristics of a smartphone, and the user simply should not notice interference in everyday work and at the same time be as protected as possible from possible threats on the Internet. Therefore, the Safe Browsing mobile system does not transmit a single bit of unnecessary information.

For example, many phishing attacks are concentrated on a specific group of users. It is unlikely that any fake site aimed at the inhabitants of Mexico will be interested in the personal data of Vasya Pupkin from Uryupinsk. And Vasya Pupkin is unlikely to get to the site of the Mexican lottery, especially from the phone. Therefore, lists of dangerous sites contain geolocation information. First of all, only the information relevant to your location comes to your phone.
The second "expense item" on which we tried to "save" is updating lists of dangerous sites. The window of a stable and fast connection can last only a few seconds, and in some countries (for example, in North Africa) they did not even hear about a fast and accessible Internet. So the most relevant and important information to ensure security is sent first.
We also joined forces with the Google team to compress traffic, so the list of dangerous sites update system uses as little CPU time, smartphone resources and, most importantly, traffic as possible. Thus, the real effect of Safe Browsing on the duration of battery life or the bill you set for traffic can be seen only by studying this issue under a microscope.
Increased mobility
We are well aware of how important it is to ensure the safety of users of mobile devices. At the same time, we wanted to build a system whose operation the user simply did not notice. Now the share of mobile traffic on the planet is growing every day, and we want to be sure that every user of Android devices is protected as much as possible.
Prospects for combating unwanted software: bringing industry giants together
UwS problems are hard to solve by acting alone. We plan to engage key players in the Internet industry in the confrontation with black technologies, join forces and make the Internet safer. Unfortunately, comprehensively solving the problem of unwanted software can only close the ecosystem very much, which contradicts the very spirit of the open Web. In addition, this can be negatively received by users. Therefore, the only acceptable way is to unite and develop strict, transparent and effective policies in the field of confronting various malware.
By teaming up and developing a unified strategy, we will be able to effectively raise the level of user security, regardless of whose final technologies they will use. We gladly met the news that FTK ( Note:The U.S. Federal Trade Commission ) launched a campaign to notify users of the dangers of UwS, and characterizes UwS as malware: that is, unwanted software, the creation of which is often prosecuted by law.
The war against unwanted software has just begun, but we are moving in the right direction and will continue to step on the tail of the authors and distributors of such programs, protecting the personal data of our users.
Sources:
Protecting hundreds of millions more mobile users by Noé Lutz, Nathan Parker, Stephan Somogyi; Google Chrome and Safe Browsing Teams.
Year one: progress in the fight against Unwanted Software by Moheeb Abu Rajab, Google Security Team.
Year one: progress in the fight against Unwanted Software by Moheeb Abu Rajab, Google Security Team.
