InterApp device steals passwords, contacts and photos from smartphones and leaves no traces
Tel Aviv-based startup Rayzone Group, executing orders for the defense of Israel, has released a small InterApp device that can simultaneously crack hundreds of smartphones on Android and iOS and receive logins and passwords from social networks, email, DropBox, photos from the gallery, contact list and information about geolocation. The main condition is WiFi enabled.
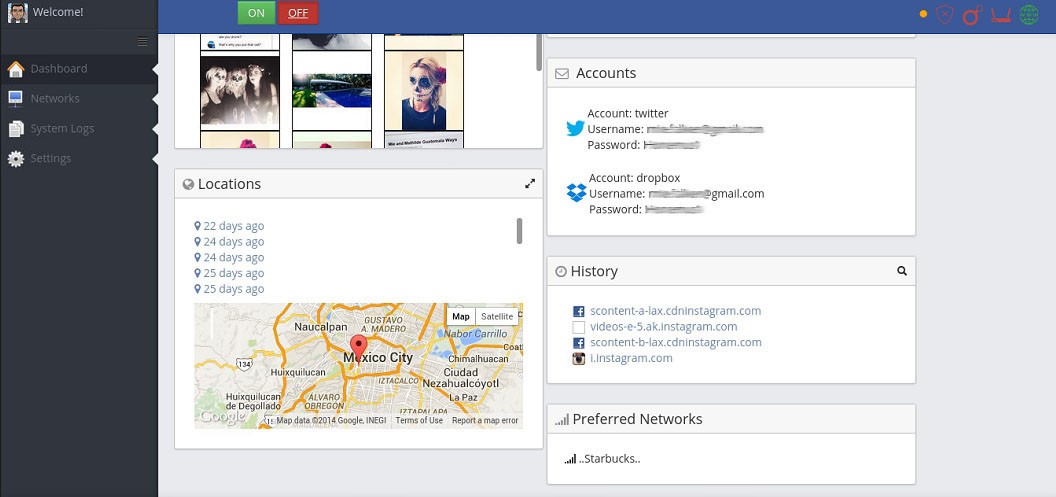
API for InterApp device
company RayZone describes your product InterAppas an intelligent system changing the rules of the game, designed for security and armed agencies, allowing them to quietly collect information using vulnerabilities in applications on the smartphone. To use the device, you don’t need any technical skills, judging by the screenshot of the interface - the application is quite simple and intuitive. The device runs on different platforms and simultaneously receives data from hundreds of smartphones on iOS and Android operating systems. Such a device will be useful to anti-terrorist and security services in crowded places - for example, at airports and shopping centers.
All that is needed from the attacked gadgets is the included WiFi module. Connections to any network and surfing the Internet are not required. There are no details about how the gadget works. Buy the device does not work - company representatives say that it is intended exclusively for government services, and do not answer journalists' questions.
Rayzone states that the device does not leave any traces of its presence on smartphones.
According to the brochure, InterApp receives the following data from the devices it attacks:
Among the company's other products are the TA9 big data analysis platform, a gripper for IMSI identifiers in 2G, 3G and 4G Pirahna networks, a device for detecting and neutralizing other ArrowCell IMSI traps, and the GeoMatrix geolocation intelligent system. RayZone is part of the Hacking Team , an Italian developer of user penetration and surveillance systems.
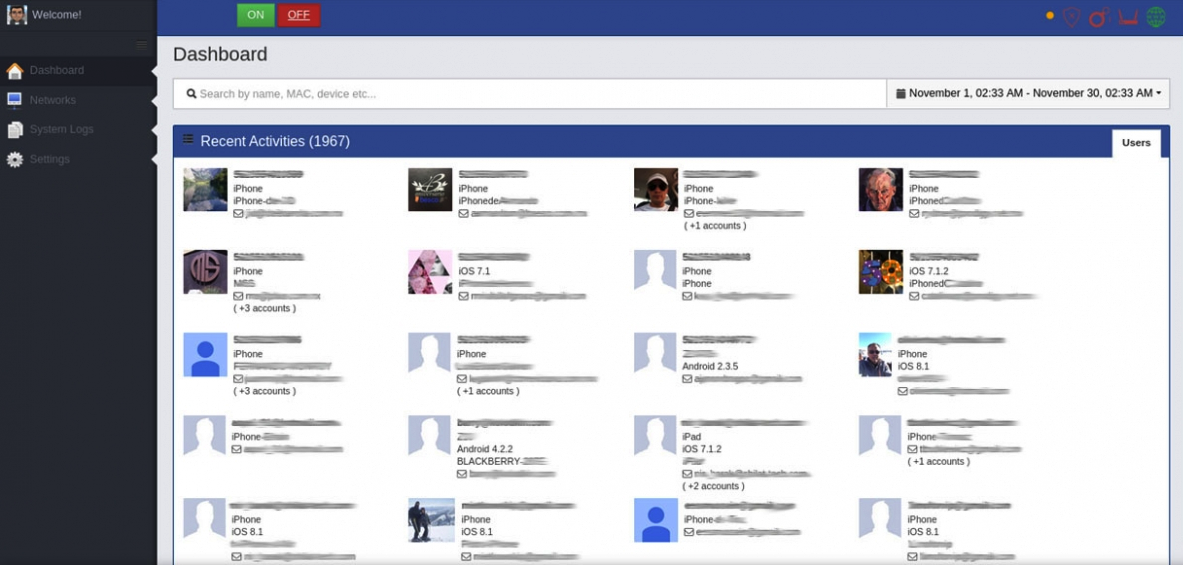
Application screenshot

InterApp device
Information security experts advise against using WiFi on smartphones, as devices are easier to crack. The British company Sensepost found out that with the help of drones you can penetrate gadgets flying over the city. Smartphones continuously send signals in an attempt to find familiar WiFi networks and connect to them, even if it is a cafe network in which the user was sitting a few weeks ago. Sensepost used a regular Amazon-bought quadrocopter and the Snoopy software they wrote, which looked for these signals and tricked the device into pretending to be a familiar network. After connecting to the quadrocopter, all data from email applications, Facebook and even banking software was sent to people who control the drone.


API for InterApp device
company RayZone describes your product InterAppas an intelligent system changing the rules of the game, designed for security and armed agencies, allowing them to quietly collect information using vulnerabilities in applications on the smartphone. To use the device, you don’t need any technical skills, judging by the screenshot of the interface - the application is quite simple and intuitive. The device runs on different platforms and simultaneously receives data from hundreds of smartphones on iOS and Android operating systems. Such a device will be useful to anti-terrorist and security services in crowded places - for example, at airports and shopping centers.
All that is needed from the attacked gadgets is the included WiFi module. Connections to any network and surfing the Internet are not required. There are no details about how the gadget works. Buy the device does not work - company representatives say that it is intended exclusively for government services, and do not answer journalists' questions.
Rayzone states that the device does not leave any traces of its presence on smartphones.
According to the brochure, InterApp receives the following data from the devices it attacks:
- User email addresses, passwords and contents
- Passwords and logins from Twitter, Facebook and other social networking applications
- Password and DropBox Content
- MSISDN and IMEI Identifiers
- MAC address, model and operating system of the device
- List of contacts
- Photo
- Personal information: gender, age, address, education and so on.
Among the company's other products are the TA9 big data analysis platform, a gripper for IMSI identifiers in 2G, 3G and 4G Pirahna networks, a device for detecting and neutralizing other ArrowCell IMSI traps, and the GeoMatrix geolocation intelligent system. RayZone is part of the Hacking Team , an Italian developer of user penetration and surveillance systems.

Application screenshot

InterApp device
Information security experts advise against using WiFi on smartphones, as devices are easier to crack. The British company Sensepost found out that with the help of drones you can penetrate gadgets flying over the city. Smartphones continuously send signals in an attempt to find familiar WiFi networks and connect to them, even if it is a cafe network in which the user was sitting a few weeks ago. Sensepost used a regular Amazon-bought quadrocopter and the Snoopy software they wrote, which looked for these signals and tricked the device into pretending to be a familiar network. After connecting to the quadrocopter, all data from email applications, Facebook and even banking software was sent to people who control the drone.

