On the other side of the war. German encryption devices

"If you know the place and time of the battle, then for thousands, can you fight." - Chinese commander Zhuge Liang (181 - 234 gg.)
The beginning of the twentieth century was marked by the emergence and creation of a new type of weapon for the struggle for dominance on the world stage - information weapons. An important component of state command and control of the armed forces was the communications system, which was able to effectively influence the course of military battles, directly influence the command and control system, and sometimes partially disable it. Such weapons are extremely dangerous for secure systems, encryption systems. If it was possible to seize the ciphers or keys to them, the opportunity was given not only to possess the information transmitted through these communication lines, but also to send false instructions, orders, encrypting them with the enemy’s cipher.
Functional Spireor "radio game" - the first procedure for imposing false commands to the enemy, was used during the First World War. The impact of radio games on the course of military battles was amazing. This was realized primarily by England and Germany. They have made tremendous efforts to create and develop their special services, which pay close attention to radio games. By the beginning of World War II, these countries became the leading countries in the field of information weapons.

In Nazi Germany, two special services were simultaneously engaged in radio games with the enemy - military intelligence (Abwehr) and the Main Directorate of Imperial Security (RSHA). In the period from 1920 to 1944, all official bodies and units of the Reichswehr, and later the Wehrmacht, intended for counterintelligence, espionage and sabotage acts, were called abwehr. RSHA is the governing body of the political intelligence and security police of the Third Reich.

In the memoirs of Walter Schellenberg, the former head of the VI Directorate of the Main Directorate of Imperial Security (RSHA):
In the field of radio intelligence, Germany has achieved exceptional success. We could intercept radio talks that were conducted between units at the front, and often received important information about troop movements and upcoming operations. The technique of using illegal enemy transmitters was developed. It consisted of the following: after detecting and capturing these transmitters, we continued to work for them on behalf of the enemy and ourselves selected the material for transmission, with some of the data being correct and some of it fictitious. So we very often misled the enemy on issues of particular importance. Sometimes we played a game so successfully that we asked for the expulsion of new agents, codes, weapons, money or explosives. It seemed to the enemy that he was expanding the network of his agents, while in reality he wasted huge amounts of money and valuable personnel. We played a particularly successful game with the Moscow radio center. There was a time when we had about sixty-four radio stations seized from the enemy, working for Moscow.

Otto Skorzeny (who was the commander of the Fridental special forces), the “Saboteur” of all the saboteurs of the Reich, devoted an entire chapter in his memoirs devoted to the radio games of the German counterintelligence.
It was a real revelation for me a lot of what I learned about the counter-intelligence activities of our special services during a trip to the Netherlands (the Third Directorate and Zipo were involved in the RSHA spies). I was amazed at the frenzied activity the British developed in this area. Almost every night, planes dropped parachutists, saboteurs, spies and saboteurs over our territory, or supplied the already deployed agents with radios, explosives, weapons and the like ... Our Dutch colleagues managed to conduct English reconnaissance and organize a “radio game”. Our services captured 10 radio stations with a complete set of “keys” and codes. The captured British radio operators, under the control of German counterintelligence, sent carefully and reliably prepared misinformation via communication channels. During the “game” we were able to expose the organization operating in the Netherlands, consisting of several hundred people. The "underground" was carefully "mothballed" and inactive. It was decided to leave them for the time being free, so as not to disrupt the successful "radio game" "
Successes of the opposite side. Scientific and technical achievements of German engineers in the field of radio interception and cryptography.

For communication between units at the front during the First World War, a one-pass with grounding field telephone was used. Since the only wire was on its territory, the military command was confident that the enemy could eavesdrop on their conversations only by directly connecting to the telephone line. Military posts controlled the area where the cable ran, and the army command did not worry that telephone conversations could be eavesdropped, so they did not take any protective measures while conducting secret conversations.
Knowing the physical basis of radio reception, such a conviction would not have arisen. In 1915, the British Expeditionary Force faced this problem in France. It became known that the Germans were able to learn with enviable regularity about their military operations and hinder their implementation. It seemed that the Germans received copies of orders for the planned offensive of the British troops.
Later it turned out that the Germans created a device that, through a network of copper wires or metal rods dug near the lines of the British troops, could receive even the weakest currents created by improper grounding of the telephone system. The supersensitive amplifier received and amplified stray currents from incorrect grounding. Thus, the Germans had the opportunity to listen to all the telephone calls of the British military at a distance of up to 500 meters, intercepting their messages.
Fu.HEv - overview (“snoop”) VHF receiver for monitoring the ether


Frequency range - 25 ... 176 MHz
Powered by a 2.4 NC 58 battery and 90 V anode battery
Dimensions 365 x 453 x 252 mm
Weight - 27 kg together with the equipped shipping box
Fu.HEc - overview ("slash") HF receiver for monitoring the ether


Frequency range - 3.75 ... 25 MHz
Types of work - TLG (A1) and TLF (A3)
Powered by 2 V 38 or 2.4 NC batteries 58 and 90 V anode battery
Dimensions 365 x 453 x 284 mm
Weight - 27 kg
Until 1940, almost 85% of the information transmitted by state and military organizations of the world was broadcast via underground and underwater cables. Technical intelligence to obtain classified information was also conducted underground, where there were telephone and telegraph cables.
In Germany, the war years did not have a single national decryption service. Each agency interested in obtaining information through cryptanalysis created its own service, which basically worked independently of the other secret service. So at the beginning of 1919, the “Z” branch was created in the German Ministry of Foreign Affairs. The employees of this department were engaged in cryptanalysis of diplomatic correspondence of foreign countries. Cryptanalysts from the “Z” branch on the eve and during the Second World War managed to uncover codes and codes of more than 30 states, among which were opponents (USA, England, France) and allies (Japan, Italy) of Germany. The information "obtained" by deciphering diplomatic correspondence was reported to the Minister of Foreign Affairs of Germany Ribentrop and personally to Hitler.
The Wehrmacht (SV), the Luftwaffe (Air Force) and the Kriegsmarine (Navy) had their own decryption services.
There was also a central decryption agency that provided information to the main command, and field decryption agencies working directly on the front line in the interests of local commanders.
The cryptographic bureau within the VNV (Shi) and its units from the very beginning of the war controlled a very significant amount of enemy communications. For example, in January 1940 they intercepted 796 British radiograms, 460 French, 209 Turkish, 163 American, and in March of the same year - 1,649 Soviet, 838 British, 676 French, 49 Spanish, 43 Polish, 40 Vatican, 39 Portuguese.
In early 1939, the Mead code crackers were divided into two specialization groups. Conventionally, they can be called mathematicians and linguists. Mathematics was headed by a doctor from the University of Heidelberg Kunze. Back in the 1920s, he was distinguished by the fact that he was able to open several British ciphers and the French diplomatic code, as well as two sophisticated Japanese machine ciphers, over which American experts were unsuccessfully puzzled.
By the beginning of World War II, more than 100,000 thousand people worked in the services of radio interception, encryption and decryption of Germany. Services were the most powerful in the world.
The most important reason for the outstanding success of German cryptographic services was the research and unique developments of German scientists and engineers in the field of mathematical analysis, reception, transmission and processing of signals of various shapes, frequencies and powers.
In the pace of the development of new radio facilities in the prewar years, Germany was significantly ahead of both the USSR and the allies. This was objectively due to the fact that it was in Germany in the early 1930s that inventions were patented, which largely determined the development of radio engineering for many decades.
Field telephone FF-33 - used in Wehrmacht infantry units

. German engineers invented the undulator to intercept and analyze telegrams transmitted by Morse code.. This is a self-recording device that extends roll paper on which zigzag rectangular images of dots and a dash of Morse code are written out. A special group of analysts could identify the radio operator’s handwriting rather accurately by the length of the intervals and then determine their belonging to a specific surface ship or enemy submarine.
For an illustrative example, I found a photo, though not of a German machine, on which a set of devices for conducting high-speed documentary telegraphic communication via radio CT-2 mod. 1936 , number three undulator.



Based on this analysis, automatic simulators of the work of enemy radio operators were created, which allowed German intelligence to effectively conduct radio games. German cryptanalysts even used IBM computers, as well as various tabs to sort texts and count symbol frequencies and intervals. Using cryptanalysis, they quickly and efficiently searched for duplicate or standing groups of the same size, determined the key length, searched for gamma and stable connections.
By 1938, Germany had become a world leader in the production of special equipment for reconnaissance. A variety of tape recorders, including small-sized, miniature microphones, eavesdropping systems were considered the best in the world, because they were developed in accordance with the latest achievements of German science in the field of radio engineering and chemistry.

the Berta knapsack combined-arms all-wave receiver 1935; the

transported infantry radio station Friedrich 1940
By the beginning of World War II, German cryptographers could decrypt most of the encrypted messages transmitted over cable radio communications lines in Europe.
This was facilitated by the fact that many international telephone and telegraph cables passed through the territory of Germany. German cryptographers have made significant progress in decrypting the S-36 and S-37 encryptors produced by the Hagelin company (the founder of the company, Boris Hagelin, was born in 1892 in Russia), with which the most important government and military organizations of France, Belgium, Denmark, the Netherlands and Norway were equipped.)
cryptographic device of the company Hagelin S-35


cryptographic device of the company Hagelin S-36

cryptographic device of the company Hagelin S-38


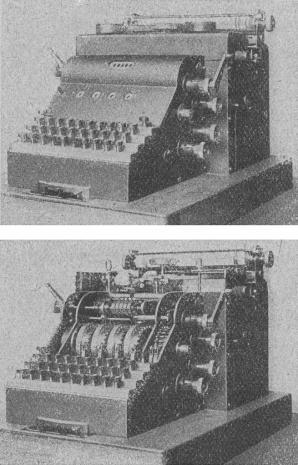
In 1936, France purchased 5,000 sets of B-21 cryptographic equipment from Hagelin, but German cryptographers did not leave any hope to decrypt these types of machines, as they already had experience in decrypting the first cryptographic devices of Hagelin C-35 and C-36, since this series of devices there were some cryptographic errors. Decryption of the B-21 device required appropriate computing tools to perform large amounts of computation. Soon, German cryptographers managed to break into B-21, and in the USA they abandoned this model, eliminated the flaws and released the following model of Hagelin S-38 encryptors (known during the Second World War as M-209)
decrypting the B-21 device



In 1934, the French General Staff specified the task. Hagelin was asked to create a “pocket” encryption machine. The inventor was able to fulfill the assignment - to develop a compact mechanical printing encoder suitable for use in the field, and only one person was enough to work with it. The result was an encoder called the S-35, and then a modernized S-36, which weighed as much as a regular codebook. The S-36 received high marks from French specialists, and as a result, France ordered 5 thousand encoders at once, which was a turning point for the prosperity of Aktibolaget Cryptoteknik. Around the same time, Hagelin created miniature encoders for the French police. It was really pocket equipment. It was set in motion by the thumb of the left hand, with the right hand it was possible to record the ciphertext.
Electromechanical encryption machines:
The Riddle

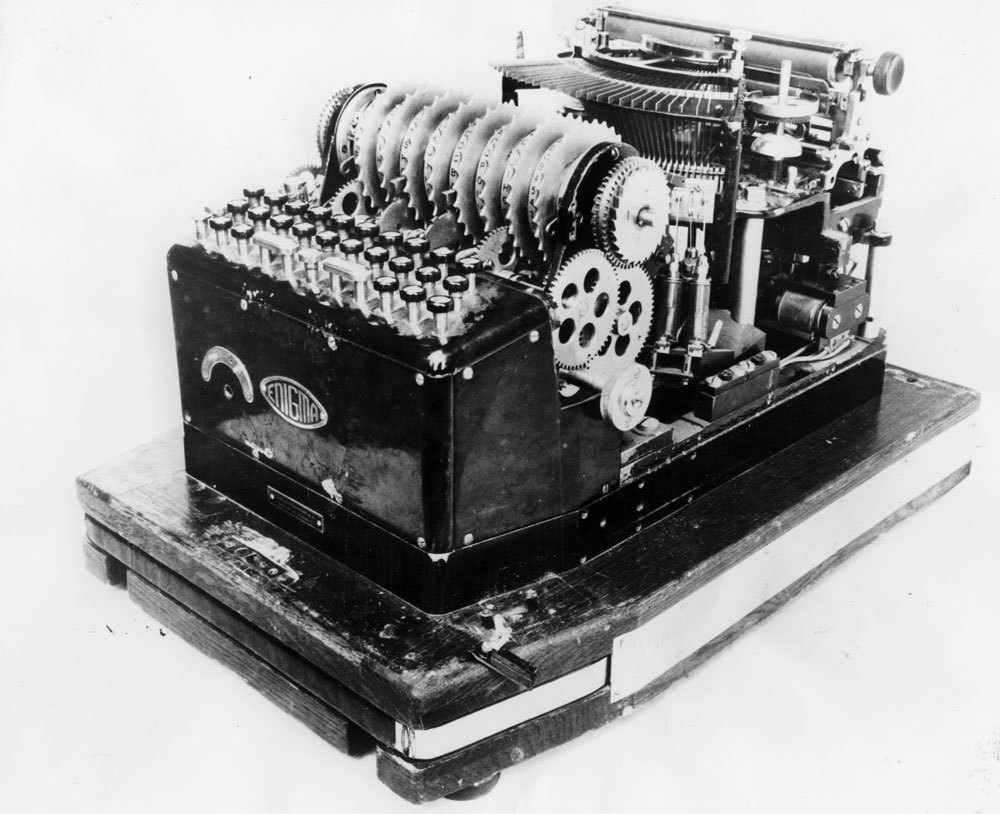
Electromechanical encryption machines first appeared after the First World War. In 1917, an American rotary cryptographic machine, later called the Enigma, was created by American Edward Hepburn. For work, she connected to an electric typewriter. A little later in 1923, the Berlin engineer Arthur Sherbius created an independent industrial version of Enigma. The German government, struck by the reliability of the machine, retained all rights to it for itself and began to use it for the army. Later, a special modification appeared, designed for the naval forces, it differed from the usual "Enigma" in the number of encryption rotors.

The Enigma disk encoder was distinguished by its simplicity of design, high reliability and excellent font resistance. The characteristics listed above brought this electromechanical encoder a well-deserved fame during the Second World War.
By design, Enigma is classified as a disk encoder, a feature of which is the presence of encryption disks rotating on the same axis. In the first Enigma samples, three cryptographic disks interlocked were used, which made regular movement during operation, similar to electricity meters of old structures.

During the war, ciphers were broken, new ones were invented, as a result of which work on improving Enigma did not stop even for a minute. The result of this work was an encryption device with six unconnected disks, the movement of which became chaotic.
“Enigma A”
As the Germans called it “Schreibende Enigma” (information on this model was found in one magazine about electrical engineering in 1923 in an article by Arthur Scherbius )
The very first model of the encryption machine of the brand “Enigma A” appeared in 1923. A very heavy and bulky machine that could output the code directly onto paper. As far as is known, there are currently no surviving examples of Enigma A.

Soon, this model was replaced by model “B”in 1924.

After several improvements, the Enigma B was replaced in 1929 by the Enigma H , known as the H-29, the latest model in the Enigma range of printing presses. But, alas, these models were unreliable, and, despite the improvements, in practice they received a lot of complaints.
As early as 1924, the Enigma C was created , which was much smaller in size and, therefore, differed in portability from the Enigma A typewriter. It was first used light bulbs.
It consisted of a 26-letter keyboard for entering open messages, 26 light bulbs that, when turned on, illuminated the necessary letters of the ciphertext, a power source (3.5-volt battery or its equivalent), three removable contact wheels that rotated on a common axis, fixed contact reflector, fixed input contact wheel.
The keyboard was identical to that used on English typewriters, with the exception of minor details. Only uppercase letters were used, numbers were absent, there were no letters with umlaut, such as U. The letters on the bulbs were arranged in the same order.
The car was placed in a wooden box. With the lid of the machine closed, only the adjusting rings of the three movable wheels protruded outward, you could see a letter on its alphabetical tire in the small window above each wheel. This was done so that the cryptographer could use the adjusting ring to rotate each wheel to the desired initial position. With the machine cover open, the encryptor could see all the wheels inside and, having pressed the lever located next to the reflector, remove all three moving wheels from the machine, remove them from the common axis and change the order of their location. Since the first Enigma, unlike later models, had only three wheels, there were only six relative wheel arrangements. The car was portable, but rather heavy, weighing about 12 kilograms.




Three removable contact wheels - R1, R2 and R3, a stationary reflector - U. When you click on one of the letters on the keyboard, the contact closes and the current from the battery passed through the wheels R1, R2 and R3. Passing through the reflector, the current "returned", and, after passing through the wheels R3, R2 and R1 again, lit a lamp that illuminated the letter of the ciphertext. The letter of the original plaintext, when converted into a letter of ciphertext, underwent 9 conversions.
But the first Enigma cipher in the kit that came with the machine had only three wheels, and they could be installed in six different ways. Therefore, the number of possible alphabets of simple replacement was 101,400.
In reality, in most military versions of Enigma there were 2 more conversions, and thus, there were 11 in all.
In 1926, Enigma D (officially A26) was developed as the successor to Enigma C. Three contact wheels were mounted on the moving spindle. The reflector U became customizable, which meant that it could be installed on any of 26 positions, which in turn increased the number of permutations and increased the reliability of this model.


Later, another model of the Enigma I electromechanical encryption machine saw the “light” . The German military insisted on making changes that significantly increased the durability of the machine. The most important of these was the introduction of the switch.
The Enigma army version of the encryption machine had a switch in front that fit under the keyboard. The switch had 26 connectors, which were paired with 13 short cables. This device made it possible at the input and output stages to swap the letters of the alphabet that make up the pairs. So, for example, if the letter A was connected by a cable to W, then every time you press the A key, the signal from the letter W leaves the cipher, and vice versa. Similarly, if the letter A of the ciphertext appeared at the output of the last wheel R1, then the W light came on, so the letter W was written in the ciphertext. The number of possible ways to split 26 letters of the switch into pairs is equal to the number of possible reflector options, i.e. exceeds 1012. And since the switch connections changed frequently (at first daily, and since 1944 three times a day),


From December 15, 1938 onwards, each Enigma was equipped with five contact wheels instead of three: three - in the car, two remote. Each day, the operator placed the three selected disks in the machine in a certain order, in accordance with the instructions of the codebook.
Two wheels were stored in a small wooden box. The image is a typical example of such a box for storing two disks.


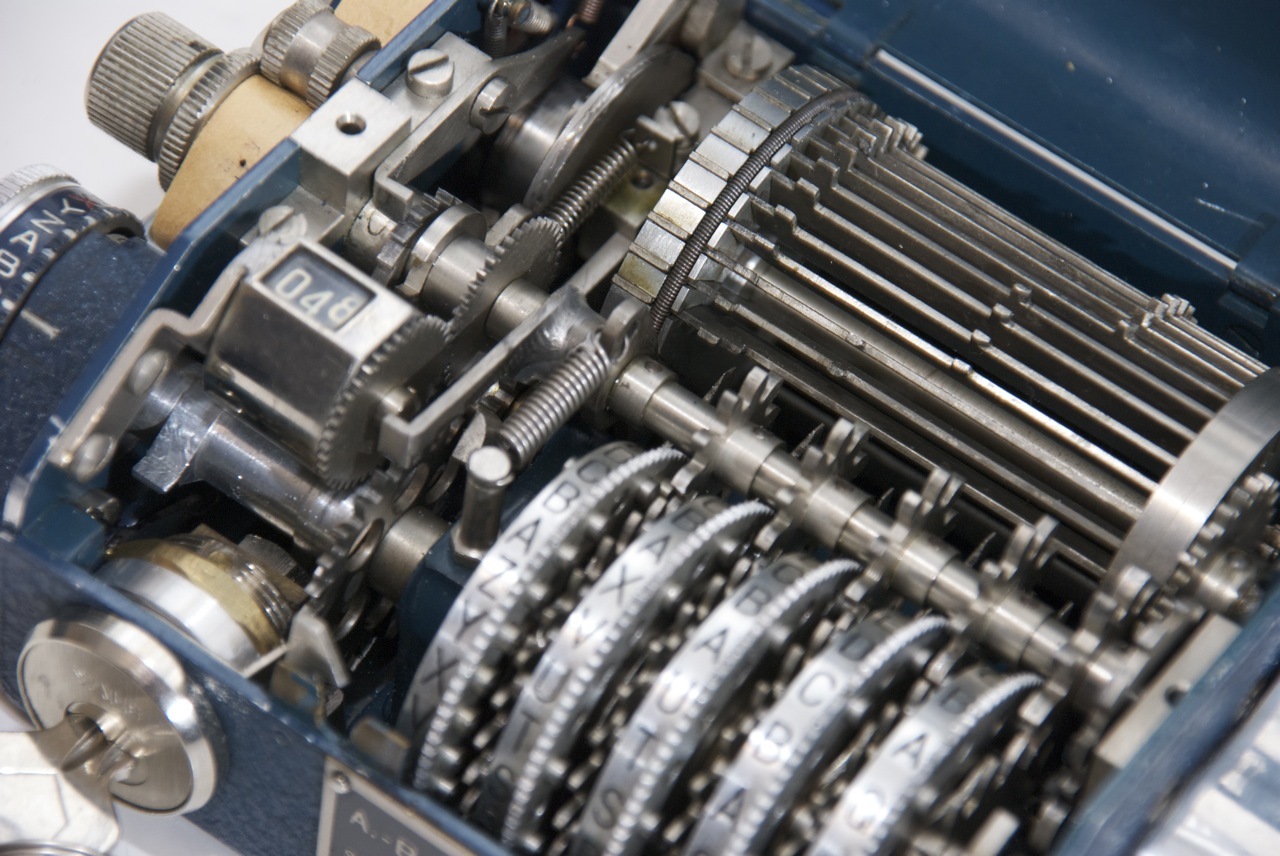
Enigma M3, M1, M2 for the German Navy, in 1939 three more contact wheels with a code were added to five. These models were used exclusively by the German Navy Kriegsmarine.
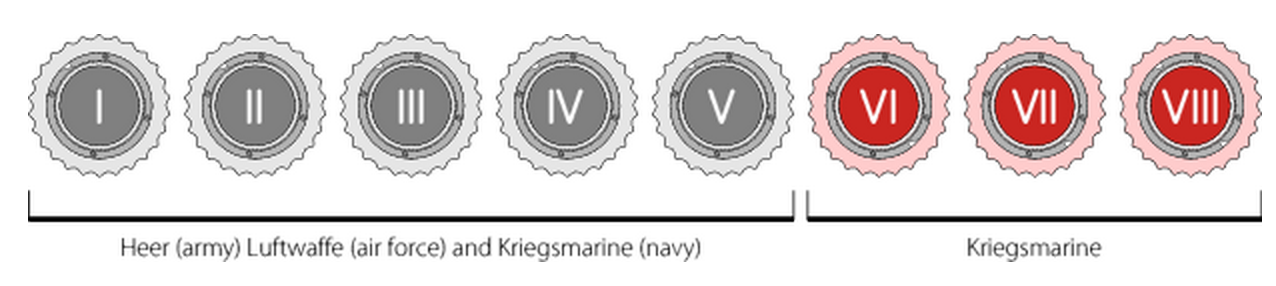
Marine Enigma M4was more complex to provide reliable secret communications with submarines. Hacking it was much more difficult (but it was still possible). 4 out of 8 possible rotors were used. Kriegsmarine also used thin reflectors B, C, an additional rotor was necessarily located near them. There was an instruction, following which the same wheel from the set (I-VIII) should not be used for two days in a row. The switchboard was designated 1-26.

Enigma G at first glance looked the same as Enigma D: the same dimensions, four coding wheels, shiny metal details. As in Enigma D, the rightmost three wheels are coding wheels, one reflector on the left. But unlike model D, the reflector moved during encryption. A counter was also installed to the left of the wheels (Zählwerk).
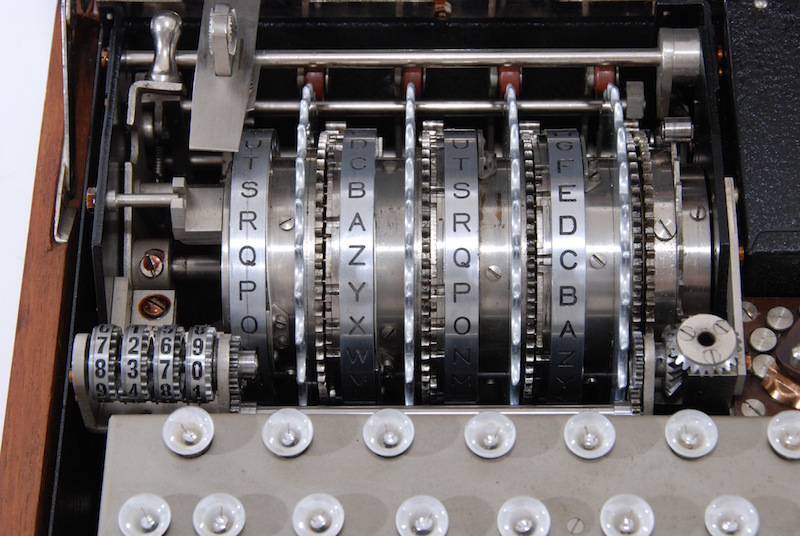

Enigma k
Enigma T (1942), code-named "Tirpitz" was used during the Second World War by the Germans to transmit ciphers to the Japanese Navy. Eight rotor wheels were also used, three of which were in the car. The difference was the presence of only 5 cutouts on the revolving discs.


Enigma KD (1944) was used more often on the railway. A special version of Enigma K, it used three wheels with 9 cutouts on the revolving discs, as well as a reflector, known as the Dora reflector.

The Enigma power supply unit , dimensions 20 x 11 x 13.5 cm, was required not for the movement of rotor wheels, but for powering the electric circuit of the lamps. Designed to power devices at 110, 125, 145, 220 and 250 volts. In front of the panel are two fuses, 125 milliamps and 80 milliamps, respectively.


Until the very end of the war, the German command was fully confident that it was impossible to crack the codes of the Enigma cryptographic machine. Nevertheless, the British, having acquired the first model of this machine from the Poles in 1939, by the middle of the war created an effective system for deciphering enemy messages codenamed Ultra, using, among other things, the world's first electronic computer, Colossus. And the British received the most important “gift” on May 8, 1941, when they captured the German U-110 submarine - they got into their hands not only a working machine, but also the entire set of documents for covert communications. Since that time, for German submariners, broadcasting for the purpose of transmitting data was often tantamount to a death sentence. Apparently, at the end of the war, Karl Dönitz guessed about this, as he once wrote the following lines in his diary:
The enemy holds a trump card, covers all areas with the help of long-range aviation and uses detection methods that we are not ready for. The enemy knows all our secrets, but we do not know anything about their secrets!
The main weakness that led to the decryption of Enigma was not in the design of the machine itself, but in the method that the Germans used to send messages. As mentioned above, if the encryptor sent a message encrypted using a system with variable parameters, then he should either inform the recipient of the values of these parameters, or provide him with the opportunity to calculate them himself. The latter method was rarely applied, although it could be applied in the case of the Jefferson cylinder. For the Enigma cipher, this method is completely unsuitable, and the recipient must provide the full information necessary to decrypt the message. What exactly does the recipient need to know? Let's say that the sender and the recipient work with the same “settings”, that is, they both use the same Enigma wheels and in the same order, the same switch connections. Even in this case, the sender must somehow inform the recipient of the initial positions of the three wheels before encrypting the message. This information must be placed in the "indicator". The initial positions (“corner settings”) must be chosen by the sender “randomly”, because if several messages are encrypted on the same initial corner settings, then one-key messages are received that can be read even if the type of wheels and / or their initial corner settings cannot be determined. Since there are 17576 variants of initial angular positions for a triple of wheels, the probability of accidentally encrypting two messages with the same initial settings will be less than 0.00006, provided that the initial settings are really chosen arbitrarily. However, in practice, cryptographers developed habits: for example, they selected three letters indicating the initial settings of the wheels from the same row of letters on the keyboard, which significantly increased the likelihood of single-key messages appearing. A common key could well have arisen by chance even with a random choice of corner installations, if the number of messages sent with the same internal machine settings (i.e., with the same wheel arrangement and the same switch) was large. For example, if 200 messages are sent, then the probability that among them there will be at least one pair of single-key messages will be more than half. Therefore, in order to reduce the likelihood of a common key appearing, it was necessary to change the machine’s internal settings as often as possible so that a large number of messages
You can download Enigma Simulator for free at the following address.
Lorenz
German encryption machine used during the Second World War to transmit information by teletype. You can read about it in my article Penetrating the thoughts of the enemy: the legendary Bletchley Park . And if Enigma was used mainly in the field, the Lorenz machine served for high-level communication - it transmitted the orders of the top German leadership.

An interesting link to the SZ40 simulator
The Nazis were actively working on the creation of new encryption machines. It took about four years for the first experimental batch of Schlüsselgerät 41 (SG-41) and its modification SG-41Z to appear in 1944. The machine was nicknamed Hitlersmuhle - "Hitler's Mill" because there was a handle on the right side of the machine, such as manual coffee mills. In the future, the mechanical handle, from which the name came from, was planned to be replaced by an engine - drawings were developed, but this project could not be realized due to the rapid advance of the Soviet Army.

German designers took something from the Enigma design: encryption and decryption were identical. The main difference between the "Hitler mill" and Enigma was the absence of electronic lamps: SG worked with two thin strips of paper. On one of them, printed letters were entered, on the other, information obtained as a result of encryption or decryption was displayed. The Germans copied most of the mechanisms from the M-209 encryption machine, which was created by Boris Hagelin.

At the end of the war, German experts also worked on other projects of encryption machines, but little is known about them today.
The Siemens T43 cryptographic machine , called by experts a ghost of cryptographic history because information about it is still classified.

T43 was one of the first machines that worked on the principle of a one-time pad. The random numbers needed for this operation were fed into the device in the form of a perforated strip that could not be used twice. T43 punched all processed strips and made them thus unsuitable for reuse.
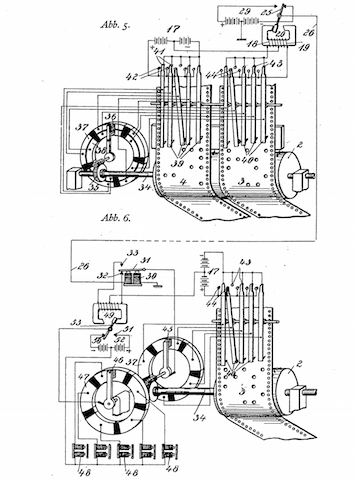
According to experts, about 30 to 50 of these machines were built and used by the Germans in the last months of the war in some combat units. Individual copies of the T43 after the war ended up in Norway, Spain and South America.
Around T43 there is still a lot of obscurity. After the war, six copies of these machines were destroyed in the United States. The machines used in Norway were sent to the British Decryption Center, in Bletchley Park. It is clear that the Allies strictly classified all information about this ultra-modern machine.
Hitler's Treasures
In the Austrian Lake Toplitz, several cryptographic machines rest at 100 meters depth. On the so-called Black Pearl Lake, the Nazis conducted experiments with explosives, tested homing T-5 torpedoes to destroy submarines, V-1, V-2.
This area is surrounded for many kilometers by impassable mountains and forests - you can get there only on foot. Exploring the lake is dangerous: the Austrian government by special order forbade diving into the water. Nevertheless, divers make dives into the black lake and they see, as a rule, a thick layer of trees - the Nazis deliberately threw thousands of cubic meters of wood into the lake, made a double bottom from the nets. But this does not deter historians and treasure hunters - they seek and find in the lake a lot of interesting things. One recent finding is the Hitler Mill cryptographic machine.
The lake is slowly revealing its secrets - the military archives of foreign intelligence are not in a hurry to do this. Whatever the result of the next new expedition, one thing is clear: the stream of adventurers on the shores of Toplitz See is not getting smaller. Perhaps because the inventions made in the field of cryptography by German experts today are of great scientific and political interest.
