Turing's Bomb Emulator on Raspberry Pi and Arduino
 " Enigma " - a series of German electro-mechanical rotor cipher machines, which have been used since the twenties of the last century. Including the time of active transmission of messages encrypted on Enigma falls during the Second World War. In this regard, enormous practical value of the Enigma encryption hack has appeared.
" Enigma " - a series of German electro-mechanical rotor cipher machines, which have been used since the twenties of the last century. Including the time of active transmission of messages encrypted on Enigma falls during the Second World War. In this regard, enormous practical value of the Enigma encryption hack has appeared. In order to crack Enigma codes, the Polish Ciphering Bureau developed a Cryptological bomb with the help of which messages were cracked. In total, six machines were created for six combinations of rotors, which had a limited scope due to the specificity of the conditions for an encrypted message. Machines quickly lost their meaning with the introduction of new rotors, and the Polish side had no resources to create another 54 “bombs”. After that I had to return to manual methods -sheets of Zygalsky . Based on Polish developments, a more advanced Bombe , an electromechanical machine, which is most often associated with the personality of Alan Turing, was created. In total, about one and a half hundred British "Bombs" were built. After the end of World War II, almost all the Bombs were destroyed for reasons of secrecy.
Although there is documentation on the device in free circulation, successful attempts to recreate the Bomb can be counted on the fingers of one hand. This, for example, is a workable reconstruction of the Bombe Rebuild Project of an amateur team led by John Harper. The replica took 13 years to create. Yesterday, the network published its much more modest projectamateur from New Zealand. This is an emulator of three rotors. In the real "Bomb" there were 26 interconnected triples.
Enigma used a polyalphabetic cipher , the most famous example of which is the Viginer cipher. We can briefly describe the principle of operation of the cipher as Caesar's dynamic cipher, in which the depth of the shift changes according to a certain algorithm. The hearts of the Enigma are three rotors, although later four copies were created. On each of the rotors on both sides there are 26 contacts corresponding to the letters of the alphabet. The electrical connections of the tracks between the contacts do not go in a straight line, they differ from rotor to rotor. The rotors can be removed, changed their location or insert other rotors from the set. Since January 1939, in the ground forces and aviation, the set consisted of 5 rotors, which gave 60 combinations, and in the fleet - 8 (336 combinations).
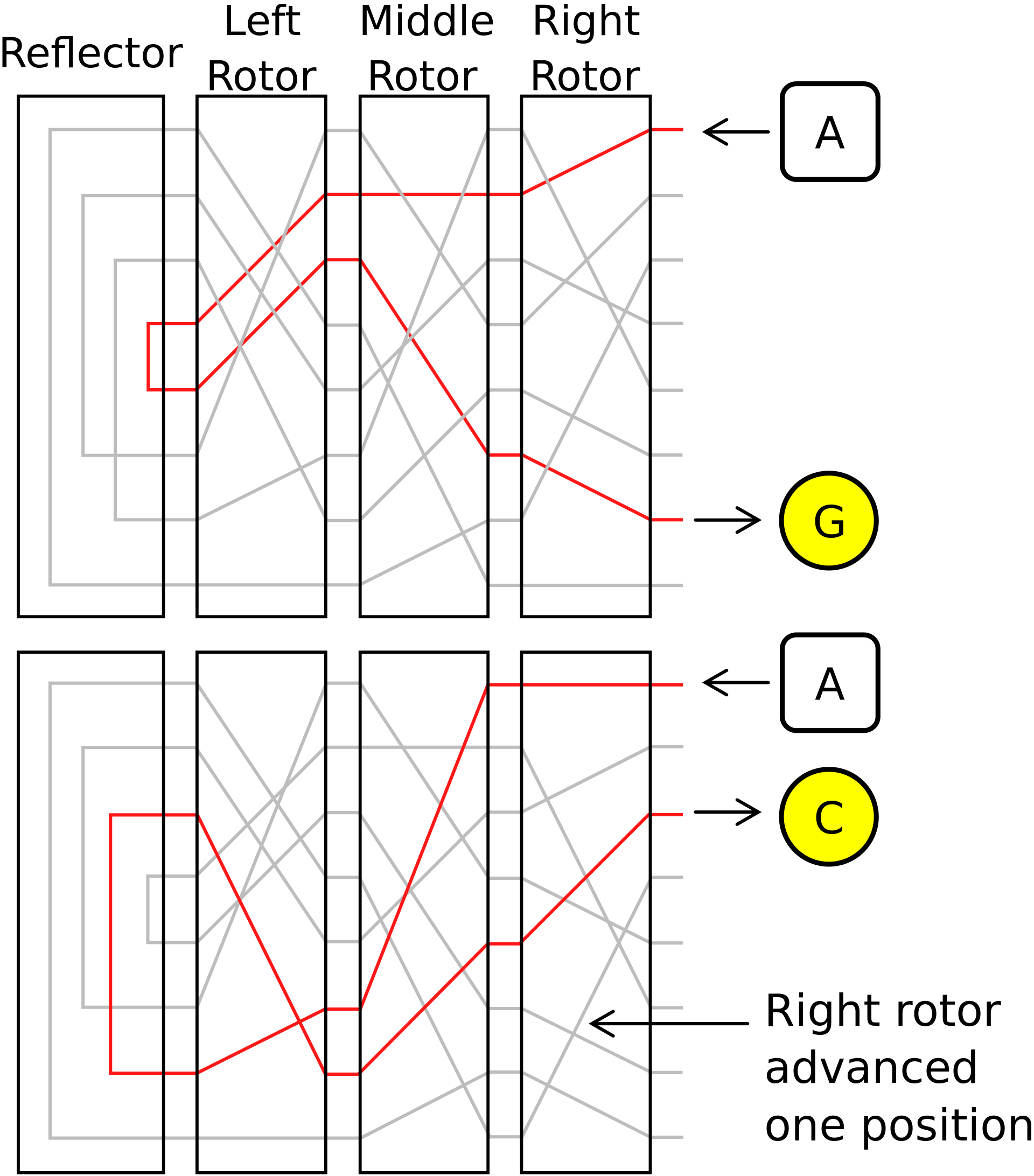
An additional measure is the use of a patch panel. Electrical connections with wires on the front panel of the machine allow you to change the letters in pairs: A can become R, and R in this case will become A. To read the message, you need to know the position of the rotors on the spindle, which rotors and reflector from the set were used, the encryption code (3 Latin characters alphabet) and the position of the wires on the patch panel. In some versions, other measures were introduced: the reflector also rotated, a larger number of rotors were used, and so on.

After pressing the key, the current passed through the electric paths from the key, through the contacts on the patch panel, through three rotors with different positions of the tracks, returned through the reflector and again through three rotors. Then a light came on on the panel with the corresponding letter of the cipher. At least one rotor made a movement, changing the combination to encrypt the next letter. The rotors rotated like a second, minute and clockwise in a mechanical watch: the fast right rotor made a full revolution, and then the 1/26 revolution made the average one. After a full turn of the middle, the 1/26 turn made the slowest left.
The Bomb helped establish the possible Enigm settings in the German forces. She did not give ready-made messages. All the same manual labor was required to complete the work. "Bombs" helped reduce the number of possible solutions to an acceptable and affordable for processing.
To decrypt messages, so-called “hints” were required. A well-known plaintext attack was carried out: the encrypted text was checked for the possibility of containing familiar words and phrases. Finding “clues” required knowledge of German military slang and the communication style of telecom operators. A significant role was played by the design of the reflector: the letter could never be encrypted into itself. After choosing a hint, a so-called “menu” was compiled, a program for finding possible solutions. The “menu” run was interrupted by stops with candidate solutions, which were then checked. Usually, there were many stops with the wrong decisions before finding the right one.
An amateur from New Zealand recreated the Bomb. It would be more accurate to say that he recreated the emulator of one of the 26 blocks of the decryption machine. The created device is compact - it can be put on the table. The calculations are performed on the Raspberry Pi 2. The device does not even hide this: the result is displayed until the end of the movement of the rotors. Three drums of the same color (in the original they had special colors for the task to be performed) rotate purely for a cosmetic effect. But they do it very convincingly and at the same speed as the original. The process is nice to watch.
The video starts the very “menu” with a report on the weather, which was used to demonstrate the real “Bomb”. It is easy to understand why: it is clear.
The project was assisted by team leader for creating a full replica John Harper and several other experts. Prior to this, the amateur created a bomb watch - a fully functional version of the Enigma hacking machine, which can be worn on the wrist.

Inside the desktop "Bombs" is a board Raspeberry Pi 2, Arduino, lead-acid battery for 12 volts and a voltmeter. The emulator consumes a lot of energy and easily draws 1.5-2 amperes each. Initially, the software for work was written in Basic, but later it was ported to C ++. The Raspberry Pi 2 connects to the Arduino and controls three stepper motors. Arduino tells Raspeberry Pi 2 the position of the motors as a series of pulses so that they can be stopped at the right time. On the side is a liquid crystal display, which plays the role of a mechanical indicator of the original "Bomb". The start and interrupt buttons are located at the front like a real sample.

The case is made of steel with a thickness of 0.8 mm, and the drums in 3/4 scale - from ordinary cans. All parts of the device are made by hand. The mass is about 10 kilograms. Files from the “menu” are loaded from a flash drive, which can be inserted by opening the lid on the back. Also on the side is a network port for monitoring the emulator, it is closed by a lid. In operation, the device is noisy with engines, even if the volume cannot be compared with the noise of a real “Bomb” .
The author promises to publish the source code of the device program, although without the hardware that exists in a single copy, there is nothing to run it on. It remains to wish the author not to bring his creation to school , much less to explain at the time of arrest what it is.
Project page with photos
Turing's Online Bomb Simulator
