Vulnerability Mikrotik allows you to get a list of all users through winbox
- From the sandbox
- Tutorial
Mikrotik devices have become widespread due to their price relative to functionality. But no one canceled the errors in the software. And this time a serious bug got out.
On March 25, one of the users of the Mikrotik forum announced the discovery of suspicious activity of mikrotik routers using telnet (TCP port 23), TR-069 (TCP port 7547) and WINBOX (TCP 8291) ports.
Employees of the company referred to a bug that was closed a year ago. Later it turned out that this was a new vulnerability, and on April 23, Mikrotik announced the release of firmware, where this vulnerability was fixed.
Despite the fact that the company quite quickly released bugfix, there are thousands of devices exposed to vulnerabilities in the network.

I recommend that all RouterOS users upgrade to at least version 6.40.8 [bugfix] or 6.42.1 [current]
Also in the public domain there are tools that allow ordinary users to access devices that are not protected by a firewall or are not updated to the current version.
In view of recent events, I suggest that all users of Mikrotik and CHR devices make at least a minimum setup.
Minimum Security Settings
Analyzing devices with a bug, I noticed that almost everyone neglects the firewall settings, despite the fact that this is the most effective tool for protecting your network infrastructure. And 90% of devices have an admin account with full rights. Just a dream for broodforsers.
Regarding RouterOS security, take a few simple steps to ensure minimal security:
Make sure you have the latest firmware.
Do not rely on the absence of bugs in the new firmware and configure the firewall:
2.1. In the INPUT chain, access to the device is allowed only from trusted ip addresses. For example, the range of the home network or ip addresses of network administrators.
Please note that the INPUT chain applies only to packets addressed directly to this router. Transit packets belong to the FORWARD chain.
2.2. Drop all packages that do not match the allowed.
2.3. In case you need periodically access from dynamic addresses, then use "port knocking" to add your ip at a fixed time.Turn off all services that you do not use (api, ssh, telnet etc.)
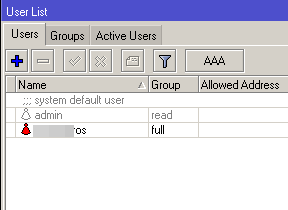
- After setting up the firewall and updating the firmware, change the password.
If you use the account name "admin", also create your account, for example, "Vasya". Go under it, check access rights and block the "admin".
Firewall
Using a terminal.
Create a list of addresses that will be allowed to connect to the router/ip firewall address-listadd address=192.168.1.0/24 list=allow-ipadd address=192.168.88.10/32 list=allow-ip
Add a rule that allows all actions from these addresses
/ip firewall filteradd action=accept chain=input comment="Allow Address List" src-address-list=allow-ip
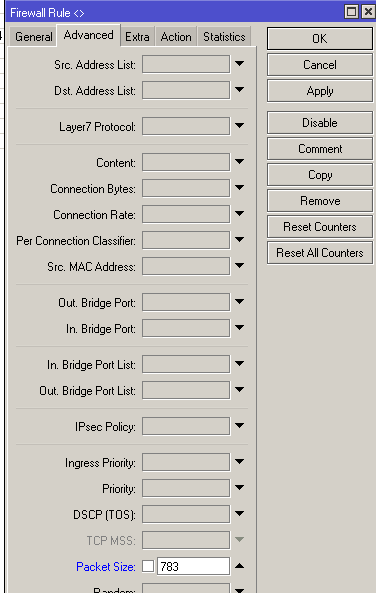
If you need access from unknown addresses, I wait for an icmp packet (ping) of a certain size. If such a packet arrives, then the source address is added to the allow-ip list with a time of 1 hour. If desired, you can make a cascade of such packages.
/ip firewall filteradd action=add-src-to-address-list address-list=allow-ip address-list-timeout=1h chain=input packet-size=783 protocol=icmp
Pay attention to the packet size packet-size 783 bytes. But when pinging, you must point to 28 bytes less. In this case, ping from windows:
ping -l 755 myhostname.domain
Deny access to all ports that are not allowed above:
/ip firewall filter add action=drop chain=input
Services,
which you do not use must also be turned off because these are extra points of failure. /ip serviceset api disabled=yesset api-ssl disabled=yes
etc.
The same with winbox.
Allowed in our address sheet.
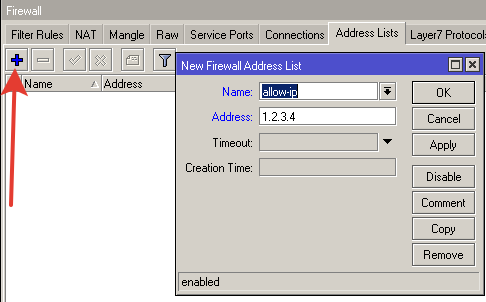
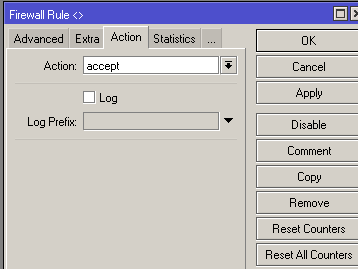
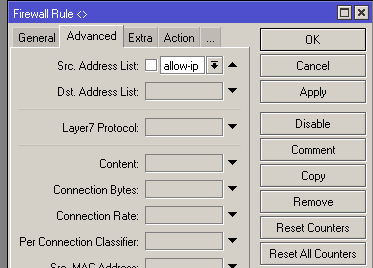
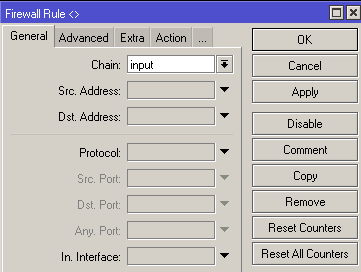
Typically added to the address list for ping
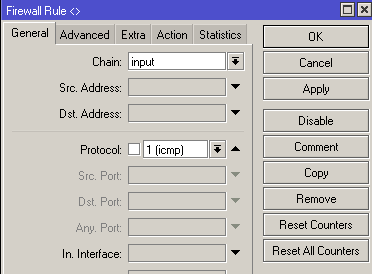
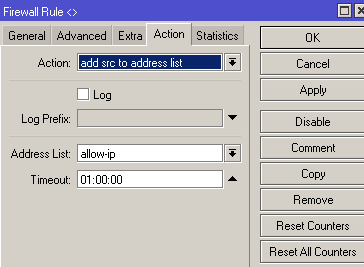
rule banning anything and everything is put the latest
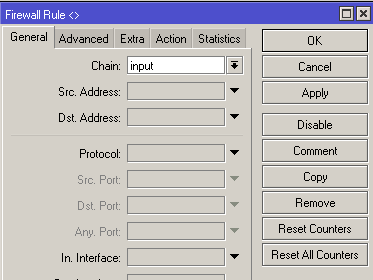
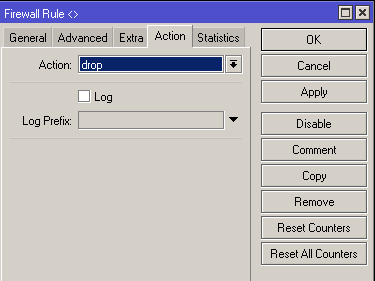
That is, it should look like this
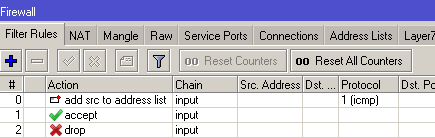
service is configured here for
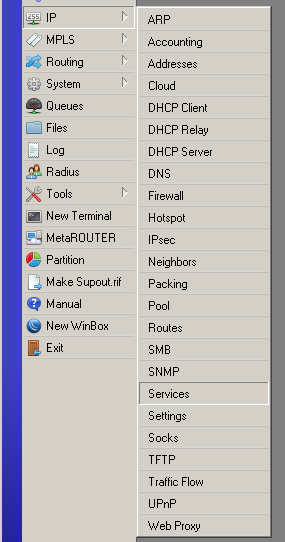
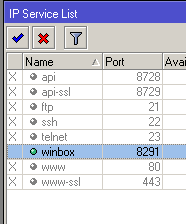
the user to add and remove "admin", and to change your password here

Conclusion
I really hope that my brief instruction will help your device not get under the control of any botnet network, including Hajim.
