A couple of words about FastPath and FastTrack in MikroTik
It is not a secret for anyone that MikroTik produces Software-Baser routers and CPU takes over most of the traffic processing. This approach has an advantage, since You can program almost any functionality and maintain a relatively unified system for all devices. But in speed they will always lag behind routers with specialized chips.
Software processing packages has several disadvantages:
- The lack of wire speed - the processor (especially single-core) can not work faster than specialized chips.
- Locks With really large amounts of traffic (for example, DoS / DDoS) you may not be able to connect to the router even through the console interface, since all processor time will be occupied by traffic processing.
- The difficulty of scaling. You cannot add a module that increases packet processing speed by hardware.
Developers go to various hardware and software solutions to improve the situation:
- Switch-chip on inexpensive models, allows processing Layer2 traffic bypassing the CPU.
- SoC with a good network chip (CCR line).
- Using hardware encryption
- Various technologies reduce the number of software processing packages (FastPath and FastTrack), and they will be discussed.
SlowPath vs FastPath
SlowPath is the basic traffic path through the internal MikroTik subsystems, it can be quite diverse and, the longer the path, the higher the CPU load and the more the speed drops.
FastPath - algorithms for transmitting traffic bypassing rather large processing blocks.
Operating conditions and support on devices
Most modern routers and motherboards from MikroTik support FastPath, but the wiki has a detailed list:
| Model | Ethernet support |
|---|---|
| RB6xx series | ether1,2 |
| Most of the RB7xx series | all ethernet ports |
| RB800 | ether1,2 |
| RB9xx series | all ethernet ports |
| RB1000 | all ethernet ports |
| RB1100 series | ether1-11 |
| RB2011 series | all ethernet ports |
| RB3011 series | all ethernet ports |
| CRS series routers | all ethernet ports |
| CCR series routers | all ethernet ports |
| Other devices | Not supported |
And a separate list for interfaces other than ethernet:
| Interface | Fastpath support | Note |
|---|---|---|
| Wireless | Yes | |
| Bridge | Yes | Starting at 6.29 |
| VLAN, VRRP | Yes | Starting at 6.30 |
| Bonding | Yes | Only RX traffic from 6.30 |
| EoIP, GRE, IPIP | Yes | Starting at 6.33. When this option is enabled, not all tunnel traffic will go via FastPath |
| L2TP, PPPoE | Yes | Starting at 6.35 |
| MPLS | Yes | Currently MPLS fast-path applies only to MPLS switched traffic. MPLS ingress and egress will operate as before. |
| Other | Not |
For the full-fledged operation of FastPath, support is needed from both the incoming and the outgoing interfaces. Interfaces should only include hardware queues.
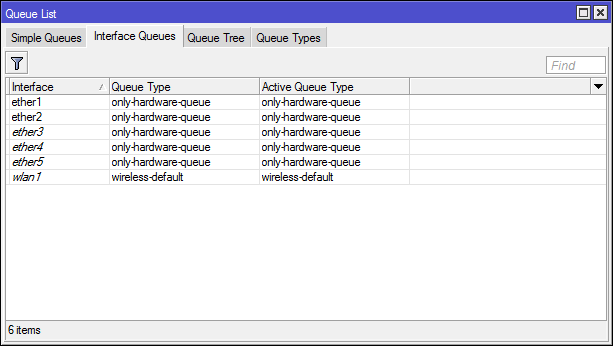
Last but not least, FastPath doesn’t like fragmented traffic. If a packet is framed, it will definitely get stuck on the CPU.
FastPath and Bridge
Bridge is a software interface used to create a Layer2 connection between multiple hardware (or software) interfaces. If you integrate 4 ethernet interfaces on the bridge (and enable hw=yes) and one wireless on the router , the traffic between the ethernet interfaces will go past the software interface, and the traffic between ethernet and wireless will use the software bridge. On routers with several chips (for example, RB2011), the traffic between interfaces from different chips will use the capabilities of the software bridge (sometimes, to reduce the load, interfaces simply join the patch cord and, in general, it works).
FatsPath - refers only to traffic coming through the CPU (software bridge), usually this is traffic between interfaces from different chips, or the option is disabled hw=yes.
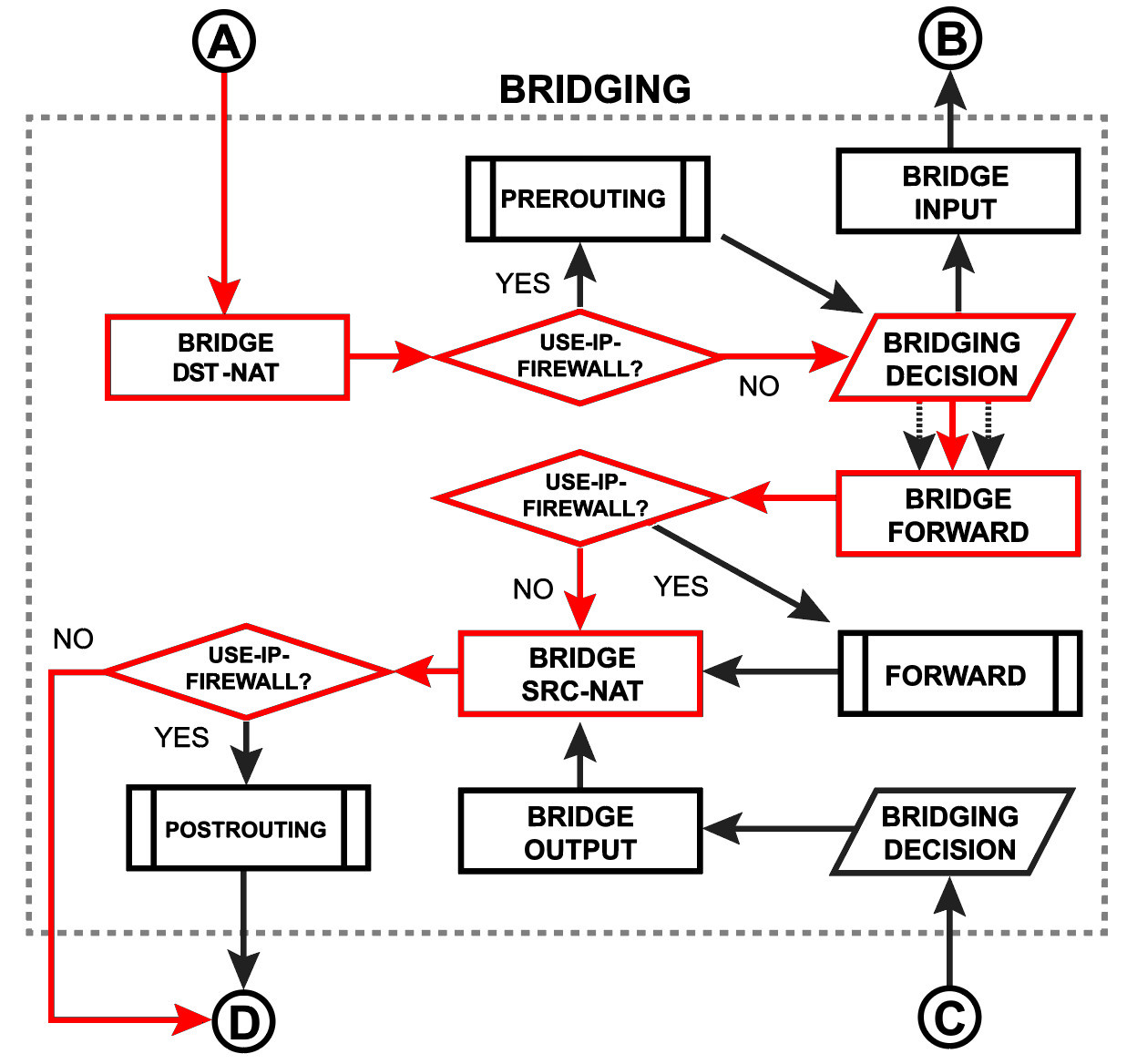
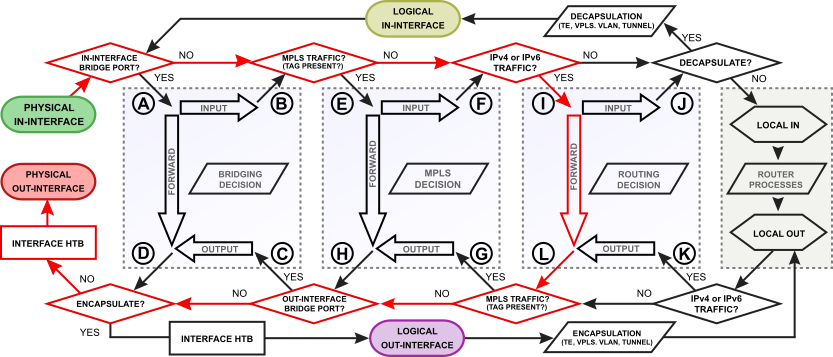
On Packet Flow, the traffic passing through Bridge looks like this:

And more:
It is included in the bridge settings (the setting is the same for all bridge interfaces) [Bridge] -> [Settings] -> [Allow FastPath], there you can also see the counters.
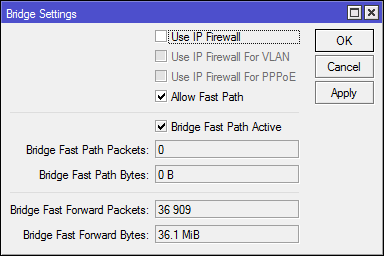
For FastPath to work in Bridge, the following conditions must be met:
- There is no vlan configuration on the bridge interfaces (I think this is not relevant for the CRS series, where the vlan are configured at the hardware level, but I could be wrong)
- There are no rules in
/interface bridge filterand/interface bridge nat, these are the same blocks from the second scheme that the frame goes through. - Ip firewall (
use-ip-firwall=no) is not enabled . A good feature for capturing traffic and debugging the network, but on an ongoing basis is rarely included. - Do not use mesh and metarouter
- The interface is not running: sniffer, torch and traffic generator.
FastPath and Tunnel
If in two words: a tunnel interface is the encapsulation of some packets into the load part of other packets. If you go along PacketFlow, then the red lines mark the original packet, the blue ones - the original packet encapsulated in the tunnel protocol packet (for example, ipip or gre; eoip gets (and comes from) in bridging decision; with tunnel ipsec is still more interesting, but not related to fastpath).
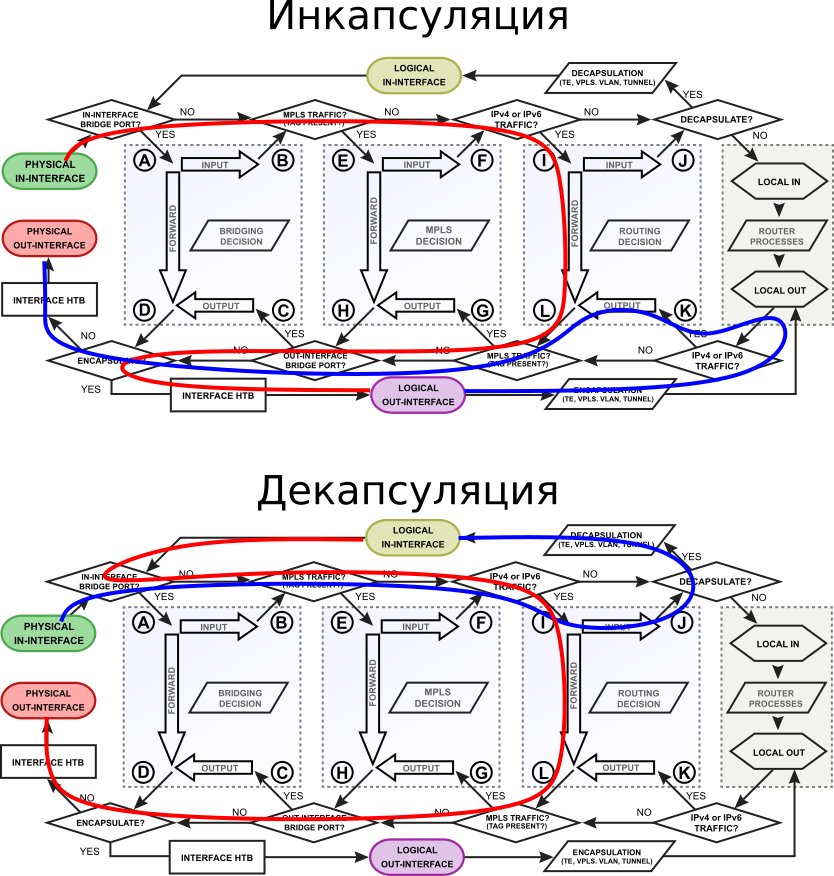
FastPath tunnel traffic will not be visible in: firewall, queues, hotspot, vrf, ip accounting. But some packets will continue to be transmitted over SlowPath, this must be taken into account when configuring the Firewall.
For FastPath to work in tunnel interfaces, the following conditions must be met:
- Do not use ipsec encryption
- Avoid packet fragmentation (properly configure mtu)
- Enable
allow-fast-path=yeson tunnel interface
FastPath and Layer3
Layer3 is the transfer of packets between subnets, the router builds routing tables and proceeds from them forwards the packet to the next hop.
On Packet Flow, the transit traffic on the network layer looks like this:
go deep
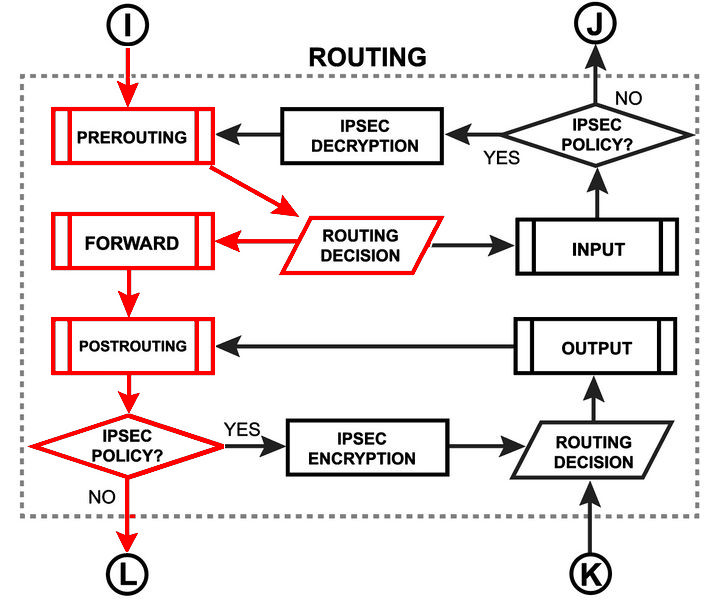
and even deeper
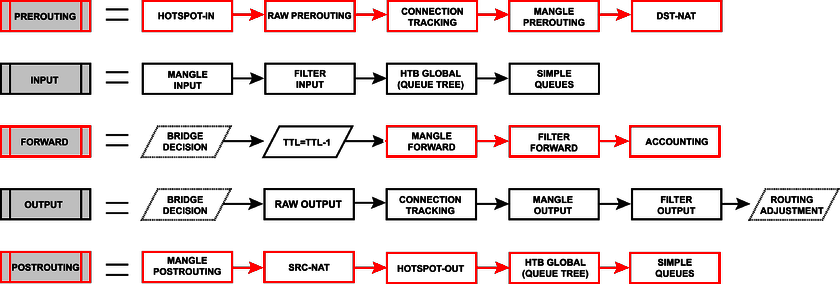
For FastPath to work on Layer3, the following conditions must be met:
- Do not add rules to the firewall (at all, even nat).
- Do not add entries to Address Lists.
- Do not configure Simple Queues and Queues Tree for
parent=global, or interfaces on which you plan to get a working FastPath. - Do not use mesh and metarouter.
- Disable Connection tracker. The auto option was introduced specifically for the operation of FastPath in the absence of rules in the firewall.
- Do not use
/ip accounting. - Do not use
/ip route vrf. - Do not configure
/ip hotspot. - Do not add ipsec policies.
- Route Cache must be enabled.
- Do not use active:
/tool mac-scanand/tool ip-scan. - Launched sniffer, torch and traffic generator interfere with the operation of FastPath.
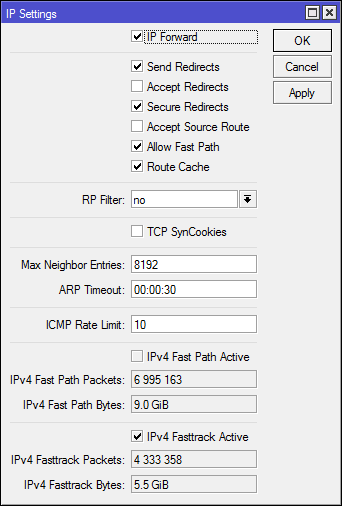
It is enabled in the ip settings: [IP] -> [Settings], there you can also see the counters of successfully processed packets.

Screenshot from home router. I have a fairly heavy firewall, several constantly enabled L2TP / IPSec connections and queues. About FastPath you can not even dream.
Fasttrack
Technology marking ip packages for quick passage through Packet Flow.
For FastTrack to work, you must comply with the following conditions:
- Route Cache and FastPath must be enabled and active.
- Correct configuration of traffic marking.
- Works only for UDP and TCP traffic.
- Do not use mesh and metarouter.
- Do not use active:
/tool mac-scanand/tool ip-scan. - Launched sniffer, torch and traffic generator interfere with the operation of FastTrack.
Traffic marked as fasttrack will not be processed in:
- Firewall filter (although this is debatable, in the example I will show why);
- Firewall mangle;
- IPSec;
- Queues with parrent = global;
- Hotspot;
- VRF.
If something interferes with the fasttrack packet, it will be transmitted like all the remaining packets along a slow path.
Enabled by adding a rule (see below) to the Firewall. FastTrack only marks packets from the established connection (you can also mark new, but then there will be problems with NAT). The filter table is used because When marking fasttrack in prerouting, again there will be problems with NAT.
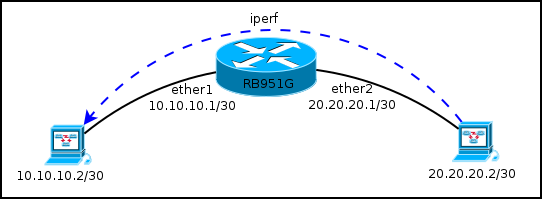
Synthetic test
| Fastpath | Connection tracker | NAT | Fasttrack | Speed | CPU |
|---|---|---|---|---|---|
| - | - | - | - | ~ 932Mb / sec | 100% (networking, ethernet) |
| + | - | - | - | ~ 923Mb / sec | 65-75% (networking, ethernet, unclassified) |
| + | + | - | - | ~ 680Mb / sec | 100% (networking, firewall, ethernet) |
| + | + | + | - | ~ 393Mb / sec | 100% (networking, firewall, ethernet) |
| + | + | + | + | ~ 911Mb / sec | 60-80% (networking, ethernet, unclassified) |
And (for the last test) what was configured and how it worked:
The filtering rules continued to process traffic (if you disable allowing for established, related traffic went to drop), postrouting + mangle was trapped for packets that did not fall into FastTrack.
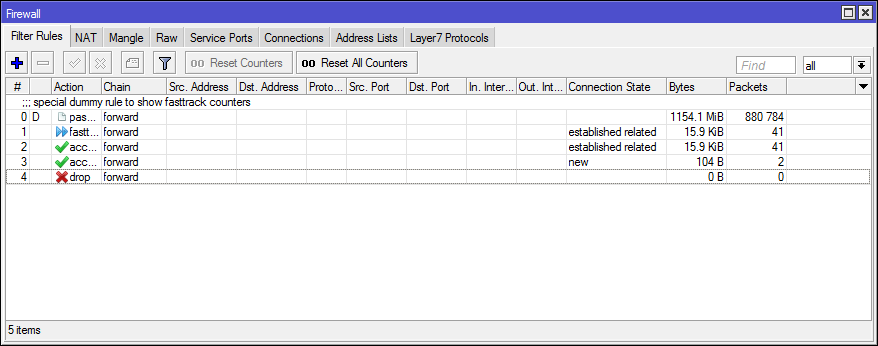
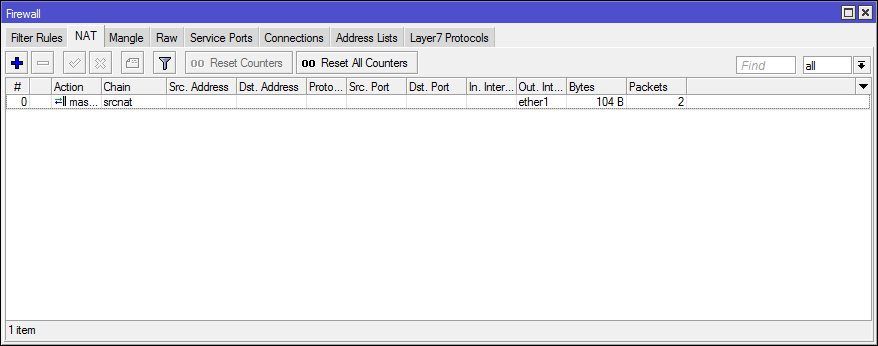
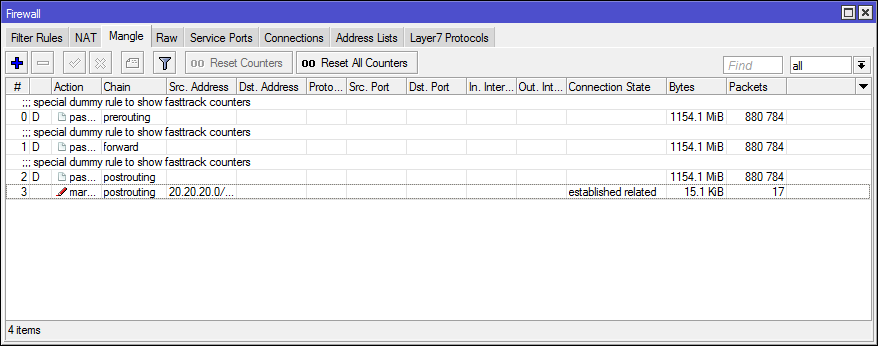
In Connection Tracker you can track FastTrack connections by the flag of the same name.
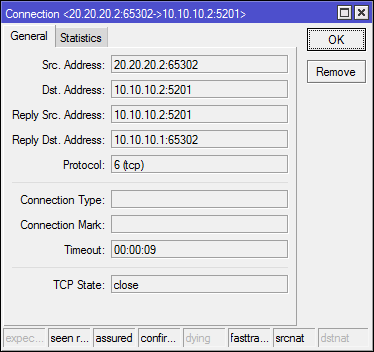
In the [IP] -> [Settings] counters, you can see that FastTrack is active and working, but FastPath is not.
/ip firewall filter
add action=fasttrack-connection chain=forward connection-state=established,related
add action=accept chain=forward connection-state=established,related
add action=accept chain=forward connection-state=new
add action=drop chain=forward
/ip firewall mangle
add action=mark-packet chain=postrouting connection-state=established,related new-packet-mark=q1 passthrough=no src-address=20.20.20.0/24
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether1Instead of conclusion
Use or not?
- FastPath for Bridge - Definitely yes. At least reduces the load on the CPU.
- FastPath for Tunnels - No. It works dull, turns off if you have encryption.
- FastPath for Layer3 - Arguably, most of the router's capabilities are lost. In a large, closed from the wild Internet, the network may have its (small) win.
- FastPath for MPLS / VLAN / Bonding / VRRP - Turns on automatically if there is a possibility. There is no separate option for management.
- FastTrack - For home and SOHO configurations without queues and a paranoid firewall will do. Synthetic tests with one client look good, in practice, it is necessary to closely monitor the traffic that leaked past FastTrack and look for the cause.
Links in addition
https://wiki.mikrotik.com/wiki/Manual:Fast_Path
https://wiki.mikrotik.com/wiki/Manual:IP/Fasttrack
http://mum.mikrotik.com/presentations/UA15/presentation_3077_1449654925.pdf
