Using Multi-Factor Authentication in Citrix Based on Aladdin RD Solutions - Webinar
In one of our past articles, we showed how to implement two-factor authentication in a simple (local) scenario through StoreFront.
It looked like that.
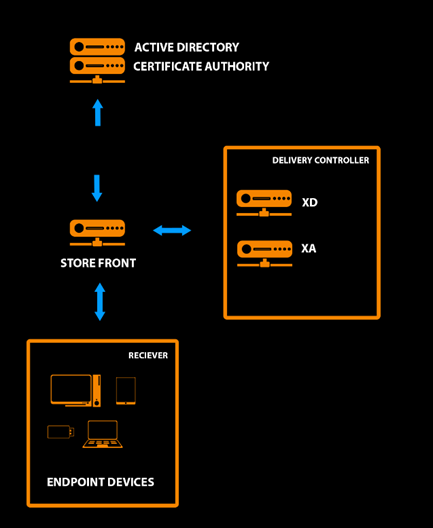
A user with an electronic key JaCarta makes a connection, the system requests a smart card and a public key on it, the user enters a PIN code. The card is unlocked, for user verification, the service asks to sign the ChallengeResponse certificate, which is stored on the card. After checking the credentials, the user gets access or denial of service.
Recently, my colleagues from Citrix and the Zvezdy i S training center conducted a joint webinar on multifactor authentication in Citrix virtual infrastructure based on PKI infrastructure and Aladdin R.D. solutions. This was the third Citrix Security Webinar. During this series, colleagues not only talk about ways to improve security, but also show technical settings in live mode. First of all, this series of webinars is interesting for administrators, engineers, and technical specialists.
This time we were invited to participate as an expert company in the field of multi-factor authentication, with extensive experience, including working with Citrix products.
The webinar showed how to set up two-factor in not the simplest scenarios on NetScaler. NetScaler and an external network with external devices were added to the scheme, in a fairly general form, the scheme looks like this:
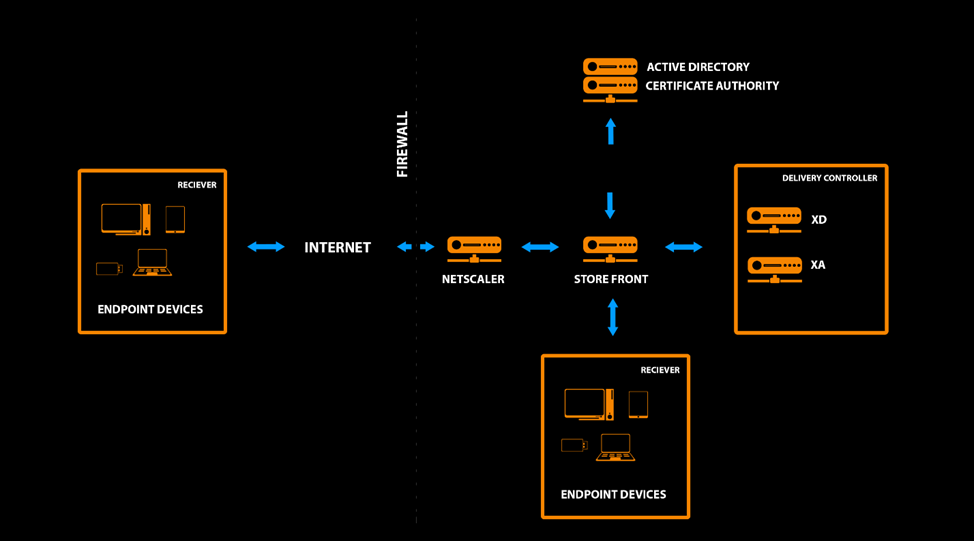
The principle of interacting with a smart card for authentication is similar to the previous one. After presenting JaCarta PKI (the first factor) and unlocking it by entering the PIN code (second factor), the credentials are checked, after which the user gets access or denial of service.
During the webinar, for our part, we tried to reflect the trend of digitalization of jobs, the development of the BYOD format and the use of various “untrusted” networks, from the aspect of the importance of protecting virtual infrastructure from unauthorized access and other attacks, the importance of using several authentication factors. They also talked about the advantages of using PKI electronic keys. And in general, topics were revealed for what it is needed, how to start using multi-factor authentication in Citrix, and how it works.
They touched upon an interesting topic of authentication based on one-time passwords; perhaps, a separate webinar will be held on the topic of OTP. If you are interested in this topic, or have other interesting questions, you can write to us about it.
Recording a webinar with our participation is onYoutube channel Citrix_ru .
The topic of the next technical webinar in the series of security enhancements will be authentication in Citrix according to GOST algorithms using the Gatekeeper solution from Sovintegra. This solution works with JaCarta GOST as a secure private key carrier and GOST certificate. This webinar will be held tomorrow, if you hurry, you can find an open link to register on facebook citrix_ru.
The channel also has past interesting technical webinars of this series:
I will add that in a similar way, through ADFS, a bunch of local AD is implemented with cloud Citrix, including with certificate authentication. As shown in the diagram below.
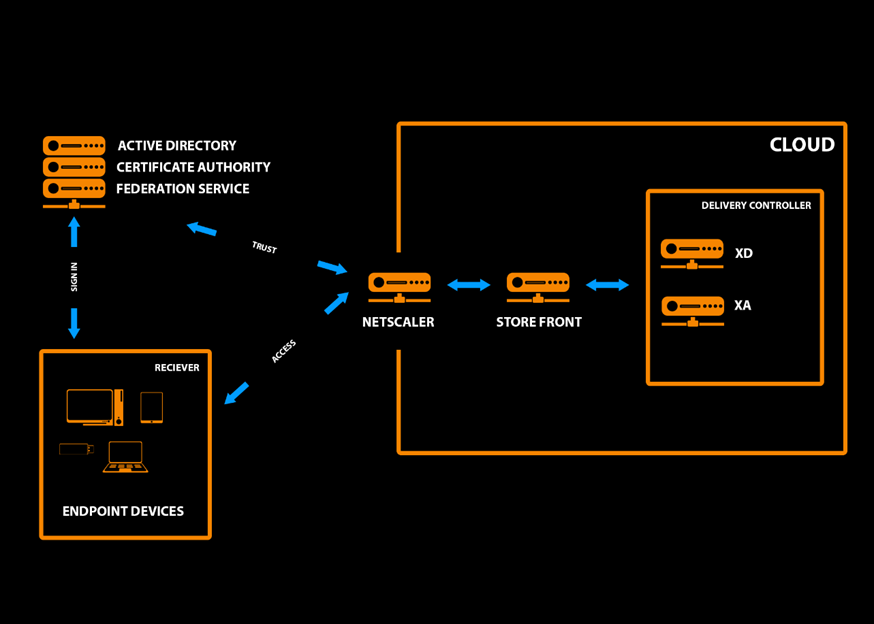
It works like this.
There are a number of external devices and JaCarta dongle users who are trying to access the resource pool through NetScaler. Next, the system redirects the user request to the proxy server for authentication. After successful authentication, the user is redirected to the EC for two-factor authentication. Using the JaCarta PKI key, with the certificate located on it, the user enters a PIN code. The system returns authentication data to ADFS, which in turn returns data to NetScaler. Next, the user gets access to the resource pool, or a denial of service message.
It looked like that.

A user with an electronic key JaCarta makes a connection, the system requests a smart card and a public key on it, the user enters a PIN code. The card is unlocked, for user verification, the service asks to sign the ChallengeResponse certificate, which is stored on the card. After checking the credentials, the user gets access or denial of service.
Recently, my colleagues from Citrix and the Zvezdy i S training center conducted a joint webinar on multifactor authentication in Citrix virtual infrastructure based on PKI infrastructure and Aladdin R.D. solutions. This was the third Citrix Security Webinar. During this series, colleagues not only talk about ways to improve security, but also show technical settings in live mode. First of all, this series of webinars is interesting for administrators, engineers, and technical specialists.
This time we were invited to participate as an expert company in the field of multi-factor authentication, with extensive experience, including working with Citrix products.
The webinar showed how to set up two-factor in not the simplest scenarios on NetScaler. NetScaler and an external network with external devices were added to the scheme, in a fairly general form, the scheme looks like this:

The principle of interacting with a smart card for authentication is similar to the previous one. After presenting JaCarta PKI (the first factor) and unlocking it by entering the PIN code (second factor), the credentials are checked, after which the user gets access or denial of service.
During the webinar, for our part, we tried to reflect the trend of digitalization of jobs, the development of the BYOD format and the use of various “untrusted” networks, from the aspect of the importance of protecting virtual infrastructure from unauthorized access and other attacks, the importance of using several authentication factors. They also talked about the advantages of using PKI electronic keys. And in general, topics were revealed for what it is needed, how to start using multi-factor authentication in Citrix, and how it works.
They touched upon an interesting topic of authentication based on one-time passwords; perhaps, a separate webinar will be held on the topic of OTP. If you are interested in this topic, or have other interesting questions, you can write to us about it.
Recording a webinar with our participation is onYoutube channel Citrix_ru .
The topic of the next technical webinar in the series of security enhancements will be authentication in Citrix according to GOST algorithms using the Gatekeeper solution from Sovintegra. This solution works with JaCarta GOST as a secure private key carrier and GOST certificate. This webinar will be held tomorrow, if you hurry, you can find an open link to register on facebook citrix_ru.
The channel also has past interesting technical webinars of this series:
- Encryption of interaction between all Citrix components using TLS;
- SAML authentication , the example demonstrates how to configure authentication in Citrix via Google.
I will add that in a similar way, through ADFS, a bunch of local AD is implemented with cloud Citrix, including with certificate authentication. As shown in the diagram below.

It works like this.
There are a number of external devices and JaCarta dongle users who are trying to access the resource pool through NetScaler. Next, the system redirects the user request to the proxy server for authentication. After successful authentication, the user is redirected to the EC for two-factor authentication. Using the JaCarta PKI key, with the certificate located on it, the user enters a PIN code. The system returns authentication data to ADFS, which in turn returns data to NetScaler. Next, the user gets access to the resource pool, or a denial of service message.
