Conference DEFCON 18. Practical espionage using a mobile phone. Part 2
- Transfer
Conference DEFCON 18. Practical espionage using a mobile phone. Part 1
We want to use certain methods to speed up the capture of phones with a fake network. At the moment we have a simple IMSI interceptor, you can try to call and hear the warning I recorded. I see that several people raised their hands. I mean, you guys are connecting to my network, and I intercept all your traffic.
First, I now know all your IMSIs and can filter them, leaving only the IMSI of the specific person who is my goal. I can do the same with IMEI filtering, which are phone identifiers. For example, I can only allow “Nokia” phones or “iPhones” to connect to the network. I can make it so that only this particular IMEI will be in my network and no one else. I can restrict access with a variety of options.
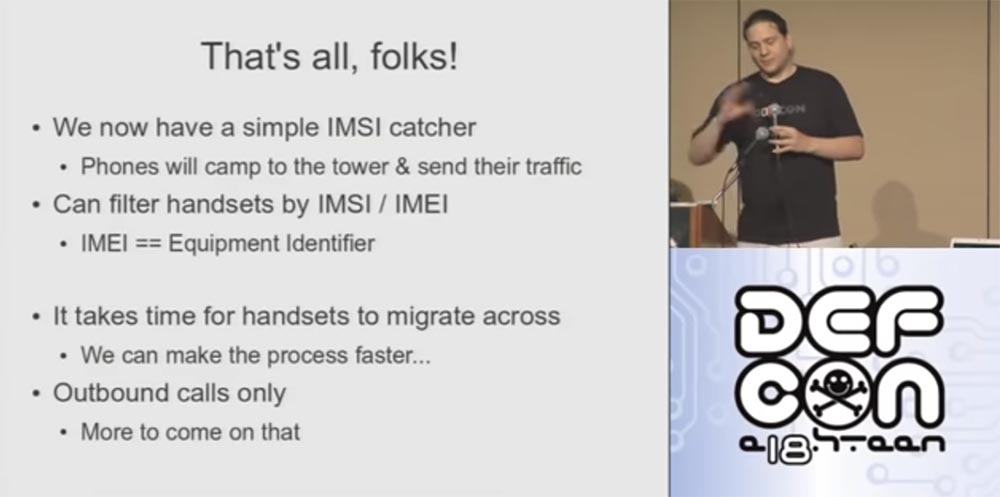
As I already mentioned, it takes time for people to migrate from the official network to my network, and we can do it faster, I will tell about it in a second. One of the main limitations of this system is that it only receives outgoing calls. When you connect to my network, regardless of whether it is T-Mobile or AT & T, your phone is turned off, because you really are not connected to any of the legal cell phone towers. That way, as soon as a call comes in, it goes straight to your voicemail. This problem is resolved, later I will show you that outgoing calls can also be recorded.
So how to speed up the connection, because I do not want to sit here all day, watching how your phones connect to my network? There are several acceleration technologies using these methods:
Raskremnem "neighborhood" GSM. Each base station knows which towers are located nearby, and when the phone is connected to it, it receives a list of "neighbors", that is, information on which channel each station works.

Your phone will monitor all these channels and monitor the signal strength, and if the signal of the neighboring tower turns out to be stronger, then it will connect to it. What are the benefits of this? We know that the cell phone will monitor the neighboring frequencies, so if we examine the entire zone and find out which towers surround us, we will be able to figure out which particular frequency the phone selects and which tower it connects to. In the end, we will be able to find a nearby channel, which may be located on the other side of the tower, and tune our station to the frequency that, as I know, your phone perceives. Suppose your phone connects to the base station, everything is going well, but then you drove a little down the street and the other tower was closer to the phone, so I just switch to its frequency so as not to lose you. In this way,
Actually it is quite easy. Suppose I have a Nokia 3310 (900/1800) or 3390 (1900) phone that accepts European and one of the American frequency bands. This phone supports the Network Monitor network monitoring mode, in which the logs of all that the GSM phone is doing are recorded every packet that it sent to the base station and every response received from it. It does not provide you with any advantages of hacking or capturing this phone, but gives full information about what this phone sees in the GSM network.
If you get one of these phones, you will need a special patch cable with Fbus / Mbus adapters and a program to control the phone called Gammu. This is an open source program, it connects to the phone through a computer using such a cable and simply displays the trace as an XML file that you can open in Wireshark. The list of adjacent towers is contained in the line "System Info type 2".
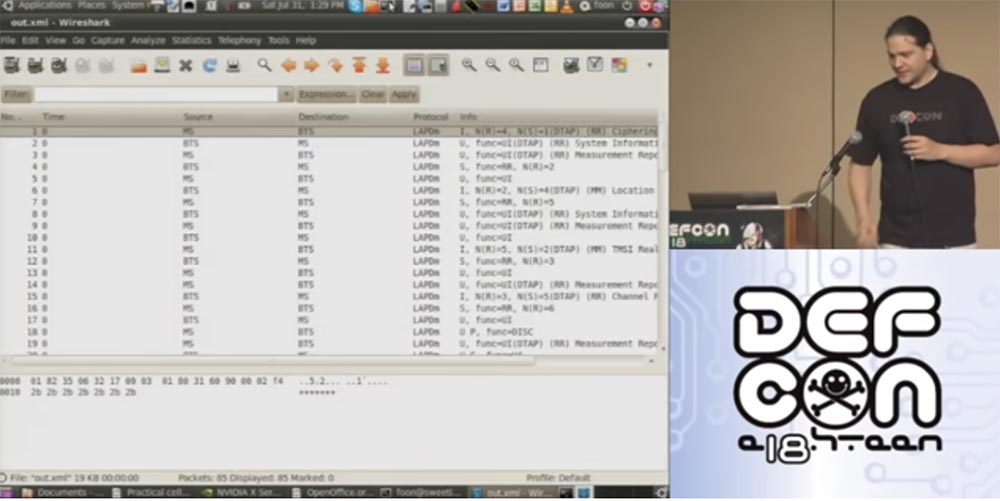
Now I will show you demo number 3, namely, what the traffic caught by Wireshark looks like. On this screen you see the traffic that I caught and recorded last night from a phone connected to the T-Mobile network.
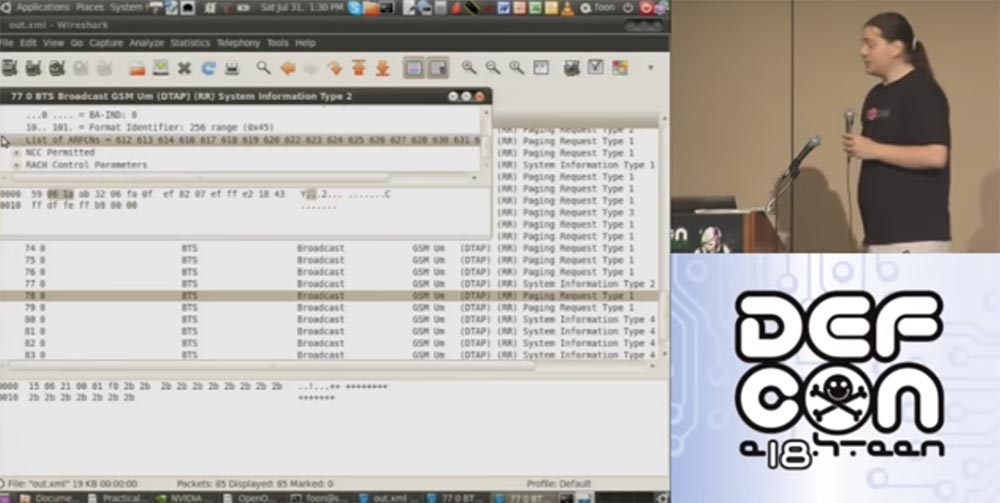
Here you see various GSM messages, and if you find the “System Info type 2” line among the packages on the right and click on it, you can get a list of neighboring GSM towers.
So you just take this phone, connect it to the computer via an adapter cable, launch Gammu, view the list of channels in Wireshark, compare them with what you know, that is, literally turn on the radio at each of these frequencies and see if you get with a signal. It is quite easy. With this technology, you can find a “neighbor” that is not used in the local zone, use it and thereby increase the connection speed. Today I just wanted to show you that an attacker can just as easily use this technique to grab your phone.
We can use another way to speed up the connection by changing the LAC code. This is the location code broadcast by the BTS base station, which groups together a bunch of towers located in the same area. That is, you have a bunch of towers in the same area providing the same LAC. They can also be manipulated. When the phone monitors all neighboring towers and at the same time the LAC changes, it can be concluded that the phone is moving. If the phone really moved to another area, it is necessary to reassign the station, that is, transfer it to another tower.
With the help of my local Open BTS, I fully control the LAC and can change it. Then all the phones in the vicinity will say: "hey, look, the LAC has changed, which means I drove 50 miles from the old tower and should connect to this new tower!" Thus, by “scrolling” other LACs every few minutes, that is, periodically changing the area code, you can attach even more phones to your station.
I'll show you the demo how to change the LAC. Let's first see how many phones are currently in my network. Before we faked the AT & T operator’s network, we had 30 connected handsets. Then I used AT & T MMC and MCC, and we see that there are 24 phones connected to the network at the moment. TIMSI has a timeout, so the repeated command that I enter follows with some delay, and it also shows that we now have 24 connected phones. You can not pay attention to it, we still have a whole bunch of phones.
We can again use the Cell ID command to scroll the LAC. My location code was 666, I think I should change it to 31337 and leave the Cell ID on 10. In fact, I will also change the Cell ID to the cell, just so that the phones know that this is a new tower. It is absolutely not difficult to change the LAC. As I said, now the phones will think that they have changed their location, and the number of phones connected to the new tower should increase.
We will come back to this after we consider the following method - launching the phone, or loading the phone with information. When the phone just turns on, before finding its first tower, it knows nothing - neither the frequency of the tower, nor the LAC, nor the neighboring towers. Therefore, after switching on, it performs a long scan of the entire frequency range, finds the towers, checks them with the MNC and MCC, tries to find out if there is a network nearby, the connection to which its SIM card allows, checks the signal strength and finally connects to the “most powerful” the tower.
As soon as he starts to find the towers, the scanning range is limited, while the phone performs scanning in a smaller volume, but faster because it already has some information about which frequency bands are used, which towers and which channels to search for. The attacker can use this to his advantage, because a similar process occurs when the phone loses the signal.
If the hacker uses DoS in relation to the network service, the phones lose the signal and start scanning the network in a larger range, which increases the chance of connecting to the attacker’s tower.
How can I make the phone lose the signal? In this example, I will only talk about the second generation of the 2G GSM connection, because 3G has much more security. So, if you jam some GSM band, the phones begin to perform an unfolded slow scan, thereby increasing the chance to find exactly our tower.
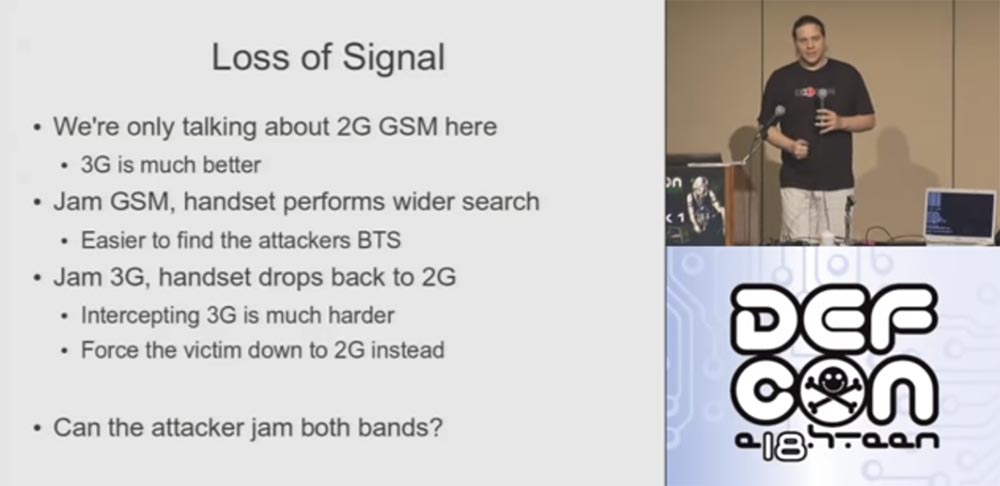
However, if you use 3G, I can’t do anything, because, thanks to powerful protocols, it’s much more difficult to intercept 3G. Therefore, we need to force the phones to connect to the 2G network, turning off the 3G signal. If your phones lose the ability to connect to the 3G network, they are happy to switch to 2G.
All you have to do is broadcast the “noise”, which will block the ability to talk on the 3G network and force the phone to switch to 2G with message passing in plain text. That is, if you cannot connect to port 22, then you try to connect to port 23. You can consider 3G as the SSH analogue and GSM as the Telnet analogue, so a situation occurs that is similar to that when you can’t connect to the SSH port, you connect to telnet port. This is exactly what a cell phone does in a similar situation.
The question is how difficult it is to mute the cellular signal in a certain frequency range. Consider what constitutes noise generation. All an attacker has to do is provide “noise.” When I talk about "noise", I mean a very specific thing. I do not mean an accident, but a completely flat spectral noise overlapping the entire frequency range and each channel.
What is most effective to do in this case, except to completely destroy the tower? This is to exclude the possibility of telephones to see this tower, completely disguised by its noise. The noise generator is not too expensive, on eBay you can buy it for $ 450. I have one such generator with me. As you can see, this is quite a hard thing!

If I connect it to the power amplifier, and the amplifier to the antenna and set it up exactly, then turning it on will cause serious disruption to the cellular network. As I said, the noise generator is on eBay $ 450, an amplifier with a power of 100 watts can be bought on the Internet for $ 400, and noise with a power of 100 watts can cause just huge network failures.
This generator operates in 2 modes - one is designed for jamming in the range of 900 MHz, the second - in the range of 1900 MHz. On the slide you see the low-frequency spectrum analyzer curve, on the left - about 500 megahertz, on the right, the highest frequency of 2.5 GHz.
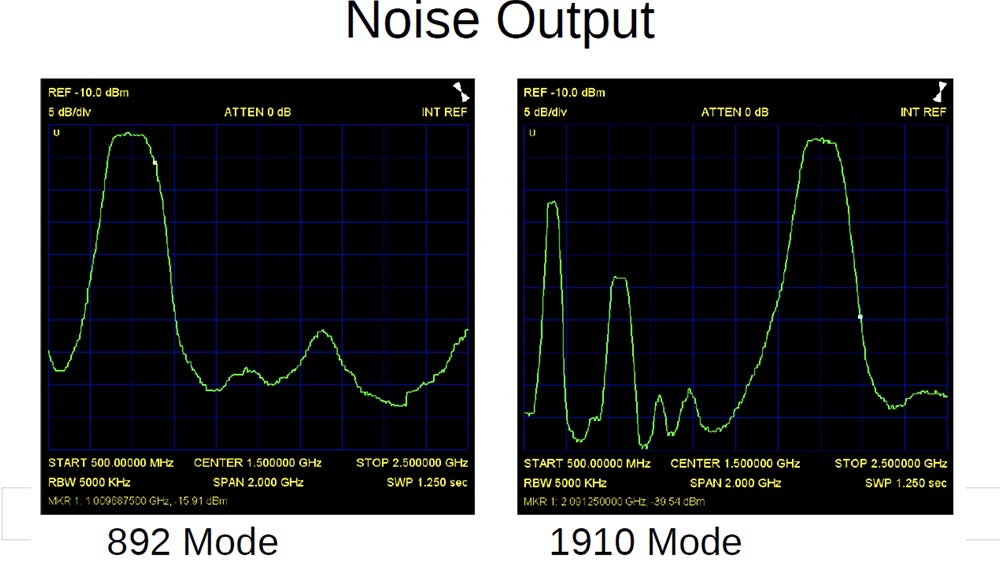
On the left, you see a “big and thick” block in the 900 MHz frequency range. The amplifier can supply the exact same unit on any cellular channel in the range from 850 to 950 megahertz.
Turn this thing on and the connection at 850 and 950 will simply stop working. Similarly, it happens in the 1900 mode - a little further you see the main frequency peak again.
Demo number 5 will show how the jamming of the carrier frequency of cellular communication. However, do not think that I am so stupid! If I turn this noise-generating piece into a 100-watt amplifier and connect it to the antenna, I’ll pick out all the cellular communications in the area — GSM, CDMA, 3G, Verizon, and virtually every cell phone in all of Las Vegas, if not further.
(applause and laughter)

So I will never turn this thing on. The main reason I have it is that this is a fabulously useful thing in the role of test equipment. If you are trying to classify filters, you pass white noise through the filter, compare the input and output waveforms, and calibrate the filter very accurately. That's what I'm using this interference generator for, and not for organizing a cellular DoS attack. The fact is that there is no protection from such a “jammer”.
You only need a short start of the generator with a duration of a few seconds to “put in” the entire network, but such a demonstration of power will be completely inappropriate here. I think that a 100 watt amplifier and a properly tuned antenna can cut off the entire Las Vegas cellular system.
Another method that we can use to intercept phones is called Receive gain, or “receive gain”. It is that the BTS can send a command to the phone: “perceive my signal as if it were X dB stronger than it actually is”. The meaning of this is as follows.
Imagine a scale graduated from +50 to -100. Anyone familiar with RF will understand why I chose this range. Suppose that my signal dropped to -80, it is really very low. I can order your phone to simply add 100 to this value, resulting in a level signal of + 20 dBm. The phone will think: “fine, this is the most powerful tower in the area, now I will connect to it”! Yes, it looks ridiculous, it is a hoax, but again, this is another great example of instructions that BTS can send to the telephone. That is, it is completely unnecessary for me to have a more powerful signal, it is enough for me to convince the phone that my signal is really stronger than everyone around. And the phone will believe this, because this is how GSM works, and it is simply obliged to carry out tower commands. Of course, An attacker can use this method of attracting phones and, having a rather weak signal, win a contest with more powerful towers. Open BTS does not yet support this feature, so I will not be able to demonstrate this method. This, in fact, is the essence of the R & S patents used in the IMSI interceptor.
In the UK, there was a case where someone sold an IMSI interceptor technology using a receive amplification method, and R & S sued it because this method was patented by their company. Substitution of MNC, MCC, renaming of networks is all quite trivial, but the method described above is patented by the developers of the “catcher” of networks.
As I already mentioned, we do not see incoming calls, we only see outgoing calls. This is because the IMSI "catcher" is a completely isolated cellular network. The operator believes that your phone is turned off or does not receive a signal. In this case, it sends all calls to you sent to your voicemail, with the result that the attacker does not see incoming calls.

How can this be circumvented? Obviously, if you contacted my tower, it will ask for authentication, your IMSI, and the phone will be happy to provide it, so I will have your IMSI. What can I do? Go to AT & T and say, “Hey, here’s my IMSI, I lured him from another guy, but you don’t have to know about it, and I know that this guy is not online because this is my network”? The problem is that I do not know the secret key on the SIM card. What can happen when I claim that this is my IMSI on the AT & T network? They send me a random 32-bit number, and it usually happens that it goes to a SIM card, is encrypted with your secret key and is divided into 2 parts. Half is sent to the tower and serves as proof that you know the secret key, and the other half is used as the encryption key.
How can I use it? I can just send this number to your phone, who knows how to encrypt the secret key, do the rest and send me the answer. However, in fact, he cannot send me an answer, because I am not able to receive incoming calls. Only one way out - to crack the secret key.
Who of you was at the presentation of the cracker of keys Cracker 5.1 at the Black Hat conference, he knows that this hacker has a serious limitation - he does not work at base stations with frequency hopping, as every base station in the world is. In real applications this does not happen. But I set the frequency “jumps” in my BTS, so I can completely turn them off, so as not to worry about anything, and then use the “rainbow tables” to crack the secret key.
After that, I will restore the session key. Now I know the session key and the response key for authentication and I can use all this for the mobile operator. It will take a little time, but in the end, I will get his answer, and my phone will be authorized on a legal basis.
This method is not yet implemented in my system, but it can definitely be done, this is the technology that commercial IMSI catchers use to intercept incoming calls. Of course, now I can not do it in my system, but it is absolutely possible.
I'll tell you a little more about hacking session key. This is the only time in the process of using the IMSI catcher you may need a crypto attack.

All I needed from the point of view of encryption when setting up my base station is to disable the traffic encryption function A5 / 0. The easiest way is to crack the A5 / 2, but some phones drop the A5 / 2, using the A5 / 1 instead, which is also not difficult to crack using the “rainbow table”. In any case, outgoing calls to your phone come to me in plain text.
How to deal with all this? The reality is that there is no convenient solution, because GSM is vulnerable in itself, it is the same Telnet, only in a cellular system. In order to fix GSM, it needs to be completely changed. You will have to update each phone, redo each tower, change all networks and so on. So why do it if you can just go to the 3G standard?
Thus, the only correct solution is the transition to 3G and later cellular communication protocols. 3G authentication is much better, 3.5G (HSPA), 3.9 G, LTE and subsequent protocols are built on the same principles. The main solution is to simply disable 2G.
Raise your hands, who has Android phones? You see that in their settings there is a function “use only 2G networks”. Presumably, it saves battery, but how many people have ever seen a phone that has the function “use only 3G networks”? Great, someone has a BlackBerry with such a function, but neither “Android” nor “iPhone” have it, so how can we feel safe?
Of course, 3G is not devoid of vulnerabilities, and if the protocol itself is hard to crack, then you can try to crack the KASUMI encryption used in it, also denoted A5 / 3, such cases are known. But still it is better to use this particular cellular standard. Just look at the screen of your phone, and if you see small 3G letters at the top, then you are fine. So the best way to protect yourself from online espionage is to turn off 2G. 3.5G networks have already appeared, 4G networks are on the horizon, so try to take advantage of this.
And now we will go to the final demo. Let's see how many phones are in my network now. So, only 17 people, probably, people began to return to the normal network! Perhaps your phones first believed that I was a real AT & T network, but then they realized that it was behaving somehow wrong and decided to leave.
One way or another, feel free, call for free from my network anywhere, the only restriction is that you have to dial 1 before the called number. If you know the code of any country, call, do not hesitate, you are limited to only 20 dollars in my SIP account. If you have not heard the recorded message, where I am talking about connecting to the network, try again in a couple of minutes, have fun, and while I answer the questions ...
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
We want to use certain methods to speed up the capture of phones with a fake network. At the moment we have a simple IMSI interceptor, you can try to call and hear the warning I recorded. I see that several people raised their hands. I mean, you guys are connecting to my network, and I intercept all your traffic.
First, I now know all your IMSIs and can filter them, leaving only the IMSI of the specific person who is my goal. I can do the same with IMEI filtering, which are phone identifiers. For example, I can only allow “Nokia” phones or “iPhones” to connect to the network. I can make it so that only this particular IMEI will be in my network and no one else. I can restrict access with a variety of options.

As I already mentioned, it takes time for people to migrate from the official network to my network, and we can do it faster, I will tell about it in a second. One of the main limitations of this system is that it only receives outgoing calls. When you connect to my network, regardless of whether it is T-Mobile or AT & T, your phone is turned off, because you really are not connected to any of the legal cell phone towers. That way, as soon as a call comes in, it goes straight to your voicemail. This problem is resolved, later I will show you that outgoing calls can also be recorded.
So how to speed up the connection, because I do not want to sit here all day, watching how your phones connect to my network? There are several acceleration technologies using these methods:
- a list of "neighbors", that is, located near the towers;
- replacement of the local area code LAC;
- phone download;
- gain reception.
Raskremnem "neighborhood" GSM. Each base station knows which towers are located nearby, and when the phone is connected to it, it receives a list of "neighbors", that is, information on which channel each station works.

Your phone will monitor all these channels and monitor the signal strength, and if the signal of the neighboring tower turns out to be stronger, then it will connect to it. What are the benefits of this? We know that the cell phone will monitor the neighboring frequencies, so if we examine the entire zone and find out which towers surround us, we will be able to figure out which particular frequency the phone selects and which tower it connects to. In the end, we will be able to find a nearby channel, which may be located on the other side of the tower, and tune our station to the frequency that, as I know, your phone perceives. Suppose your phone connects to the base station, everything is going well, but then you drove a little down the street and the other tower was closer to the phone, so I just switch to its frequency so as not to lose you. In this way,
Actually it is quite easy. Suppose I have a Nokia 3310 (900/1800) or 3390 (1900) phone that accepts European and one of the American frequency bands. This phone supports the Network Monitor network monitoring mode, in which the logs of all that the GSM phone is doing are recorded every packet that it sent to the base station and every response received from it. It does not provide you with any advantages of hacking or capturing this phone, but gives full information about what this phone sees in the GSM network.
If you get one of these phones, you will need a special patch cable with Fbus / Mbus adapters and a program to control the phone called Gammu. This is an open source program, it connects to the phone through a computer using such a cable and simply displays the trace as an XML file that you can open in Wireshark. The list of adjacent towers is contained in the line "System Info type 2".
Now I will show you demo number 3, namely, what the traffic caught by Wireshark looks like. On this screen you see the traffic that I caught and recorded last night from a phone connected to the T-Mobile network.

Here you see various GSM messages, and if you find the “System Info type 2” line among the packages on the right and click on it, you can get a list of neighboring GSM towers.

So you just take this phone, connect it to the computer via an adapter cable, launch Gammu, view the list of channels in Wireshark, compare them with what you know, that is, literally turn on the radio at each of these frequencies and see if you get with a signal. It is quite easy. With this technology, you can find a “neighbor” that is not used in the local zone, use it and thereby increase the connection speed. Today I just wanted to show you that an attacker can just as easily use this technique to grab your phone.
We can use another way to speed up the connection by changing the LAC code. This is the location code broadcast by the BTS base station, which groups together a bunch of towers located in the same area. That is, you have a bunch of towers in the same area providing the same LAC. They can also be manipulated. When the phone monitors all neighboring towers and at the same time the LAC changes, it can be concluded that the phone is moving. If the phone really moved to another area, it is necessary to reassign the station, that is, transfer it to another tower.
With the help of my local Open BTS, I fully control the LAC and can change it. Then all the phones in the vicinity will say: "hey, look, the LAC has changed, which means I drove 50 miles from the old tower and should connect to this new tower!" Thus, by “scrolling” other LACs every few minutes, that is, periodically changing the area code, you can attach even more phones to your station.
I'll show you the demo how to change the LAC. Let's first see how many phones are currently in my network. Before we faked the AT & T operator’s network, we had 30 connected handsets. Then I used AT & T MMC and MCC, and we see that there are 24 phones connected to the network at the moment. TIMSI has a timeout, so the repeated command that I enter follows with some delay, and it also shows that we now have 24 connected phones. You can not pay attention to it, we still have a whole bunch of phones.
We can again use the Cell ID command to scroll the LAC. My location code was 666, I think I should change it to 31337 and leave the Cell ID on 10. In fact, I will also change the Cell ID to the cell, just so that the phones know that this is a new tower. It is absolutely not difficult to change the LAC. As I said, now the phones will think that they have changed their location, and the number of phones connected to the new tower should increase.
We will come back to this after we consider the following method - launching the phone, or loading the phone with information. When the phone just turns on, before finding its first tower, it knows nothing - neither the frequency of the tower, nor the LAC, nor the neighboring towers. Therefore, after switching on, it performs a long scan of the entire frequency range, finds the towers, checks them with the MNC and MCC, tries to find out if there is a network nearby, the connection to which its SIM card allows, checks the signal strength and finally connects to the “most powerful” the tower.
As soon as he starts to find the towers, the scanning range is limited, while the phone performs scanning in a smaller volume, but faster because it already has some information about which frequency bands are used, which towers and which channels to search for. The attacker can use this to his advantage, because a similar process occurs when the phone loses the signal.
If the hacker uses DoS in relation to the network service, the phones lose the signal and start scanning the network in a larger range, which increases the chance of connecting to the attacker’s tower.
How can I make the phone lose the signal? In this example, I will only talk about the second generation of the 2G GSM connection, because 3G has much more security. So, if you jam some GSM band, the phones begin to perform an unfolded slow scan, thereby increasing the chance to find exactly our tower.

However, if you use 3G, I can’t do anything, because, thanks to powerful protocols, it’s much more difficult to intercept 3G. Therefore, we need to force the phones to connect to the 2G network, turning off the 3G signal. If your phones lose the ability to connect to the 3G network, they are happy to switch to 2G.
All you have to do is broadcast the “noise”, which will block the ability to talk on the 3G network and force the phone to switch to 2G with message passing in plain text. That is, if you cannot connect to port 22, then you try to connect to port 23. You can consider 3G as the SSH analogue and GSM as the Telnet analogue, so a situation occurs that is similar to that when you can’t connect to the SSH port, you connect to telnet port. This is exactly what a cell phone does in a similar situation.
The question is how difficult it is to mute the cellular signal in a certain frequency range. Consider what constitutes noise generation. All an attacker has to do is provide “noise.” When I talk about "noise", I mean a very specific thing. I do not mean an accident, but a completely flat spectral noise overlapping the entire frequency range and each channel.
What is most effective to do in this case, except to completely destroy the tower? This is to exclude the possibility of telephones to see this tower, completely disguised by its noise. The noise generator is not too expensive, on eBay you can buy it for $ 450. I have one such generator with me. As you can see, this is quite a hard thing!

If I connect it to the power amplifier, and the amplifier to the antenna and set it up exactly, then turning it on will cause serious disruption to the cellular network. As I said, the noise generator is on eBay $ 450, an amplifier with a power of 100 watts can be bought on the Internet for $ 400, and noise with a power of 100 watts can cause just huge network failures.
This generator operates in 2 modes - one is designed for jamming in the range of 900 MHz, the second - in the range of 1900 MHz. On the slide you see the low-frequency spectrum analyzer curve, on the left - about 500 megahertz, on the right, the highest frequency of 2.5 GHz.

On the left, you see a “big and thick” block in the 900 MHz frequency range. The amplifier can supply the exact same unit on any cellular channel in the range from 850 to 950 megahertz.
Turn this thing on and the connection at 850 and 950 will simply stop working. Similarly, it happens in the 1900 mode - a little further you see the main frequency peak again.
Demo number 5 will show how the jamming of the carrier frequency of cellular communication. However, do not think that I am so stupid! If I turn this noise-generating piece into a 100-watt amplifier and connect it to the antenna, I’ll pick out all the cellular communications in the area — GSM, CDMA, 3G, Verizon, and virtually every cell phone in all of Las Vegas, if not further.
(applause and laughter)

So I will never turn this thing on. The main reason I have it is that this is a fabulously useful thing in the role of test equipment. If you are trying to classify filters, you pass white noise through the filter, compare the input and output waveforms, and calibrate the filter very accurately. That's what I'm using this interference generator for, and not for organizing a cellular DoS attack. The fact is that there is no protection from such a “jammer”.
You only need a short start of the generator with a duration of a few seconds to “put in” the entire network, but such a demonstration of power will be completely inappropriate here. I think that a 100 watt amplifier and a properly tuned antenna can cut off the entire Las Vegas cellular system.
Another method that we can use to intercept phones is called Receive gain, or “receive gain”. It is that the BTS can send a command to the phone: “perceive my signal as if it were X dB stronger than it actually is”. The meaning of this is as follows.
Imagine a scale graduated from +50 to -100. Anyone familiar with RF will understand why I chose this range. Suppose that my signal dropped to -80, it is really very low. I can order your phone to simply add 100 to this value, resulting in a level signal of + 20 dBm. The phone will think: “fine, this is the most powerful tower in the area, now I will connect to it”! Yes, it looks ridiculous, it is a hoax, but again, this is another great example of instructions that BTS can send to the telephone. That is, it is completely unnecessary for me to have a more powerful signal, it is enough for me to convince the phone that my signal is really stronger than everyone around. And the phone will believe this, because this is how GSM works, and it is simply obliged to carry out tower commands. Of course, An attacker can use this method of attracting phones and, having a rather weak signal, win a contest with more powerful towers. Open BTS does not yet support this feature, so I will not be able to demonstrate this method. This, in fact, is the essence of the R & S patents used in the IMSI interceptor.
In the UK, there was a case where someone sold an IMSI interceptor technology using a receive amplification method, and R & S sued it because this method was patented by their company. Substitution of MNC, MCC, renaming of networks is all quite trivial, but the method described above is patented by the developers of the “catcher” of networks.
As I already mentioned, we do not see incoming calls, we only see outgoing calls. This is because the IMSI "catcher" is a completely isolated cellular network. The operator believes that your phone is turned off or does not receive a signal. In this case, it sends all calls to you sent to your voicemail, with the result that the attacker does not see incoming calls.

How can this be circumvented? Obviously, if you contacted my tower, it will ask for authentication, your IMSI, and the phone will be happy to provide it, so I will have your IMSI. What can I do? Go to AT & T and say, “Hey, here’s my IMSI, I lured him from another guy, but you don’t have to know about it, and I know that this guy is not online because this is my network”? The problem is that I do not know the secret key on the SIM card. What can happen when I claim that this is my IMSI on the AT & T network? They send me a random 32-bit number, and it usually happens that it goes to a SIM card, is encrypted with your secret key and is divided into 2 parts. Half is sent to the tower and serves as proof that you know the secret key, and the other half is used as the encryption key.
How can I use it? I can just send this number to your phone, who knows how to encrypt the secret key, do the rest and send me the answer. However, in fact, he cannot send me an answer, because I am not able to receive incoming calls. Only one way out - to crack the secret key.
Who of you was at the presentation of the cracker of keys Cracker 5.1 at the Black Hat conference, he knows that this hacker has a serious limitation - he does not work at base stations with frequency hopping, as every base station in the world is. In real applications this does not happen. But I set the frequency “jumps” in my BTS, so I can completely turn them off, so as not to worry about anything, and then use the “rainbow tables” to crack the secret key.
After that, I will restore the session key. Now I know the session key and the response key for authentication and I can use all this for the mobile operator. It will take a little time, but in the end, I will get his answer, and my phone will be authorized on a legal basis.
This method is not yet implemented in my system, but it can definitely be done, this is the technology that commercial IMSI catchers use to intercept incoming calls. Of course, now I can not do it in my system, but it is absolutely possible.
I'll tell you a little more about hacking session key. This is the only time in the process of using the IMSI catcher you may need a crypto attack.

All I needed from the point of view of encryption when setting up my base station is to disable the traffic encryption function A5 / 0. The easiest way is to crack the A5 / 2, but some phones drop the A5 / 2, using the A5 / 1 instead, which is also not difficult to crack using the “rainbow table”. In any case, outgoing calls to your phone come to me in plain text.
How to deal with all this? The reality is that there is no convenient solution, because GSM is vulnerable in itself, it is the same Telnet, only in a cellular system. In order to fix GSM, it needs to be completely changed. You will have to update each phone, redo each tower, change all networks and so on. So why do it if you can just go to the 3G standard?
Thus, the only correct solution is the transition to 3G and later cellular communication protocols. 3G authentication is much better, 3.5G (HSPA), 3.9 G, LTE and subsequent protocols are built on the same principles. The main solution is to simply disable 2G.
Raise your hands, who has Android phones? You see that in their settings there is a function “use only 2G networks”. Presumably, it saves battery, but how many people have ever seen a phone that has the function “use only 3G networks”? Great, someone has a BlackBerry with such a function, but neither “Android” nor “iPhone” have it, so how can we feel safe?
Of course, 3G is not devoid of vulnerabilities, and if the protocol itself is hard to crack, then you can try to crack the KASUMI encryption used in it, also denoted A5 / 3, such cases are known. But still it is better to use this particular cellular standard. Just look at the screen of your phone, and if you see small 3G letters at the top, then you are fine. So the best way to protect yourself from online espionage is to turn off 2G. 3.5G networks have already appeared, 4G networks are on the horizon, so try to take advantage of this.
And now we will go to the final demo. Let's see how many phones are in my network now. So, only 17 people, probably, people began to return to the normal network! Perhaps your phones first believed that I was a real AT & T network, but then they realized that it was behaving somehow wrong and decided to leave.
One way or another, feel free, call for free from my network anywhere, the only restriction is that you have to dial 1 before the called number. If you know the code of any country, call, do not hesitate, you are limited to only 20 dollars in my SIP account. If you have not heard the recorded message, where I am talking about connecting to the network, try again in a couple of minutes, have fun, and while I answer the questions ...
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January free of charge if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
