DEFCON 22. “Traveling the Dark Side of the Internet. Introduction to Tor, Darknet and Bitcoin »
- Transfer
My name is Grifter, next to my good friend Metacortex, we are from the DC801 group, which is based in Salt Lake City, Utah. We want to show something that looks pretty funny and to give you a guided tour on the dark side of the Internet.
We are both researchers who like to roam the dark alleys, for example, in Tokyo, I don’t even know where exactly this happened.
Metacortex: "To Shinjuku!"
Well, yes, it was in Shinjuk, I just did not pay attention to it. But this is exactly what we like to do, and we spent most of our trip on this activity. I think exploring the dark alleys is a good metaphor for describing the activities of hackers. We decided to take the train, and then chose a random number, it was 6, got off the train after 6 stops and just went wherever our eyes were. We did not know Japanese, did not know how to read or speak this language, but simply went to wander. It was cool, and we like that kind of activity.
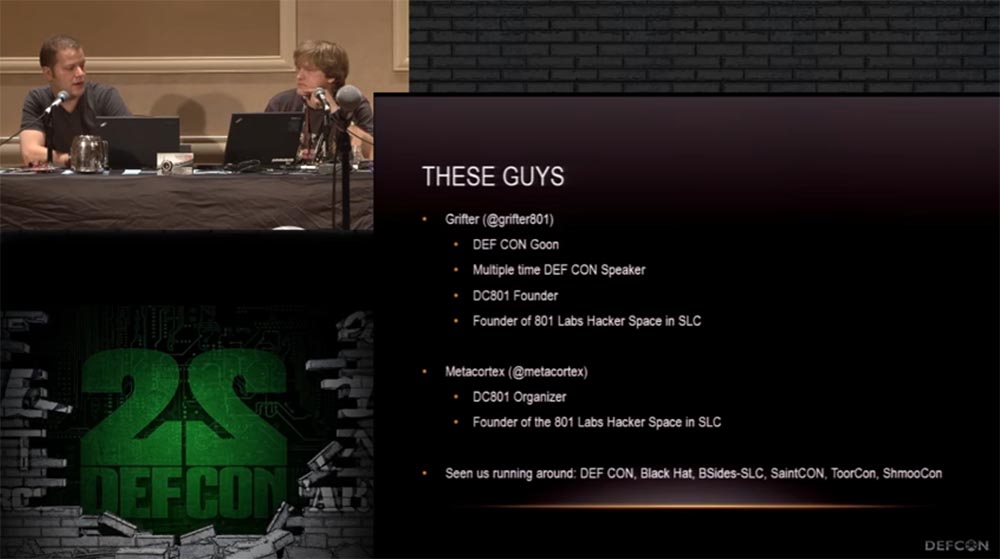
So, I, Grifter, the DEFCON bandit who has been the speaker of our conferences many times, this is my sixth speech. I am the creator of the DEFCON 801 group since ancient times and co-founder of the 801 Hacker Space laboratory in Salt Lake City.
Metacortex: this is my first ever performance at DEFCON, so I'm a little worried. I am an assistant to this laboratory and the organizer of the 801st group, so if you get to Salt Lake City, go visit, there you will find free booze.
You can also meet us at the DEFCON, Black Hat, BSides-SLC, SaintCON and ToorCon conferences.
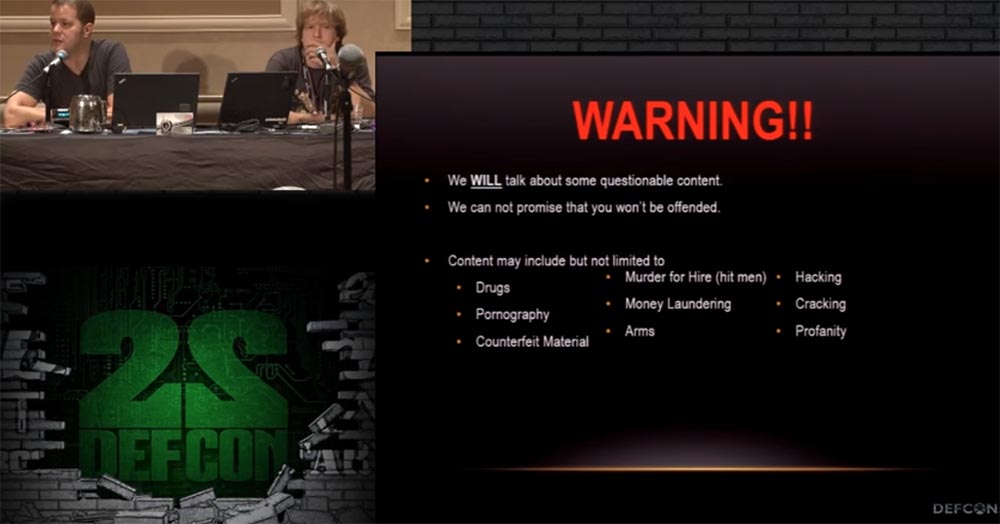
I'll start with a little caution. I know that goes without saying, but we are still talking about rather dubious things. But who can determine what is doubtful and what can be proved? We cannot promise that what we hear will not offend you, because we can talk about drugs, contract killings, hacking, weapons, pornography, and if this makes you a sad panda, you should cede your place in this room to someone else.
Now Metacortex has launched a clip on the screen. Who is the fan of this show, what is it called? "House of cards"? Yes exactly. For some reason we have no sound. This is the sad panda. Help us, sound men, all hope for you! Yeah, this is a bad cable ... this is USB for a sound card ... there is a problem in it ...
(Metacortex starts looking for another cable for a laptop, a guy comes on the scene trying to connect something, Grifter sings into the microphone: “Come on guys, help, and then we look here like gaddy assholes ... ”).

Nothing works, it was a bad idea!
But now the video finally comes with the sound:
"... 96% of the Internet, but most of it is unused in search engines, so we go here to find anything. Drugs, hired hackers.
- How did you get access to it?
- Pretty easy, I can show you if you want.
“Yes, of course, go on!”
“Okay, the first thing you need is Thor.” Some people prefer ITP, but I think Thor is better ... "
Yes, Thor is really much better!
And now we jumped onto the Darknet slide because Metacortex continues to torment its laptop and cannot find the desktop. Darknet is really a cool place , here you can hire hackers, wander around the black market and all that.

Finally Metacortex got to his desktop, and we continue the slide show in order.
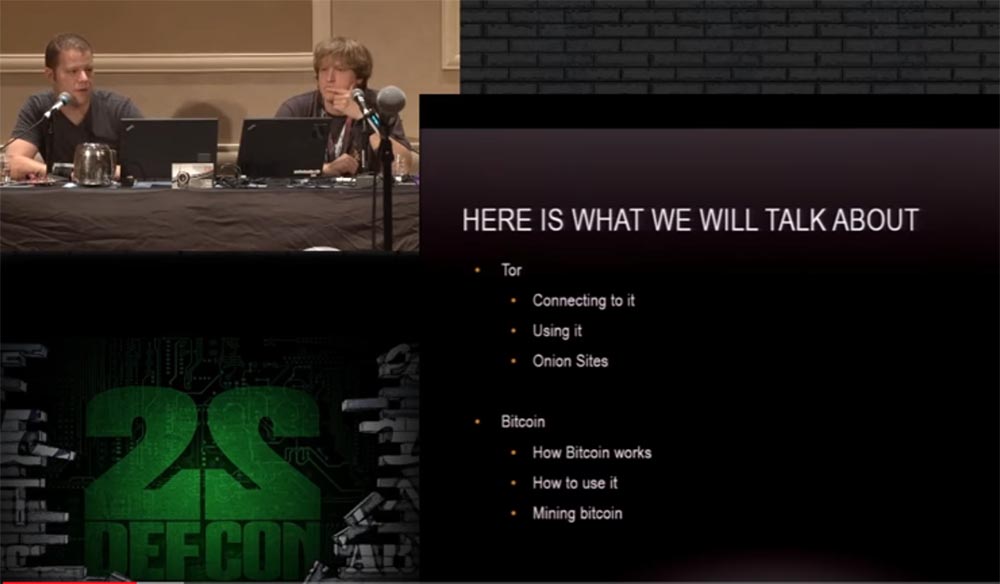
We will talk about Thor, how to connect to it and how to use it, and what Onion onion sites are. We will talk about Bitcoin, how it works, how to use it and how to mine bitcoins.
Interesting information about this can be found on Darknet forums, hacker forums, and carding forums. Do not think that the Dark Network is an extremely vile place. Here are Internet platforms for people who want to avoid government censorship and freely discuss issues and things related to their country, without fear that they will pick you up in the middle of the night and put a black bag on their heads. I will show you a couple of tricks how to find them, while remaining unidentified, I will talk about Darknet search engines and markets where you can order physical things. They will be delivered not to your home, but to another place where these things can be taken from and no one will know who you are.
Metacortex: so, let's move on to the first topic and consider what Tor is, most of the DEFCON participants have probably heard about it.
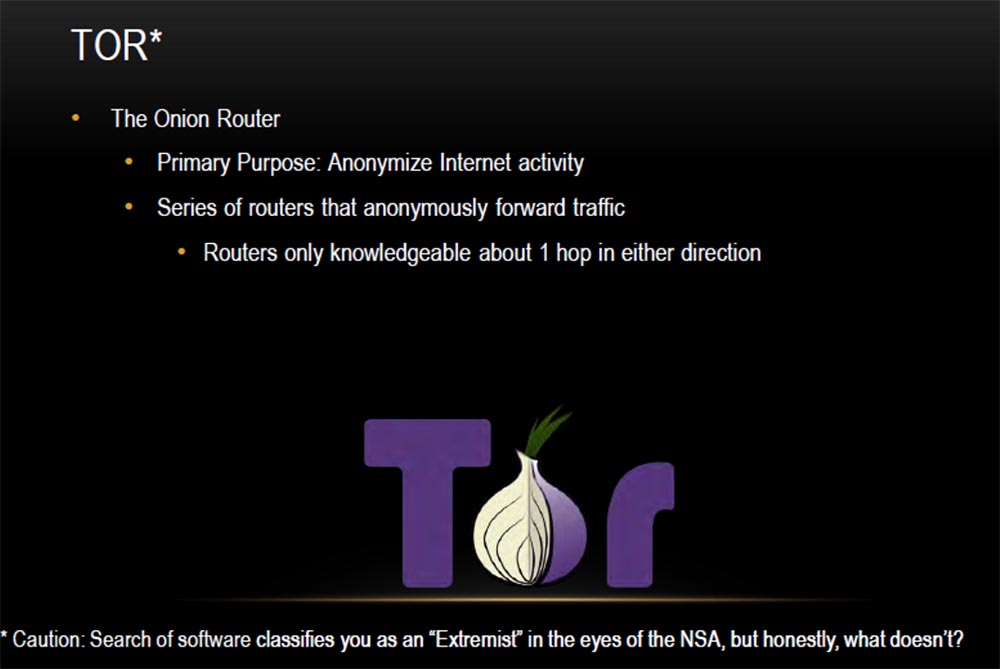
This is an onion router that makes your traffic anonymous. This is one of the most serious anonymizers, representing a series of routers that ensure the anonymity of your Internet activity.
Pay attention to the warning below: if you start looking for this anonymizer on the network, the NSA can put you on the list of extremists, but honestly, why not?
Grifter: this does not happen so fast, say, if you use Thor and download something from there for 3 years, then yes, you will be on the list. And now we are sure to get to the first lines of this list, because we are talking about Tor here on DEFCON.
Metacortex: The next slide shows an excellent diagram showing the principle of action of Thor. The “+” sign marks the nodes of the Tor network (distributed servers), green arrows indicate encrypted data chains, red arrows indicate unencrypted ones.

Alice uses the Thor client, which selects a random path to the desired server.
The only thing I don’t like here is the red arrow of Bob, which says that he uses unencrypted traffic, or, in the case of HTTP, it will be encrypted or unencrypted traffic.
We believe that Thor works like this (shows the clip).

Grifter: we, too, are jumping over these little things and boxes!
Metacortex: and I also scream with joy when I manage to join the Torah!
So how do we connect to the Tor network? There are several different possibilities - you can use the Linux command line or the Mac command line or a binary installation application for this thing. I prefer Linux, you see it on the slides, this is the command / etc / tor / torrc, which you set up the connection configuration for. This starts the socks5 proxy server on your local host and allows you to start the Top client on the selected port, by default it is port 9050, after you connect to the Tor network.
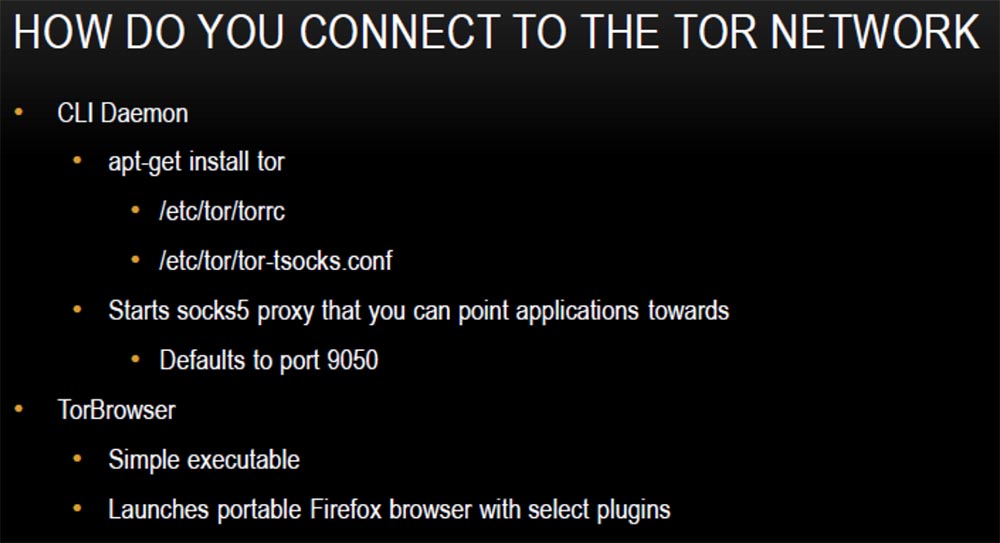
To work on the network you need to download and install the Tor client, it is very easy to use. It will provide a connection and launch the portable version of Firefox, which will be running Tor. You can also use additional plugins.
We will quickly go over this issue because we will show a demo version, this is how your screen will look after installing and connecting to the Tor network.
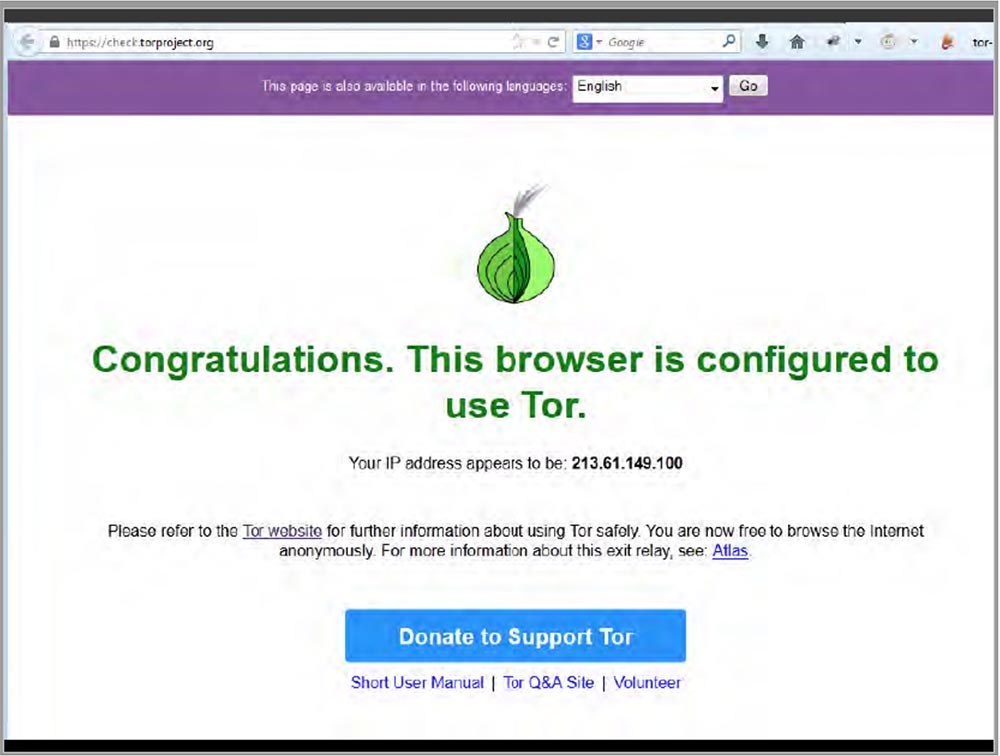
Today, the gods of video presentations are angry at me, but I still try to demonstrate to you the connection of my laptop to the Tor network. Here, a couple of seconds and you're done!
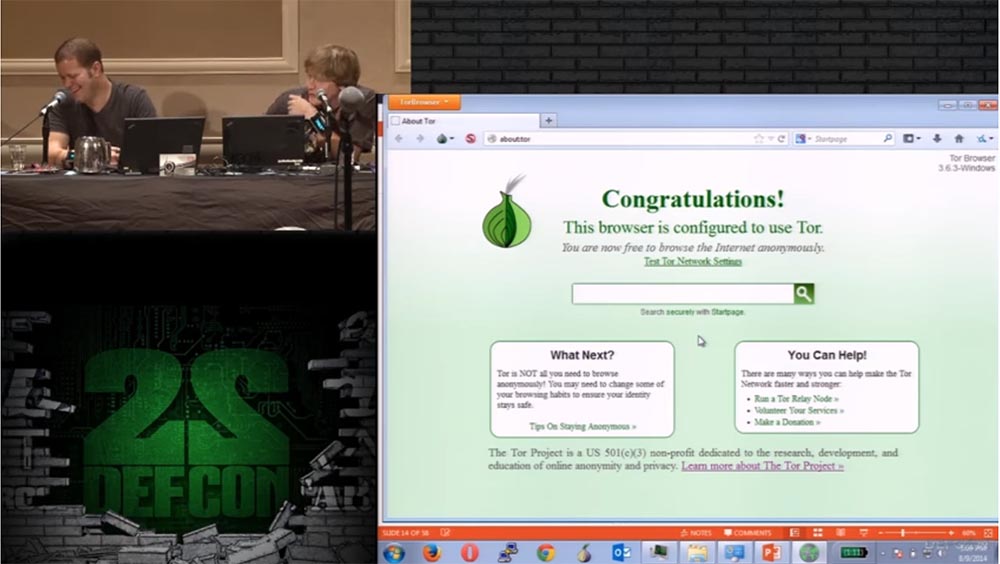
Grifter: you said you screamed like a moron when you connected to Thor!
The metacortex emits a victorious cry: “we see a message that this browser is configured to use Tor”!
I click on the search bar and theoretically become an anonymous user of the network. After connecting to the browser, we see the icons of already installed plugins on the toolbar.
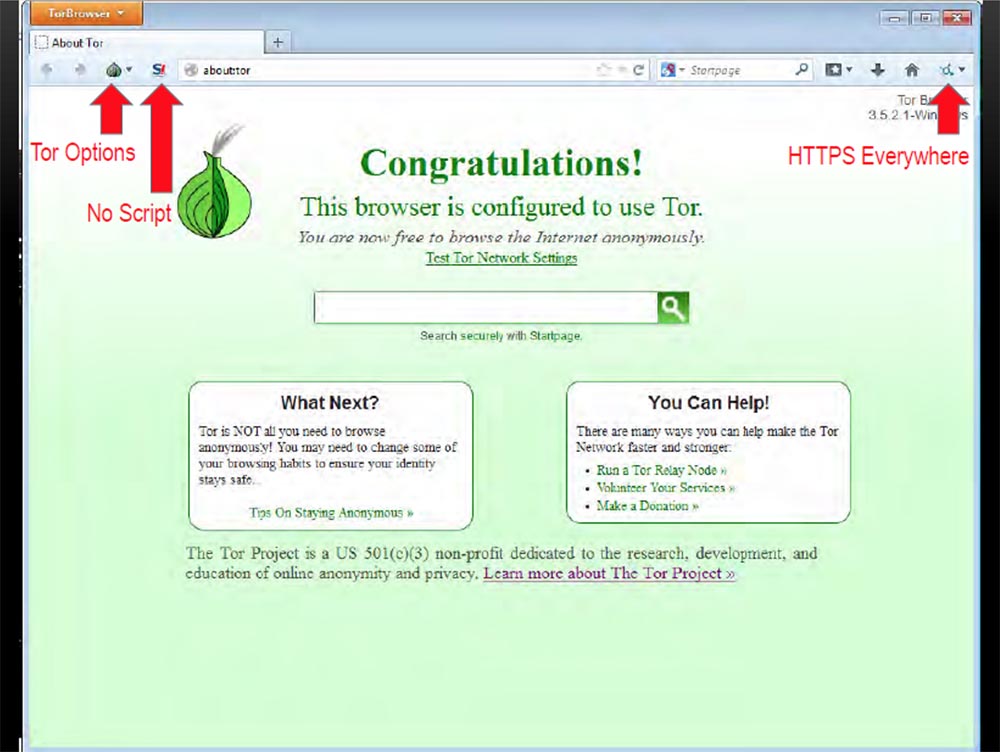
When you click on the bulb icon, a drop-down menu will appear with options where you can configure the Tor configuration. The icon in the form of the letter S with an exclamation mark means “no script”, the use of this plugin is very important, and the icon of the HTTPS Everywhere plugin in the form of a small circle on the right indicates that a secure HTTPS connection is used everywhere when browsing the pages. This means that even when passing between the Tor nodes in any direction, all our traffic will be encrypted.
Another way to ensure anonymity is to use the TAILS distribution. This is a Debian-based Linux Live distribution. It “wraps” all outgoing traffic in Tor and blocks non-anonymous traffic. This program does not leave any traces on the computer disk, so you can work completely anonymously. It works right out of the box and comes preloaded with apps like the HTTPS Everywhere plugin, plugin, OpenPGP, Pidgin OTR, Truecrypt and KeePassX, the most important of which is Truecrypt.
TAILS will transfer you to another interface - this is how it looks if you run it in Normal mode. This is the standard Debian desktop, nothing fun.
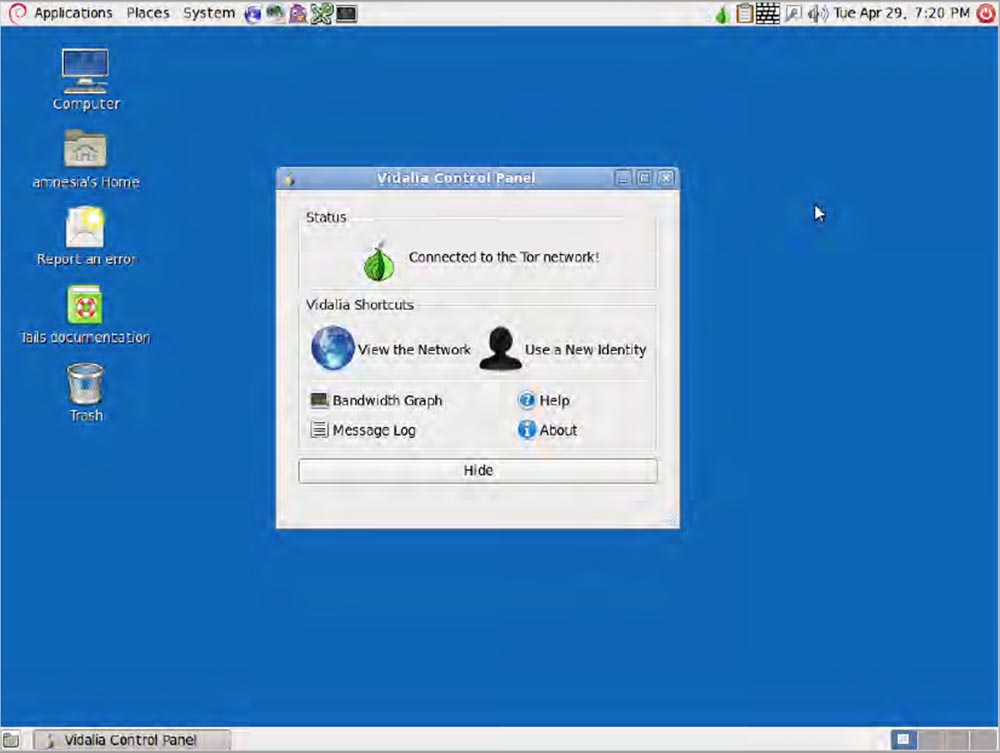
But you can easily put it into XP mode. If you are sitting at a table in a cafe and doing terrible hacking things, no one will pay attention to you if your laptop’s monitor has a regular Windows XP desktop.
So, when we connected to the Internet via Tor, we can do very interesting things:
Tor services are wonderful things that allow you to use Darknet, that is, sites that live exclusively on the Tor network and which cannot be reached without. You will not be able to track who owns such a site if you do not have its trust. Most Darknet sites have an onion address. The Tor documentation on the site describes how this all works.
Finding hidden services is the most difficult thing when you go into Tor.
This is the Hidden Wiki Hidden Wikipedia, most people like to use it, but I found extremely outdated information, and most of the links in it are damaged or do not work. But you can still find “gems” in it.
Torfind and TorSearch are Tor search engines.
Gram is another Tor search engine, made in the style of the Google search engine, it will help you find any thing on the Darknet markets, you just have to enter its name in the search bar.
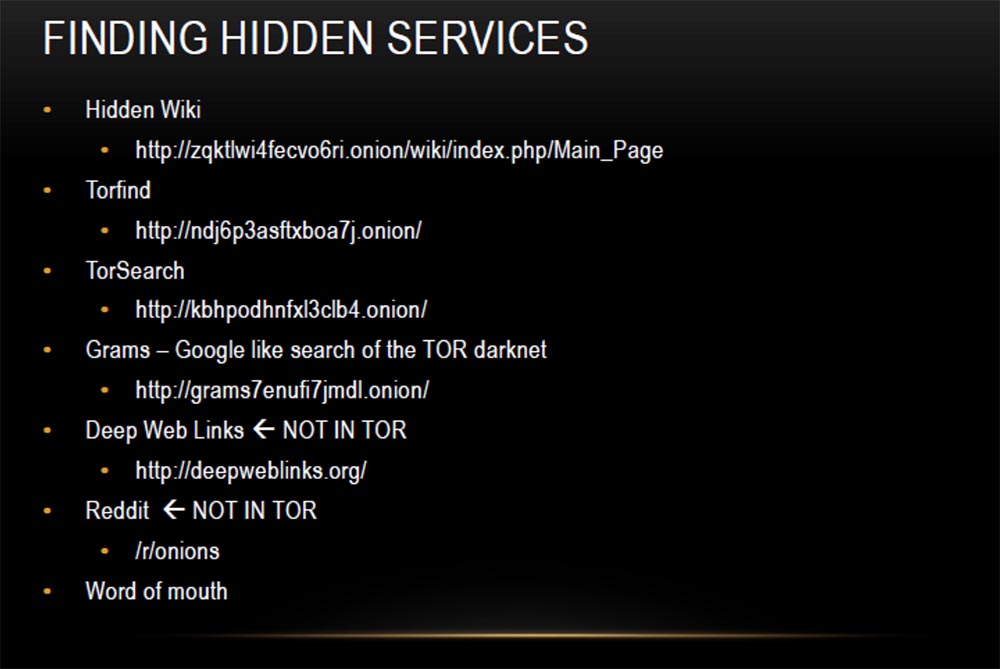
Deep Web Links and Reddit are not on the Thor network. They do not have onion addresses, but they have many links such as word of mouth. Many people spread the addresses of onion sites, so to speak, by word of mouth, sending them to their friends. It also has "hobby" sites, such as The Pirate Bay, where you can download various content. Therefore, it is bad if your Bittorrent does not support work with onion sites. Also note that if you are trying to download illegal torrents, it is better to do this through Tor, because downloading files from Pirate Bay does not mean that you remain anonymous.
My favorite “Killing Market” is a “nationwide finance” website. Now, regardless of whether it is legal or not, I doubt it. The essence of the market is that you pay bitcoins for someone to kill a person, and everyone around you starts investing bitcoins in it, and if someone can prove that he is the killer, they give him all the collected bitcoins . Pretty funny names came across this list, but, unfortunately, I can’t show it to you.
Another useful resource is the Rent-A-Hacker hacker exchange, here you can order hacking anything for an appropriate fee in bitcoins.
Next I list the addresses of the forums that are useful to you. TCF is a forum of Thor carding, it is devoted to issues of hacking bank cards. Access to the database costs $ 50 to prevent spammers from getting into it. By paying for the entry, you can buy credit card numbers, identification data and other hacker information, later we will talk about this in more detail.
Intellectual Exchange, or Intel Exchange, is visited by many people. This forum is dedicated to the exchange of various information that people share with each other, while remaining anonymous. Here, all sorts of "secret knowledge" are mainly trolled, the Deep web and the Miranda network are discussed, it's pretty fun. There is also a lot of useful information.
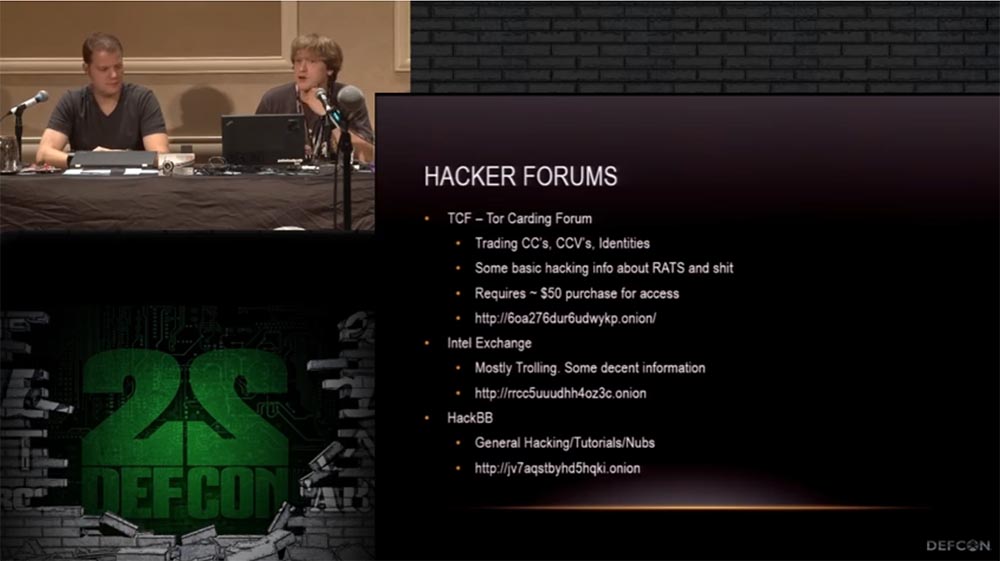
HackBB is a slightly different kind of forum, they make simple executive files that will allow you to gain hidden control over anything.
Network markets are places where people are interested in buying these kinds of things. You can check the Darknet markets, on the side of the page there is a regularly updated list with the status, regardless of whether they are considered trustworthy, and a quality assessment. This is very relevant information.
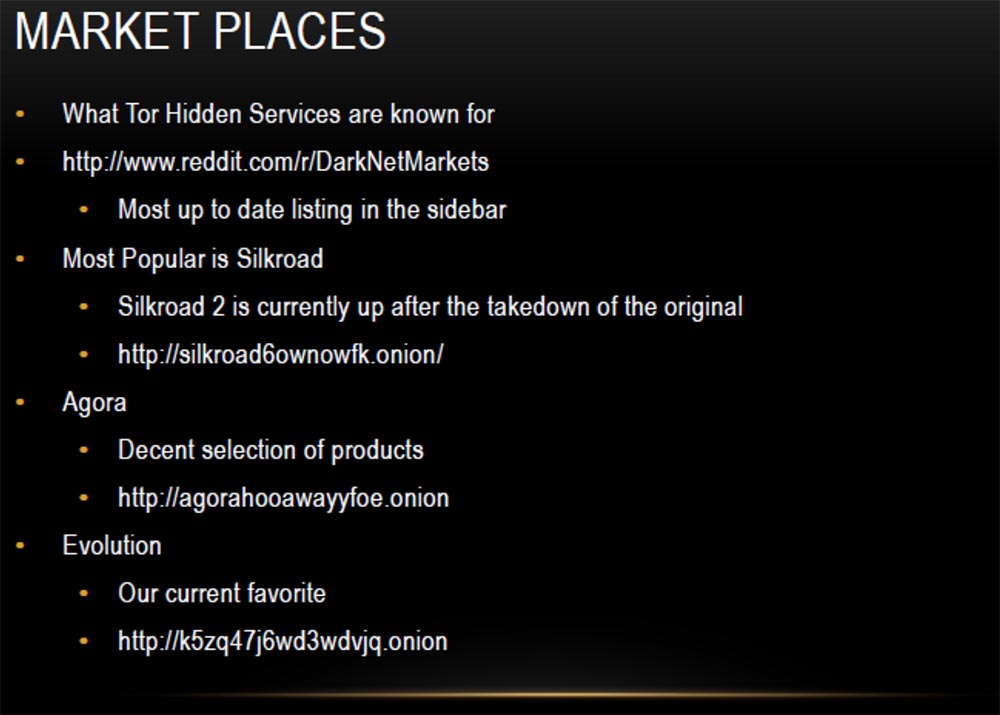
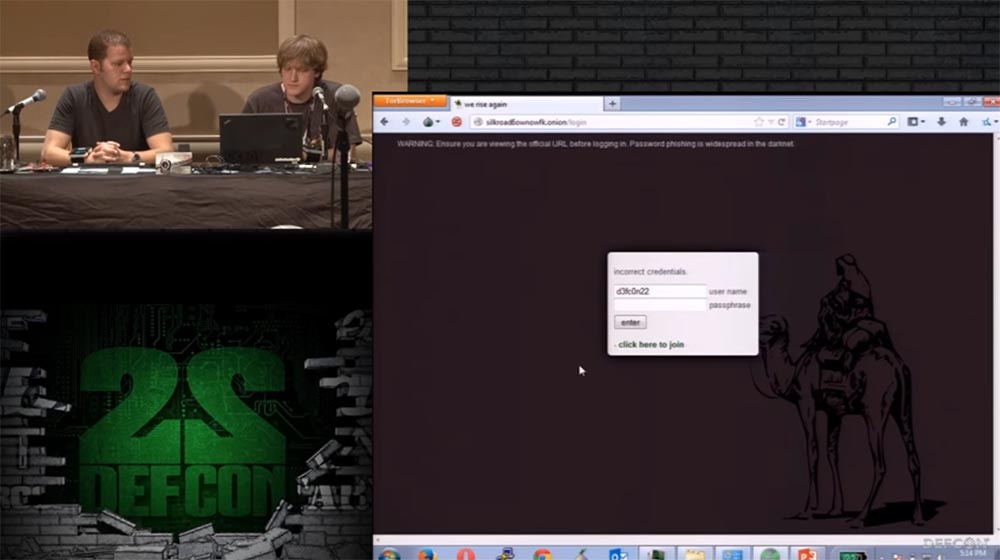
The most popular is the second version of Silkroad, or the Silk Road, followed by Agora with a decent selection of products, but I like Evolution most of all, and I'll tell you more about it later. Now I will give you a small demonstration on how to get to the Silkroad market. To do this, I copy the linkand paste it into the browser line of Thor. Done, now you need to enter your username and password.
Here is the main Silkroad page.
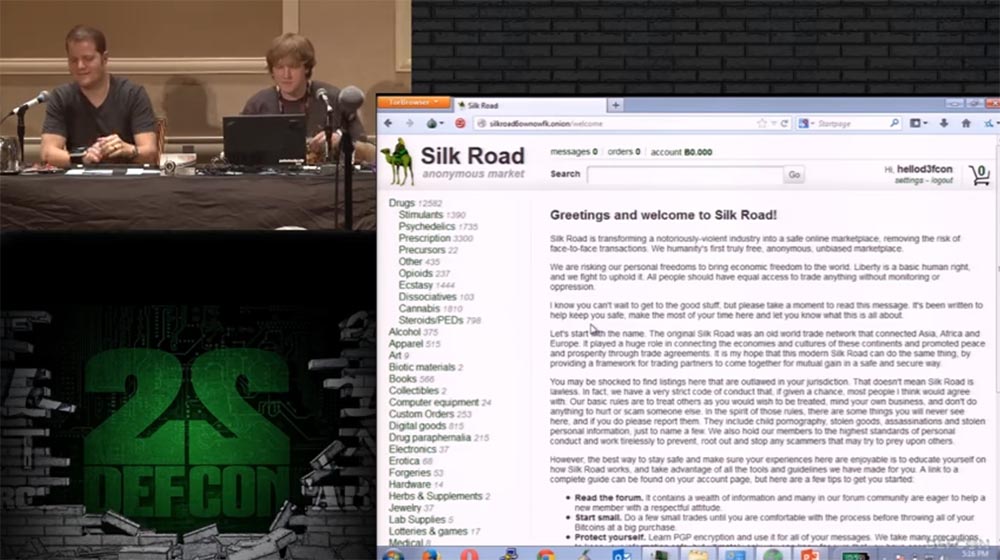
On the left you see a list of drugs that many people can find here, alcohol and more interesting things, for example, electronics. We’ll go to the electronics offers page, its range is constantly being updated, and we don’t know what we will find here today.
As you can see, they offer anonymous SIM cards, hacked Wi-Fi, MacBook Pro with a 13-inch screen, Virtual Honeyports book, quadcopter drone, external drives, Hackers Underground reference book and so on.
Grifter: as you can see, you can find many different things here, some of them are worth their money, some are not, and you have to “sift through” the entire range to find the thing you need. I will say this: if you do not want to lose your bitcoins, it is better not to waste them.
Metacortex: followed by TCF Carding Sites and Forums. As I said, for $ 50 you can buy credit card numbers, identification data, birth dates, social security numbers. The actual cost of these things varies depending on the inflation or deflation of bitcoin, but in any case, the use of such data will cost you $ 50. The SS site does not look too convenient for shopping, and I do not know how legal this is, but here you can ask for such things. Now I will try to go to the TCF website using this link.

Here you also need to enter a username and password. Let's see if we can buy the stolen information. There is a section of virtual cards and physical bank cards.
Grifter: we do not contribute to the distribution and use of stolen personal information, but only want to show how valuable your data is to other people. Keep this in mind when Metacortex will call their cost. From media reports, you know how urgent the problem of identity theft is and how they steal millions of credit cards from different stores, and this site eloquently testifies to the activities of such intermediaries.
Metacortex: I have never seen such low prices - a dollar for each card!
Grifter: You are worth $ 1!
Metacortex: here is the product page, there is a credit card number, card expiration date information, CVV code, card name, country, state, city, address and postal code. $ 6, and if you need a European card - $ 10. Everyone hates us!
Grifter: You ask, what is the chance that the seller of cards will not be torn to pieces? The chances are pretty small, because there is the same feedback system, for example, on Amazon, where people write that they bought goods from this seller and used it for a while, and recommend this seller as a verified one.
For us, these markets are not consumer but research interest. We go here to look at the dynamics of prices, what they sell, how they sell and how this system works. And when we start a conversation with the seller, he is completely open for dialogue, because he also works anonymously.
Metacortex: continue on, and again I can’t find the right video. There are still very interesting things for me, such as fake documents.
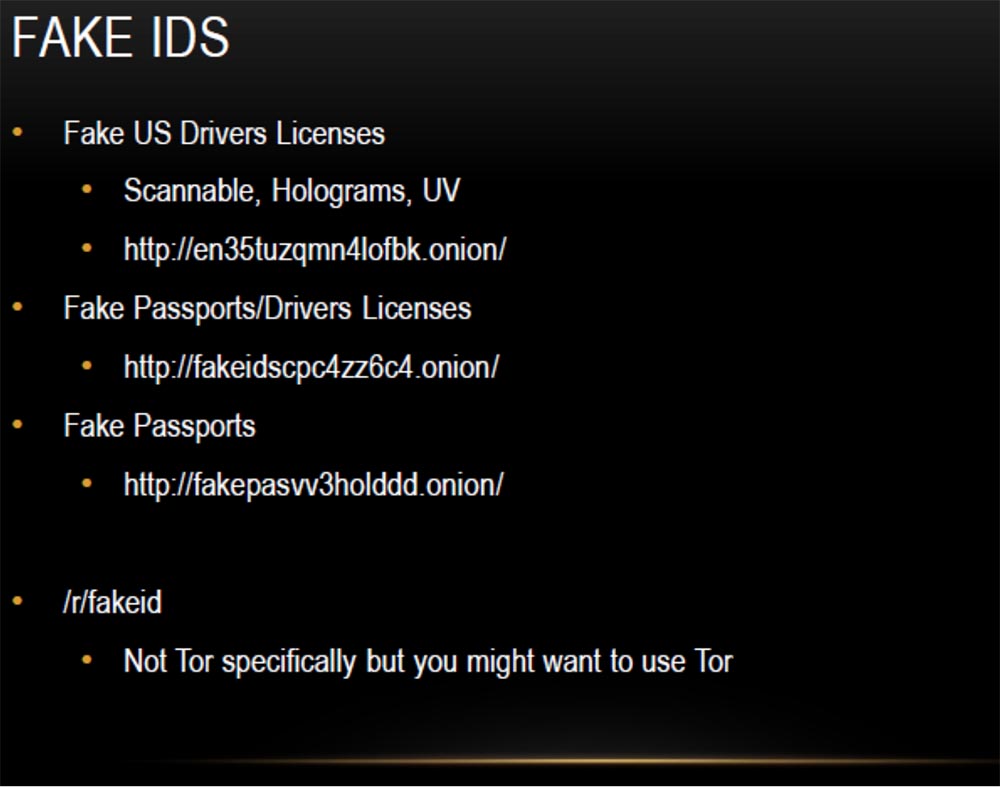
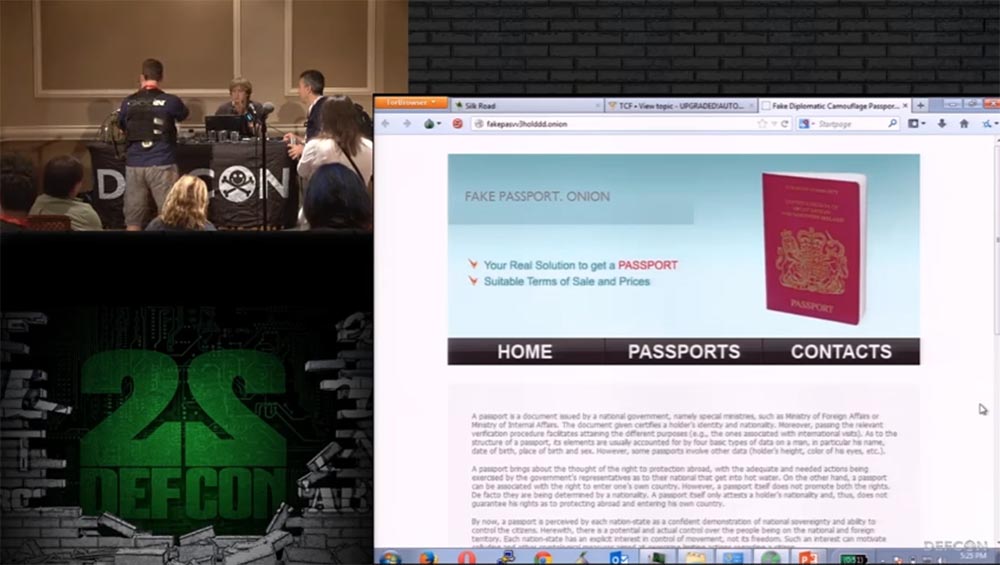
On the first site, you can buy fake US driver's licenses that can be safely scanned, they have a hologram and UV tags. On the second, fake passports and driver’s licenses are sold, on the third, fake passports, which are needed so that you can disappear to commit any unseemly act. I have heard that all the fake documents are completely legal, as they are made as high quality as possible, and you do not need to use Tor when purchasing them, but I would advise you to use Tor for this.
This is what the main page of the FakeID passport sales website looks like. You see that here you can buy passports of all these beautiful countries: Australia, Austria, Belgium, Canada, Finland, France, Germany, Japan, Switzerland, Great Britain and the USA.
Grifter: now we will see that a US passport is as expensive as a $ 1 credit card.
Metacortex: here is a scan of the passport and its description, it is written that it consists of 28 pages, has holographic marks and lamination, it looks absolutely legal, people can take their photo, and it will be placed in the passport with a UV mark. Theoretically, you can send them all the necessary information and get a ready-made passport.
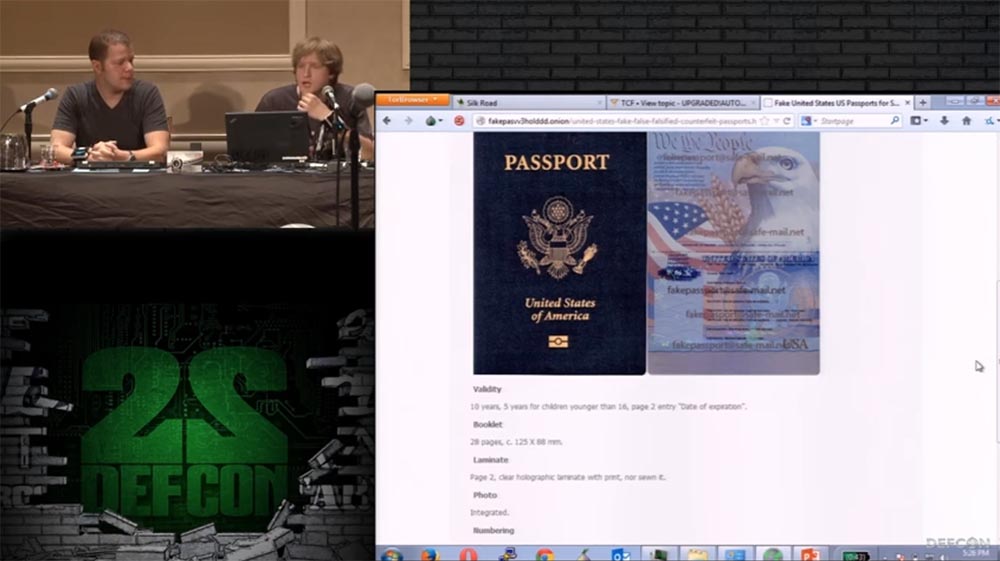
Its manufacture is worth $ 1000. For a Japanese passport they ask for $ 700. And now we went to the site where they sell a driver’s license. Several states are listed here; the cost of a driver’s license for each of these states is $ 200. Let's try to go to the last site.
Grifter: it says Free Shipping! Very good buy!
Metacortex: look at the prices, there is a very convenient table here. A US passport costs 700 euros. You can order a set of documents a passport and a driver’s license or identification card, and the purchase will cost less.
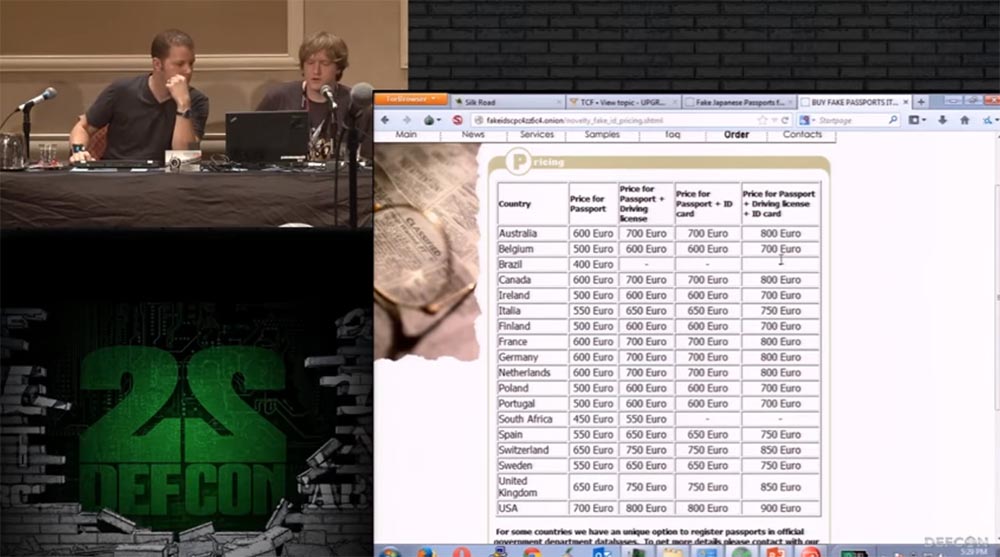
For an additional cost of 25-110 euros, they will put down a visa in your passport and put down the appropriate stamps.
Grifter: this is necessary in order to make your passport more like a real one, like you really traveled with it. Because, based on my experience, I note that if you fly with a blank passport, it is checked for much longer than a passport filled with seals.
Metacortex: so what can we do with all these passports? I will demonstrate to you this video with an excerpt from the movie “Bourne Identification”.
Grifter: yes, that’s what you need! That's why you might need a bunch of fake passports.
Metacortex: so we met with all the useful things that are offered here, and how can we get them?
Usually a purchase is made for bitcoins, most people on the Internet pay with this currency. They do not use Defcoin, because they are afraid of them, but this situation may change (joke). Usually, bitcoins are downloaded into the electronic wallet of your account on the market and you buy anything, your bitcoins are credited to a special Escrow conditional account, and when you receive your goods, Escrow sends your money to the seller. You select a delivery point, and you can find out more detailed information by reading the OPSEC rules.
I have more background information about bitcoin in the form of slides, then we will return to them, but for now we will continue in order. In fact, Bitcoin has a technology called “tumbler,” which ensures its anonymity. A toggle switch is a service offered to mix potentially identifiable bitcoins with others, to confuse anyone who wants to follow a chain of transactions back to their original sender. In fact, you throw your money into a common boiler, everyone throws their money there, Tumbler mixes them, and then returns their investments to people. Therefore, it is very difficult to track what really happens inside this boiler, where do bitcoins come from and where do they go. If you are engaged in very dubious matters (some people oppose the tumblers, but they do not bring much damage),
Now we will discuss some considerations about the Thor that violate its safety, because of which, in some cases, you can lose your anonymity. As I know, today the greatest danger to TOR is represented by correlation attacks on the stream cipher. If someone owns an input and output node of the Tor network, he can establish a connection between these nodes. We discussed correlation attacks a few days ago on Thor’s blogs, which talked about malicious sites that injected headers into data packets to track some of Darknet’s locations. It was possible to fix this a week or two ago by throwing such nodes from the Tor network.
Mention should also be made of some browser exploits capable of identifying you. These are browsers on the JavaScript engine, such as Firefox, XSS, and reverse ping produced on top of the Tor network, which allows you to identify you very quickly.
The following are some thoughts on bitcoins that will make you more anonymous. Keep in mind that bitcoins are not a completely anonymous currency, because blockchain technology is public. You can track any transaction that occurs within the Bitcoin network. Toggle switches help fight this. In addition, many people invest in bitcoins very large funds, which are scattered into millions of pieces, so it is simply unrealistic to track where exactly they came from.
Here's another slide about OPSEC.
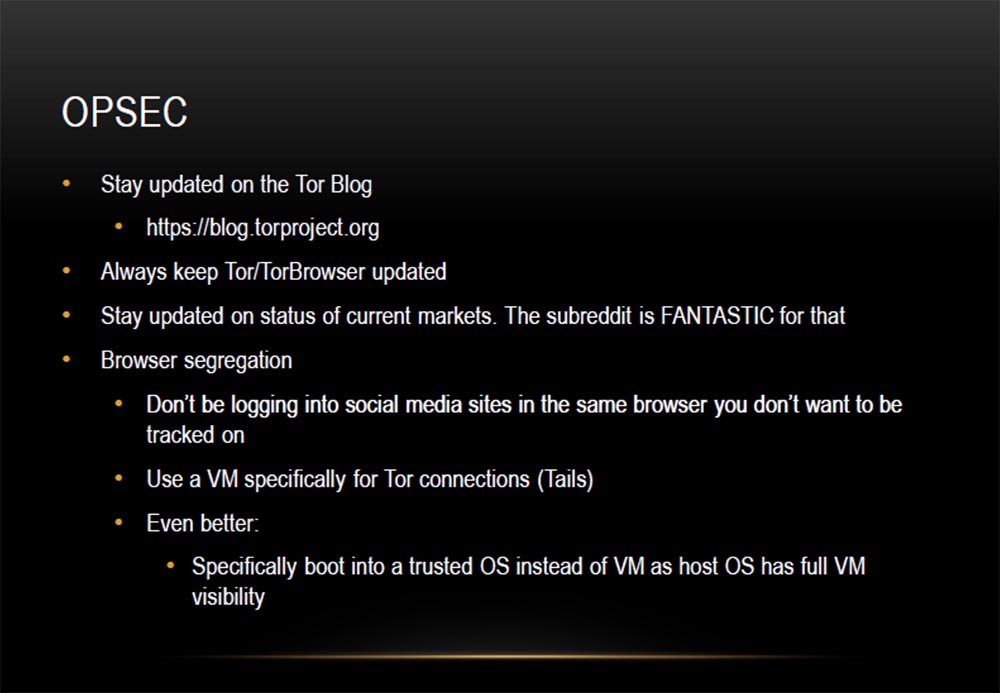
Grifter: let's talk about some things that allow you to verify your anonymity. First, stay up to date with all of Thor's events by visiting blogs. You need to be aware of vulnerabilities that are regularly identified, such as the recent Tails vulnerability. Keep track of which features have appeared as a result of the update, and which have disappeared. Secondly, regularly update the Tor browser. Also stay tuned for the status of existing markets.
Subreddit platforms are just a fantastic tool for this. They are not located on the Tor network, but on the “clean” Internet. Control your activity in the browser and try to anonymously do the things that require it. Use different browsers for different purposes, that is, do not register on Facebook through the same browser that you use to visit Darkmarket on the Tor network if you do not want to be tracked.
Use VM technology specifically to create Tails connections. I even have a separate laptop for Tails. I load it fast enough in Windows 8. As we have said, it is very convenient in a cafe when you are doing something dishonest. This laptop does not have a traditional hard drive; a Tails-drive is installed in it. You can also boot from a flash drive, such a flash drive with Tails is in my pocket, I used it at a DEFCON101 conference a year ago. This is a different level of security.
There is an even better option: load a trusted OS instead of a virtual machine, since the virtual machine is completely visible in the main OS.
Metacortex: yes, if your main operating system is compromised, it is better to use a virtual machine.
Grifter: Let's continue the discussion on how to make using the Tor network more secure. The following slide lists additional security measures.
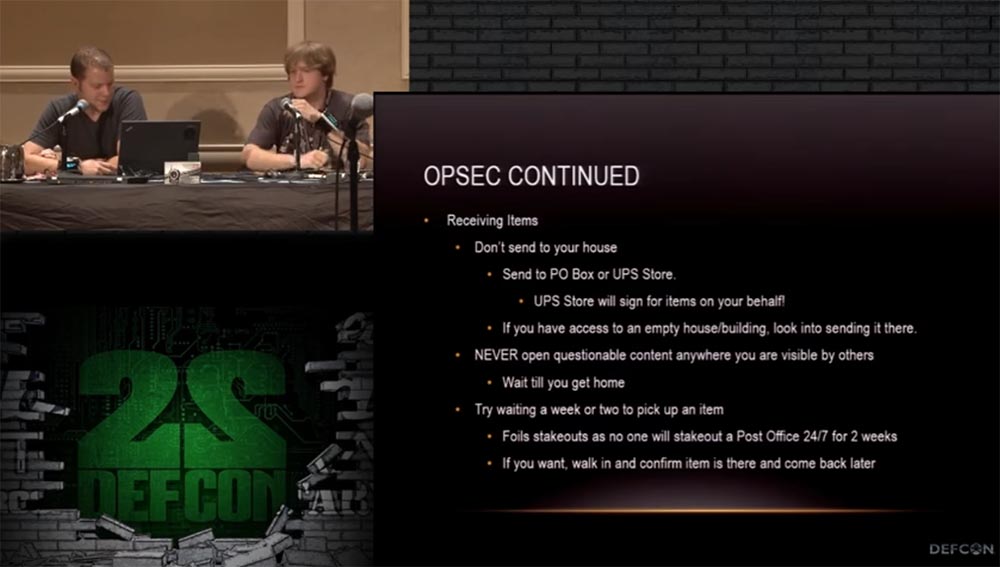
When receiving items from Darkmarket, do not send them to your home address. Send them to your PO Box at your post office or to a UPS shipping warehouse. Please note that at the UPS warehouse you will need to sign the receipt of the parcel! If you ordered fake documents to some mailbox, change it immediately after receiving the parcel. If you have access to some abandoned house with a mailbox, order delivery there, even if this house is located next to yours.
Never print the received package where other people can see its contents. You can wait a week or two before you come to get your package, so it is less likely that you will be caught on the spot when you receive it.
Moreover: try not to reuse your credentials, passwords and email, which you used to contact the black market merchant. For this, use mail registered to a fictitious person or from another location.
The next slide shows the thing that we purchased on the black market. This is Baby Monitor Baby Monitor. It works through the GSM mobile network, and you need to place a SIM card in it, to which the phone number is attached. Thus, if you want to hear what the child is doing in your room, you simply call this number and listen from any distance. This monitor has a very small size and the ability to call back. For example, when the noise in the room reaches a predetermined limit, which indicates an unusual activity of the child, the monitor will call you so that you can intervene in the situation. To activate the callback mode, you need to send an SMS with the code 1111, to cancel the mode - with the code 0000. This is a "baby monitor", as it is named on the order page. I will show you what the order form and order confirmation look like,
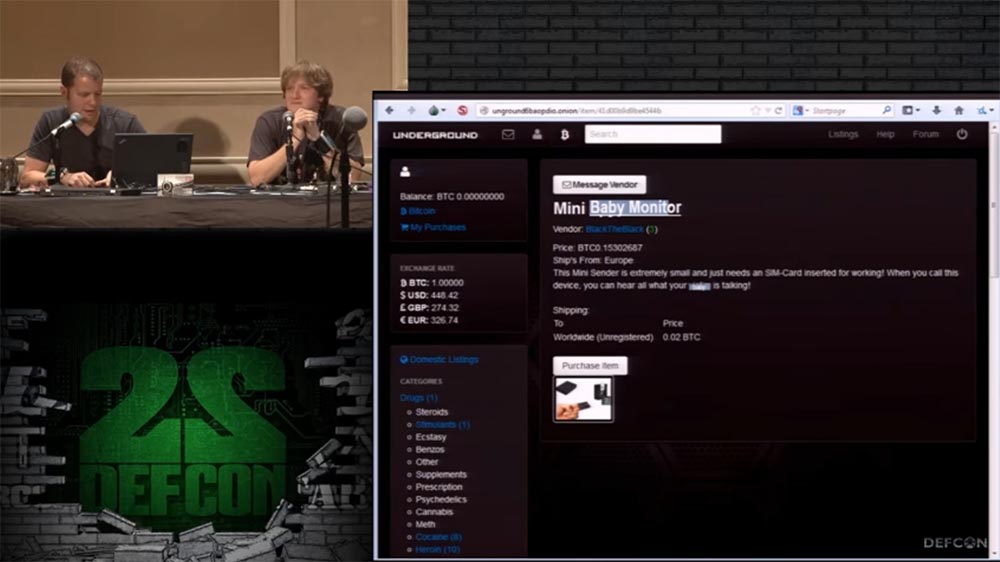
The following is a tracklist of delivery tracking via the USPS mail service.

And now thoughts that we want to share with you in parting.
Everything that we talked about sounds fun, but still immerses you in a certain “gray area”. You decide where to stay - in the twilight area or continue on into total darkness. Keep in mind that the place where you live or are, after your trip there already ceases to be a "gray area". So beware of this and remain anonymous. Like any thing, Darknet can be used for good or evil.
The good thing is that if you live under the oppression of the government, then Darknet is a fantastic tool for people to keep in touch with those who, just like you, do not like what is happening in the country. And you can get together and possibly change things for the better. If you are interested in what is happening in the world, and you want to talk with people who are in a difficult situation, Darknet will help you. Do not listen to media reports, but go in there and hear the truth directly from the lips of people.
So Darknet can be used with legal purposes, it is intended not only for all sorts of dark affairs. Both I and Metacortex believe that this is the future through which we will communicate, this should be the future mode of communication, because we no longer trust our own government and no longer think that we live in a free country. This is sad, but the way it is.
Therefore, start studying these materials and become pioneers who can help everyone else. Find out how to ensure anonymity on the network, how to encrypt your traffic and stay safe.
Thank you Internet!

If you’re in Salt Lake City, come see us because we like to treat hackers with dinner!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

We are both researchers who like to roam the dark alleys, for example, in Tokyo, I don’t even know where exactly this happened.
Metacortex: "To Shinjuku!"
Well, yes, it was in Shinjuk, I just did not pay attention to it. But this is exactly what we like to do, and we spent most of our trip on this activity. I think exploring the dark alleys is a good metaphor for describing the activities of hackers. We decided to take the train, and then chose a random number, it was 6, got off the train after 6 stops and just went wherever our eyes were. We did not know Japanese, did not know how to read or speak this language, but simply went to wander. It was cool, and we like that kind of activity.
So, I, Grifter, the DEFCON bandit who has been the speaker of our conferences many times, this is my sixth speech. I am the creator of the DEFCON 801 group since ancient times and co-founder of the 801 Hacker Space laboratory in Salt Lake City.
Metacortex: this is my first ever performance at DEFCON, so I'm a little worried. I am an assistant to this laboratory and the organizer of the 801st group, so if you get to Salt Lake City, go visit, there you will find free booze.
You can also meet us at the DEFCON, Black Hat, BSides-SLC, SaintCON and ToorCon conferences.
I'll start with a little caution. I know that goes without saying, but we are still talking about rather dubious things. But who can determine what is doubtful and what can be proved? We cannot promise that what we hear will not offend you, because we can talk about drugs, contract killings, hacking, weapons, pornography, and if this makes you a sad panda, you should cede your place in this room to someone else.

Now Metacortex has launched a clip on the screen. Who is the fan of this show, what is it called? "House of cards"? Yes exactly. For some reason we have no sound. This is the sad panda. Help us, sound men, all hope for you! Yeah, this is a bad cable ... this is USB for a sound card ... there is a problem in it ...
(Metacortex starts looking for another cable for a laptop, a guy comes on the scene trying to connect something, Grifter sings into the microphone: “Come on guys, help, and then we look here like gaddy assholes ... ”).

Nothing works, it was a bad idea!
But now the video finally comes with the sound:
"... 96% of the Internet, but most of it is unused in search engines, so we go here to find anything. Drugs, hired hackers.
- How did you get access to it?
- Pretty easy, I can show you if you want.
“Yes, of course, go on!”
“Okay, the first thing you need is Thor.” Some people prefer ITP, but I think Thor is better ... "
Yes, Thor is really much better!
And now we jumped onto the Darknet slide because Metacortex continues to torment its laptop and cannot find the desktop. Darknet is really a cool place , here you can hire hackers, wander around the black market and all that.

Finally Metacortex got to his desktop, and we continue the slide show in order.

We will talk about Thor, how to connect to it and how to use it, and what Onion onion sites are. We will talk about Bitcoin, how it works, how to use it and how to mine bitcoins.
Interesting information about this can be found on Darknet forums, hacker forums, and carding forums. Do not think that the Dark Network is an extremely vile place. Here are Internet platforms for people who want to avoid government censorship and freely discuss issues and things related to their country, without fear that they will pick you up in the middle of the night and put a black bag on their heads. I will show you a couple of tricks how to find them, while remaining unidentified, I will talk about Darknet search engines and markets where you can order physical things. They will be delivered not to your home, but to another place where these things can be taken from and no one will know who you are.
Metacortex: so, let's move on to the first topic and consider what Tor is, most of the DEFCON participants have probably heard about it.

This is an onion router that makes your traffic anonymous. This is one of the most serious anonymizers, representing a series of routers that ensure the anonymity of your Internet activity.
Pay attention to the warning below: if you start looking for this anonymizer on the network, the NSA can put you on the list of extremists, but honestly, why not?
Grifter: this does not happen so fast, say, if you use Thor and download something from there for 3 years, then yes, you will be on the list. And now we are sure to get to the first lines of this list, because we are talking about Tor here on DEFCON.
Metacortex: The next slide shows an excellent diagram showing the principle of action of Thor. The “+” sign marks the nodes of the Tor network (distributed servers), green arrows indicate encrypted data chains, red arrows indicate unencrypted ones.

Alice uses the Thor client, which selects a random path to the desired server.
The only thing I don’t like here is the red arrow of Bob, which says that he uses unencrypted traffic, or, in the case of HTTP, it will be encrypted or unencrypted traffic.
We believe that Thor works like this (shows the clip).

Grifter: we, too, are jumping over these little things and boxes!
Metacortex: and I also scream with joy when I manage to join the Torah!
So how do we connect to the Tor network? There are several different possibilities - you can use the Linux command line or the Mac command line or a binary installation application for this thing. I prefer Linux, you see it on the slides, this is the command / etc / tor / torrc, which you set up the connection configuration for. This starts the socks5 proxy server on your local host and allows you to start the Top client on the selected port, by default it is port 9050, after you connect to the Tor network.

To work on the network you need to download and install the Tor client, it is very easy to use. It will provide a connection and launch the portable version of Firefox, which will be running Tor. You can also use additional plugins.
We will quickly go over this issue because we will show a demo version, this is how your screen will look after installing and connecting to the Tor network.

Today, the gods of video presentations are angry at me, but I still try to demonstrate to you the connection of my laptop to the Tor network. Here, a couple of seconds and you're done!

Grifter: you said you screamed like a moron when you connected to Thor!
The metacortex emits a victorious cry: “we see a message that this browser is configured to use Tor”!
I click on the search bar and theoretically become an anonymous user of the network. After connecting to the browser, we see the icons of already installed plugins on the toolbar.

When you click on the bulb icon, a drop-down menu will appear with options where you can configure the Tor configuration. The icon in the form of the letter S with an exclamation mark means “no script”, the use of this plugin is very important, and the icon of the HTTPS Everywhere plugin in the form of a small circle on the right indicates that a secure HTTPS connection is used everywhere when browsing the pages. This means that even when passing between the Tor nodes in any direction, all our traffic will be encrypted.
Another way to ensure anonymity is to use the TAILS distribution. This is a Debian-based Linux Live distribution. It “wraps” all outgoing traffic in Tor and blocks non-anonymous traffic. This program does not leave any traces on the computer disk, so you can work completely anonymously. It works right out of the box and comes preloaded with apps like the HTTPS Everywhere plugin, plugin, OpenPGP, Pidgin OTR, Truecrypt and KeePassX, the most important of which is Truecrypt.
TAILS will transfer you to another interface - this is how it looks if you run it in Normal mode. This is the standard Debian desktop, nothing fun.

But you can easily put it into XP mode. If you are sitting at a table in a cafe and doing terrible hacking things, no one will pay attention to you if your laptop’s monitor has a regular Windows XP desktop.

So, when we connected to the Internet via Tor, we can do very interesting things:
- surf the internet anonymously;
- enter the selected resource through the tunnel laid by Thor;
- fight censorship;
- criticize the government and its official representatives;
- just remain anonymous;
- use the services of the Torah.
Tor services are wonderful things that allow you to use Darknet, that is, sites that live exclusively on the Tor network and which cannot be reached without. You will not be able to track who owns such a site if you do not have its trust. Most Darknet sites have an onion address. The Tor documentation on the site describes how this all works.
Finding hidden services is the most difficult thing when you go into Tor.
This is the Hidden Wiki Hidden Wikipedia, most people like to use it, but I found extremely outdated information, and most of the links in it are damaged or do not work. But you can still find “gems” in it.
Torfind and TorSearch are Tor search engines.
Gram is another Tor search engine, made in the style of the Google search engine, it will help you find any thing on the Darknet markets, you just have to enter its name in the search bar.

Deep Web Links and Reddit are not on the Thor network. They do not have onion addresses, but they have many links such as word of mouth. Many people spread the addresses of onion sites, so to speak, by word of mouth, sending them to their friends. It also has "hobby" sites, such as The Pirate Bay, where you can download various content. Therefore, it is bad if your Bittorrent does not support work with onion sites. Also note that if you are trying to download illegal torrents, it is better to do this through Tor, because downloading files from Pirate Bay does not mean that you remain anonymous.
My favorite “Killing Market” is a “nationwide finance” website. Now, regardless of whether it is legal or not, I doubt it. The essence of the market is that you pay bitcoins for someone to kill a person, and everyone around you starts investing bitcoins in it, and if someone can prove that he is the killer, they give him all the collected bitcoins . Pretty funny names came across this list, but, unfortunately, I can’t show it to you.
Another useful resource is the Rent-A-Hacker hacker exchange, here you can order hacking anything for an appropriate fee in bitcoins.
Next I list the addresses of the forums that are useful to you. TCF is a forum of Thor carding, it is devoted to issues of hacking bank cards. Access to the database costs $ 50 to prevent spammers from getting into it. By paying for the entry, you can buy credit card numbers, identification data and other hacker information, later we will talk about this in more detail.
Intellectual Exchange, or Intel Exchange, is visited by many people. This forum is dedicated to the exchange of various information that people share with each other, while remaining anonymous. Here, all sorts of "secret knowledge" are mainly trolled, the Deep web and the Miranda network are discussed, it's pretty fun. There is also a lot of useful information.

HackBB is a slightly different kind of forum, they make simple executive files that will allow you to gain hidden control over anything.
Network markets are places where people are interested in buying these kinds of things. You can check the Darknet markets, on the side of the page there is a regularly updated list with the status, regardless of whether they are considered trustworthy, and a quality assessment. This is very relevant information.

The most popular is the second version of Silkroad, or the Silk Road, followed by Agora with a decent selection of products, but I like Evolution most of all, and I'll tell you more about it later. Now I will give you a small demonstration on how to get to the Silkroad market. To do this, I copy the linkand paste it into the browser line of Thor. Done, now you need to enter your username and password.

Here is the main Silkroad page.

On the left you see a list of drugs that many people can find here, alcohol and more interesting things, for example, electronics. We’ll go to the electronics offers page, its range is constantly being updated, and we don’t know what we will find here today.
As you can see, they offer anonymous SIM cards, hacked Wi-Fi, MacBook Pro with a 13-inch screen, Virtual Honeyports book, quadcopter drone, external drives, Hackers Underground reference book and so on.
Grifter: as you can see, you can find many different things here, some of them are worth their money, some are not, and you have to “sift through” the entire range to find the thing you need. I will say this: if you do not want to lose your bitcoins, it is better not to waste them.
Metacortex: followed by TCF Carding Sites and Forums. As I said, for $ 50 you can buy credit card numbers, identification data, birth dates, social security numbers. The actual cost of these things varies depending on the inflation or deflation of bitcoin, but in any case, the use of such data will cost you $ 50. The SS site does not look too convenient for shopping, and I do not know how legal this is, but here you can ask for such things. Now I will try to go to the TCF website using this link.

Here you also need to enter a username and password. Let's see if we can buy the stolen information. There is a section of virtual cards and physical bank cards.
Grifter: we do not contribute to the distribution and use of stolen personal information, but only want to show how valuable your data is to other people. Keep this in mind when Metacortex will call their cost. From media reports, you know how urgent the problem of identity theft is and how they steal millions of credit cards from different stores, and this site eloquently testifies to the activities of such intermediaries.
Metacortex: I have never seen such low prices - a dollar for each card!
Grifter: You are worth $ 1!
Metacortex: here is the product page, there is a credit card number, card expiration date information, CVV code, card name, country, state, city, address and postal code. $ 6, and if you need a European card - $ 10. Everyone hates us!
Grifter: You ask, what is the chance that the seller of cards will not be torn to pieces? The chances are pretty small, because there is the same feedback system, for example, on Amazon, where people write that they bought goods from this seller and used it for a while, and recommend this seller as a verified one.
For us, these markets are not consumer but research interest. We go here to look at the dynamics of prices, what they sell, how they sell and how this system works. And when we start a conversation with the seller, he is completely open for dialogue, because he also works anonymously.
Metacortex: continue on, and again I can’t find the right video. There are still very interesting things for me, such as fake documents.

On the first site, you can buy fake US driver's licenses that can be safely scanned, they have a hologram and UV tags. On the second, fake passports and driver’s licenses are sold, on the third, fake passports, which are needed so that you can disappear to commit any unseemly act. I have heard that all the fake documents are completely legal, as they are made as high quality as possible, and you do not need to use Tor when purchasing them, but I would advise you to use Tor for this.
This is what the main page of the FakeID passport sales website looks like. You see that here you can buy passports of all these beautiful countries: Australia, Austria, Belgium, Canada, Finland, France, Germany, Japan, Switzerland, Great Britain and the USA.
Grifter: now we will see that a US passport is as expensive as a $ 1 credit card.

Metacortex: here is a scan of the passport and its description, it is written that it consists of 28 pages, has holographic marks and lamination, it looks absolutely legal, people can take their photo, and it will be placed in the passport with a UV mark. Theoretically, you can send them all the necessary information and get a ready-made passport.

Its manufacture is worth $ 1000. For a Japanese passport they ask for $ 700. And now we went to the site where they sell a driver’s license. Several states are listed here; the cost of a driver’s license for each of these states is $ 200. Let's try to go to the last site.
Grifter: it says Free Shipping! Very good buy!

Metacortex: look at the prices, there is a very convenient table here. A US passport costs 700 euros. You can order a set of documents a passport and a driver’s license or identification card, and the purchase will cost less.

For an additional cost of 25-110 euros, they will put down a visa in your passport and put down the appropriate stamps.
Grifter: this is necessary in order to make your passport more like a real one, like you really traveled with it. Because, based on my experience, I note that if you fly with a blank passport, it is checked for much longer than a passport filled with seals.
Metacortex: so what can we do with all these passports? I will demonstrate to you this video with an excerpt from the movie “Bourne Identification”.
Grifter: yes, that’s what you need! That's why you might need a bunch of fake passports.
Metacortex: so we met with all the useful things that are offered here, and how can we get them?
Usually a purchase is made for bitcoins, most people on the Internet pay with this currency. They do not use Defcoin, because they are afraid of them, but this situation may change (joke). Usually, bitcoins are downloaded into the electronic wallet of your account on the market and you buy anything, your bitcoins are credited to a special Escrow conditional account, and when you receive your goods, Escrow sends your money to the seller. You select a delivery point, and you can find out more detailed information by reading the OPSEC rules.
I have more background information about bitcoin in the form of slides, then we will return to them, but for now we will continue in order. In fact, Bitcoin has a technology called “tumbler,” which ensures its anonymity. A toggle switch is a service offered to mix potentially identifiable bitcoins with others, to confuse anyone who wants to follow a chain of transactions back to their original sender. In fact, you throw your money into a common boiler, everyone throws their money there, Tumbler mixes them, and then returns their investments to people. Therefore, it is very difficult to track what really happens inside this boiler, where do bitcoins come from and where do they go. If you are engaged in very dubious matters (some people oppose the tumblers, but they do not bring much damage),
Now we will discuss some considerations about the Thor that violate its safety, because of which, in some cases, you can lose your anonymity. As I know, today the greatest danger to TOR is represented by correlation attacks on the stream cipher. If someone owns an input and output node of the Tor network, he can establish a connection between these nodes. We discussed correlation attacks a few days ago on Thor’s blogs, which talked about malicious sites that injected headers into data packets to track some of Darknet’s locations. It was possible to fix this a week or two ago by throwing such nodes from the Tor network.
Mention should also be made of some browser exploits capable of identifying you. These are browsers on the JavaScript engine, such as Firefox, XSS, and reverse ping produced on top of the Tor network, which allows you to identify you very quickly.
The following are some thoughts on bitcoins that will make you more anonymous. Keep in mind that bitcoins are not a completely anonymous currency, because blockchain technology is public. You can track any transaction that occurs within the Bitcoin network. Toggle switches help fight this. In addition, many people invest in bitcoins very large funds, which are scattered into millions of pieces, so it is simply unrealistic to track where exactly they came from.
Here's another slide about OPSEC.

Grifter: let's talk about some things that allow you to verify your anonymity. First, stay up to date with all of Thor's events by visiting blogs. You need to be aware of vulnerabilities that are regularly identified, such as the recent Tails vulnerability. Keep track of which features have appeared as a result of the update, and which have disappeared. Secondly, regularly update the Tor browser. Also stay tuned for the status of existing markets.
Subreddit platforms are just a fantastic tool for this. They are not located on the Tor network, but on the “clean” Internet. Control your activity in the browser and try to anonymously do the things that require it. Use different browsers for different purposes, that is, do not register on Facebook through the same browser that you use to visit Darkmarket on the Tor network if you do not want to be tracked.
Use VM technology specifically to create Tails connections. I even have a separate laptop for Tails. I load it fast enough in Windows 8. As we have said, it is very convenient in a cafe when you are doing something dishonest. This laptop does not have a traditional hard drive; a Tails-drive is installed in it. You can also boot from a flash drive, such a flash drive with Tails is in my pocket, I used it at a DEFCON101 conference a year ago. This is a different level of security.
There is an even better option: load a trusted OS instead of a virtual machine, since the virtual machine is completely visible in the main OS.
Metacortex: yes, if your main operating system is compromised, it is better to use a virtual machine.
Grifter: Let's continue the discussion on how to make using the Tor network more secure. The following slide lists additional security measures.

When receiving items from Darkmarket, do not send them to your home address. Send them to your PO Box at your post office or to a UPS shipping warehouse. Please note that at the UPS warehouse you will need to sign the receipt of the parcel! If you ordered fake documents to some mailbox, change it immediately after receiving the parcel. If you have access to some abandoned house with a mailbox, order delivery there, even if this house is located next to yours.
Never print the received package where other people can see its contents. You can wait a week or two before you come to get your package, so it is less likely that you will be caught on the spot when you receive it.
Moreover: try not to reuse your credentials, passwords and email, which you used to contact the black market merchant. For this, use mail registered to a fictitious person or from another location.
The next slide shows the thing that we purchased on the black market. This is Baby Monitor Baby Monitor. It works through the GSM mobile network, and you need to place a SIM card in it, to which the phone number is attached. Thus, if you want to hear what the child is doing in your room, you simply call this number and listen from any distance. This monitor has a very small size and the ability to call back. For example, when the noise in the room reaches a predetermined limit, which indicates an unusual activity of the child, the monitor will call you so that you can intervene in the situation. To activate the callback mode, you need to send an SMS with the code 1111, to cancel the mode - with the code 0000. This is a "baby monitor", as it is named on the order page. I will show you what the order form and order confirmation look like,

The following is a tracklist of delivery tracking via the USPS mail service.

And now thoughts that we want to share with you in parting.
Everything that we talked about sounds fun, but still immerses you in a certain “gray area”. You decide where to stay - in the twilight area or continue on into total darkness. Keep in mind that the place where you live or are, after your trip there already ceases to be a "gray area". So beware of this and remain anonymous. Like any thing, Darknet can be used for good or evil.
The good thing is that if you live under the oppression of the government, then Darknet is a fantastic tool for people to keep in touch with those who, just like you, do not like what is happening in the country. And you can get together and possibly change things for the better. If you are interested in what is happening in the world, and you want to talk with people who are in a difficult situation, Darknet will help you. Do not listen to media reports, but go in there and hear the truth directly from the lips of people.
So Darknet can be used with legal purposes, it is intended not only for all sorts of dark affairs. Both I and Metacortex believe that this is the future through which we will communicate, this should be the future mode of communication, because we no longer trust our own government and no longer think that we live in a free country. This is sad, but the way it is.
Therefore, start studying these materials and become pioneers who can help everyone else. Find out how to ensure anonymity on the network, how to encrypt your traffic and stay safe.
Thank you Internet!

If you’re in Salt Lake City, come see us because we like to treat hackers with dinner!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
