DEFCON 22. Conference "Alone at home with an automatic protection system." Chris Littlebury
- Transfer
My name is Chris Littlebury, I work as a senior penetration security tester at Knowledge Consulting Group, located in the District of Columbia. I like to design all sorts of interesting things, giving ordinary devices unusual functions. For example, this XBox Live controller quickly detects a fire. I used it only once, combining it with an Arduino microprocessor. The second picture shows a device for replacing the fifth gear in the gearbox of my car, which improves mileage. I love to do things with my own hands.
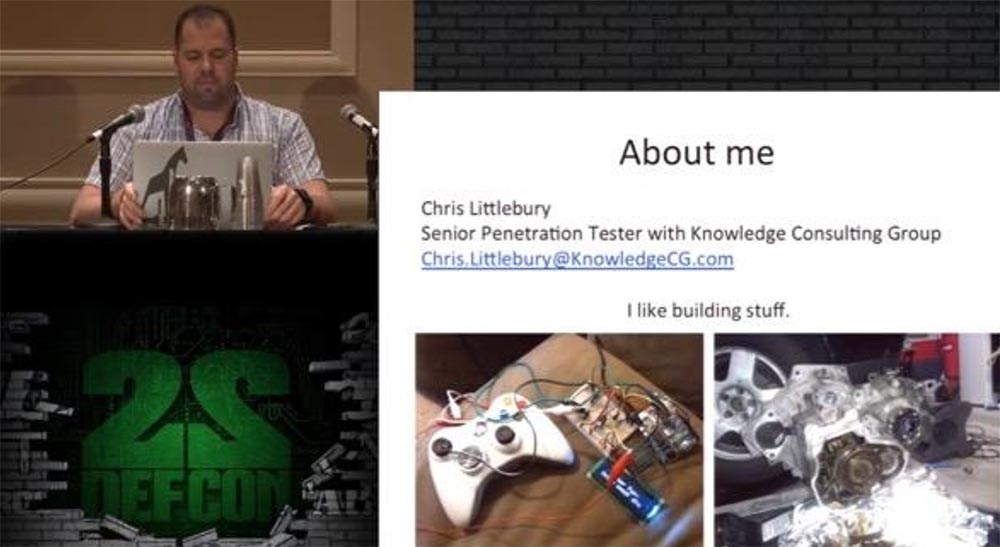
I create ideas, samples and codes that work for me and answer any questions related to their subsequent use.
I do not take money for laudatory comments about any products that I test. I do not promise to end the thefts, especially if you live in a house located in a criminal area. I do not advocate that you set traps in your homes that threaten thieves with death. This is prohibited by federal laws, so do not ask me to arrange a hidden pit with peaks sticking up at your place. If you set yourself something like a trap from the movie “Home Alone”, when the thief opens the front door and falls into the trap, you yourself will go to jail. I do not do anything that could injure people or damage property, and I do not use such devices to protect your car or apartment.
And I do not advise anyone to “penetrate” my home. Please do not try to do this! I do not want to find a stranger standing near my bed early in the morning, although I know that some of you are so crazy that you would try to do it.
So, let's move on to the story that I called Once Upon a Time in South Texas. It will be about the city of San Antonio, a famous tourist center, where many people with families come on excursions to such a beautiful place as Riverwalk. I lived in San Antonio for almost 10 years, so I understand what I'm saying. I propose to look at a map of the criminal situation in this city. She's just awful.
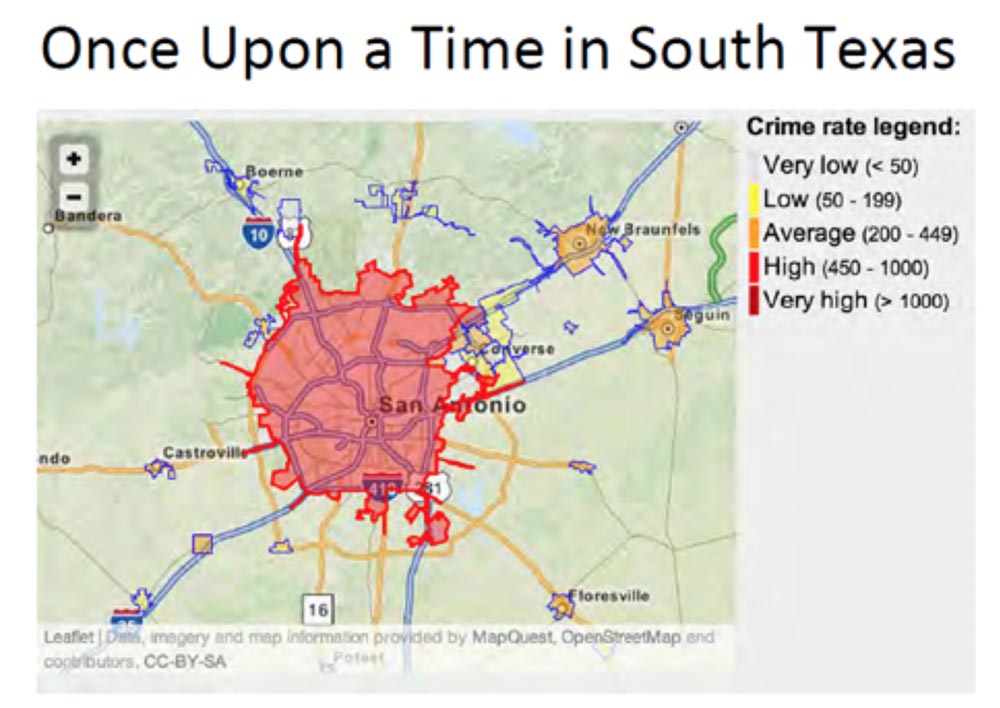
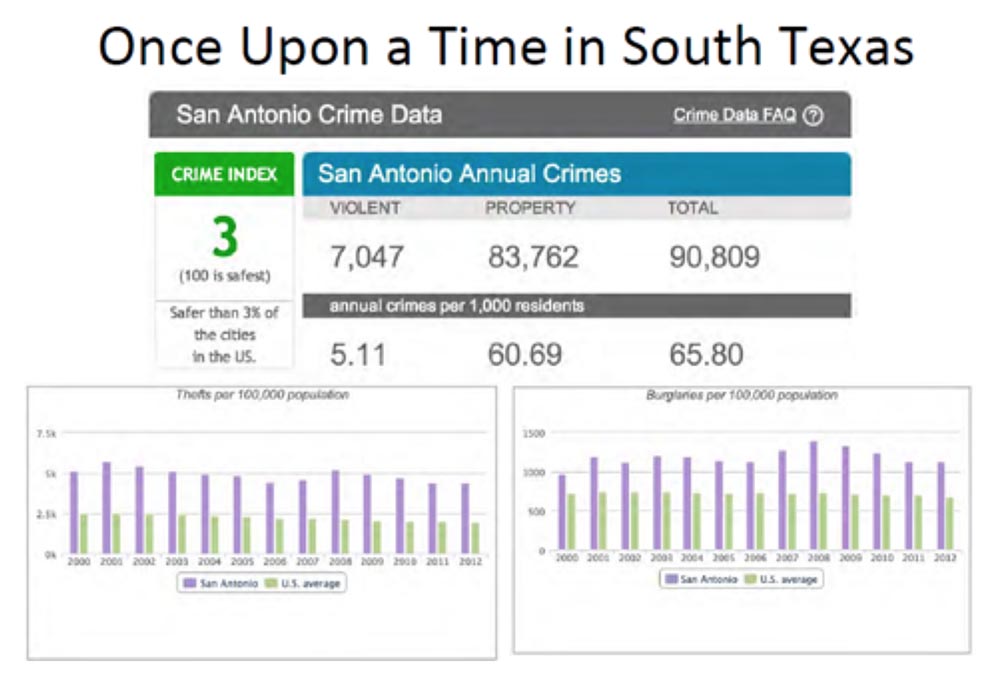
Among the crimes, in addition to street attacks, the number of cases of illegal entry into homes is also taken into account. This city got the 3rd place in the ranking of criminal cities in America (the safest city is at 100th place), since the number of crimes committed here is significantly higher than the average in the United States. More than 5 crimes against the person and about 60 crimes against property occur annually per thousand residents.
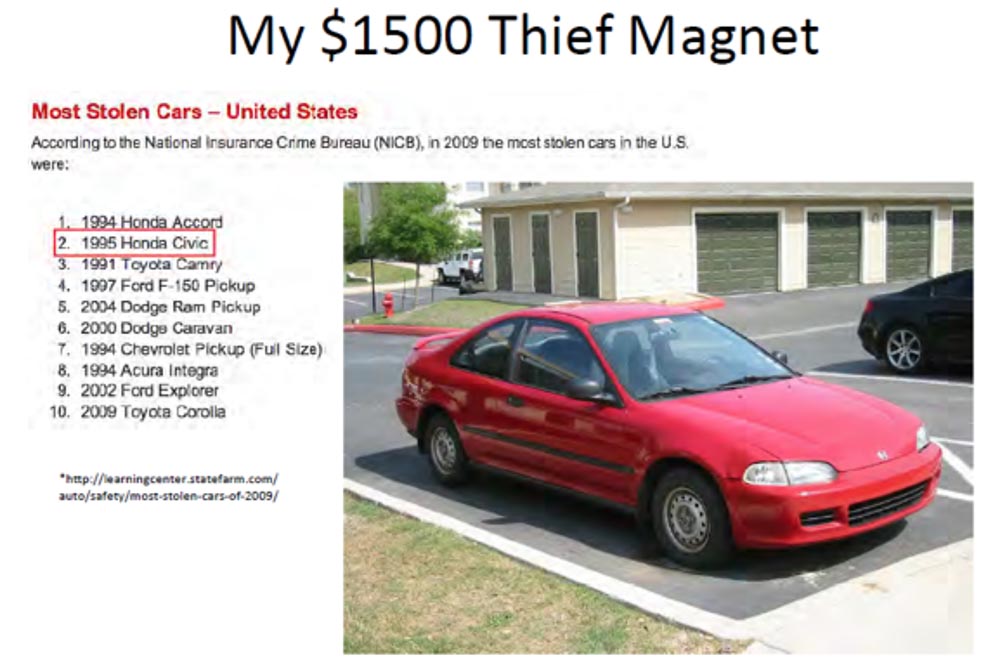
At that time, I had this small Honda Civic of 1995, one of the most stolen cars in the USA. In 2009, this car ranked 2nd in the hijacking rating. It was my $ 1,500 thief magnet.
Do any of you have or have ever had such a car? Raise your hands, from whom they stole it. I see, you can give up, you are real men. My car had air conditioning and low mileage when I bought it. One morning I saw that someone had opened the door and delved into my things, but did not steal the car. I thought that I had to somehow resist this and outsmart the thieves, since I knew how to assemble all kinds of things, solder and all that and could apply my knowledge in the IT field.

I came up with a 12-pin connector, which allowed the main fuel control relay to be disconnected and pulled out overnight, fixed the bottom of the dashboard so that it could not be removed, and installed a two-way alarm with a burglar alarm on the key fob. I specifically installed the cheapest version of the immobilizer without sound and light alarms, so as not to scare the thieves when they get into the car and want to steal it. I knew that even if they pull out or turn off all the relays that activate the siren, the turn signals, and so on, I still get a message on the pager. In fact, I got a car-trap for hijackers, but I needed it to travel to work, so I used it anyway.
Once, early in the morning after 3 months, the alarm went off, I rushed out into the street and saw in my car two decently dressed strangers digging around in the car’s cabin with a steering column. One managed to escape, and the second tried to enter into dialogue with me, but I laid him on the ground and handed over to the police. It was a success, after which I got out of this shitty area, especially since my neighbors had a bunch of similar cases, and even worse.
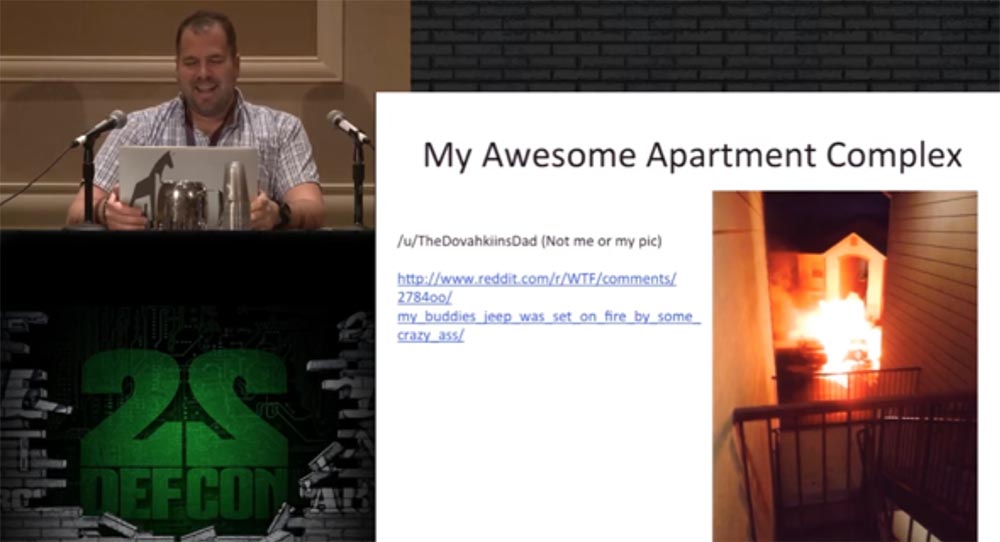
A year later, I saw a photograph that depicted my apartment complex and a neighbor’s burning jeep, and was delighted to get out of there on time.
I moved to a more decent area. This photo, by the way, shows the snow that fell in San Antonio only three times during its existence. This snow was like fine dust, but people were about to ride the sled, you understand. I rented an apartment on the third floor for security reasons, because there are sliding doors everywhere, even on balconies, and a thief can easily enter the apartment on the lower floors by opening a door or window lock. One of the police advice was to use the light to simulate the presence of the owners in the house when no one was there. That is, to set all kinds of timers, which would include light bulbs, a TV, and so on, so that a person who looks into the window thinks that the owners of the house. They also advised to inspect all windows and doors before going to bed, and lock them, even if you leave the house for a short time.

It was also advised to regularly remove mail from your mailbox, and when you were away, ask the post office not to deliver mail to you or to get it from your neighbors. I think that these rules were taken as a basis when shooting the movie "Home Alone".
I often worked at night, worked during the day, that is, my apartment looked inhabited all the time. I also installed at home the cheapest version of the X10 automatic device, the so-called "silly chip." This really bad device, created in the late 70s, it sends data to your home electrical network.
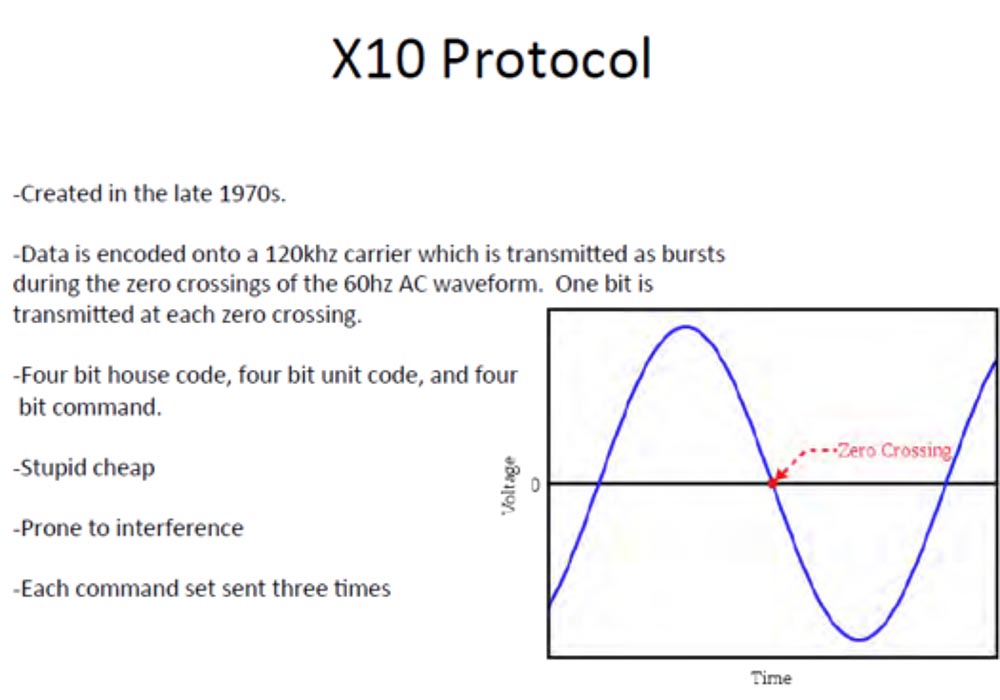
It forms a carrier frequency of 120 KHz in the form of a sinusoid from branches of 60 KHz crossing the axis of zero voltage. Each time a wave crosses the zero horizontal, it transmits one bit. The home code, module control code and command consist of 4 bits of information. The waves were subject to interference, and each command had to be entered three times. That is, it was completely unsuitable for comfortable use. But if you live in a small apartment or an old residential complex, you do not need to use a more complex device, this also works. Before use, it had to be programmed.

It automatically turned on and off the light by the days of the week and by the hours, had a security timer, allowed to create macros and could be controlled remotely. The security timer allowed randomly turning the light on and off on different days of the week at different times of the day.
Then I moved from the apartment to my house and immediately decided to do something with the outdoor lighting. I wanted to automatically change the lighting, turn on and off different lights, use photo sensors based on the same X10 device, that is, nothing special. I don’t know how this helped, but for all the time that I lived in this house, no one broke into me even once, although my neighbors were robbed.
Finally, after 10 years, I moved back to Colorado and began to equip my house, taking into account all the experience gained. I was not going to turn my house into a trap, just to make the housing comfortable, and made up such a “wish list”:
I didn’t have to install cameras everywhere to watch children with a smartphone, or to automatically open the front doors and garage doors as soon as my car approached the house, because I was afraid of all these terrible things. I just wanted to make my home protect itself.
I needed a person who wants to enter the house to be detained at the doorstep. You know, many have a powerful alarm system, or there is a billboard on the front lawn that says: "Do not get close to my house, otherwise the alarm will work" and so on - so if they intend to ensure their safety in this way, let do as they want. Because there were times when such an alarm was triggered by your friends in the living room or the police detained a completely stranger in front of your house due to incorrect operation of the security system.
I didn’t need this, I wanted my alarm to really work on a real threat, but it was hidden, without any sirens and anything else. That is, when an outsider got into the house, some unusual events would start to take place there, attracting my attention.
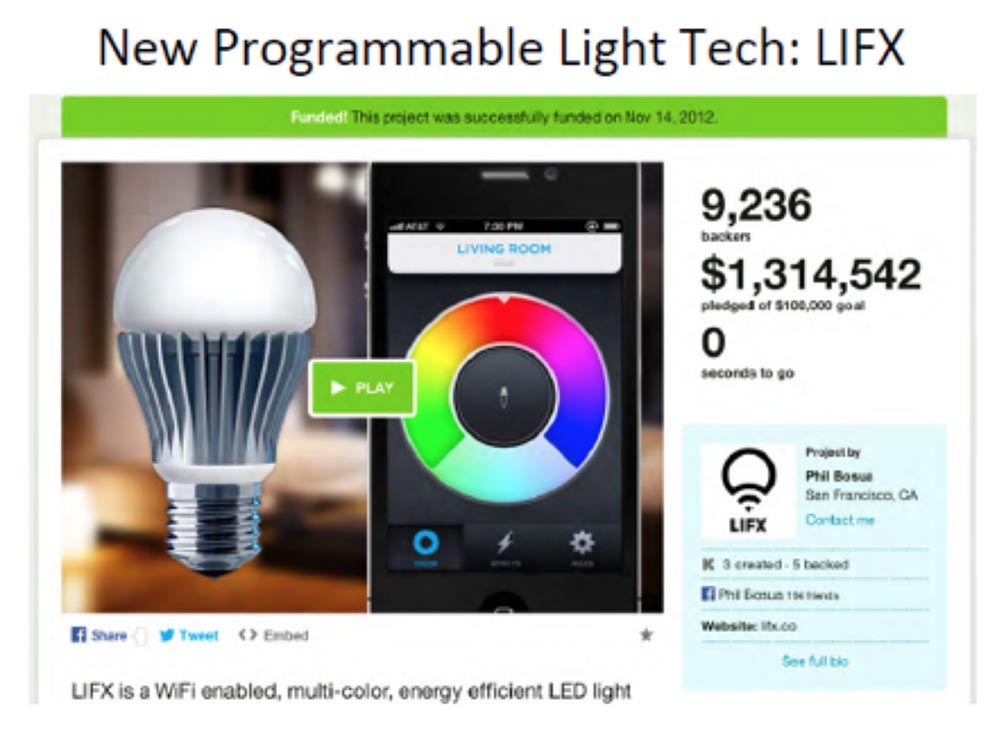
The first thing I acquired was WiFi LIFX. This device is for programmable control of a color LED light bulb wirelessly. It was the result of the implementation of the project, which launched on the Kickstarter portal in 2012. It was a cool light bulb with a WIFi module with a brightness of 1000 Lumens, which shone as abnormal and at the same time consumed only 17 watts. She had a fantastic color palette giving lighting of any color. The slide shows the blue lighting of my living room, which is provided by only two of these bulbs mounted on the ceiling. This is really cool. So, when the alarm goes off, your whole house starts flashing red. All chandeliers, staircase lighting, table lamps - everything starts to shine flashing red, as if aliens had arrived. If you still run the car,
Imagine how this will affect the robber.

There is a Python API for encoding this light bulb, so its operation can be programmed in the mode you need. The disadvantages of these lamps are the large size and weight, so you can not use them like ordinary lamps for wall lighting, in addition, they heat up well, so they can not be covered with an ordinary lampshade or shade.
An alternative to these bulbs is Philips Hue. They are much smaller, consume less energy - only 8.5 watts at full brightness, a little cheaper. Three of these bulbs correspond to the brightness of a conventional 360 W lamp. Their disadvantages are a poor color palette and a small brightness. But if you want to use such bulbs to illuminate the dining room or hall, and at the same time be able to arrange a “red” Terrible Security light alarm, then they will become a fantastically good choice.
The following slides show the illumination of my rooms on July 4, however, the camera was not able to transmit really purple and blue light, which creates a combination of 3 Philips Hue lamps and 4 LIFX LED lamps.


The next device I used in my house is called WeMo. It is manufactured by Belkin. This device has the following features:
The following slide shows the Home Defense Server that I developed. The main requirements during its development were:

I needed the system to be able to call me, transmitting video or text messages, so that I did not have to call the police and say: “Hey, my name is Chris, I created Ruba Goldberg’s“ abstruse car ”in my house, and I swear to you, that someone entered my house, could you check it? ” and hear back: "Sir, this is 911, don’t call here anymore!"
The next slide shows my WiFi barbecue smokehouse, which reported the temperature of smoke and meat, the time left until fully cooked, the number of servings and so on, created on the basis of the Raspberry Pi, so I was well versed in its amazing capabilities.
The processor was connected to the sensors via the ten-bit ADC interface and the Rails server was used for its operation, because I had some experience with Ruby on Rails, it is an open-source web framework.

The following site shows the Home Defense server. It is connected with existing home security systems in the form of such a local network, deployed on the basis of the Raspberry Pi. Independent PIR / X-band components of the sensor radar, that is, relays, transistors, motion sensors, are added to the system. The server allows you to activate the alarm system using hardware or wireless panic buttons. The hardware circuits were programmed for the contact type of operation, that is, as normally closed or normally open circuits, and recorded the movement or opening of the door.

To solve all these problems, I used open source software, a list of which is given on the next slide. For example, Magicmonkey processed LIFX protocols of bulbs, combining them into a synchronized system with flexible settings for the flash frequency of certain groups. The Sharph programming language is a LIFX version of Python, based on Magicmonkey libraries and protocols, and allows you to create stunning APIs that provide communication between WLAN and ZigBee network protocols that control LIFX lamps based on the 802.15 wireless protocol at 915 MHz.

The official LIFX Api application, written in Rubi, supported the simultaneous management of multiple light bulbs. I also used something unpronounceable - iancmcc's ouimeaux - an extended version of Python IPI for WeMo devices with an application written on top of the official API. The system had code and linear support. After that, I connected to the network elements of the external interface and services that ensure their functioning.
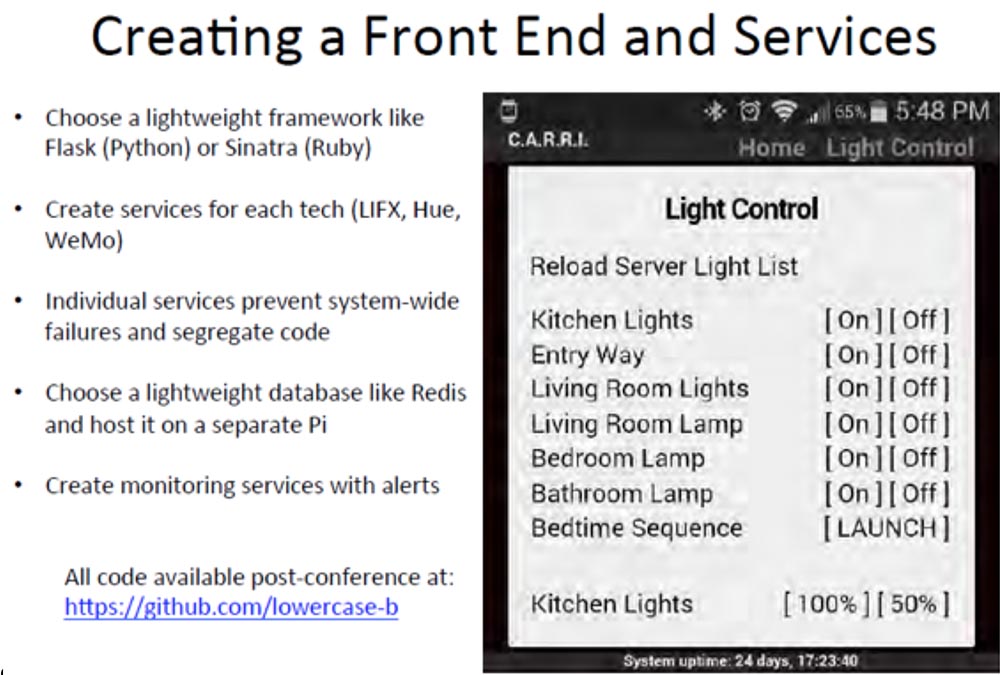
On the right side of the slide you can see how the “Light Control System” application looks on the smartphone screen. To write this application, I used the lightweight frameworks Flask (in Python) or Sinatra (in Ruby). I created services for each type of equipment - LIFX, Hue, WeMo. Individual services prevented system-wide crashes by running applications on separate ports, that is, if a service failed, the system continued to function. To ensure the performance of such a bulky structure, I used a lightweight Redis-like database, placed it on separate Pi, which were in different rooms, and created tracking services with alarm. I also provided each Raspberry Pi platform with its own hard drive so that there are no delays,
I note that I am not a programmer or an expert in the field of writing codes, but just a tester, so my codes do not look elegant and cumbersome enough, but still work pretty well. I had to test the security system, for which I used the Bluetooth channel. For example, I entered a room with my smartphone, and the system had to see it and respond to my stay there properly, starting certain processes. Moreover, it was quite difficult, because it was necessary to check the signal intensity of my smartphone so that the system “saw” that I was approaching or moving away from the receiver, that is, it was tracking my movement around the house. I give a link to the video of testing the range of Bluetooth CARRI, where it is shown how the light on the second floor goes out when I leave the room and go down the stairs and how it lights up in another room when I enter there. To do this, I used a special device called RSSI - an indicator of the strength of the received signal.
I wrote a script based on Linux rfcomm / hcitool / l2ping, which pinged the MAC address of my phone, checked the constant transmission of packets of RSSI arrays, that is, the intensity of the Bluetooth signal, and gave the command to execute the given function. If the Bluetooth signal was too powerful, the application blocked the wireless interface of the smartphone, so I tried to use only the 802.11 protocol, i.e. WiFi.
The system was tied specifically to my smartphone, and if a neighbor came into the house with her smartphone, she would not have responded to it, because it has a different MAC address.
Thus, I created a system that monitored the owner’s movements around the house by monitoring the approach or removal of a mobile device. “Device proximity monitoring” had the following properties:

I tied a scheduler called SmartCron to my system, which planned changes in lighting system modes depending on the time of sunrise and sunset according to the data obtained from the free Weather Underground application. This is an awesome API with fantastic lighting intensity adjustments depending on weather conditions, for example, it turned on the light if it was cloudy outside the window.
Now consider a system of protection against wireless attacks. It is based on the principle of sports radio direction finding “Fox Hunting”, when using a receiver, a map and a compass they find transmitters hidden on the ground.
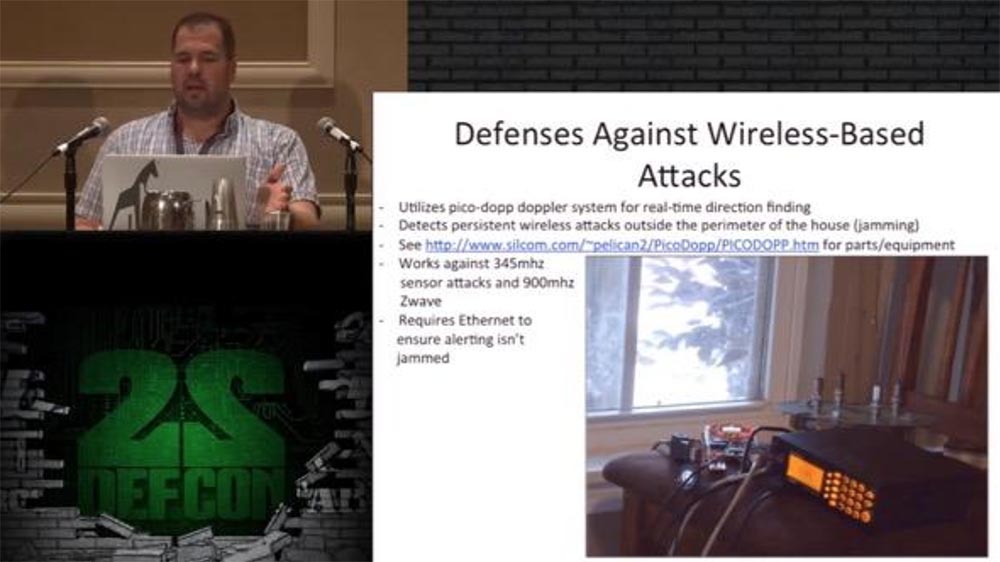
The system detects Z-Wave attacks on access control devices or attempts to drown out the wireless data transmission of sensors and sensors operating at a frequency of 345 MHz to disable the security system. The receivers of the protection system are antennas that detect the beginning of the transmission of signals and the place from where it is produced, that is, they detect the signal of the transmitter of the attacker. They are configured to respond to sensory attacks performed at 345 MHz and Z-wave at 900 MHz, and use the Ehternet network to function in jamming conditions of wireless signals. This technology is based on the Doppler effect, which allows you to detect moving objects due to a change in the frequency and wavelength of the transmitter, which moves relative to the stationary receiver.
Thus, if someone tries to pick up electronic keys to my house, being outside the perimeter indicated by the system, the receiver detects its coordinates. To provide this function, I used the Agrello DF text message format, where the quality of signal detection has a fixed value of 7 picodopts.

The antennas are connected to the serial port of the RS232 interface, then to the USB adapter and the Raspberry Pi processor, where their signals are processed using the Python application. Here, the obtained coordinates are compared with the coordinates of the protected perimeter, and even if the key matches, but is obtained from a source outside this perimeter, the system does not respond to it.
I also provided an active element of protection in case the thief does get into the house. If he thinks that he was not noticed, he will try to steal something and escape. Therefore, I needed a tool showing that the attacker was detected. It was supposed to be electronically activated and produce a lot of noise, but not cause the thief any physical damage. Firstly, the lights in the house began to flash red. Secondly, I connected 12 V solenoids to heavy metal objects that created a knocking effect. That is, when the thief was in the house, the whole house began to flash red, and from the side of the stairs there was a knock, as if someone was going down the stairs.

The last thing I did and from which I categorically discourage you is the signal fireworks from firecrackers. Do not try to do this in your house, because burn it to the ground. Keep in mind that making artisanal fireworks is a federal crime. Remember that I warned you about this!
So, I used a 12V circuit to create a spark that set firecrackers on fire. It was triggered automatically by a security signal, while the firecrackers were not set on fire all at once, but in turn at random and made sounds resembling shooting, similar to the one that the kid had made in the movie "Home Alone".
I note that I did not use Z-wave devices in my home system, because they are expensive and are not an open source. But I plan to test them in the future, and also want to integrate the SDR scanning devices in the 345 MHz range for all wireless sensors and to perform an engineering analysis of the dual-band 2 GIG transmitter operating at 345/900 MHz. I did not have time to do this because I got on a plane and flew here, but I will definitely continue my work. If you have questions about the use of devices to protect your home, please contact me by e-mail, because, unfortunately, I have completely exhausted the time limit allotted for my presentation.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

I create ideas, samples and codes that work for me and answer any questions related to their subsequent use.
I do not take money for laudatory comments about any products that I test. I do not promise to end the thefts, especially if you live in a house located in a criminal area. I do not advocate that you set traps in your homes that threaten thieves with death. This is prohibited by federal laws, so do not ask me to arrange a hidden pit with peaks sticking up at your place. If you set yourself something like a trap from the movie “Home Alone”, when the thief opens the front door and falls into the trap, you yourself will go to jail. I do not do anything that could injure people or damage property, and I do not use such devices to protect your car or apartment.
And I do not advise anyone to “penetrate” my home. Please do not try to do this! I do not want to find a stranger standing near my bed early in the morning, although I know that some of you are so crazy that you would try to do it.
So, let's move on to the story that I called Once Upon a Time in South Texas. It will be about the city of San Antonio, a famous tourist center, where many people with families come on excursions to such a beautiful place as Riverwalk. I lived in San Antonio for almost 10 years, so I understand what I'm saying. I propose to look at a map of the criminal situation in this city. She's just awful.

Among the crimes, in addition to street attacks, the number of cases of illegal entry into homes is also taken into account. This city got the 3rd place in the ranking of criminal cities in America (the safest city is at 100th place), since the number of crimes committed here is significantly higher than the average in the United States. More than 5 crimes against the person and about 60 crimes against property occur annually per thousand residents.

At that time, I had this small Honda Civic of 1995, one of the most stolen cars in the USA. In 2009, this car ranked 2nd in the hijacking rating. It was my $ 1,500 thief magnet.

Do any of you have or have ever had such a car? Raise your hands, from whom they stole it. I see, you can give up, you are real men. My car had air conditioning and low mileage when I bought it. One morning I saw that someone had opened the door and delved into my things, but did not steal the car. I thought that I had to somehow resist this and outsmart the thieves, since I knew how to assemble all kinds of things, solder and all that and could apply my knowledge in the IT field.

I came up with a 12-pin connector, which allowed the main fuel control relay to be disconnected and pulled out overnight, fixed the bottom of the dashboard so that it could not be removed, and installed a two-way alarm with a burglar alarm on the key fob. I specifically installed the cheapest version of the immobilizer without sound and light alarms, so as not to scare the thieves when they get into the car and want to steal it. I knew that even if they pull out or turn off all the relays that activate the siren, the turn signals, and so on, I still get a message on the pager. In fact, I got a car-trap for hijackers, but I needed it to travel to work, so I used it anyway.
Once, early in the morning after 3 months, the alarm went off, I rushed out into the street and saw in my car two decently dressed strangers digging around in the car’s cabin with a steering column. One managed to escape, and the second tried to enter into dialogue with me, but I laid him on the ground and handed over to the police. It was a success, after which I got out of this shitty area, especially since my neighbors had a bunch of similar cases, and even worse.
A year later, I saw a photograph that depicted my apartment complex and a neighbor’s burning jeep, and was delighted to get out of there on time.

I moved to a more decent area. This photo, by the way, shows the snow that fell in San Antonio only three times during its existence. This snow was like fine dust, but people were about to ride the sled, you understand. I rented an apartment on the third floor for security reasons, because there are sliding doors everywhere, even on balconies, and a thief can easily enter the apartment on the lower floors by opening a door or window lock. One of the police advice was to use the light to simulate the presence of the owners in the house when no one was there. That is, to set all kinds of timers, which would include light bulbs, a TV, and so on, so that a person who looks into the window thinks that the owners of the house. They also advised to inspect all windows and doors before going to bed, and lock them, even if you leave the house for a short time.

It was also advised to regularly remove mail from your mailbox, and when you were away, ask the post office not to deliver mail to you or to get it from your neighbors. I think that these rules were taken as a basis when shooting the movie "Home Alone".
I often worked at night, worked during the day, that is, my apartment looked inhabited all the time. I also installed at home the cheapest version of the X10 automatic device, the so-called "silly chip." This really bad device, created in the late 70s, it sends data to your home electrical network.

It forms a carrier frequency of 120 KHz in the form of a sinusoid from branches of 60 KHz crossing the axis of zero voltage. Each time a wave crosses the zero horizontal, it transmits one bit. The home code, module control code and command consist of 4 bits of information. The waves were subject to interference, and each command had to be entered three times. That is, it was completely unsuitable for comfortable use. But if you live in a small apartment or an old residential complex, you do not need to use a more complex device, this also works. Before use, it had to be programmed.

It automatically turned on and off the light by the days of the week and by the hours, had a security timer, allowed to create macros and could be controlled remotely. The security timer allowed randomly turning the light on and off on different days of the week at different times of the day.
Then I moved from the apartment to my house and immediately decided to do something with the outdoor lighting. I wanted to automatically change the lighting, turn on and off different lights, use photo sensors based on the same X10 device, that is, nothing special. I don’t know how this helped, but for all the time that I lived in this house, no one broke into me even once, although my neighbors were robbed.
Finally, after 10 years, I moved back to Colorado and began to equip my house, taking into account all the experience gained. I was not going to turn my house into a trap, just to make the housing comfortable, and made up such a “wish list”:
- efficient lighting. It would be an automatic wall switch off and such a staircase lighting so that all these 60-80 W bulbs would not create the effect of a “microwave”.
- Setting the lighting by zones, that is, adjusting the intensity of illumination in different parts of the house and centralized control of the change in lighting;
- flexible timing, that is, entering random or constant lighting parameters;
- “Smart” air conditioning system, which itself would turn on and off the air conditioners, depending on the temperature in the premises;
- internal geofencing, that is, the creation of a closed zone, the entrance or exit from which forces the application to execute any commands. This allows you to automatically activate any functions of home equipment, depending on where its owner is located. For example, when you leave home, your mobile phone gives a command to carry out some events.
- Protect your home from wireless auto-attacks. If you remember, one gentleman at last year's DEFCON made a report on z-waves that can decrypt a door lock code and crack it;
- creating a defensive reaction of the house to external stimuli, for example, activation of protection systems when breaking or entering the house.
I didn’t have to install cameras everywhere to watch children with a smartphone, or to automatically open the front doors and garage doors as soon as my car approached the house, because I was afraid of all these terrible things. I just wanted to make my home protect itself.
I needed a person who wants to enter the house to be detained at the doorstep. You know, many have a powerful alarm system, or there is a billboard on the front lawn that says: "Do not get close to my house, otherwise the alarm will work" and so on - so if they intend to ensure their safety in this way, let do as they want. Because there were times when such an alarm was triggered by your friends in the living room or the police detained a completely stranger in front of your house due to incorrect operation of the security system.
I didn’t need this, I wanted my alarm to really work on a real threat, but it was hidden, without any sirens and anything else. That is, when an outsider got into the house, some unusual events would start to take place there, attracting my attention.
The first thing I acquired was WiFi LIFX. This device is for programmable control of a color LED light bulb wirelessly. It was the result of the implementation of the project, which launched on the Kickstarter portal in 2012. It was a cool light bulb with a WIFi module with a brightness of 1000 Lumens, which shone as abnormal and at the same time consumed only 17 watts. She had a fantastic color palette giving lighting of any color. The slide shows the blue lighting of my living room, which is provided by only two of these bulbs mounted on the ceiling. This is really cool. So, when the alarm goes off, your whole house starts flashing red. All chandeliers, staircase lighting, table lamps - everything starts to shine flashing red, as if aliens had arrived. If you still run the car,
Imagine how this will affect the robber.


There is a Python API for encoding this light bulb, so its operation can be programmed in the mode you need. The disadvantages of these lamps are the large size and weight, so you can not use them like ordinary lamps for wall lighting, in addition, they heat up well, so they can not be covered with an ordinary lampshade or shade.
An alternative to these bulbs is Philips Hue. They are much smaller, consume less energy - only 8.5 watts at full brightness, a little cheaper. Three of these bulbs correspond to the brightness of a conventional 360 W lamp. Their disadvantages are a poor color palette and a small brightness. But if you want to use such bulbs to illuminate the dining room or hall, and at the same time be able to arrange a “red” Terrible Security light alarm, then they will become a fantastically good choice.
The following slides show the illumination of my rooms on July 4, however, the camera was not able to transmit really purple and blue light, which creates a combination of 3 Philips Hue lamps and 4 LIFX LED lamps.


The next device I used in my house is called WeMo. It is manufactured by Belkin. This device has the following features:
- creates a WLAN with devices such as LIFX, and allows you to manage this network using your smartphone via WiFi. With its help, you can control quite powerful equipment, for example, motors, and depending on what devices it controls, you can even light a fire and burn your house to hell.
- It uses UPnP and SOAP, automatically updates the firmware and with the help of a router it can lock everything that can be locked in your house;
- controls sockets and wall switches, as well as street lighting, reducing the night power consumption of CFL bulbs to 20 watts;
- inexpensive;
- supports Terrible App and Terrible Security;
- sometimes it works according to your rules, because the built-in application is quite problematic and may not execute certain commands or execute them with errors.
The following slide shows the Home Defense Server that I developed. The main requirements during its development were:
- working capacity 24 hours 7 days a week;
- low power consumption, allowing the use of UPS during a power outage;
- compatibility with analog and digital sensors and components, allowing you to connect it to your home WLAN, that is, it must be a modular system;
- outputs for connecting to traditional home security systems;
- An open platform based on the Raspberry Pi microprocessor.

I needed the system to be able to call me, transmitting video or text messages, so that I did not have to call the police and say: “Hey, my name is Chris, I created Ruba Goldberg’s“ abstruse car ”in my house, and I swear to you, that someone entered my house, could you check it? ” and hear back: "Sir, this is 911, don’t call here anymore!"
The next slide shows my WiFi barbecue smokehouse, which reported the temperature of smoke and meat, the time left until fully cooked, the number of servings and so on, created on the basis of the Raspberry Pi, so I was well versed in its amazing capabilities.
The processor was connected to the sensors via the ten-bit ADC interface and the Rails server was used for its operation, because I had some experience with Ruby on Rails, it is an open-source web framework.

The following site shows the Home Defense server. It is connected with existing home security systems in the form of such a local network, deployed on the basis of the Raspberry Pi. Independent PIR / X-band components of the sensor radar, that is, relays, transistors, motion sensors, are added to the system. The server allows you to activate the alarm system using hardware or wireless panic buttons. The hardware circuits were programmed for the contact type of operation, that is, as normally closed or normally open circuits, and recorded the movement or opening of the door.

To solve all these problems, I used open source software, a list of which is given on the next slide. For example, Magicmonkey processed LIFX protocols of bulbs, combining them into a synchronized system with flexible settings for the flash frequency of certain groups. The Sharph programming language is a LIFX version of Python, based on Magicmonkey libraries and protocols, and allows you to create stunning APIs that provide communication between WLAN and ZigBee network protocols that control LIFX lamps based on the 802.15 wireless protocol at 915 MHz.

The official LIFX Api application, written in Rubi, supported the simultaneous management of multiple light bulbs. I also used something unpronounceable - iancmcc's ouimeaux - an extended version of Python IPI for WeMo devices with an application written on top of the official API. The system had code and linear support. After that, I connected to the network elements of the external interface and services that ensure their functioning.

On the right side of the slide you can see how the “Light Control System” application looks on the smartphone screen. To write this application, I used the lightweight frameworks Flask (in Python) or Sinatra (in Ruby). I created services for each type of equipment - LIFX, Hue, WeMo. Individual services prevented system-wide crashes by running applications on separate ports, that is, if a service failed, the system continued to function. To ensure the performance of such a bulky structure, I used a lightweight Redis-like database, placed it on separate Pi, which were in different rooms, and created tracking services with alarm. I also provided each Raspberry Pi platform with its own hard drive so that there are no delays,
I note that I am not a programmer or an expert in the field of writing codes, but just a tester, so my codes do not look elegant and cumbersome enough, but still work pretty well. I had to test the security system, for which I used the Bluetooth channel. For example, I entered a room with my smartphone, and the system had to see it and respond to my stay there properly, starting certain processes. Moreover, it was quite difficult, because it was necessary to check the signal intensity of my smartphone so that the system “saw” that I was approaching or moving away from the receiver, that is, it was tracking my movement around the house. I give a link to the video of testing the range of Bluetooth CARRI, where it is shown how the light on the second floor goes out when I leave the room and go down the stairs and how it lights up in another room when I enter there. To do this, I used a special device called RSSI - an indicator of the strength of the received signal.
I wrote a script based on Linux rfcomm / hcitool / l2ping, which pinged the MAC address of my phone, checked the constant transmission of packets of RSSI arrays, that is, the intensity of the Bluetooth signal, and gave the command to execute the given function. If the Bluetooth signal was too powerful, the application blocked the wireless interface of the smartphone, so I tried to use only the 802.11 protocol, i.e. WiFi.
The system was tied specifically to my smartphone, and if a neighbor came into the house with her smartphone, she would not have responded to it, because it has a different MAC address.
Thus, I created a system that monitored the owner’s movements around the house by monitoring the approach or removal of a mobile device. “Device proximity monitoring” had the following properties:
- launched a service that monitored the MAC addresses of mobile phones in the table;
- watched WLAN data signal packets and calculated signal strength;
- recorded the recorded signal intensity and the time of its last detection in the Redis database;
- had the ability to keep a history of location;
- affixed separate timestamps and determined the presence of the device. That is, if the system “saw” that a device appeared in the room that it should not have been there at that time, then it would launch another event;
- updated database event triggers that started processes on other devices.

I tied a scheduler called SmartCron to my system, which planned changes in lighting system modes depending on the time of sunrise and sunset according to the data obtained from the free Weather Underground application. This is an awesome API with fantastic lighting intensity adjustments depending on weather conditions, for example, it turned on the light if it was cloudy outside the window.
Now consider a system of protection against wireless attacks. It is based on the principle of sports radio direction finding “Fox Hunting”, when using a receiver, a map and a compass they find transmitters hidden on the ground.

The system detects Z-Wave attacks on access control devices or attempts to drown out the wireless data transmission of sensors and sensors operating at a frequency of 345 MHz to disable the security system. The receivers of the protection system are antennas that detect the beginning of the transmission of signals and the place from where it is produced, that is, they detect the signal of the transmitter of the attacker. They are configured to respond to sensory attacks performed at 345 MHz and Z-wave at 900 MHz, and use the Ehternet network to function in jamming conditions of wireless signals. This technology is based on the Doppler effect, which allows you to detect moving objects due to a change in the frequency and wavelength of the transmitter, which moves relative to the stationary receiver.
Thus, if someone tries to pick up electronic keys to my house, being outside the perimeter indicated by the system, the receiver detects its coordinates. To provide this function, I used the Agrello DF text message format, where the quality of signal detection has a fixed value of 7 picodopts.

The antennas are connected to the serial port of the RS232 interface, then to the USB adapter and the Raspberry Pi processor, where their signals are processed using the Python application. Here, the obtained coordinates are compared with the coordinates of the protected perimeter, and even if the key matches, but is obtained from a source outside this perimeter, the system does not respond to it.
I also provided an active element of protection in case the thief does get into the house. If he thinks that he was not noticed, he will try to steal something and escape. Therefore, I needed a tool showing that the attacker was detected. It was supposed to be electronically activated and produce a lot of noise, but not cause the thief any physical damage. Firstly, the lights in the house began to flash red. Secondly, I connected 12 V solenoids to heavy metal objects that created a knocking effect. That is, when the thief was in the house, the whole house began to flash red, and from the side of the stairs there was a knock, as if someone was going down the stairs.

The last thing I did and from which I categorically discourage you is the signal fireworks from firecrackers. Do not try to do this in your house, because burn it to the ground. Keep in mind that making artisanal fireworks is a federal crime. Remember that I warned you about this!
So, I used a 12V circuit to create a spark that set firecrackers on fire. It was triggered automatically by a security signal, while the firecrackers were not set on fire all at once, but in turn at random and made sounds resembling shooting, similar to the one that the kid had made in the movie "Home Alone".
I note that I did not use Z-wave devices in my home system, because they are expensive and are not an open source. But I plan to test them in the future, and also want to integrate the SDR scanning devices in the 345 MHz range for all wireless sensors and to perform an engineering analysis of the dual-band 2 GIG transmitter operating at 345/900 MHz. I did not have time to do this because I got on a plane and flew here, but I will definitely continue my work. If you have questions about the use of devices to protect your home, please contact me by e-mail, because, unfortunately, I have completely exhausted the time limit allotted for my presentation.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
