New 4G LTE Vulnerabilities: Mass Messaging, Impersonation of Subscriber Devices and Others
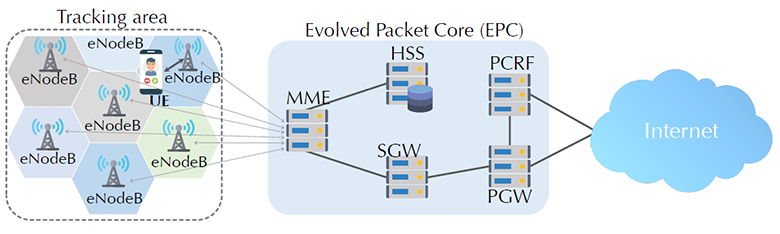
LTE network architecture
At the last conference on security of networks and distributed systems in San Diego NDSS 2018 was a lot of interesting, but the most attention was attracted by the report of American researchers from the University of Iowa and Purdue University on the vulnerabilities in fourth-generation communication networks (4G): LTEInspector: A Systematic Approach for Adversarial Testing of 4G LTE (pdf) . This attention is understandable given the widespread use of 4G LTE networks.
Researchers focused on analyzing three critical procedures that are used in the protocol:
- Attach - a procedure that connects a subscriber device to the network (for example, when you turn on the phone).
- Detach - performed when the device is turned off or the network is disconnected (for example, due to poor signal quality or if the phone cannot authenticate with the network).
- Paging - this protocol is part of the call setup to force the system to re-receive system information, as well as emergency messages.
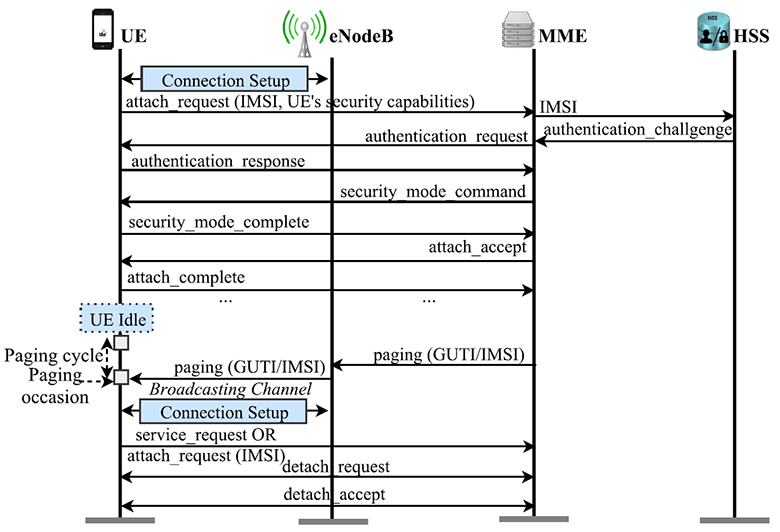
Attach, paging, and detach
routines These routines are critical for the rest to function properly. For example, without the proper execution of the Attach procedure, the entire subsequent security chain does not work and serious consequences arise like MiTM attacks.
To test LTE networks, the researchers created a tool called LTEInspector, which they launched in a relevant model ( code on GitHub ).
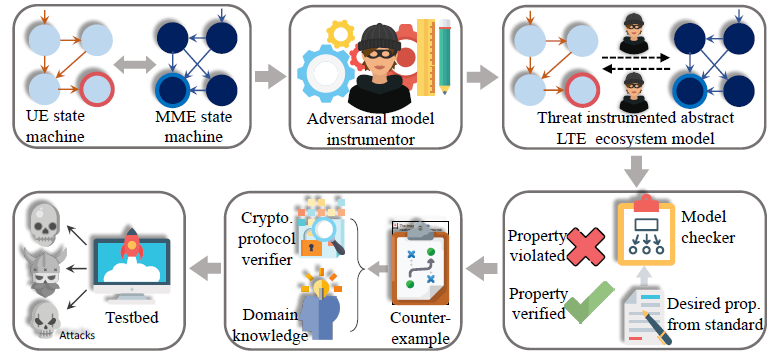
LTEInspector Architecture
Vulnerabilities were found in the simplified ecosystem model of LTE after checking 14 protocol properties according to standards. Although the model is abstract and simplified, the researchers verified that most of the new attacks (8 out of 10) are practicable with SIM cards of US telecom operators. Such attacks will be relatively inexpensive (the cost of equipment is from $ 1300 to $ 3900), if we neglect the legal consequences. In most cases, such testing in real conditions will be a violation of the law.
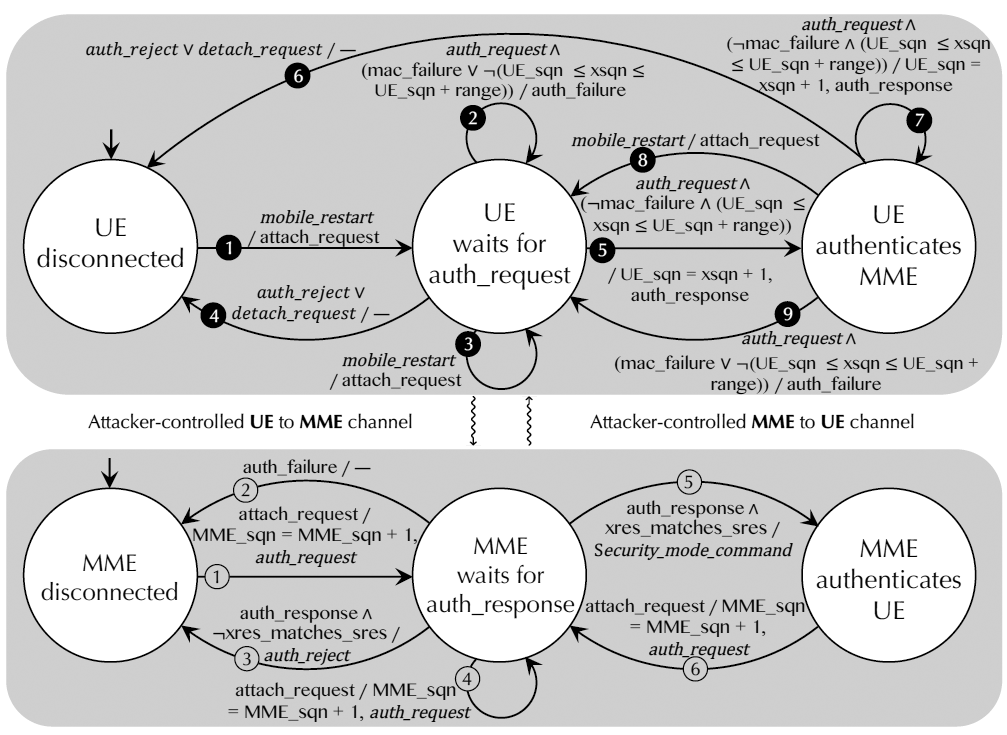
Simplified LTE Ecosystem Model
Based on testing results, LTEInspector was able to detect new vulnerabilities that can be used to conduct 10 new attacks. Among them is an authentication relay attack, which allows an attacker to connect to main networks by passing his terminal as a victim device. In this way, you can change the coordinates of registering the device on the network - for example, you can use this to create a “fake alibi” or, conversely, fabricate evidence in the investigation of a criminal offense. If the victim’s phone at the time of the crime was in the area of the crime scene, this information will be known to the investigating authorities - and an innocent person may be suspected.
Other options for using the discovered vulnerabilities are obtaining approximate information about the user's real location, denial of service (DoS) attacks, and introducing an operator into the paging channel. In the latter case, it is possible not only to block the victim from receiving calls or SMS, but also transmit to him a fabricated “emergency” message through the service channels of cellular communication.
For example, an attack with an authentication transfer belongs to the class of attacks against the attach procedure (A-4 attack in the table below). Here, the attacker must establish an intermediate cellular communications node (eNodeB) and know the IMSI of the victim’s device. For the fake cellular node to work correctly, you must first connect to the operator’s network with its SIM card and find out the parameters that the operator transmits in messages
system_info_block. To intercept and listen to incoming and outgoing LTE messages, the sniffer and the QXDM program (Qualcomm Extensible Diagnostic-Monitor) are used . The following configuration parameters are intercepted from system_info_blockoperator messages : band, dl_earfcn, mcc, mnc, p0_nominal_pucch, p0_nominal_pusch, q_rx_lev_min, q_hyst, DRX cycle. An attacker can find out the IMSI number of a subscriber's device when it connects to its eNodeB. Then a request
identity_requestis sent to the device - and the answer comes identity_response. 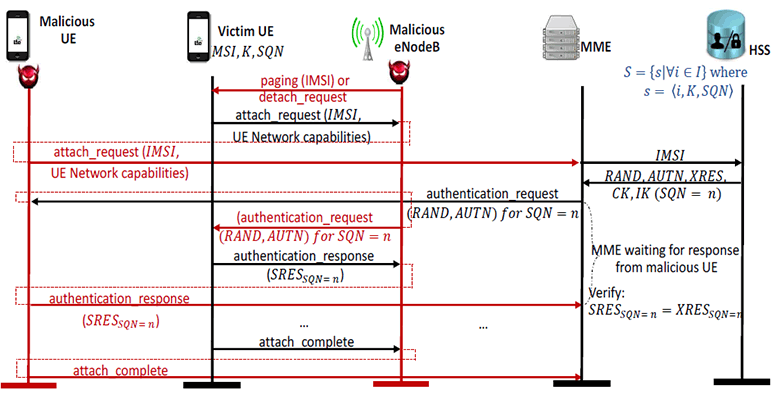
Authentication Attack
This is the most “expensive” attack, because to validate it requires the installation of three USRP devices at a cost of about $ 1300 each. This is necessary in order to raise your own dummy network, similar to the real operator’s network, and to validate it without violating the law.
USRP is a peripheral hardware platform for software defined radio system (SDR). In the field test, the researchers used the USRP B210 board ($ 1315) with the srsUE program , which is part of srsLTE (the source code is open in the repository on GitHub).
The table lists all new attacks discovered during the study. Seven of them are fully confirmed in practice, one partially (P-4), and two are not confirmed (P-3 and P-5). The cost of attack validation varies from $ 1300 to $ 3900, depending on the number of required USRP boards. In fact, this is the maximum cost of equipment to attack, not counting the cost of the terminal device (UE). In reality, USRP can be found cheaper, and in some cases, for a real attack, you do not need as much USRP as for its validation.
| ID | Attack name | Conditions | Standard / subject | The consequences |
|---|---|---|---|---|
| A-1 | Authentication Sync Error | Famous IMSI, malicious UE | 3GPP | Denial of connection, denial of service |
| A-2 | Traceability | Valid security_mode command, malicious eNodeB | Operator networks, mobile devices | Sample Location Information |
| A-3 | Disabling via auth_reject | malicious eNodeB | 3GPP | Denial of all cellular services |
| A-4 | Authentication transfer | Known IMSI, malicious eNodeB | 3GPP, network operators | Reading the victim's incoming / outgoing messages, secretly disabling all or certain services, replacing the location history |
| P-1 | Paging channel capture | Known IMSI, malicious eNodeB | 3GPP | Secretly disabling inbound services |
| P-2 | Discreet discharge | Known IMSI, malicious eNodeB | 3GPP | Unprecedented for the victim disconnection from the network |
| P-3 | Panic | Malicious eNodeB | 3GPP | Mass mailing of life-threatening emergency warnings: for example, artificial chaos in the event of terrorist activities |
| P-4 | Energy depletion | Known IMSI, GUTI, malicious eNodeB | 3GPP | Battery depletion |
| P-5 | Connectivity | Known IMSI or old pseudo-IMSI | 3GPP Extended 5G AKA | Sample Location Information |
| D-1 | Mute / lower | Malicious eNodeB known by IMSI (for targeted version) | 3GPP | Denial of service, downgrade to 2G / 3G |
Note that attacks like "Panic" are really capable of causing chaos in the population. In January 2018, the Hawaiian Emergency Management Agency mistakenly sent an emergency message about a ballistic missile approaching , frightening locals who massively went to bomb shelters.
The authors of the study are skeptical about the ability to close identified vulnerabilities in existing protocols. According to them, if you add retrospectively security measures to existing protocols without violating backward compatibility, this often leads to unreliable solutions such as “patches”. Therefore, before using communication protocols, it is important to test them thoroughly first.

