Why photography Scarlett Johansson caused PostgresSQL to mine Monero
- Transfer
As part of our client’s data protection campaign, we at Imperva talk about different methods of attacking databases. If you are new to our StickyDB research project, read past articles: Part I and Part II . It describes a device of a network of chanipot (Fig. 1), which lures attackers to attack our databases, so that we learn their methods and improve protection.
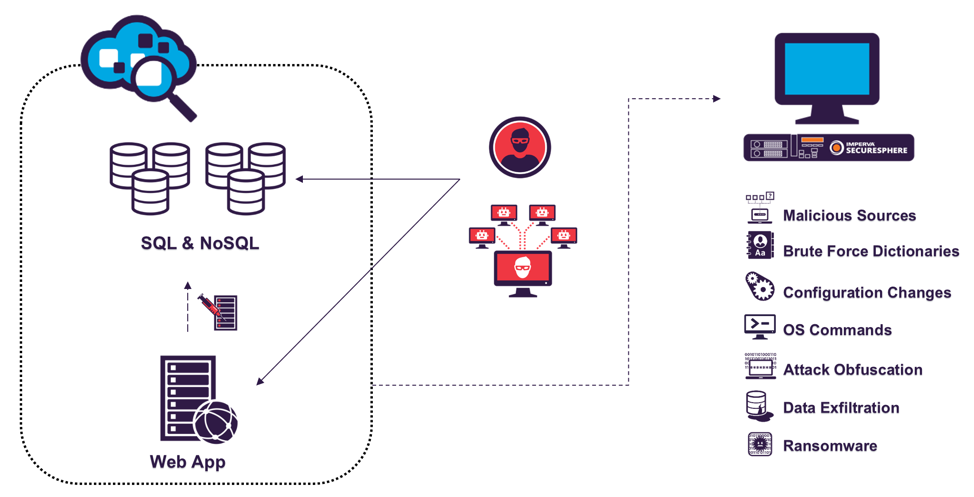
Fig. 1. Network environment of StickyDB
We recently discovered an interesting technique during an attack on one of the PostgreSQL servers. After entering the database, the attacker continued to create payloads from the built-in binaries in the downloaded pictures, save payloads to disk, and launch them. As often happens recently, an attacker seized server resources for mining Monero. As if this were not enough, the attack vector was a photograph of Scarlett Johansson . Well then fine. Let's see how it works!
Like other popular databases, PostgreSQL has a metasploit module that makes it easy to interact with the OS. The standard method is used here - creating a payload at runtime by flushing the binary to disk using the lo_export function . One small change in the module is the introduction of the lo_export function as an entry in the pg_proc directory instead of a direct call. This is done to avoid detection by some database audit monitoring systems (DAMs) that closely monitor privileged operations like lo_export . Thus, obj6440002537 is essentially an indirect call to lo_export (Fig. 2).

Fig. 2. Technique of evasion through an indirect call lo_export
An attacker can now run local system commands with one simple function
So what are the next attack steps? A little intelligence. A hacker starts by acquiring information about the GPU by running the lshw -c video command and then cat / proc / cpuinfo to obtain information about the processor (Figure 3-4). Although this seems strange at first glance, such a check makes sense if the ultimate goal is to get more of your favorite cryptocurrency, right?

Fig. 3. View GPU Information
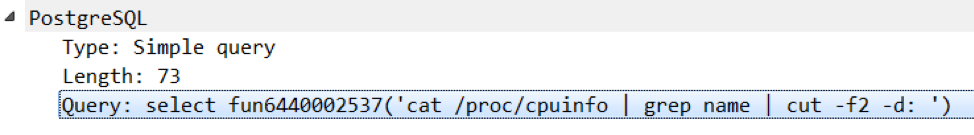
Fig. 4. Viewing information about the CPU So
far, the attacker has gained access to the database, set up a remote code execution channel, and also bypassed DAM solutions and learned about the details of the system. Now everything is ready to ... upload a photo of Scarlett Johansson ?! Wait, what?
I must say, attackers are showing more and more creativity.
In this case, the attackers wanted to download a new sample of malicious code, so they placed it on the usual free photo hosting imagehousing.com . However, the payload must have a binary format. If you simply rename the binary to .PNG format, the file will not pass the test when uploading to photo hosting as an invalid image that cannot be viewed. Instead of renaming the file, the attacker added malicious binary code to the real photo of the beautiful Scarlett Johansson (Fig. 5). So the download succeeds - the image is viewable, it seems benign, and the payload is still there.

Fig. 5. The payload. When opened, it seems like an ordinary image. Do not worry - here the picture is clean, that's for sure!
See the binary code? He is right under her left elbow! :)
We reported imagehousing.com about the problem - and the image was deleted.
So, downloading the image ( art-981754.png ) with the payload was easy with the wget command . Extracting the executable from the photo is done with the dd (data duplicator) command . Then the execution permissions are set, in fact, full permissions ( chmod 777 ) for the created x4060014400 file . The final step is to launch this newly-extracted payload.

Fig. 6: How to download a picture using SQL tools, extract the binary and execute it.
The x4060014400 file creates another binary called s4060014400 . Its task is to mine Monero (XMR) in the pool https://monero.crypto-pool.fr/, IP 163.172.226.218 (Fig. 7). This address Monero has now listed more than 312,5 XMR worth more than $ 90,000:
4BBgotjSkvBjgx8SG6hmmhEP3RoeHNei9mz2iqwhws8wefvwuvi6keplwdfnx6guiq5451fv2soxod7rhzqhqtvbdtfl8xs
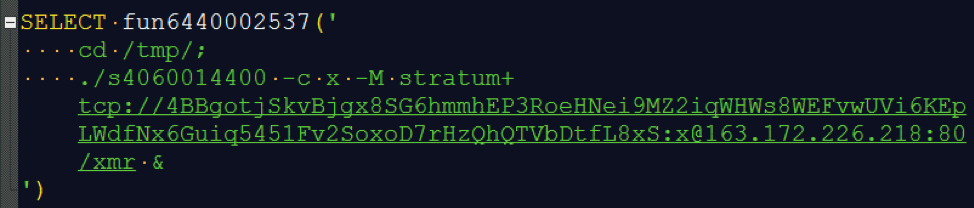
Fig. 7. SQL statement to start mining Monero
Of course, when it’s done, you need to cover the tracks.
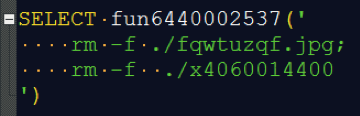
Fig. 8. Clearing traces
From the point of view of the attacker - the mission is completed!
Using VirusTotal from Google, we checked how nearly 60 antiviruses respond to three different forms of cryptominer in this attack: the URL where the malicious image was located, the image file itself and the cryptominer. Results:
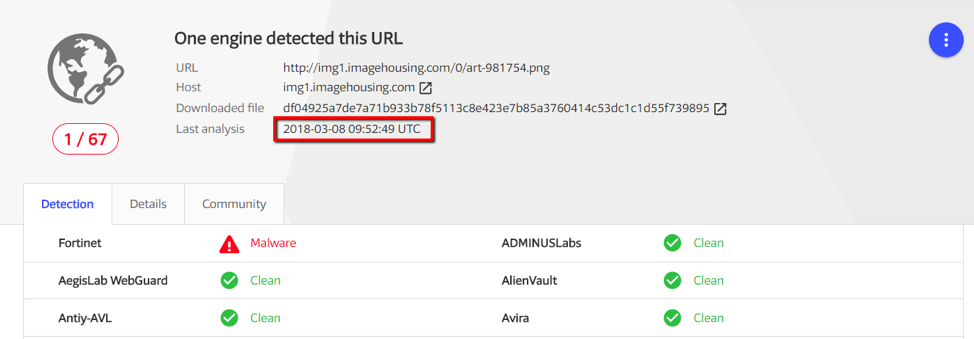
Fig. 9. One antivirus responded to a malicious URL
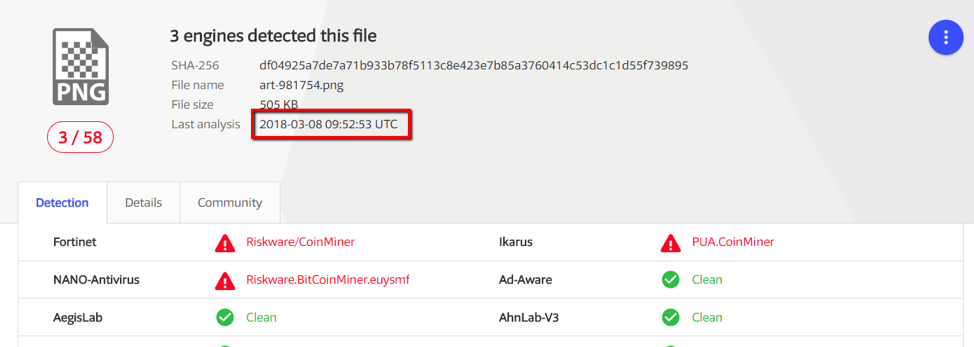
. 10. Three antiviruses reacted to a malicious image
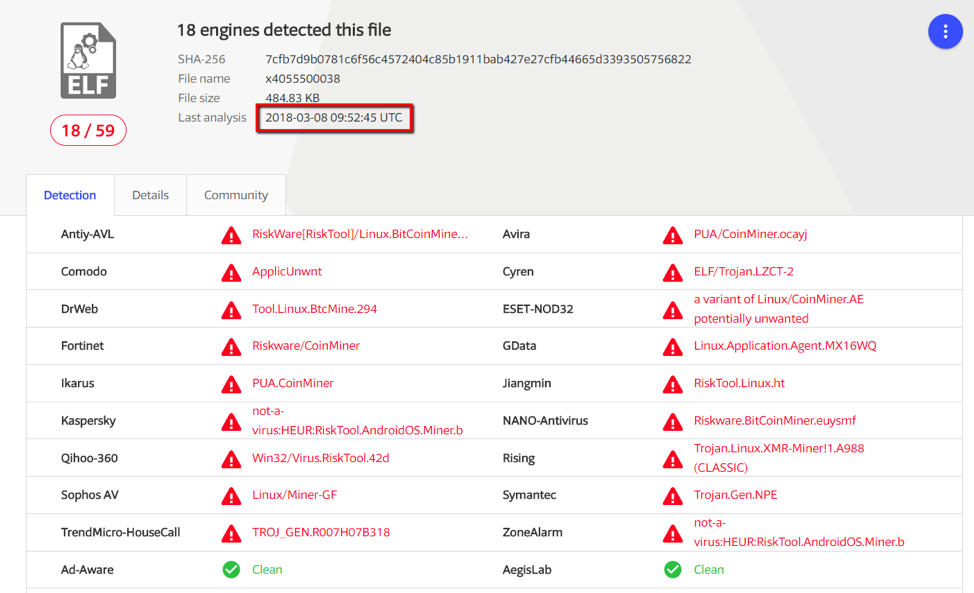
. 11. Eighteen antiviruses discovered the
Trick crypto miner with the addition of a binary to normal files (images, documents) - a very old method, but it still allows you to bypass most antiviruses. This is a really shocking fact.
Creating such a mutant file is trivial in one line:
Linux: cat myExecutableFile >> myImageFile.png
Windows: type myExecutableFile.exe >> myImageFile.png
You can find PostgreSQL instances on domains using discovery tools, such as Nmap , if the attacker is already inside the local network. But can simpler goals be found? What about PostgreSQL databases open to the outside world? It is known that this is not recommended, but do such databases exist? Well ... actually, yes, at least 710,000 of them are hosted on AWS in a bunch (Fig. 12). And find them elementary through Shodan . So an attacker can easily get a list, run a password bruteforce for the default postgres user , log in and apply some of the methods described.
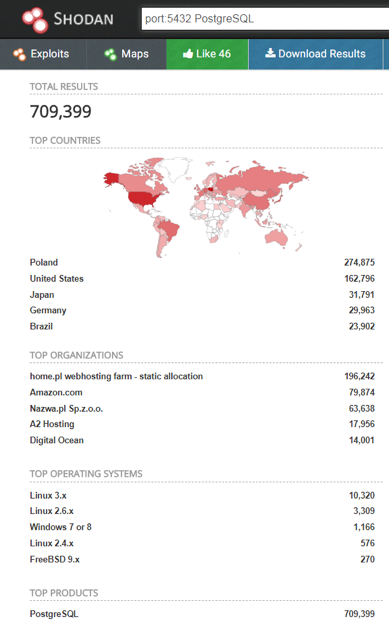
Fig. 12.710 thousand PostgreSQL instances with public IP addresses. Illustration: shodan.io
In the next article in this series, we will discuss other attacks. The final article will be devoted to protection, but here are some quick tips on how to avoid this threat:

Fig. 1. Network environment of StickyDB
We recently discovered an interesting technique during an attack on one of the PostgreSQL servers. After entering the database, the attacker continued to create payloads from the built-in binaries in the downloaded pictures, save payloads to disk, and launch them. As often happens recently, an attacker seized server resources for mining Monero. As if this were not enough, the attack vector was a photograph of Scarlett Johansson . Well then fine. Let's see how it works!
Remote code execution and DAM protection bypass
Like other popular databases, PostgreSQL has a metasploit module that makes it easy to interact with the OS. The standard method is used here - creating a payload at runtime by flushing the binary to disk using the lo_export function . One small change in the module is the introduction of the lo_export function as an entry in the pg_proc directory instead of a direct call. This is done to avoid detection by some database audit monitoring systems (DAMs) that closely monitor privileged operations like lo_export . Thus, obj6440002537 is essentially an indirect call to lo_export (Fig. 2).

Fig. 2. Technique of evasion through an indirect call lo_export
OK, your database is under control. And what is your GPU?
An attacker can now run local system commands with one simple function
fun6440002537. This SQL function is a wrapper for calling a C language function sys_eval, a small exported function in tmp406001440(a binary file based on sqlmapproject ), which is usually used as a proxy to invoke shell commands. So what are the next attack steps? A little intelligence. A hacker starts by acquiring information about the GPU by running the lshw -c video command and then cat / proc / cpuinfo to obtain information about the processor (Figure 3-4). Although this seems strange at first glance, such a check makes sense if the ultimate goal is to get more of your favorite cryptocurrency, right?

Fig. 3. View GPU Information

Fig. 4. Viewing information about the CPU So
far, the attacker has gained access to the database, set up a remote code execution channel, and also bypassed DAM solutions and learned about the details of the system. Now everything is ready to ... upload a photo of Scarlett Johansson ?! Wait, what?
Malware under the guise of a photograph of Scarlett Johansson
I must say, attackers are showing more and more creativity.
In this case, the attackers wanted to download a new sample of malicious code, so they placed it on the usual free photo hosting imagehousing.com . However, the payload must have a binary format. If you simply rename the binary to .PNG format, the file will not pass the test when uploading to photo hosting as an invalid image that cannot be viewed. Instead of renaming the file, the attacker added malicious binary code to the real photo of the beautiful Scarlett Johansson (Fig. 5). So the download succeeds - the image is viewable, it seems benign, and the payload is still there.

Fig. 5. The payload. When opened, it seems like an ordinary image. Do not worry - here the picture is clean, that's for sure!
See the binary code? He is right under her left elbow! :)
We reported imagehousing.com about the problem - and the image was deleted.
From uploading pictures to crypto mining
So, downloading the image ( art-981754.png ) with the payload was easy with the wget command . Extracting the executable from the photo is done with the dd (data duplicator) command . Then the execution permissions are set, in fact, full permissions ( chmod 777 ) for the created x4060014400 file . The final step is to launch this newly-extracted payload.

Fig. 6: How to download a picture using SQL tools, extract the binary and execute it.
The x4060014400 file creates another binary called s4060014400 . Its task is to mine Monero (XMR) in the pool https://monero.crypto-pool.fr/, IP 163.172.226.218 (Fig. 7). This address Monero has now listed more than 312,5 XMR worth more than $ 90,000:
4BBgotjSkvBjgx8SG6hmmhEP3RoeHNei9mz2iqwhws8wefvwuvi6keplwdfnx6guiq5451fv2soxod7rhzqhqtvbdtfl8xs

Fig. 7. SQL statement to start mining Monero
Of course, when it’s done, you need to cover the tracks.

Fig. 8. Clearing traces
From the point of view of the attacker - the mission is completed!
Do antiviruses respond to these malicious photos?
Using VirusTotal from Google, we checked how nearly 60 antiviruses respond to three different forms of cryptominer in this attack: the URL where the malicious image was located, the image file itself and the cryptominer. Results:
- URL: one antivirus reacted (Figure 9)
- Image file: three antiviruses warned of a hidden crypto miner (Fig. 10)
- Recovered cryptominer: detected by 18 antiviruses (Fig. 11)

Fig. 9. One antivirus responded to a malicious URL

. 10. Three antiviruses reacted to a malicious image

. 11. Eighteen antiviruses discovered the
Trick crypto miner with the addition of a binary to normal files (images, documents) - a very old method, but it still allows you to bypass most antiviruses. This is a really shocking fact.
Creating such a mutant file is trivial in one line:
Linux: cat myExecutableFile >> myImageFile.png
Windows: type myExecutableFile.exe >> myImageFile.png
How does an attacker find PostgreSQL databases?
You can find PostgreSQL instances on domains using discovery tools, such as Nmap , if the attacker is already inside the local network. But can simpler goals be found? What about PostgreSQL databases open to the outside world? It is known that this is not recommended, but do such databases exist? Well ... actually, yes, at least 710,000 of them are hosted on AWS in a bunch (Fig. 12). And find them elementary through Shodan . So an attacker can easily get a list, run a password bruteforce for the default postgres user , log in and apply some of the methods described.

Fig. 12.710 thousand PostgreSQL instances with public IP addresses. Illustration: shodan.io
In the next article in this series, we will discuss other attacks. The final article will be devoted to protection, but here are some quick tips on how to avoid this threat:
- Watch for direct calls to lo_export or indirect calls through entries in pg_proc .
- Beware of functions that access binaries in C (as in Figure 2).
- Use a firewall to block outgoing network traffic from the database to the Internet.
- Make sure your database is not assigned a public IP address. If so, restrict access only to hosts that interact with the database (application server or DBA clients).
