What is a PAT? Lab at Packet Tracer
- Tutorial
Introduction
PAT (Port Address Translation) is a technology for translating addresses using ports. This technology solves the problem of delivery of return packets . Since the number of white IPs is limited, we need to save these addresses. With this in mind, the PAT technology was created. It allows local hosts to use private IP addresses.and set one registered address on the access router. In the RAT address translation technology, a feature of the TCP protocol is used: from the server’s point of view, it doesn’t matter whether connections are made to three different hosts with different addresses or connections are made from one host to one IP address, but with different ports. Therefore, in order to connect to the Internet hosts a lot of small office with the help of only a registered public IP address, the PAT service translates the private addresses of local hosts into one registered one. In order to correctly forward reverse communication packets to local hosts, the router stores a table of IP addresses and port numbers for the TCP and UDP protocols. You can read about IP addresses and subnet masks in my other article .
Laboratory work assignment
Create a simple network using PAT technology (NAT overloaded). The network diagram is presented below. All work will be done in Cisco Packet Tracer.
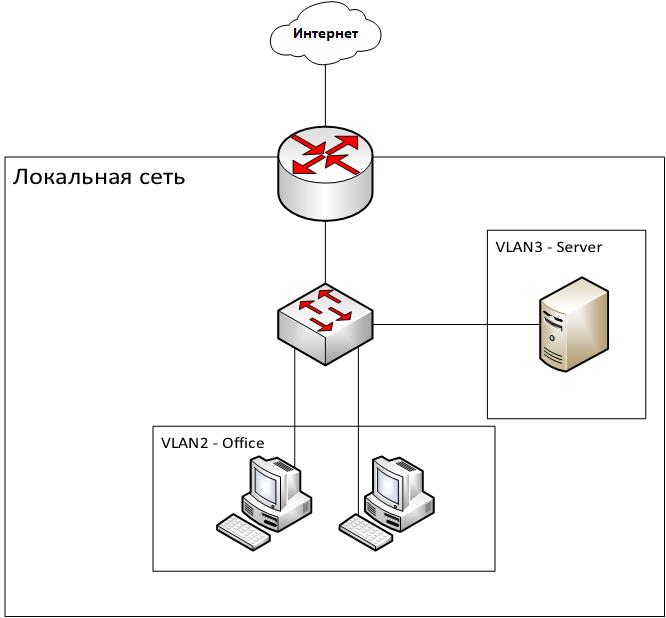
Laboratory work
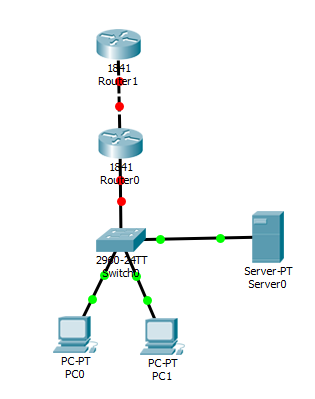
1. Create 2 PCs, a server, a switch and 2 routers on the Packet Tracer dashboard and connect all devices as shown.
2. On the switch, configure 2 VLANs so that the operation scheme is as follows. Who does not know how to do this and what is VLAN, see my last article .
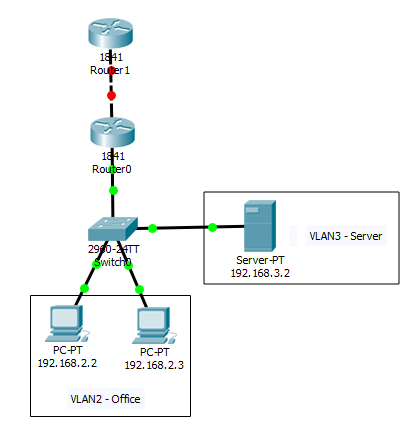
3. Raise duplexes on Router0 to the port connected to the switch. We did all this work in the previous lab (laboratory work on VLAN), so I will not dwell on this point in detail. Then we ping the server from any PC.

4. Configure routers. On router 1, set the white IP address on the port that is connected to router 0 with a cross-cable. For example, I took 120.120.53.1. On router 0, set the same white IP, but put 2 at the end, since this is the next device on the network (120.120.53.2). Thus, we simulated the situation of Internet connection from the provider.
5. Check the ability to access the Internet from any PC. That is pinganem 120.120.53.1.
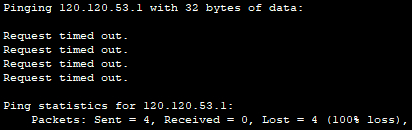
We cannot connect, as can be seen in the screenshot above.
6.Now configure PAT with the access list. This is necessary so that we can expand our network and connect several vlanes. Pay attention to our scheme. From it you can see that the local network ends on a zero router. It starts accessing the Internet via public IP. Therefore, it is on it that we will configure PAT. First, we need to determine which interface for PAT will be external and which internal. The external interface is the one that goes to the Internet, and the internal one that is inside the local network. That is, in our case, the external one is fa0 / 0, and the internal two, since there are two departments (fa0 / 0.2 and fa0 / 0.3)
7. Set up a zero router to work with PAT. Based on paragraph 6, we introduce the following commands: 8.
Router>en
Router#conf t
Router(config)#int fa0/0
Router(config-if)#ip nat outside
Router(config-if)#exit
Router(config)#int fa0/1.2
Router(config-subif)#ip nat inside
Router(config-subif)#exit
Router(config)#int fa0/1.3
Router(config-subif)#ip nat inside
Router(config-subif)#exit
Router(config)#end
Router#wr memLet's create an access list on the same router so that the router “understands” what to put on it.
We will introduce the following commands: 9. You can verify what happened with the show run command . To start PAT, we will need to enter another command in the configuration settings: Check the Internet connection. And the victory! Everything works. Let's deal with all the teams now.
Router>en
Router#conf t
Router(config)#ip access-list standard HABRAHABR
Router(config-std-nacl)#permit 192.168.2.0 0.0.0.255
Router(config-std-nacl)#permit 192.168.3.0 0.0.0.255
Router(config-std-nacl)#endip nat inside source list HABRAHABR int fa0/0 overload
ip access-list standard HABRAHABR - create a standard access list with the name HABRAHABR
permit 192.168.2.0 0.0.0.255 - add network addresses with a reverse network mask
ip nat inside source list HABRAHABR int fa0 / 0 overload - start the NAT path from the inside (from insider) by access to a sheet called HABRAHABR on the int fa0 / 0 interface. Overload indicates the type of NAT, namely overloaded NAT, that is, PAT.
