FastTrack Training. "Network Basics." "The Basics of Wireless LAN." Part one. Eddie Martin December 2012
- Tutorial
About a year ago, I noticed an interesting and fascinating series of lectures by Eddie Martin, which is incredibly intelligible, thanks to its history and real life examples, as well as colossal experience in teaching, which allows us to gain an understanding of rather complex technologies.
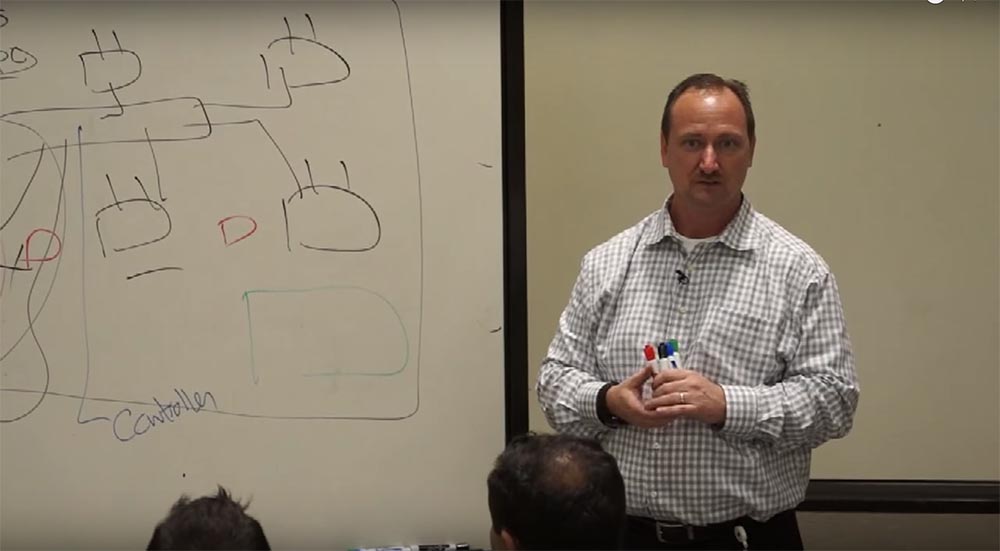
We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “Fundamentals of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Fundamentals”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the eighth of them.
So, the next thing we'll talk about is a wireless local area network. We will start with the basics.
It is simply unbelievable that we are talking about this now, because among us there are those who do not even remember the times when the networks were only wired. There is nothing wrong with being young; I would never blame someone for being too young. I will envy, but I will not blame.
But just imagine that there was a time when we were all tied to wired networks. I remember exactly those times. But now I can’t tell you exactly when I last connected the laptop by wire. I cannot do this. I could use a USB connection, but definitely not a wired network.
We cannot completely get rid of wired networks, for example, in data centers. Wireless bandwidth will not be enough for you to replace 10 gigabit or 40 gigabit networks. It will take a lot of time.
But let's think about a wireless network in terms of how it has changed our world. Wireless networks have been in our service for a long time, remember the first cordless phones? They stood at our house. What frequency did they work at, you remember? 900 megahertz. They had good coverage, but what was wrong with them? What was wrong with these phones at home with a frequency of 900 megahertz? They were not protected. People could hear you. It’s good if the first one had such a phone, but then the neighbors appeared and they could get on your communication channel and hear you. I still have a couple of 900 megahertz speakers in my backyard that I use for all kinds of sports activities and more. And my neighbor across the road still has a phone operating at a frequency of 900 megahertz.
900 megahertz provide a large range, but low bandwidth. But you know, at that time we already had wireless networks operating at a frequency of 900 megahertz. They had a megabit of bandwidth, and it was already a revolution. Few knew about this, because this function was very unique and specialized. The frequencies crossed and people said no, I need something more secure. I do not want other people to hear me, so I want a frequency of 2.4 gigahertz.
And we switched to a free spectrum frequency, 2.4 GHz DSS (digital spread spectrum), digital spread spectrum. You may not have to worry that they will hear you and choose your channel for communication using the phone settings. But why didn’t we stay in that network? Why aren’t we still using it?
Yes, everyone just switched to this spectrum, we got interference. We no longer had the opportunity to listen to each other at this frequency, but the phones interfered with the normal operation of each other. And then we switched to another frequency. What frequency was that? 5 gigahertz. We switched to a new spectrum and the people began to catch up there. As a result, there were noises, and then a new spectrum appeared.
Not sure what frequency it worked at, possibly 1.9 GHz, but it was called Dect 6.0. It was outside the working range of all other devices and therefore, perhaps, was considered the most secure. These ranges have been filled. I will tell you that when in the late 90s we developed standards, and this was very important, there were many companies and they all had their own. There were their working frequencies, their expanded digital spectra. And they did not work with each other normally. Many thought - this is not part of my business, I will not do anything. Then came these standards.
I won’t say that Cisco invented wireless networks, but they acquired Era Net, the market leader at the time. They were the best engineers and developed the best technical solutions in this area. Cisco has become leaders in the field of wireless technology in an instant. It was a great time, then standards appeared and people began to use these technologies in business. But it turned out that we were not as smart as we thought.
What do you think happens when Cisco buys another company? First of all, we transfer all products to our operating system. When we bought Era Net, the first thing we did was give them our equipment, 350 series access points. And we upgraded their operating system to ours. We converted their software, their OSes, and got the smartest access point in the world. There was nothing that she would not do. Looking ahead, I’ll say that this was not the best solution at that stage.
Let's see what a wireless network is and tell you that it is not as difficult as it seems. I will draw the building, let it be the floor plan of the building. I have access points here.
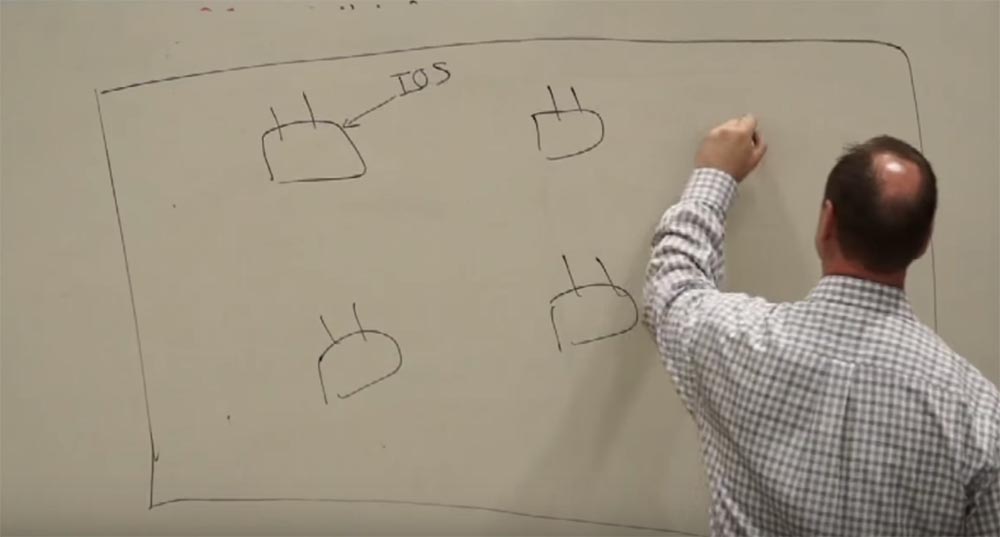
And we have network users, computers, mobile phones and any other devices, no matter which. An access point is a gateway to a wired network. The process of getting into the network is a two-step process. But you can skip one of the steps if you want.

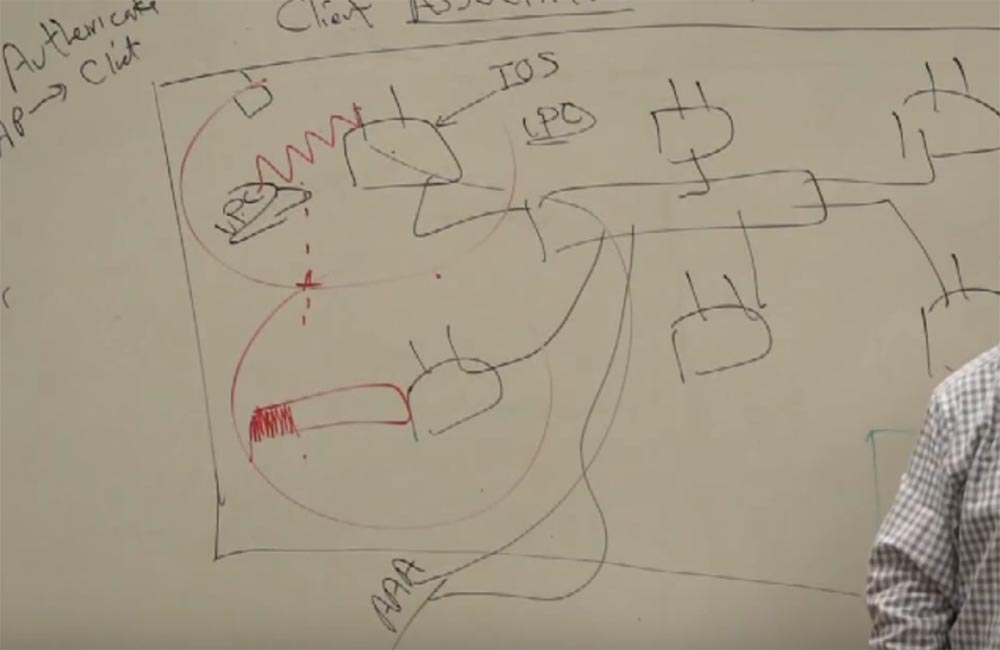
I'll explain now. The client is associated with an access point. It looks like this. The computer sees the wireless network, and says: "I want to connect." Imagine that we have three access points and one client. I say: "All three of you look the same for me, let me ask you a few questions." - “How many users do you have on the network”? - "And how much do you have"? - "And you"? “What is your disposal?” I can understand which of the access points suits me best, where there are fewer users, where the connection will be better, based on a survey of many access points. Then I choose, and I say: "I want to connect to you." How often do we connect to a network that was not created for us? Often. Why not connect to a neighbor’s network? It's free. So it is, agree. There is no protection here.
We pass to the second stage - authentication.

At this point, the access point polls the client. The network says, “Wait a minute, show me your credentials. “Then I will miss you.” This is the whole principle of wireless networks.
Do you have such authority at home? You have an SSID (service set identifier) translated as a wireless network name by a router that you can hide and you have a key that can consist of many letters, numbers or a phrase. At home, we have a network sharing key for authentication. I have many devices and one access key for them. Why is this not suitable in business?
Just imagine that 70 thousand people work in Cisco. Imagine that we would have a Blizzard username and password in Blizzard. You are not telling anyone. It's a secret. You take your laptop, log in, then leave it somewhere unattended and your login details are stolen. What will happen? I will have to change the login information on the remaining 60,999 computers. What really identifies you, how exactly you are is your username and password.
That is why business authentication will be different from home network authentication. We want to give you a unique username and password and a unique secure connection. Therefore, when you connect to the access point and she tells you - wait, give me your credentials, you are sent to the AAA server.

What kind of server is this?
These are three letters A, that is, authentication, authorization and accounting. We also sell these AAA servers. When you are hired by our company, you are immediately assigned your details to enter the network. Your login in the form of email and your first password. You log in and then immediately change the password. There you will immediately see the password requirements, for example, at least 8 letters, with capital letters, numbers, or something else. But we need all this in order to understand that it is you.
Customers are often used to saying that a wireless network is unsafe. But I explain that a wireless network can be much safer than a wired one. I could come to clients, connect my computer and immediately get to them on the network. Now to access the network you need to authenticate. It is the AAA server that tells us who you are when you connected and where you have access and when you disconnected. This is exactly what the AAA server does. When you have been given access, your request is sent to this server and you receive the first encryption key (encrypted key), each has its own unique encryption key. You have your own key, you have your own, and we give them out randomly. Everything is very safe. Any information coming from the computer is encrypted thanks to this key and the key is constantly changing.
I had a client who represented a savings and lending institution, and he came to talk to me and I began to tell him about wireless networks. His eyes literally popped out of his orbit when he heard about wireless networks. He shouted - we won’t have it, we are a financial institution. He literally wanted to pounce on me. I told him - hey, calm down. Put your eyes in place.
What do we say to a client who doubts the security of wireless networks? He will say - I do not need a wireless network, it is unsafe. What do you tell him? I don’t know about you, but I said: “Do you know where there are wireless networks”? If the access point didn’t hang so clearly in this office now, how could you understand this? Can you smell it, taste it, hear it? Not. You cannot understand if there is a wireless network here. You will need a device to find out.
There used to be such small access points, remember? I once did a training in Southern California at Long Beach at the Marriott Hotel. We were in a remote corner of this entire hotel complex, it wasn’t very well with a wireless network signal. As an instructor, I bought a wired connection. Everything was fine with my connection, but the students were furious. Communication lags, well, or how to say it technically. And what have I done? The next day I installed Lynksys, here you have access, stop whining and let's continue classes. I actually made an unauthorized connection with that network and no one ever said anything to me.
We will return to the client with eyes jumping out of the eye sockets. I asked him: “How do you know that you do not have a wireless network”? My account manager, of course, then kicked me for it with his sharp boots. Kicked right in the shin and it was encouraging. And guess how it all ended? We sold to that client access points that performed a single function - they protected against intrusion into the network. He was afraid that someone behind the firewall would connect the wireless network and what did we do? We set up a wireless network to prevent wireless connectivity.
There are no security documents that would not include wireless networks, even then in 2003, 2004 or 2005. Today you need to have protection through a wireless connection.
Let's get back to my story. We placed our operating system on the devices and created the smartest access points in the world. Imagine that I have a meeting here.

I take my computer and start wandering around with it. I go from here to here, from one point to another and this is called roaming. This is similar to what you do with your cell phones. Points have a radius, and so on. At this point, my computer understands that neither this access point gives me the desired signal level, nor the other. Imagine that I am showing a presentation in PowerPoint, because I'm still at a Cisco meeting. That is, I have a download. What will happen to this download?
It will stop for a second while I reconnect from one access point to another. She stops for a second and continues on.
We have the opportunity to do this and the customers are thrilled. They liked our limitless roaming. The same thing will happen between these access points and between others.
Everything was nowhere better, but then Cisco began to sell other products. We released phones, Spectral link - these were the first phones that we connected here. We were able to start transmitting voice wirelessly. And then the problems began.

So, let's talk about phones. We put here a special VLAN called Voice Net. Suppose I work for Blizzard here and want to put all my voice devices on Voice Net. Give them greater priority, greater bandwidth, the ability for voice transmission to go perfectly. I'm just thrilled and plug in these devices. The voice is connected to Voice Net, I myself am to Blizzard, everything works fine, I upload my file, I begin to move around the room. And when I start walking and find myself at about this point, my wife calls. Hello dear, how are you? Want to tell me what I did wrong today? Let me cancel my meeting, and you continue? The conversation takes place at this point.

I start walking and talking with my wife, and what happens when I find myself on the edge of the networks? My conversation will be interrupted. The conversation is interrupted, although the failure is only 1 second. And I find myself in the zone of another access point. My wife calls me back. She says, “Have you dropped me?” “No, what are you, it's all technology.” “It's all wireless technology.” “You don’t have to blame the technology, you geeks are always talking about them all the time.” Then I go out of this network and do not call back, let him leave me a voice message. I'm already done, no chance. Just one second of stopping and switching to another network is 20 lifespan for a phone call.
The problem was that the device was too smart, it knew everything about the network. And this device was so smart that it also knew everything about the network. And it took them both a second to realize that they were both not together at that moment and my call was interrupted.
And here Cisco found a way out of the situation. This required the Catalyst 6500, a supervisor for 40 thousand dollars, a line card for 45 thousand dollars, 20 hours of work for the engineers who organized all these tunnels on the network. Not the best solution. Cisco has such small cards that we are distributing, and one of them says - no worship of technology. And we had to buy another company to solve this issue. After all, sometimes there are situations when being smart is not so smart.
So, Cisco bought Airspace. It was a great acquisition for Cisco, because at that moment we decided - let's not make access points smart. Let's make them simplified or, in other words, stupid. Some started calling them dumb. Instead of installing all the features on all access points, I will install them in one place - in the controller. I will put a new device on the network. This controller will be the brain center of all access points. This point used to have its own brain, but now it is not there. He is in the controller.
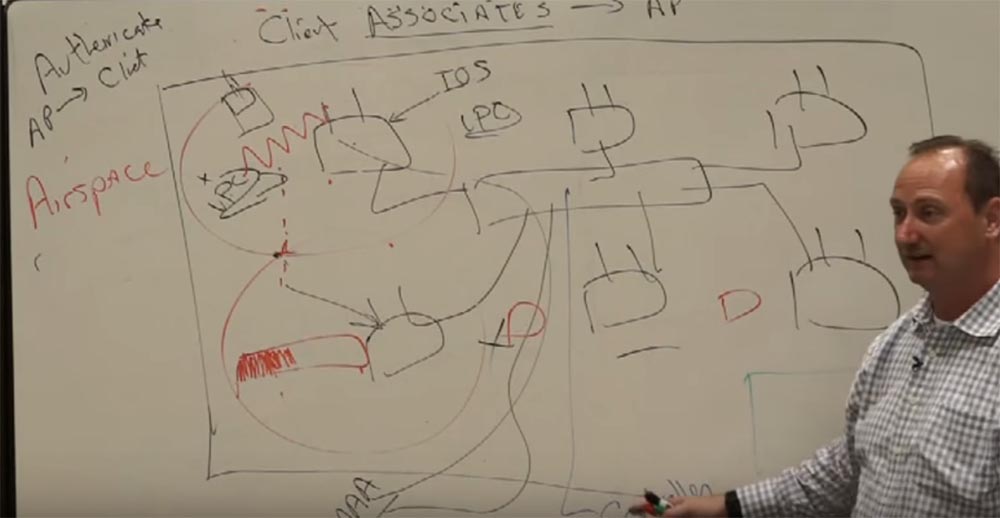
And the same with other access points. That is, instead of moving from one brain to another and so on, I will move from one finger to another, and these fingers will belong to one common brain. We created this and before we had 50 milliseconds that went to switch, today we reduced this time to 8. Today, even video calls work smoothly for us. All thanks to these simplified access points.
When we had not bought this company yet, we thought that simplified access points were terrible, but then we realized that it was a great idea. I don’t even know if this process of transition to simplified points can be considered an upgrade, because at first there were smart access points, and now there are not the smartest access points, but with a controller. We had to do this because the rules of the game have changed. We have moved from the world of data to the world of voice and video. People really needed this for business reasons. Wireless networks are already firmly embedded in their business processes. That is why in our case, in the case of this technology - the simpler the better. We use simplified access points with controllers, which can be very small, for example 50 access points, or simply huge for 1000 access points and more, depending on your needs.
Now let's talk about BYOD (bring your own device) again, we discussed this concept earlier here . I believe BYOD is the easiest way to communicate with the client about anything. I really like to conduct such conversations with clients and bring them to the solution I need. What does this concept mean for your customer? The ability to bring your devices anywhere and have access to information.
Is there any security concern about this? Yes, of course. We at Cisco can have up to 16 VLANs per access point. We can give them priorities and distribute traffic in accordance with priority. In this case, wireless can be compared to hubs.
Imagine that I am an access point, and you are all my clients, which can be iPhones and iPads, others can be computers or something else, and I can give them all the priorities. I choose who will speak. The wireless network resembles a walkie-talkie. Remember the walkie-talkie? People still use them, and I, too, when I go hunting. But how do we use the walkie-talkie? We press the button to say something, then release it, but why? Because if both people speak at the same time, nothing will come of it.
The same situation with the wireless network. If someone wants to send something, he kind of raises his hand and says, I have a request. You, say, a computer and here the phone also raises a hand. I will say, hey, computer, you have to wait, and give the phone a higher priority so that the call takes place, which is determined by QoS. We can do this, it is part of our portfolio. This is the difference between your home network and commercial.
So, you can have 16 VLANs and a controller for operation, but now we have your devices and you need to determine, thanks to priorities, which devices can be connected and how. To do this, we have a backend ISE (Cisco Identity Services Engine) - an identification service.
This is actually one of our latest services. The objective of this service is to give people the opportunity to register their device. If we allow people to bring their gadgets, that's cool. But so that they can do whatever they want, they need to register their device. We need to know what this device is. We don’t want to let anyone get into our network.
So, you can register the device and ask to specify any parameters that you want. Time of day, place, application, but so far we can’t request the color of the person’s t-shirt. Imagine that you are our new employee and you want to bring your iPad with you. It will be important for your work as well as your iPhone and computer. We will say - no problem, we will create your profile and you will be able to bring an iPad. But if we refuse, you will not get into the network.
Is it important for customers now? Of course. We cannot forbid people to bring their gadgets, but we can control this process and limit our vulnerability. The integration between the controller and ISE is very smooth. This is the latest service designed exclusively for this task and for this new wave of mobility.
How about troubleshooting? What do you think IT people thought when we first introduced wireless technology to them? They hated them. Why did they hate wireless technology? I had a client who said: “I don’t need wireless networks, I don’t want to see them at home.” And that was the desktop support manager. He said, “Can you imagine how many extra calls I will receive?”
This is happening now. Monday morning, at five to nine, someone has a meeting at exactly 9 a.m. “My computer worked perfectly wirelessly on Friday, and now it’s not working and this needs to be fixed urgently.” A support officer asks what has changed. And they answer him that nothing. “I turned off the computer and went home.” - "True"? -"Yes". They finally manage to get into the computer and see what is there and they see 6 different networks, a running game and then they are told: "Well, maybe my son played a little with him at home." Could this have been prevented? No. It has many advantages in the business and cultural fields.
It's all about culture. Someone said - if you want to get BYOD support, give the leader an iPad and just wait. Just be patient and he will impose it by force.
So, what about troubleshooting? We need a way to troubleshoot. What is the history of Cisco in network management? We had many management products, applications. And what is our reputation among clients in this matter? Not very good, not very. Cisco has a lot of network resource management tools and I’ll tell you that they all suck. This is a technical term.
Prime is the first network manager I would recommend to my clients. He is really good. But Prime is not a Cisco innovation. We got it from the very Airspace company we bought. Prime allows us to look at access points, switches or routers to which they are connected, the controller and ISE. So, if someone calls and says that they cannot connect to the network, I can say: “Wait a minute, where exactly are you?” - "Oh, now I see, it seems that you are shining in the home network, not in ours, I can see it from here." “Okay, I need to use Blizzard.” “So, it still doesn't work.” - "It seems that you are not authenticated, because the login was not recognized, the password is incorrect." We will always need functions outside SNMP, and if you want to download MIBS, you can do it,
We at Cisco work with many wireless networks at home. One of them is Blizzard, distributed throughout our offices. Hurricane is already a new network, we are gradually migrating people to it. There is also a separate network for Jabber, for those who use Jabber for video and voice.
Wireless networks are not rocket science, as I said. You will not be able to fulfill your plan only through the sale of wireless services. But this is the tool that will pull along with everything else thanks to BYOD.
I have a friend from the sales department, Mike, and he says: "I will never fulfill my quota for the sale of wireless networks only at the expense of wireless networks, but I can achieve a plan if I sell them in all my transactions." It used to be a kind of supplement, now it is already ahead. Now wireless networks are pulling switches, network management and everything else. It’s like the tip of a spear, which serves to puncture, because not with the help of a pole we pierce the spear, but with the sharp end. Thanks to the SNMP protocol, I can manage devices of any production, as this is a standard protocol. I can then download additional MIBs to unlock the necessary accessibility features. You will have to pay for the MIBs to gain access.
And again I remind you that we are talking about a security system, but this is also an AAA server. There were two access control products - NAG (Network Admissions Control) and ACS from Cisco. And we combined these two products together. Now Prime will be able to follow everything that happens here and here and anywhere on the network.
And now back to what our customers will do on these devices. I used to have 2 devices, but what do I have now? I have an iPad, what can I do on it? What can I do on the iPad if I take it with me? I want to use mail, that is, use data applications. What else? Video. Can I watch high definition video? Yes. Will all of these my tasks make the network do more work?
Now we are not talking about Medianet, switches and routers, but about WLAN. What has changed for WLAN, for wireless networks? To begin with, how many options do I have? Can I use wired and wireless network for iPad? Not. And what does this mean for me? That the wireless network must be reliable. After all, this is the only possible connection for me. I can’t say that the wireless connection is not working, give me a cable. This will not work, so network availability should increase. Therefore, one of the main functions will be the availability of these access points, and their ability to eliminate interference. Do you think there will be more or less wireless devices on the network? Of course more. What can interfere with a wireless network? Not only other wireless devices, but also microwaves. Do you know how microwaves work? They use frequencies, to make the molecules rub against each other. So there is heat and so the food heats up. This frequency is 2.4 gigahertz. The same frequency as that used by us. But we use 100 milliwatts, and microwave ovens 1,500 watts. That is, we are slowly preparing you using wireless networks. This is a joke, I didn’t say it seriously.
What about bluetooth? All these headsets sticking out of people's ears. Recently, I often use a taxi and taxi drivers begin to mumble something and I ask again and it turns out that they are not talking with me, but with their own thing in their ears. Can Bluetooth interfere with the wireless network? Yes. In a call center, when many people use wireless devices, this can be especially noticeable due to the large interference. You can go to this place and the video will not work for you. And all because of interference.
How to prevent this? We need access points to be able to see these interference on certain communication channels and to be able to leave them, add more intelligence to them. This feature is called Clean Air.
Cisco bought the whole company, which was engaged in only one task - spectral analysis, and nothing more. Had to pay hundreds of millions of dollars for a company that did just that. Then we put this function on the chip and put it in our access points. Our access points can operate in two frequency ranges of 2.4 and 5 gigahertz. They can choose the best channel and go to it and drag and drop customers.
Wireless networks have spectra of 2.4 and 5 gigahertz. There is a difference between them. Which one is the oldest? Which do we use longer? The first, 2.4 GHz, is older. How many channels are there on it? 13. Can we use them all at once? Not. But if we write all the channels and imagine that I am at 1, and someone else at 3, will we interfere with each other? Yes. In this spectrum there are only 3 channels that do not overlap each other.

These are channels 1, 6, and 11 for the United States. That is, it turns out that I can only place three access points in this room here. What about 5 gigahertz? Are there more channels here that don't overlap? How many channels are there? 23 at the moment. It used to be 18, now 23. And how many of them do not overlap? 20 approximately. That is, you have 20 independent channels. Good opportunities for their bonding (combining) in order to obtain greater bandwidth. Which of these spectral ranges has the best predictions for the future?
Continuation:
FastTrack Training. "Network Basics." "The Basics of Wireless LAN." Part two. Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
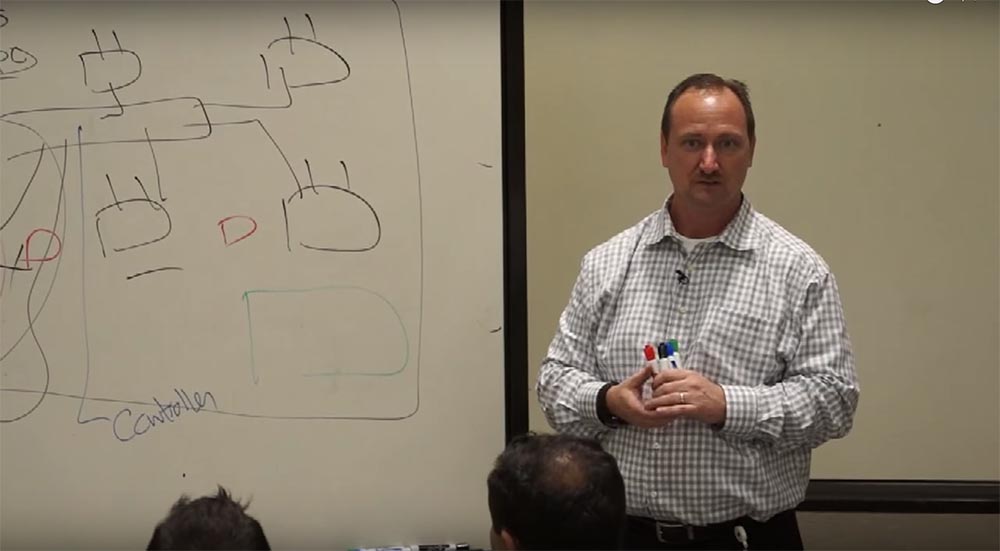
We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “Fundamentals of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Fundamentals”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the eighth of them.
FastTrack Training. "Network Basics." "The Basics of Wireless LAN." Part one. Eddie Martin December 2012
So, the next thing we'll talk about is a wireless local area network. We will start with the basics.
It is simply unbelievable that we are talking about this now, because among us there are those who do not even remember the times when the networks were only wired. There is nothing wrong with being young; I would never blame someone for being too young. I will envy, but I will not blame.
But just imagine that there was a time when we were all tied to wired networks. I remember exactly those times. But now I can’t tell you exactly when I last connected the laptop by wire. I cannot do this. I could use a USB connection, but definitely not a wired network.
We cannot completely get rid of wired networks, for example, in data centers. Wireless bandwidth will not be enough for you to replace 10 gigabit or 40 gigabit networks. It will take a lot of time.
But let's think about a wireless network in terms of how it has changed our world. Wireless networks have been in our service for a long time, remember the first cordless phones? They stood at our house. What frequency did they work at, you remember? 900 megahertz. They had good coverage, but what was wrong with them? What was wrong with these phones at home with a frequency of 900 megahertz? They were not protected. People could hear you. It’s good if the first one had such a phone, but then the neighbors appeared and they could get on your communication channel and hear you. I still have a couple of 900 megahertz speakers in my backyard that I use for all kinds of sports activities and more. And my neighbor across the road still has a phone operating at a frequency of 900 megahertz.
900 megahertz provide a large range, but low bandwidth. But you know, at that time we already had wireless networks operating at a frequency of 900 megahertz. They had a megabit of bandwidth, and it was already a revolution. Few knew about this, because this function was very unique and specialized. The frequencies crossed and people said no, I need something more secure. I do not want other people to hear me, so I want a frequency of 2.4 gigahertz.
And we switched to a free spectrum frequency, 2.4 GHz DSS (digital spread spectrum), digital spread spectrum. You may not have to worry that they will hear you and choose your channel for communication using the phone settings. But why didn’t we stay in that network? Why aren’t we still using it?
Yes, everyone just switched to this spectrum, we got interference. We no longer had the opportunity to listen to each other at this frequency, but the phones interfered with the normal operation of each other. And then we switched to another frequency. What frequency was that? 5 gigahertz. We switched to a new spectrum and the people began to catch up there. As a result, there were noises, and then a new spectrum appeared.
Not sure what frequency it worked at, possibly 1.9 GHz, but it was called Dect 6.0. It was outside the working range of all other devices and therefore, perhaps, was considered the most secure. These ranges have been filled. I will tell you that when in the late 90s we developed standards, and this was very important, there were many companies and they all had their own. There were their working frequencies, their expanded digital spectra. And they did not work with each other normally. Many thought - this is not part of my business, I will not do anything. Then came these standards.
I won’t say that Cisco invented wireless networks, but they acquired Era Net, the market leader at the time. They were the best engineers and developed the best technical solutions in this area. Cisco has become leaders in the field of wireless technology in an instant. It was a great time, then standards appeared and people began to use these technologies in business. But it turned out that we were not as smart as we thought.
What do you think happens when Cisco buys another company? First of all, we transfer all products to our operating system. When we bought Era Net, the first thing we did was give them our equipment, 350 series access points. And we upgraded their operating system to ours. We converted their software, their OSes, and got the smartest access point in the world. There was nothing that she would not do. Looking ahead, I’ll say that this was not the best solution at that stage.
Let's see what a wireless network is and tell you that it is not as difficult as it seems. I will draw the building, let it be the floor plan of the building. I have access points here.

And we have network users, computers, mobile phones and any other devices, no matter which. An access point is a gateway to a wired network. The process of getting into the network is a two-step process. But you can skip one of the steps if you want.

I'll explain now. The client is associated with an access point. It looks like this. The computer sees the wireless network, and says: "I want to connect." Imagine that we have three access points and one client. I say: "All three of you look the same for me, let me ask you a few questions." - “How many users do you have on the network”? - "And how much do you have"? - "And you"? “What is your disposal?” I can understand which of the access points suits me best, where there are fewer users, where the connection will be better, based on a survey of many access points. Then I choose, and I say: "I want to connect to you." How often do we connect to a network that was not created for us? Often. Why not connect to a neighbor’s network? It's free. So it is, agree. There is no protection here.
We pass to the second stage - authentication.

At this point, the access point polls the client. The network says, “Wait a minute, show me your credentials. “Then I will miss you.” This is the whole principle of wireless networks.
Do you have such authority at home? You have an SSID (service set identifier) translated as a wireless network name by a router that you can hide and you have a key that can consist of many letters, numbers or a phrase. At home, we have a network sharing key for authentication. I have many devices and one access key for them. Why is this not suitable in business?
Just imagine that 70 thousand people work in Cisco. Imagine that we would have a Blizzard username and password in Blizzard. You are not telling anyone. It's a secret. You take your laptop, log in, then leave it somewhere unattended and your login details are stolen. What will happen? I will have to change the login information on the remaining 60,999 computers. What really identifies you, how exactly you are is your username and password.
That is why business authentication will be different from home network authentication. We want to give you a unique username and password and a unique secure connection. Therefore, when you connect to the access point and she tells you - wait, give me your credentials, you are sent to the AAA server.

What kind of server is this?
These are three letters A, that is, authentication, authorization and accounting. We also sell these AAA servers. When you are hired by our company, you are immediately assigned your details to enter the network. Your login in the form of email and your first password. You log in and then immediately change the password. There you will immediately see the password requirements, for example, at least 8 letters, with capital letters, numbers, or something else. But we need all this in order to understand that it is you.
Customers are often used to saying that a wireless network is unsafe. But I explain that a wireless network can be much safer than a wired one. I could come to clients, connect my computer and immediately get to them on the network. Now to access the network you need to authenticate. It is the AAA server that tells us who you are when you connected and where you have access and when you disconnected. This is exactly what the AAA server does. When you have been given access, your request is sent to this server and you receive the first encryption key (encrypted key), each has its own unique encryption key. You have your own key, you have your own, and we give them out randomly. Everything is very safe. Any information coming from the computer is encrypted thanks to this key and the key is constantly changing.
I had a client who represented a savings and lending institution, and he came to talk to me and I began to tell him about wireless networks. His eyes literally popped out of his orbit when he heard about wireless networks. He shouted - we won’t have it, we are a financial institution. He literally wanted to pounce on me. I told him - hey, calm down. Put your eyes in place.
What do we say to a client who doubts the security of wireless networks? He will say - I do not need a wireless network, it is unsafe. What do you tell him? I don’t know about you, but I said: “Do you know where there are wireless networks”? If the access point didn’t hang so clearly in this office now, how could you understand this? Can you smell it, taste it, hear it? Not. You cannot understand if there is a wireless network here. You will need a device to find out.
There used to be such small access points, remember? I once did a training in Southern California at Long Beach at the Marriott Hotel. We were in a remote corner of this entire hotel complex, it wasn’t very well with a wireless network signal. As an instructor, I bought a wired connection. Everything was fine with my connection, but the students were furious. Communication lags, well, or how to say it technically. And what have I done? The next day I installed Lynksys, here you have access, stop whining and let's continue classes. I actually made an unauthorized connection with that network and no one ever said anything to me.
We will return to the client with eyes jumping out of the eye sockets. I asked him: “How do you know that you do not have a wireless network”? My account manager, of course, then kicked me for it with his sharp boots. Kicked right in the shin and it was encouraging. And guess how it all ended? We sold to that client access points that performed a single function - they protected against intrusion into the network. He was afraid that someone behind the firewall would connect the wireless network and what did we do? We set up a wireless network to prevent wireless connectivity.
There are no security documents that would not include wireless networks, even then in 2003, 2004 or 2005. Today you need to have protection through a wireless connection.
Let's get back to my story. We placed our operating system on the devices and created the smartest access points in the world. Imagine that I have a meeting here.

I take my computer and start wandering around with it. I go from here to here, from one point to another and this is called roaming. This is similar to what you do with your cell phones. Points have a radius, and so on. At this point, my computer understands that neither this access point gives me the desired signal level, nor the other. Imagine that I am showing a presentation in PowerPoint, because I'm still at a Cisco meeting. That is, I have a download. What will happen to this download?

It will stop for a second while I reconnect from one access point to another. She stops for a second and continues on.
We have the opportunity to do this and the customers are thrilled. They liked our limitless roaming. The same thing will happen between these access points and between others.
Everything was nowhere better, but then Cisco began to sell other products. We released phones, Spectral link - these were the first phones that we connected here. We were able to start transmitting voice wirelessly. And then the problems began.

So, let's talk about phones. We put here a special VLAN called Voice Net. Suppose I work for Blizzard here and want to put all my voice devices on Voice Net. Give them greater priority, greater bandwidth, the ability for voice transmission to go perfectly. I'm just thrilled and plug in these devices. The voice is connected to Voice Net, I myself am to Blizzard, everything works fine, I upload my file, I begin to move around the room. And when I start walking and find myself at about this point, my wife calls. Hello dear, how are you? Want to tell me what I did wrong today? Let me cancel my meeting, and you continue? The conversation takes place at this point.

I start walking and talking with my wife, and what happens when I find myself on the edge of the networks? My conversation will be interrupted. The conversation is interrupted, although the failure is only 1 second. And I find myself in the zone of another access point. My wife calls me back. She says, “Have you dropped me?” “No, what are you, it's all technology.” “It's all wireless technology.” “You don’t have to blame the technology, you geeks are always talking about them all the time.” Then I go out of this network and do not call back, let him leave me a voice message. I'm already done, no chance. Just one second of stopping and switching to another network is 20 lifespan for a phone call.
The problem was that the device was too smart, it knew everything about the network. And this device was so smart that it also knew everything about the network. And it took them both a second to realize that they were both not together at that moment and my call was interrupted.
And here Cisco found a way out of the situation. This required the Catalyst 6500, a supervisor for 40 thousand dollars, a line card for 45 thousand dollars, 20 hours of work for the engineers who organized all these tunnels on the network. Not the best solution. Cisco has such small cards that we are distributing, and one of them says - no worship of technology. And we had to buy another company to solve this issue. After all, sometimes there are situations when being smart is not so smart.
So, Cisco bought Airspace. It was a great acquisition for Cisco, because at that moment we decided - let's not make access points smart. Let's make them simplified or, in other words, stupid. Some started calling them dumb. Instead of installing all the features on all access points, I will install them in one place - in the controller. I will put a new device on the network. This controller will be the brain center of all access points. This point used to have its own brain, but now it is not there. He is in the controller.

And the same with other access points. That is, instead of moving from one brain to another and so on, I will move from one finger to another, and these fingers will belong to one common brain. We created this and before we had 50 milliseconds that went to switch, today we reduced this time to 8. Today, even video calls work smoothly for us. All thanks to these simplified access points.
When we had not bought this company yet, we thought that simplified access points were terrible, but then we realized that it was a great idea. I don’t even know if this process of transition to simplified points can be considered an upgrade, because at first there were smart access points, and now there are not the smartest access points, but with a controller. We had to do this because the rules of the game have changed. We have moved from the world of data to the world of voice and video. People really needed this for business reasons. Wireless networks are already firmly embedded in their business processes. That is why in our case, in the case of this technology - the simpler the better. We use simplified access points with controllers, which can be very small, for example 50 access points, or simply huge for 1000 access points and more, depending on your needs.
Now let's talk about BYOD (bring your own device) again, we discussed this concept earlier here . I believe BYOD is the easiest way to communicate with the client about anything. I really like to conduct such conversations with clients and bring them to the solution I need. What does this concept mean for your customer? The ability to bring your devices anywhere and have access to information.
Is there any security concern about this? Yes, of course. We at Cisco can have up to 16 VLANs per access point. We can give them priorities and distribute traffic in accordance with priority. In this case, wireless can be compared to hubs.
Imagine that I am an access point, and you are all my clients, which can be iPhones and iPads, others can be computers or something else, and I can give them all the priorities. I choose who will speak. The wireless network resembles a walkie-talkie. Remember the walkie-talkie? People still use them, and I, too, when I go hunting. But how do we use the walkie-talkie? We press the button to say something, then release it, but why? Because if both people speak at the same time, nothing will come of it.
The same situation with the wireless network. If someone wants to send something, he kind of raises his hand and says, I have a request. You, say, a computer and here the phone also raises a hand. I will say, hey, computer, you have to wait, and give the phone a higher priority so that the call takes place, which is determined by QoS. We can do this, it is part of our portfolio. This is the difference between your home network and commercial.
So, you can have 16 VLANs and a controller for operation, but now we have your devices and you need to determine, thanks to priorities, which devices can be connected and how. To do this, we have a backend ISE (Cisco Identity Services Engine) - an identification service.
This is actually one of our latest services. The objective of this service is to give people the opportunity to register their device. If we allow people to bring their gadgets, that's cool. But so that they can do whatever they want, they need to register their device. We need to know what this device is. We don’t want to let anyone get into our network.
So, you can register the device and ask to specify any parameters that you want. Time of day, place, application, but so far we can’t request the color of the person’s t-shirt. Imagine that you are our new employee and you want to bring your iPad with you. It will be important for your work as well as your iPhone and computer. We will say - no problem, we will create your profile and you will be able to bring an iPad. But if we refuse, you will not get into the network.
Is it important for customers now? Of course. We cannot forbid people to bring their gadgets, but we can control this process and limit our vulnerability. The integration between the controller and ISE is very smooth. This is the latest service designed exclusively for this task and for this new wave of mobility.
How about troubleshooting? What do you think IT people thought when we first introduced wireless technology to them? They hated them. Why did they hate wireless technology? I had a client who said: “I don’t need wireless networks, I don’t want to see them at home.” And that was the desktop support manager. He said, “Can you imagine how many extra calls I will receive?”
This is happening now. Monday morning, at five to nine, someone has a meeting at exactly 9 a.m. “My computer worked perfectly wirelessly on Friday, and now it’s not working and this needs to be fixed urgently.” A support officer asks what has changed. And they answer him that nothing. “I turned off the computer and went home.” - "True"? -"Yes". They finally manage to get into the computer and see what is there and they see 6 different networks, a running game and then they are told: "Well, maybe my son played a little with him at home." Could this have been prevented? No. It has many advantages in the business and cultural fields.
It's all about culture. Someone said - if you want to get BYOD support, give the leader an iPad and just wait. Just be patient and he will impose it by force.
So, what about troubleshooting? We need a way to troubleshoot. What is the history of Cisco in network management? We had many management products, applications. And what is our reputation among clients in this matter? Not very good, not very. Cisco has a lot of network resource management tools and I’ll tell you that they all suck. This is a technical term.
Prime is the first network manager I would recommend to my clients. He is really good. But Prime is not a Cisco innovation. We got it from the very Airspace company we bought. Prime allows us to look at access points, switches or routers to which they are connected, the controller and ISE. So, if someone calls and says that they cannot connect to the network, I can say: “Wait a minute, where exactly are you?” - "Oh, now I see, it seems that you are shining in the home network, not in ours, I can see it from here." “Okay, I need to use Blizzard.” “So, it still doesn't work.” - "It seems that you are not authenticated, because the login was not recognized, the password is incorrect." We will always need functions outside SNMP, and if you want to download MIBS, you can do it,
We at Cisco work with many wireless networks at home. One of them is Blizzard, distributed throughout our offices. Hurricane is already a new network, we are gradually migrating people to it. There is also a separate network for Jabber, for those who use Jabber for video and voice.
Wireless networks are not rocket science, as I said. You will not be able to fulfill your plan only through the sale of wireless services. But this is the tool that will pull along with everything else thanks to BYOD.
I have a friend from the sales department, Mike, and he says: "I will never fulfill my quota for the sale of wireless networks only at the expense of wireless networks, but I can achieve a plan if I sell them in all my transactions." It used to be a kind of supplement, now it is already ahead. Now wireless networks are pulling switches, network management and everything else. It’s like the tip of a spear, which serves to puncture, because not with the help of a pole we pierce the spear, but with the sharp end. Thanks to the SNMP protocol, I can manage devices of any production, as this is a standard protocol. I can then download additional MIBs to unlock the necessary accessibility features. You will have to pay for the MIBs to gain access.
And again I remind you that we are talking about a security system, but this is also an AAA server. There were two access control products - NAG (Network Admissions Control) and ACS from Cisco. And we combined these two products together. Now Prime will be able to follow everything that happens here and here and anywhere on the network.
And now back to what our customers will do on these devices. I used to have 2 devices, but what do I have now? I have an iPad, what can I do on it? What can I do on the iPad if I take it with me? I want to use mail, that is, use data applications. What else? Video. Can I watch high definition video? Yes. Will all of these my tasks make the network do more work?
Now we are not talking about Medianet, switches and routers, but about WLAN. What has changed for WLAN, for wireless networks? To begin with, how many options do I have? Can I use wired and wireless network for iPad? Not. And what does this mean for me? That the wireless network must be reliable. After all, this is the only possible connection for me. I can’t say that the wireless connection is not working, give me a cable. This will not work, so network availability should increase. Therefore, one of the main functions will be the availability of these access points, and their ability to eliminate interference. Do you think there will be more or less wireless devices on the network? Of course more. What can interfere with a wireless network? Not only other wireless devices, but also microwaves. Do you know how microwaves work? They use frequencies, to make the molecules rub against each other. So there is heat and so the food heats up. This frequency is 2.4 gigahertz. The same frequency as that used by us. But we use 100 milliwatts, and microwave ovens 1,500 watts. That is, we are slowly preparing you using wireless networks. This is a joke, I didn’t say it seriously.
What about bluetooth? All these headsets sticking out of people's ears. Recently, I often use a taxi and taxi drivers begin to mumble something and I ask again and it turns out that they are not talking with me, but with their own thing in their ears. Can Bluetooth interfere with the wireless network? Yes. In a call center, when many people use wireless devices, this can be especially noticeable due to the large interference. You can go to this place and the video will not work for you. And all because of interference.
How to prevent this? We need access points to be able to see these interference on certain communication channels and to be able to leave them, add more intelligence to them. This feature is called Clean Air.
Cisco bought the whole company, which was engaged in only one task - spectral analysis, and nothing more. Had to pay hundreds of millions of dollars for a company that did just that. Then we put this function on the chip and put it in our access points. Our access points can operate in two frequency ranges of 2.4 and 5 gigahertz. They can choose the best channel and go to it and drag and drop customers.
Wireless networks have spectra of 2.4 and 5 gigahertz. There is a difference between them. Which one is the oldest? Which do we use longer? The first, 2.4 GHz, is older. How many channels are there on it? 13. Can we use them all at once? Not. But if we write all the channels and imagine that I am at 1, and someone else at 3, will we interfere with each other? Yes. In this spectrum there are only 3 channels that do not overlap each other.

These are channels 1, 6, and 11 for the United States. That is, it turns out that I can only place three access points in this room here. What about 5 gigahertz? Are there more channels here that don't overlap? How many channels are there? 23 at the moment. It used to be 18, now 23. And how many of them do not overlap? 20 approximately. That is, you have 20 independent channels. Good opportunities for their bonding (combining) in order to obtain greater bandwidth. Which of these spectral ranges has the best predictions for the future?
Continuation:
FastTrack Training. "Network Basics." "The Basics of Wireless LAN." Part two. Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
