“Do not get in, kill!” Or the whole truth about the safety of ICS. Part 2
Somewhere thanks to an independent initiative of the organization, somewhere due to the active actions of the state in terms of regulating the issues of protecting industrial control systems and the critical infrastructures of the Russian Federation, in most companies at least one of the processes is currently running:
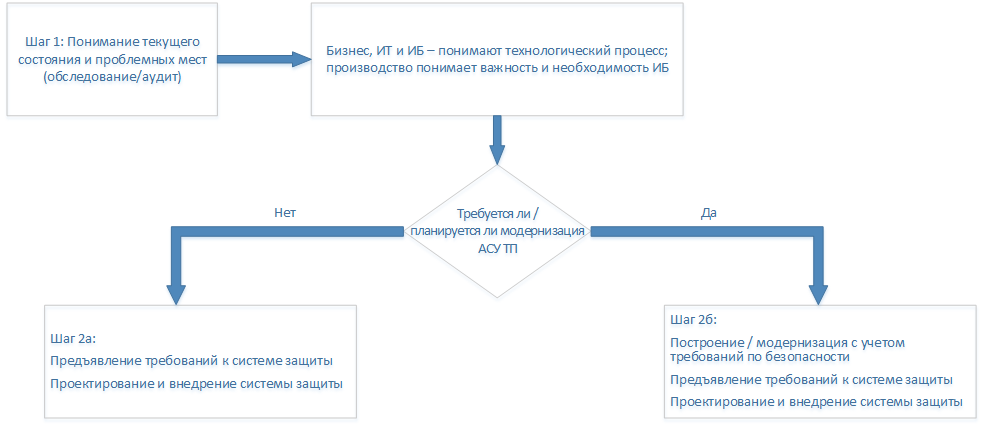
Regardless of the movement along these stages, activities can be carried out on the side of the Customer that can slightly increase security, but at the same time do not require large expenses. For example, setting up and using authentication where it is provided but not used, and where its use does not affect the process.

One of such steps can also be coverage of production and technological networks with passive monitoring.
First of all, we are talking about monitoring segments of the interface between corporate and technological networks, complementing the monitoring of corporate infrastructure.
Further, as far as possible and ready, the customer carries out monitoring at the top level of industrial control systems - for operator, dispatch and engineering workstations, industrial SCADA servers with system-wide and application software installed on them, as well as the corresponding network telecommunication equipment (switches, routers, internetwork screens, etc.).
In conjunction with monitoring the corporate network and the perimeter of the organization, no matter how vague it may be, these actions allow you to identify problems in a timely manner and, as a result, increase the level of security of process control systems. By detecting atomic incidents in a corporate network, for example, a compromise of a 0-day end host by malware or privilege escalation in a domain network, we see a potential attacker even before he moves and penetrates the ICS. And in fact, we prevent possible penetrations and incidents in technological segments due to timely response on the side of the Customer.
At the same time, any malicious ligaments in the network interface segment and in the industrial control system are under similar control. As an example, atomic incidents of changing the configuration of border / segmenting equipment, any incidents on the host from which the corresponding changes are being made, or on the host for which the configuration is being changed, indicate a potential violation of access and potential malicious actions directed directly to the ICS.
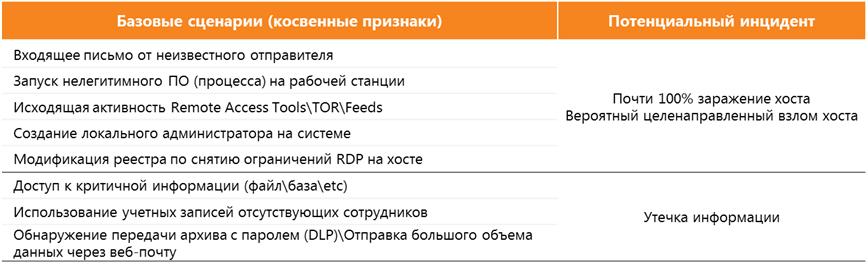
Things are somewhat different with lower levels of process control systems. So, programmable logic controllers and other hardware with installed software that receive data from the lower level, transmit data to the upper level and form control commands, can also potentially act as event sources for the monitoring center.
Integration with them is a rather complicated but feasible task. However, when immersed in lower levels, there is always a need for deep study of completely individual monitoring and analysis scenarios. And in this case, one should proceed from the specifics of the technological process, the specific and justified needs of the Customer and the corresponding possibilities for using SIEM. As a result of which it is often advisable to use specialized tools and solutions on the side of the Customer that provide access to relevant information from devices of the middle and lower levels without working directly with them.
It is worth saying that now on the market there are a number of offers of information protection tools for ACS TP segments. Both from vendors of industrial control systems, and from vendors of various IT and information security products. Regardless of the type and purpose of these funds, the requirement to register events de facto is mandatory for them. As a result, any of the possible remedies becomes an additional source for receiving and correlating events in the monitoring center.
Of course, monitoring and identification alone is not enough, and it in no way replaces or solves all the tasks of providing IS ACS TP, being a necessary but not sufficient condition for providing IS in ACS TP.
APCS Safety Approach - A simplified block diagram of possible movement.
In the case of expanding the monitoring service at ICS, we fall into one of the above ongoing activities on the side of the Customer, but none of them is an obstacle to the task of operational monitoring and identifying IS incidents.
So, for example, each of the possible schemes for interfacing corporate and technological networks (see the first part of the article ), including well-developed complex schemes for interfacing and segmenting, allows you to obtain information from closed production and technological segments. In this case, there is no risk of interruption of any of the services and processes within the corresponding closed segments, and there is no effect on the availability or integrity of the data.
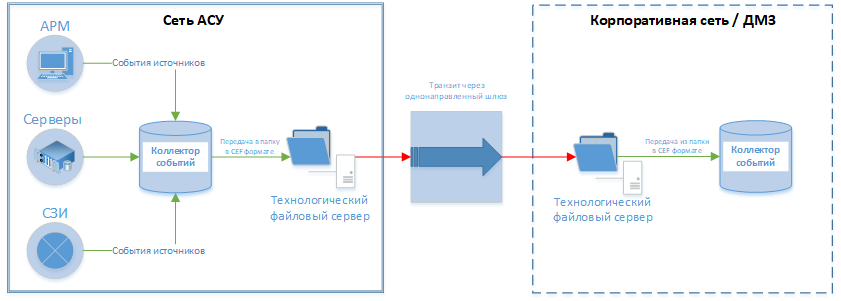
As an example, below is a possible scheme for connecting a closed segment to monitoring. And although it is far from ideal, at the same time it allows the customer to get the required level of service and result now, without waiting for the completion of the design and operation of the created interface segments and protection systems.
So, in a first approximation, the initial stage of a possible practical approach to providing information security in industrial control systems looks like. To a greater extent, it concerns the rapid provision of basic IS hygiene in matters of interfacing and the construction of ICS infrastructure. However, neither the approach nor our articles on such a complex topic as information security in automated process control systems end there. And in the future we plan to continue this series of publications with more practical examples and solved problems.
- Analysis of the current slice of the state of information security in industrial control system (audit).
- Design and construction of appropriate protection systems for industrial control systems.
- Or in addition to this - the construction or modernization of the automatic process control system itself, taking into account the relevant safety requirements.
Regardless of the movement along these stages, activities can be carried out on the side of the Customer that can slightly increase security, but at the same time do not require large expenses. For example, setting up and using authentication where it is provided but not used, and where its use does not affect the process.

One of such steps can also be coverage of production and technological networks with passive monitoring.
First of all, we are talking about monitoring segments of the interface between corporate and technological networks, complementing the monitoring of corporate infrastructure.
Further, as far as possible and ready, the customer carries out monitoring at the top level of industrial control systems - for operator, dispatch and engineering workstations, industrial SCADA servers with system-wide and application software installed on them, as well as the corresponding network telecommunication equipment (switches, routers, internetwork screens, etc.).
In conjunction with monitoring the corporate network and the perimeter of the organization, no matter how vague it may be, these actions allow you to identify problems in a timely manner and, as a result, increase the level of security of process control systems. By detecting atomic incidents in a corporate network, for example, a compromise of a 0-day end host by malware or privilege escalation in a domain network, we see a potential attacker even before he moves and penetrates the ICS. And in fact, we prevent possible penetrations and incidents in technological segments due to timely response on the side of the Customer.
An example of an incident in the ICS segment
Hackers managed to disable a blast furnace in Germany via the Internet
According to the Federal Information Security Bureau of Germany, the attackers gained access to the control panels of the ovens due to a phishing attack.
At the beginning of the attack, they sent out infected emails to office employees who were not involved in the production process. Having infected working computers located on the corporate network, hackers were later able to integrate into the control panel system of the plant, from which the automated line of furnaces was controlled.
As specified by German officials, the hack was not a one-off. The attack was a series of separate penetrations into the plant's systems, one of which ultimately led to the failure of the furnace shutdown mechanism.
The attack led to an incident in which one of the furnaces could not be turned off in the usual way. As a result, the furnace began to appear in the system as having an "undefined state". This led to significant damage throughout the production.
(From the report of the Federal Office for Security of Germany in the field of information technology).
Source . Translation .
Judging by its analysis, such penetration could be caught more than once in a corporate network until intruders penetrated the technological network and gained access to technological equipment.
According to the Federal Information Security Bureau of Germany, the attackers gained access to the control panels of the ovens due to a phishing attack.
At the beginning of the attack, they sent out infected emails to office employees who were not involved in the production process. Having infected working computers located on the corporate network, hackers were later able to integrate into the control panel system of the plant, from which the automated line of furnaces was controlled.
As specified by German officials, the hack was not a one-off. The attack was a series of separate penetrations into the plant's systems, one of which ultimately led to the failure of the furnace shutdown mechanism.
The attack led to an incident in which one of the furnaces could not be turned off in the usual way. As a result, the furnace began to appear in the system as having an "undefined state". This led to significant damage throughout the production.
(From the report of the Federal Office for Security of Germany in the field of information technology).
Source . Translation .
Judging by its analysis, such penetration could be caught more than once in a corporate network until intruders penetrated the technological network and gained access to technological equipment.
At the same time, any malicious ligaments in the network interface segment and in the industrial control system are under similar control. As an example, atomic incidents of changing the configuration of border / segmenting equipment, any incidents on the host from which the corresponding changes are being made, or on the host for which the configuration is being changed, indicate a potential violation of access and potential malicious actions directed directly to the ICS.

Things are somewhat different with lower levels of process control systems. So, programmable logic controllers and other hardware with installed software that receive data from the lower level, transmit data to the upper level and form control commands, can also potentially act as event sources for the monitoring center.
Integration with them is a rather complicated but feasible task. However, when immersed in lower levels, there is always a need for deep study of completely individual monitoring and analysis scenarios. And in this case, one should proceed from the specifics of the technological process, the specific and justified needs of the Customer and the corresponding possibilities for using SIEM. As a result of which it is often advisable to use specialized tools and solutions on the side of the Customer that provide access to relevant information from devices of the middle and lower levels without working directly with them.
It is worth saying that now on the market there are a number of offers of information protection tools for ACS TP segments. Both from vendors of industrial control systems, and from vendors of various IT and information security products. Regardless of the type and purpose of these funds, the requirement to register events de facto is mandatory for them. As a result, any of the possible remedies becomes an additional source for receiving and correlating events in the monitoring center.
Of course, monitoring and identification alone is not enough, and it in no way replaces or solves all the tasks of providing IS ACS TP, being a necessary but not sufficient condition for providing IS in ACS TP.

APCS Safety Approach - A simplified block diagram of possible movement.
In the case of expanding the monitoring service at ICS, we fall into one of the above ongoing activities on the side of the Customer, but none of them is an obstacle to the task of operational monitoring and identifying IS incidents.
So, for example, each of the possible schemes for interfacing corporate and technological networks (see the first part of the article ), including well-developed complex schemes for interfacing and segmenting, allows you to obtain information from closed production and technological segments. In this case, there is no risk of interruption of any of the services and processes within the corresponding closed segments, and there is no effect on the availability or integrity of the data.
As an example, below is a possible scheme for connecting a closed segment to monitoring. And although it is far from ideal, at the same time it allows the customer to get the required level of service and result now, without waiting for the completion of the design and operation of the created interface segments and protection systems.

So, in a first approximation, the initial stage of a possible practical approach to providing information security in industrial control systems looks like. To a greater extent, it concerns the rapid provision of basic IS hygiene in matters of interfacing and the construction of ICS infrastructure. However, neither the approach nor our articles on such a complex topic as information security in automated process control systems end there. And in the future we plan to continue this series of publications with more practical examples and solved problems.
