Get a neighbor’s Wi-Fi using standard MacOS tools
I have always been a fan of bugs and vulnerabilities “on the surface”, I have always envied the dudes who write exploits for the most secure operating systems, and I only knew how to script scripts (term from zero). However, my post about vulnerabilities in version control systems scored more than 1000 likes on Habr and remains the top1 post in the entire history of Habr, despite the fact that it was written 9 (!) Years ago.
And today I would like to show and tell on fingers about such a thing as wardriving. More precisely, how can standard passwords for MacOS get Wi-Fi neighbors. A hard one threw me into another apartment. Somehow, historically, I'm lazy. A couple of years ago I already wrote that my laziness, a new apartment and a Beeline wire (formerly Corbina) helped me find a bug at Beelineand have free internet on their network. “Today” is happening “like”, I’m in a new apartment, there’s not even a wire, but my neighbors have many networks.
Hesitating to spend mobile traffic, I decided that “neighbors need help”, and under “neighbors” I had to introduce myself ...
Once upon a time I was fond of wardriving, just before the moment I found Beeline wire in the old apartment) There there were also a lot of networks nearby and the first thing that came to mind was i need wi-fi. Many years have passed since then. Updating my data on wardriving, I found on the network a mention that 90% of the work of special utilities “today” can be made standard MacOS services. Looking ahead, I would like to note that I am not the author of this method, I myself found it on a foreign internet, just, say, this is a free translation and a detailed, artistic description of the way to get wi-fi passwords using standard makoshi methods, no more.
You need to understand that having a Wi-Fi-receiver, which is today in any laptop, you can "sniff" all the wireless traffic around you. Previously, when the networks were open, it was enough to come to the McDuck and in the evening you could get 100-200 acces to classmates. An open network + lack of https did the trick.
Now everything is more interesting, everyone is switching to https (taking this opportunity, I want to say hello to Lets Encypt . My favorite Lets Encypt, I’m on TV and say hello to you, thank you for being there) and even forgot about WEP, all routers use WPA2. But, as you know, the sword was invented before the shield, and no WPA2 is a hindrance to a person who is hungry for the Internet and sees a bunch of Wi-Fi near him.
Let's continue. Having a Wi-Fi card, i.e. any modern laptop, we can sniff traffic near us. But it is useless, because it is encrypted. The only thing that can be disassembled from it is metadata, such as the name of itp networks and “handshakes”, handshake, i.e. authorization of users on the network. They occur every time a user connects to a Wi-Fi network. For example, when a neighbor comes home and his smartphone in his pocket clings to home wi-fi.
If absolutely rude, handshakes are a regular hash like md5.
And yes, I lied in my first paragraph about “decryption”, this is a technical error and a substitution of concepts. Of course, it is impossible to decrypt the hash. This is how to say “taxi license”, knowing that taxi activity in the Russian Federation is not licensed. But just so convenient)
So here. All we need to do is find handshakes around the radio network around us and “decrypt” them. And before there was a bunch of software for all this. Someone knew how to correctly scan a radio channel, someone perfectly sniffed it into dumps, someone found hashes in dumps, someone knew how to break them. Now everything has become easier, thanks to Tim Cook. 90% of the work for third-party software is done by the standard Wireless Diagnostics application. Many saw him - when there is a problem with Wi-Fi, the poppy offers to check the network. A useless utility that gives advice such as "reboot the router." Well, i.e. it seemed to me)
So, let's go. Hold Alt and click on the Wi-Fi logo in the top panel. In general, Alt and click always open additional options in MacOS, but this is the topic of a separate topic.
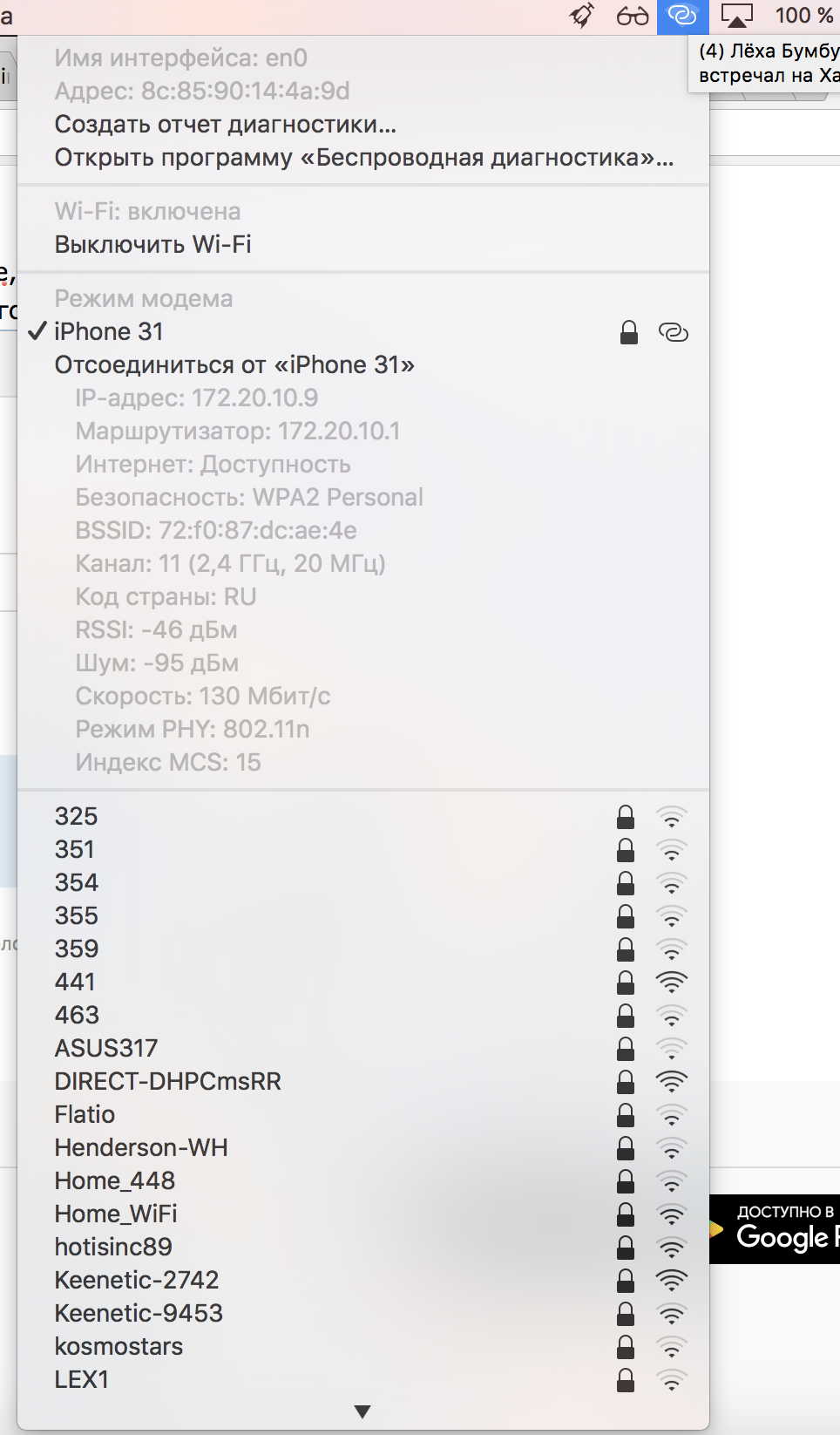
In addition to other additional info, which is sometimes very useful, we can launch the Wireless Diagnostics program. I think everyone who uses poppies remembers this window.
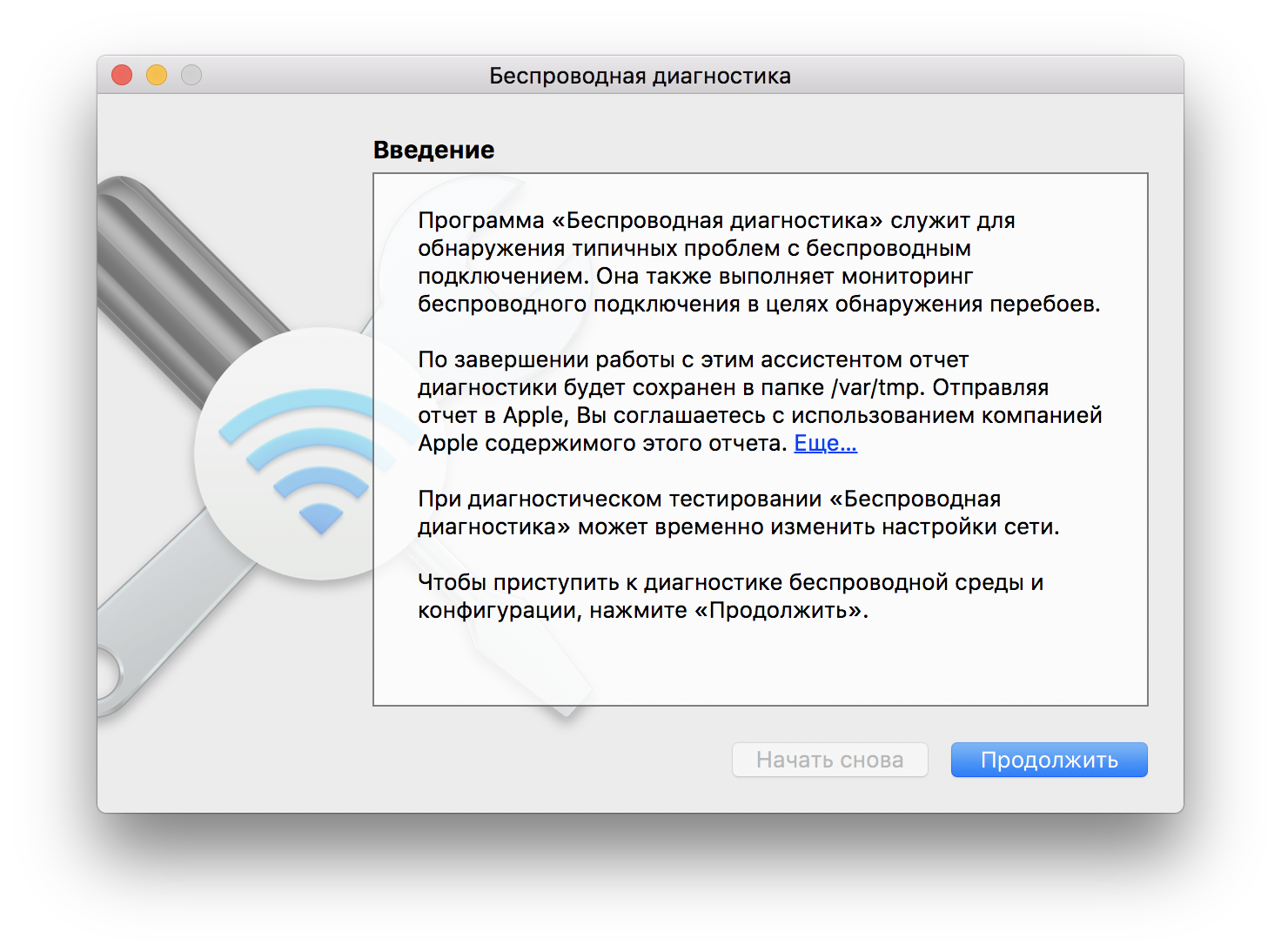
But we are interested in something else. Click on the menu item "Window" and see a set of additional utilities.

And right there is everything that is needed, even more) Specifically, we are interested in 2 points. Scanning and Analyzer. The first one will show us all the networks around with additional info, such as on which channel and at what frequency the network works. The second item will allow you to sniff traffic on a specific channel and frequency.
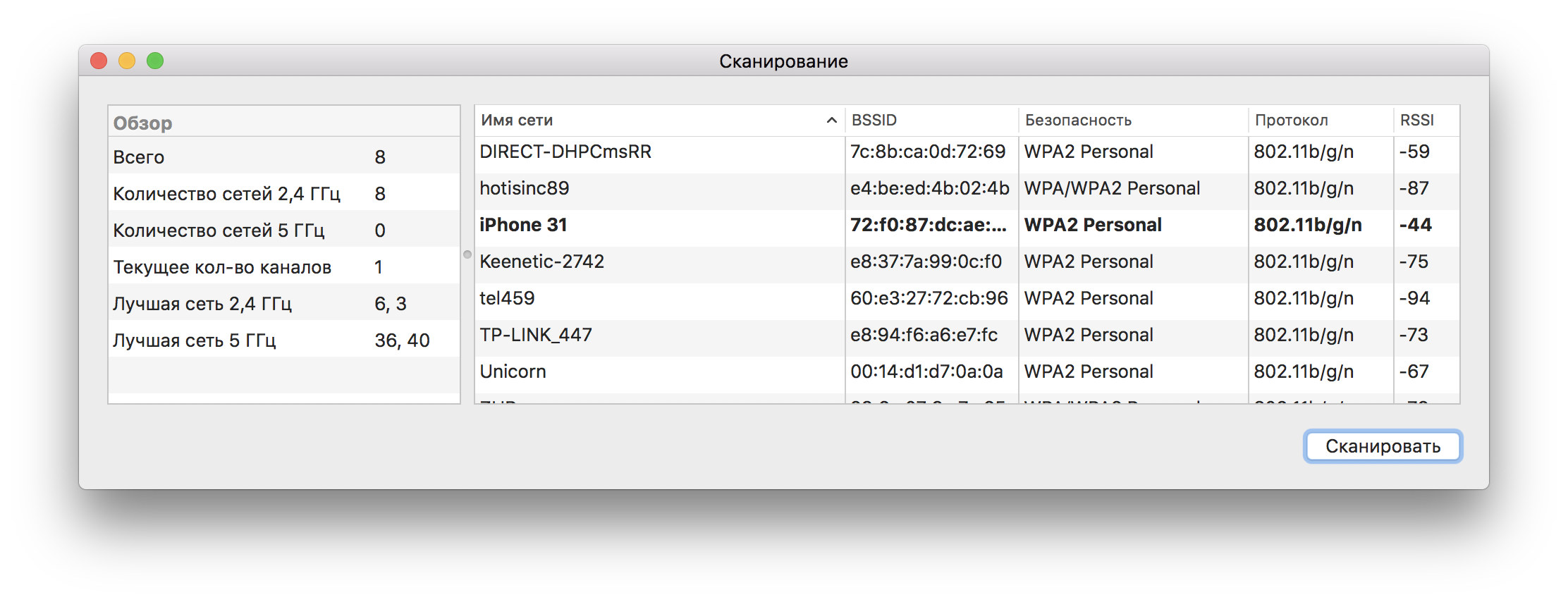

By clicking on the “Start” button in the Analyzer, the Wi-Fi card will switch to receive mode and start scanning the radio frequency around itself, the dump will be written to / var / tmp.
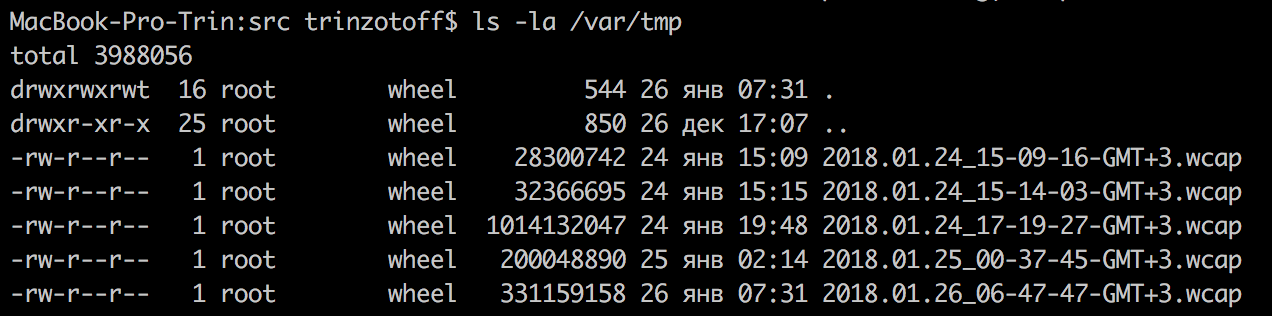
* .Wcap files are our dumps that contain traffic that is useless to us and the handshakes we need.
You have to understand that we need to catch handshakes. Those. we need to catch and sniff traffic when a neighbor comes home in the evening. Or, if you have another device on the makoshi, or any other axis, nukers will help you. Programs sending fake de-authentication commands. For example, JamWiFi . But this is straight if I can’t wait at all) In my experience, it is enough to simply start the Analyzer at 6 pm for an hour.
Next we need to put naive-hashcat andhashcat-utils .
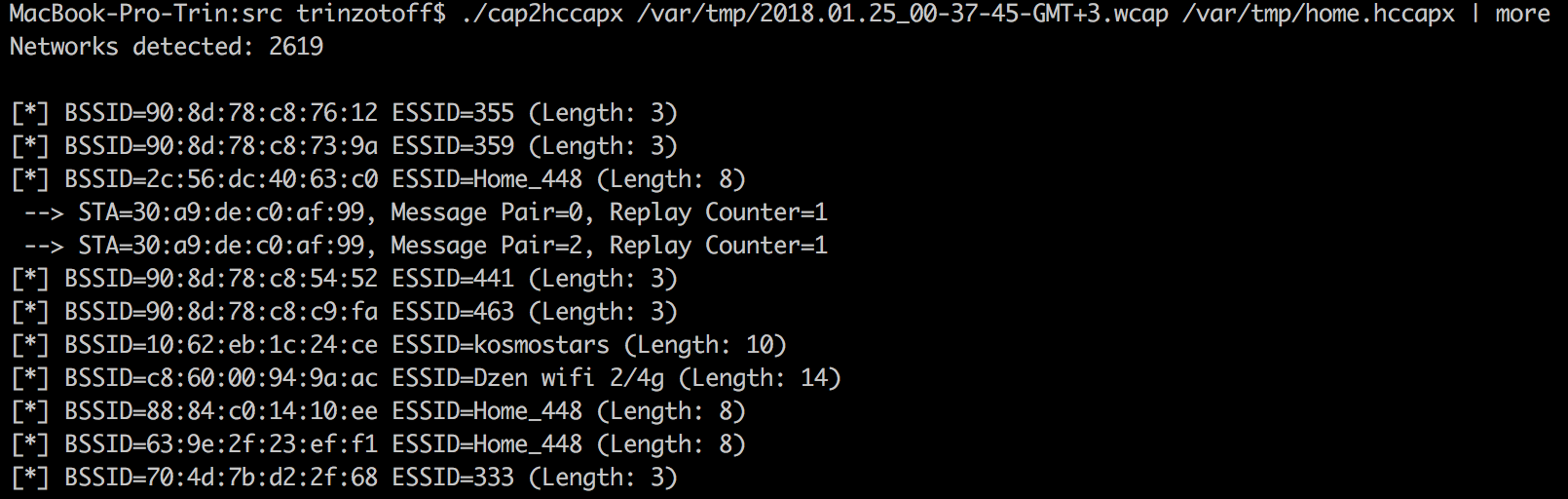
“Stop,” you say, “did you promise to break into the neighbor’s networks using standard methods?”) Ha! And did you believe me ?! In fact, we did 90% of the work through the GUI using standard methods. We already have hashes, all we need to do is break them. I'm sure everything can be done with standard utilities, but hashcat is easier to use. We collect software through brew or from sorts. First of all, we need to convert our dump, leaving only our hashes in it. The cap2hccapx binary from the package does this.
...

We see that we managed to intercept 2 handshakes, try to "break them." For this we need naive-hashcat:
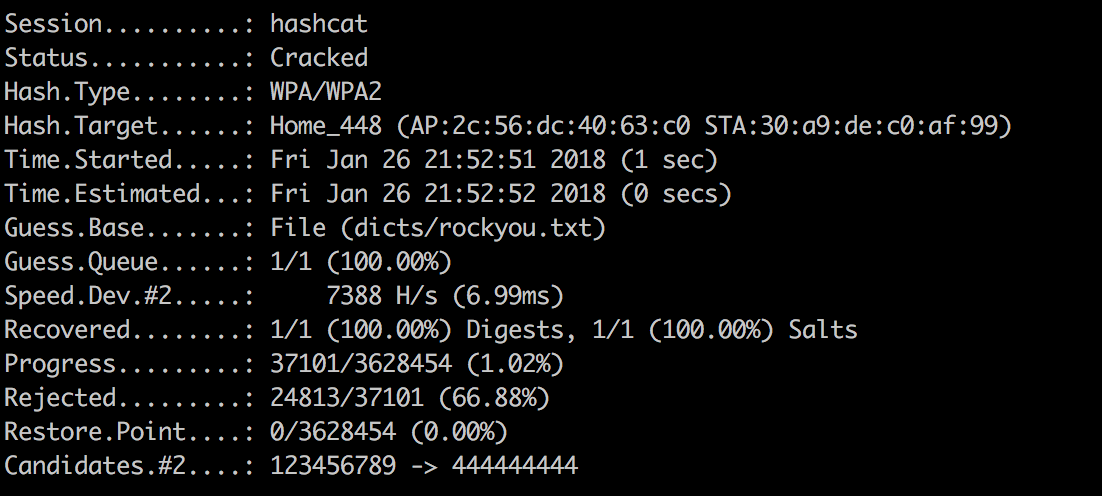
The cat went to work. On average, on my poppy, I have a speed of 2000 hashes per second, on the screen 7k, but this is only the start. Judging by this document , at 1080gtx you can get a speed of 400k hashes per second. However, I only have 2 handshakes and not such a big dictionary, so running through it was not a problem. We look at the file home-wifi.txt, voila:
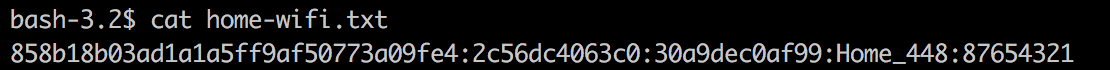
That's all. Unfortunately, this network is a few apartments from me and on another floor, ping is 7 seconds) We need to catch a neighbor from below or take an external wi-fi card with a normal antenna. But the principle, I think, is clear.
Successful scans to you, youngwarriors are served. And many thanks to the developers of Kali Linux MacOS for such gifts.
Well, you will find a lot more interestinghere .
And today I would like to show and tell on fingers about such a thing as wardriving. More precisely, how can standard passwords for MacOS get Wi-Fi neighbors. A hard one threw me into another apartment. Somehow, historically, I'm lazy. A couple of years ago I already wrote that my laziness, a new apartment and a Beeline wire (formerly Corbina) helped me find a bug at Beelineand have free internet on their network. “Today” is happening “like”, I’m in a new apartment, there’s not even a wire, but my neighbors have many networks.

Hesitating to spend mobile traffic, I decided that “neighbors need help”, and under “neighbors” I had to introduce myself ...
Once upon a time I was fond of wardriving, just before the moment I found Beeline wire in the old apartment) There there were also a lot of networks nearby and the first thing that came to mind was i need wi-fi. Many years have passed since then. Updating my data on wardriving, I found on the network a mention that 90% of the work of special utilities “today” can be made standard MacOS services. Looking ahead, I would like to note that I am not the author of this method, I myself found it on a foreign internet, just, say, this is a free translation and a detailed, artistic description of the way to get wi-fi passwords using standard makoshi methods, no more.
Neighbor Wi-Fi password mining principles
You need to understand that having a Wi-Fi-receiver, which is today in any laptop, you can "sniff" all the wireless traffic around you. Previously, when the networks were open, it was enough to come to the McDuck and in the evening you could get 100-200 acces to classmates. An open network + lack of https did the trick.
Now everything is more interesting, everyone is switching to https (taking this opportunity, I want to say hello to Lets Encypt . My favorite Lets Encypt, I’m on TV and say hello to you, thank you for being there) and even forgot about WEP, all routers use WPA2. But, as you know, the sword was invented before the shield, and no WPA2 is a hindrance to a person who is hungry for the Internet and sees a bunch of Wi-Fi near him.
Let's continue. Having a Wi-Fi card, i.e. any modern laptop, we can sniff traffic near us. But it is useless, because it is encrypted. The only thing that can be disassembled from it is metadata, such as the name of itp networks and “handshakes”, handshake, i.e. authorization of users on the network. They occur every time a user connects to a Wi-Fi network. For example, when a neighbor comes home and his smartphone in his pocket clings to home wi-fi.
If absolutely rude, handshakes are a regular hash like md5.
This is really rude. The key there is obtained by 4096 rounds of SHA1. To be precise, the formula is as follows: Key = PBKDF2 (HMAC − SHA1, passphrase, ssid, 4096, 256)thanks to jia3ep
By the way, you can notice that the name of the point is mixed up, therefore, with a unique name, the calculations do not help. And this is an argument for changing the name of the point to your own.
And yes, I lied in my first paragraph about “decryption”, this is a technical error and a substitution of concepts. Of course, it is impossible to decrypt the hash. This is how to say “taxi license”, knowing that taxi activity in the Russian Federation is not licensed. But just so convenient)
So here. All we need to do is find handshakes around the radio network around us and “decrypt” them. And before there was a bunch of software for all this. Someone knew how to correctly scan a radio channel, someone perfectly sniffed it into dumps, someone found hashes in dumps, someone knew how to break them. Now everything has become easier, thanks to Tim Cook. 90% of the work for third-party software is done by the standard Wireless Diagnostics application. Many saw him - when there is a problem with Wi-Fi, the poppy offers to check the network. A useless utility that gives advice such as "reboot the router." Well, i.e. it seemed to me)
We get passwords. Neighbors hang themselves;)
So, let's go. Hold Alt and click on the Wi-Fi logo in the top panel. In general, Alt and click always open additional options in MacOS, but this is the topic of a separate topic.

In addition to other additional info, which is sometimes very useful, we can launch the Wireless Diagnostics program. I think everyone who uses poppies remembers this window.

But we are interested in something else. Click on the menu item "Window" and see a set of additional utilities.

And right there is everything that is needed, even more) Specifically, we are interested in 2 points. Scanning and Analyzer. The first one will show us all the networks around with additional info, such as on which channel and at what frequency the network works. The second item will allow you to sniff traffic on a specific channel and frequency.


By clicking on the “Start” button in the Analyzer, the Wi-Fi card will switch to receive mode and start scanning the radio frequency around itself, the dump will be written to / var / tmp.

* .Wcap files are our dumps that contain traffic that is useless to us and the handshakes we need.
You have to understand that we need to catch handshakes. Those. we need to catch and sniff traffic when a neighbor comes home in the evening. Or, if you have another device on the makoshi, or any other axis, nukers will help you. Programs sending fake de-authentication commands. For example, JamWiFi . But this is straight if I can’t wait at all) In my experience, it is enough to simply start the Analyzer at 6 pm for an hour.
Next we need to put naive-hashcat andhashcat-utils .
“Stop,” you say, “did you promise to break into the neighbor’s networks using standard methods?”) Ha! And did you believe me ?! In fact, we did 90% of the work through the GUI using standard methods. We already have hashes, all we need to do is break them. I'm sure everything can be done with standard utilities, but hashcat is easier to use. We collect software through brew or from sorts. First of all, we need to convert our dump, leaving only our hashes in it. The cap2hccapx binary from the package does this.
# Качаем hashcat-utils
git clone https://github.com/hashcat/hashcat-utils.git
Cloning into 'hashcat-utils'...
remote: Counting objects: 403, done.
remote: Total 403 (delta 0), reused 0 (delta 0), pack-reused 403
Receiving objects: 100% (403/403), 114.23 KiB | 61.00 KiB/s, done.
Resolving deltas: 100% (257/257), done.
# Собираем бины
cd hashcat-utils/src/ && make
rm -f ../bin/*
rm -f *.bin *.exe
cc -Wall -W -pipe -O2 -std=gnu99 -o cap2hccapx.bin cap2hccapx.c
cc -Wall -W -pipe -O2 -std=gnu99 -o cleanup-rules.bin cleanup-rules.c
…
cc -Wall -W -pipe -O2 -std=gnu99 -o strip-bsr.bin strip-bsr.c
cc -Wall -W -pipe -O2 -std=gnu99 -o strip-bsn.bin strip-bsn.c
# Конвертируем дамп
./cap2hccapx.bin /var/tmp/2018.01.25_00-37-45-GMT+3.wcap /var/tmp/home.hccapx
...

We see that we managed to intercept 2 handshakes, try to "break them." For this we need naive-hashcat:
git clone https://github.com/brannondorsey/naive-hashcat
cd naive-hashcat
# Собираем софт для osx
./build-hashcat-osx.sh
# качаем вордлист для побора wpa/wpa2 сетей пароли (134MB)
curl -L -o dicts/rockyou.txt https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
# указываем адрес нашего дампа и файл, куда будем писать подобранные пассы, 2500 это метка хэшкэту, что надо ломать именно WPA, ну и запускаем naive-hashcat
HASH_FILE=/var/tmp/home.hccapx POT_FILE=home-wifi.txt HASH_TYPE=2500 ./naive-hashcat.sh

The cat went to work. On average, on my poppy, I have a speed of 2000 hashes per second, on the screen 7k, but this is only the start. Judging by this document , at 1080gtx you can get a speed of 400k hashes per second. However, I only have 2 handshakes and not such a big dictionary, so running through it was not a problem. We look at the file home-wifi.txt, voila:

That's all. Unfortunately, this network is a few apartments from me and on another floor, ping is 7 seconds) We need to catch a neighbor from below or take an external wi-fi card with a normal antenna. But the principle, I think, is clear.
Successful scans to you, young
Well, you will find a lot more interestinghere .
