Digital hygiene: rules of the game
Hello everyone, my name is Alexander Dvoryansky, I have been working as a commercial director for more than five years at Infosekury Company and today I want to talk with you about the basic principles of working with confidential information.
At one time, Canadian psychologist Elliot Jacks introduced the concept of "corporate culture". I allow myself to use the term "digital hygiene". This is the part of the corporate culture that determines what actions of employees and how they affect the company's information security.
I’ll draw a little attention to our industry, so that you understand why this topic is interesting to me. Infosecurity provides information security, system integration and consulting services. It is important for us to show that we can protect not only the data that customers trust us, but also their own information assets. Even a minor security incident in a cybersecurity company can strike its reputation. And to rise after such a blow is not easy.
So, the formation of digital hygiene in the company is affected by:
Today I’ll dwell on the first of these three whales - raising awareness, or, as it is now fashionable to say, avarnes.
In any self-respecting company, there are internal regulations, policies and methodologies about the rules for processing information of limited access. Alas, the mere existence of these documents does not give anything. Real protection is provided by employees who exactly follow the requirements specified in the documents. But where to find such ideal employees?
The trick is not to look for them, but, let's say, to grow them. The complex of training activities and materials allows you to create in the company a culture of working with information. If everything is right, the employees start to follow the IB rules at the reflex level - and you no longer need to worry that one of them does not block the computer screen, lose the token or forget the quarterly report in the printer tray.
First, divide your employees into groups and identify topics that are relevant to each group. Top managers are unlikely to be interested in exploring current software vulnerabilities, but for developers - very much so.
When topics are defined, think about the formats of educational materials: they also need to be personalized. For example, front-office employees do not have much free time, and sometimes there is no personal working computer. They will suit bright posters and short videos that can be placed and displayed in sales areas. And back-office employees can pay more attention to training, so it’s better to address e-courses and training mailings.
Another good practice is to check that your employees already know before conducting training in information security. The easiest way to do this is to test and send out phishing emails. So you will understand which topics need to pay more attention. And, of course, you shouldn’t forget about performance monitoring in the learning process and after it.
Let's start with the good old full-time study. In some way, it is irreplaceable: everyone knows that information is perceived much better when accompanied by live communication. Training can be carried out in the classical form or by the case method. In the second case, the instructor divides the students into groups, describes the problem that is relevant to the company, and invites each group to give and justify its own version of its solution. It is possible to combine two types of trainings: conduct an introductory for employees on their first working day, and case training - monthly or quarterly.
Distance learning is a worthy competition to full-time, and in the future, most likely, will completely pull the blanket over himself. Electronic courses, videos, mailings and online games are good because employees can view them on different types of devices at a convenient time. And they also provide an opportunity to boast to competitors with the words “gamification” and “micro-education”.
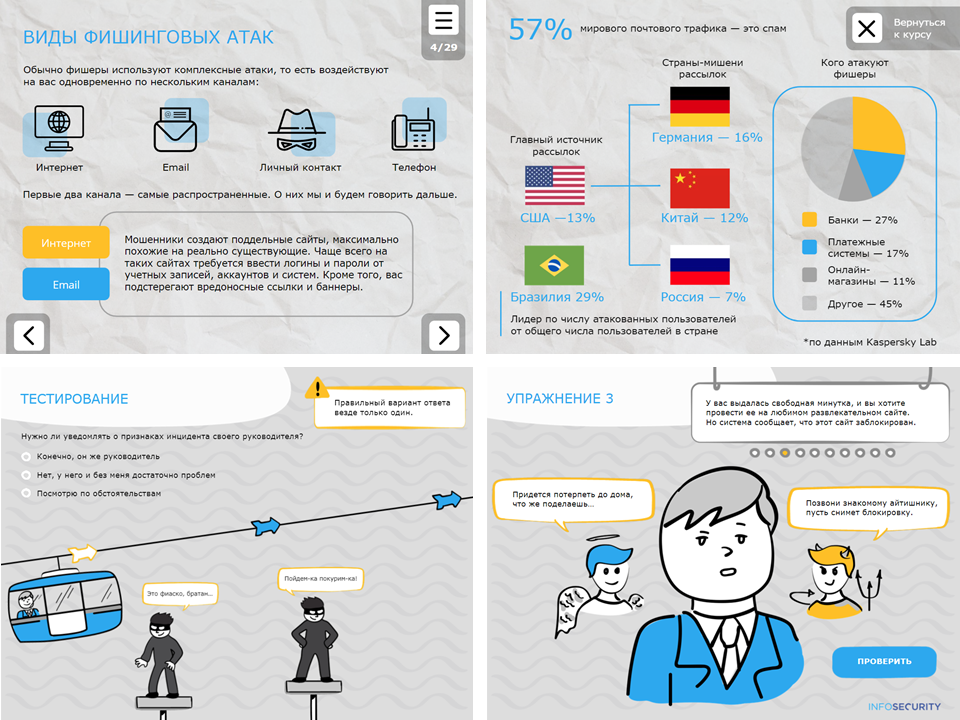
In the picture - slides from the electronic courses of our company.
Gamification is especially actively used in e-courses. It involves the addition of game elements: awards and achievements, the gradual complication of tasks, a fascinating story, characters. Gamification is generally an interesting story, because it can be completely electronic, and it can “flow” into real life. For example, for the successful completion of courses on IB employee can be awarded one extra day of vacation. Such things, of course, are coordinated with HR. Who among us has not dreamed at work about computer games?
Microtraining involves the supply of material in small blocks and the consolidation of each block with practical tasks. For example, I looked at 5 course slides - answer a test question or do a small exercise. If we are talking about videos, they should be no more than one and a half minutes long. It is better to make a series of short clips (by the way, they can be combined with one funny plot) than to make an employee watch a seven-minute sermon. But you shouldn’t split up the training to infinity: you can lose the logic of the story.
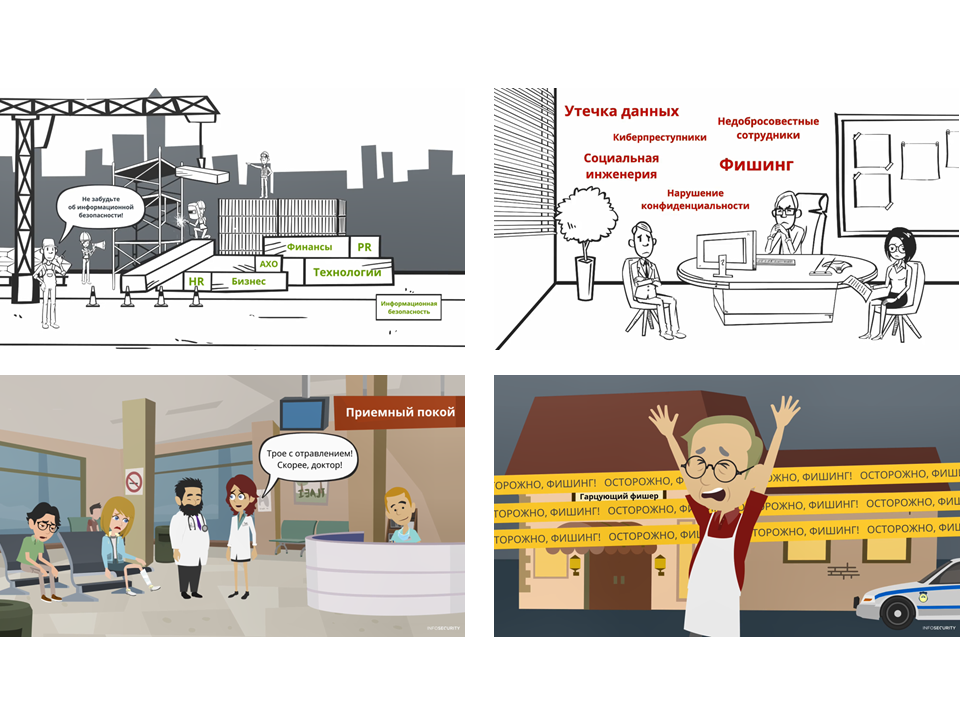
In the picture - screenshots from our videos
In addition to full-time and distance learning, additional training materials are very useful. Memos, posters, stickers and screensavers do an excellent job with the task of making learning diverse and memorable. Do not be afraid to involve in their design professional designers and illustrators: the materials will benefit from it.

The picture shows screenshots from the Phishing Battle flash game.
It is impossible to force a person to teach what he is not interested in and to observe what he does not understand. By creating comprehensive training programs for employees, presenting the material in simple and accessible language and putting it into play form, you essentially make a contribution to security - yours, your company and your customers. And if everything is done "according to science", your investments will certainly pay off.
Alexander Dvoryansky, Commercial Director, Infosecurity a Softline company
At one time, Canadian psychologist Elliot Jacks introduced the concept of "corporate culture". I allow myself to use the term "digital hygiene". This is the part of the corporate culture that determines what actions of employees and how they affect the company's information security.

I’ll draw a little attention to our industry, so that you understand why this topic is interesting to me. Infosecurity provides information security, system integration and consulting services. It is important for us to show that we can protect not only the data that customers trust us, but also their own information assets. Even a minor security incident in a cybersecurity company can strike its reputation. And to rise after such a blow is not easy.
So, the formation of digital hygiene in the company is affected by:
- Raising awareness of information security staff
- Distribution of access to information
- The use of technical means of control and monitoring information
Today I’ll dwell on the first of these three whales - raising awareness, or, as it is now fashionable to say, avarnes.
Why is it even needed?
In any self-respecting company, there are internal regulations, policies and methodologies about the rules for processing information of limited access. Alas, the mere existence of these documents does not give anything. Real protection is provided by employees who exactly follow the requirements specified in the documents. But where to find such ideal employees?
The trick is not to look for them, but, let's say, to grow them. The complex of training activities and materials allows you to create in the company a culture of working with information. If everything is right, the employees start to follow the IB rules at the reflex level - and you no longer need to worry that one of them does not block the computer screen, lose the token or forget the quarterly report in the printer tray.
Well, how to pick up everything?
First, divide your employees into groups and identify topics that are relevant to each group. Top managers are unlikely to be interested in exploring current software vulnerabilities, but for developers - very much so.
When topics are defined, think about the formats of educational materials: they also need to be personalized. For example, front-office employees do not have much free time, and sometimes there is no personal working computer. They will suit bright posters and short videos that can be placed and displayed in sales areas. And back-office employees can pay more attention to training, so it’s better to address e-courses and training mailings.
Another good practice is to check that your employees already know before conducting training in information security. The easiest way to do this is to test and send out phishing emails. So you will understand which topics need to pay more attention. And, of course, you shouldn’t forget about performance monitoring in the learning process and after it.
Can you elaborate on the formats?
Let's start with the good old full-time study. In some way, it is irreplaceable: everyone knows that information is perceived much better when accompanied by live communication. Training can be carried out in the classical form or by the case method. In the second case, the instructor divides the students into groups, describes the problem that is relevant to the company, and invites each group to give and justify its own version of its solution. It is possible to combine two types of trainings: conduct an introductory for employees on their first working day, and case training - monthly or quarterly.
Distance learning is a worthy competition to full-time, and in the future, most likely, will completely pull the blanket over himself. Electronic courses, videos, mailings and online games are good because employees can view them on different types of devices at a convenient time. And they also provide an opportunity to boast to competitors with the words “gamification” and “micro-education”.

In the picture - slides from the electronic courses of our company.
Gamification is especially actively used in e-courses. It involves the addition of game elements: awards and achievements, the gradual complication of tasks, a fascinating story, characters. Gamification is generally an interesting story, because it can be completely electronic, and it can “flow” into real life. For example, for the successful completion of courses on IB employee can be awarded one extra day of vacation. Such things, of course, are coordinated with HR. Who among us has not dreamed at work about computer games?
Microtraining involves the supply of material in small blocks and the consolidation of each block with practical tasks. For example, I looked at 5 course slides - answer a test question or do a small exercise. If we are talking about videos, they should be no more than one and a half minutes long. It is better to make a series of short clips (by the way, they can be combined with one funny plot) than to make an employee watch a seven-minute sermon. But you shouldn’t split up the training to infinity: you can lose the logic of the story.

In the picture - screenshots from our videos
In addition to full-time and distance learning, additional training materials are very useful. Memos, posters, stickers and screensavers do an excellent job with the task of making learning diverse and memorable. Do not be afraid to involve in their design professional designers and illustrators: the materials will benefit from it.

The picture shows screenshots from the Phishing Battle flash game.
So it’s all about diversity?
It is impossible to force a person to teach what he is not interested in and to observe what he does not understand. By creating comprehensive training programs for employees, presenting the material in simple and accessible language and putting it into play form, you essentially make a contribution to security - yours, your company and your customers. And if everything is done "according to science", your investments will certainly pay off.
Alexander Dvoryansky, Commercial Director, Infosecurity a Softline company
